August 2025 saw critical vulnerabilities in software like WinRAR, SharePoint, and Azure OpenAI, with risks including remote code execution and data breaches. Patches available for most; immediate action recommended. 2025-9-2 12:28:20 Author: securityboulevard.com(查看原文) 阅读量:19 收藏
August brought serious security concerns with critical vulnerabilities in software like WinRAR and SharePoint. These CVEs & Vulnerabilities of August 2025 have the potential to expose you to major risks.
In this blog, we’ll break down the most impactful vulnerabilities discovered this month, why they matter, and what steps you need to take to protect yourself.
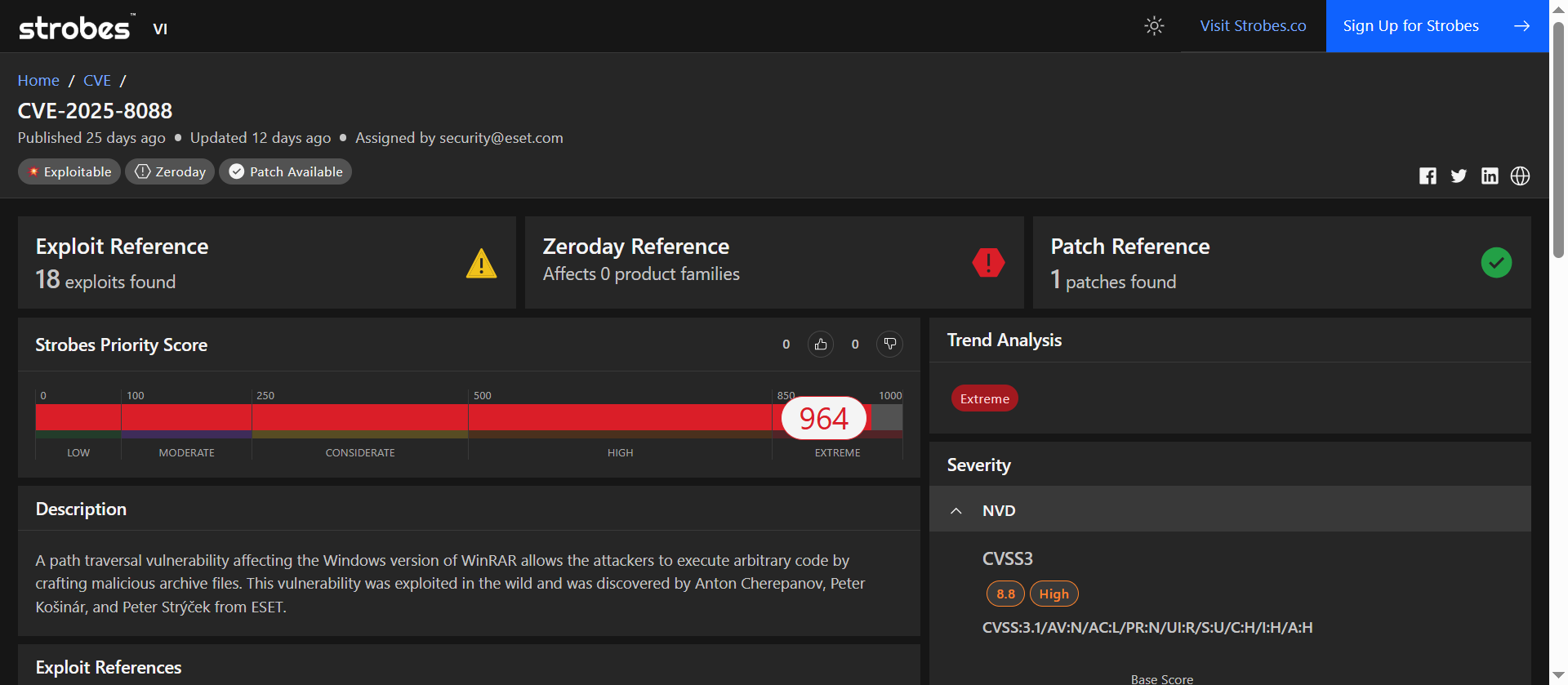
1. CVE-2025-8088: Directory Traversal Vulnerability in WinRAR
CVE-2025-8088 is a critical directory traversal vulnerability in the Windows version of WinRAR, allowing attackers to execute arbitrary code by crafting malicious archive files. This flaw has been actively exploited in the wild, particularly by the Russian-aligned threat group RomCom, which has used it to deploy backdoor malware onto targeted systems.
Overview
| Field | Details |
| CVSS v3.1 | 8.8 (High) |
| Strobes Priority Score | 964 / 1000 (Critical) |
| Exploit Availability | Actively exploited in the wild |
| Patch Available | Yes (WinRAR 7.13) |
| Vulnerability Type | Directory Traversal |
| Affected Versions | WinRAR versions prior to 7.13 |
| CISA KEV Catalog | Yes (Action due by 2025-09-02) |
Vulnerability Breakdown
CVE-2025-8088 arises from WinRAR’s failure to properly handle pathnames in archives, allowing attackers to exploit alternate data streams (ADS) to perform directory traversal. By embedding malicious files in these streams, attackers can place files in sensitive system directories, such as the Windows Startup folder, enabling automatic execution upon system reboot. This vulnerability affects not only WinRAR but also related components like UnRAR.dll and the portable UnRAR source code.
Impact of Exploitation
If exploited, this vulnerability could lead to:
- Remote Code Execution: Attackers can execute arbitrary code on the affected system.
- Persistence: Malicious files placed in startup directories ensure execution upon system reboot.
- Data Breach: Potential unauthorized access to sensitive information.
- Network Compromise: Further exploitation within the network environment.
RomCom has used this vulnerability to deploy backdoors like SnipBot, RustyClaw, and Mythic Agent, targeting sectors such as government, defense, and logistics across Europe and North America.
Mitigation & Patching
| Mitigation Step | Status |
| Patch Availability | WinRAR 7.13 released on 2025-07-30 |
| Exploit Activity | Actively exploited in the wild |
| Immediate Workaround | Upgrade to WinRAR 7.13 |
| Hardening Tip | Use Windows Software Restriction Policies (SRP) and Image File Execution Options (IFEO) to block unauthorized executables |
| Detection | Monitor for unusual file extraction activities and the presence of unauthorized executables in startup directories |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-8088 is a high-severity vulnerability with a CVSS score of 8.8, indicating significant risk. The active exploitation by a sophisticated threat group, coupled with the availability of a public exploit, underscores the urgency of addressing this issue. The vulnerability’s impact is compounded by WinRAR’s widespread use and the lack of an auto-update mechanism, requiring manual intervention to mitigate the risk.
Strobes Recommendation
Organizations using WinRAR should immediately upgrade to version 7.13. Additionally, implementing SRP and IFEO can provide an added layer of defense against unauthorized execution. Regular monitoring for signs of exploitation and unauthorized file placements is also recommended to detect and respond to potential incidents promptly.
Bottomline
Directory traversal vulnerability in WinRAR. Active exploitation by the RomCom group. Remote code execution is possible. Device compromise is imminent without mitigation. Patch available in WinRAR 7.13. Immediate update required.
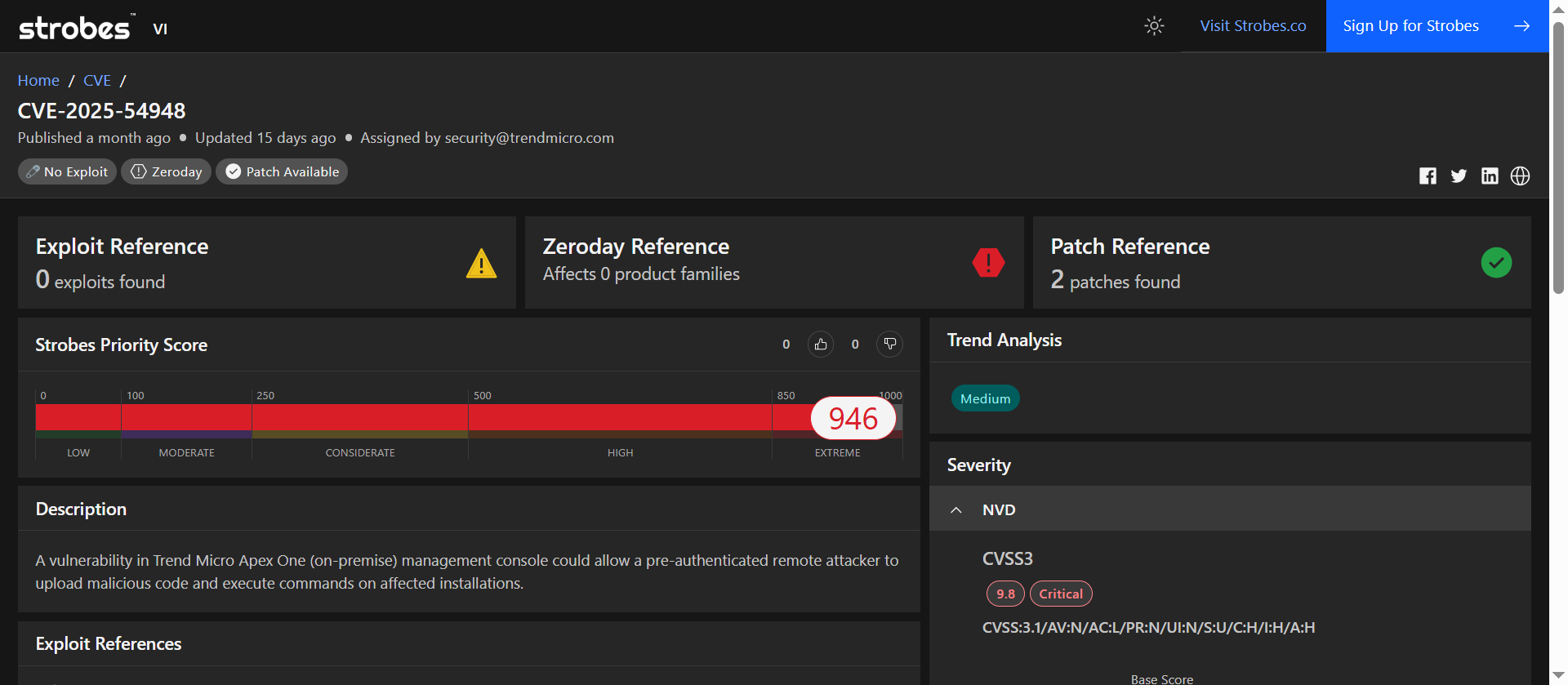
2. CVE-2025-54948: Command Injection Vulnerability in Trend Micro Apex One Management Console
CVE-2025-54948 is a critical command injection vulnerability affecting the on-premise version of Trend Micro Apex One Management Console. This flaw allows unauthenticated remote attackers to upload malicious code and execute arbitrary commands on affected installations, posing significant risks to enterprise environments. The vulnerability has been actively exploited in the wild.
Overview
| Field | Details |
| CVSS v3.1 | 9.4 (Critical) |
| Strobes Priority Score | 946 / 1000 (Critical) |
| Exploit Availability | Actively exploited in the wild |
| Patch Available | Yes (FixTool_Aug2025 and Critical Patch) |
| Vulnerability Type | OS Command Injection |
| Affected Versions | Apex One 2019 Management Server Version 14039 and below |
| CISA KEV Catalog | Yes (Action due by 2025-09-08) |
Vulnerability Breakdown
CVE-2025-54948 arises from improper input validation in the Apex One Management Console, allowing attackers to inject and execute arbitrary OS commands. Exploitation requires network or physical access to the vulnerable system. The flaw has been observed in active attacks, underscoring its severity.
Impact of Exploitation
If exploited, this vulnerability could lead to:
- Remote Code Execution: Attackers can execute arbitrary commands on the affected system.
- System Compromise: Full control over the Apex One Management Console, potentially leading to further network penetration.
- Data Breach: Access to sensitive information stored within the console.
- Service Disruption: Potential interruption of endpoint protection services.
The exploitation of this vulnerability has been linked to the deployment of malware and ransomware in targeted environments.
Mitigation & Patching
| Mitigation Step | Status |
| Patch Availability | FixTool_Aug2025 (Short-term Mitigation) and Critical Patch released on August 15, 2025 |
| Exploit Activity | Actively exploited in the wild |
| Immediate Workaround | Apply FixTool_Aug2025 to block known exploits |
| Hardening Tip | Restrict access to the Management Console by implementing source IP restrictions |
| Detection | Monitor for unusual file uploads and command executions on the Management Console |
Applying the FixTool_Aug2025 disables the Remote Install Agent function temporarily. The Critical Patch restores this functionality and provides a permanent fix.
Why is this CVE in Our Top Picks of the Month?
CVE-2025-54948 is assigned a CVSS v3.1 score of 9.4, indicating a critical severity level. The vulnerability’s active exploitation, combined with the availability of a public exploit and the absence of an auto-update mechanism, necessitates immediate attention. The widespread deployment of Apex One in enterprise environments amplifies the potential impact of this flaw.
Strobes Recommendation
Organizations using Trend Micro Apex One should immediately apply the FixTool_Aug2025 and subsequently the Critical Patch to mitigate this vulnerability. Additionally, restrict access to the Management Console to trusted networks and monitor for signs of exploitation. Assume exposure and initiate forensic investigations if the console has been externally accessible.
Bottomline
Critical OS command injection vulnerability in Trend Micro Apex One Management Console. Active exploitation observed. Remote code execution is possible. Patch available. Immediate action is required.
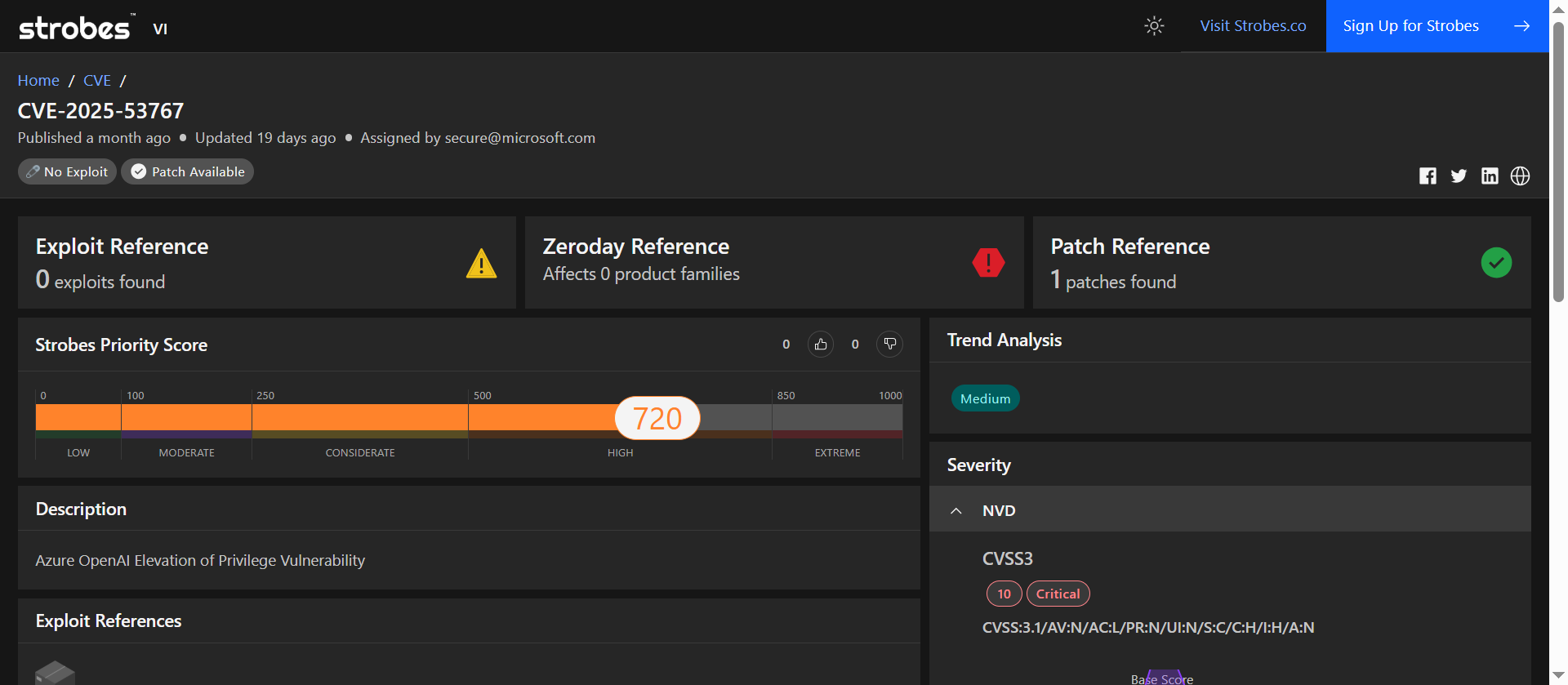
3. CVE-2025-53767: Azure OpenAI Elevation of Privilege Vulnerability
CVE-2025-53767 is a critical elevation of privilege vulnerability in Azure OpenAI services, identified during Microsoft’s August 2025 Patch Tuesday. This flaw allows unauthenticated attackers to exploit server-side request forgery (SSRF) mechanisms, potentially gaining unauthorized access to sensitive internal resources within the Azure environment.
Overview
| Field | Details |
| CVSS v3.1 | 10.0 (Critical) |
| Strobes Priority Score | 720 / 1000 (High) |
| Exploit Availability | No public exploit reported |
| Patch Available | Yes (Released August 2025) |
| Vulnerability Type | Server-Side Request Forgery (SSRF) |
| Affected Versions | All Azure OpenAI services prior to the patch |
Vulnerability Breakdown
CVE-2025-53767 stems from insufficient validation of user-supplied input in Azure OpenAI services, enabling attackers to craft requests that the server processes without proper authorization checks. This flaw, classified under CWE-918, allows attackers to bypass security controls and access internal endpoints, such as the Azure Instance Metadata Service, potentially exposing sensitive information like access tokens.
Impact of Exploitation
If exploited, this vulnerability could lead to:
- Unauthorized Access: Attackers gaining access to internal Azure resources.
- Privilege Escalation: Elevation of privileges within the Azure environment.
- Data Exposure: Leakage of sensitive information, including access tokens and credentials.
- Potential Lateral Movement: Facilitation of further attacks within the cloud infrastructure.
Given the nature of the vulnerability, exploitation could have significant implications for organizations relying on Azure OpenAI services for critical operations.
Mitigation & Patching
| Mitigation Step | Status |
| Patch Availability | Microsoft released patches in August 2025 |
| Exploit Activity | No public exploit reported |
| Immediate Workaround | Apply the latest security updates from Microsoft |
| Hardening Tip | Review and restrict network access controls to internal endpoints |
| Detection | Monitor for unusual request patterns or unauthorized access attempts |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-53767 is a high-severity vulnerability with a CVSS score of 10.0, indicating critical risk. The potential for unauthorized access and privilege escalation within Azure OpenAI services makes this flaw particularly concerning. Although no public exploit has been reported, the nature of the vulnerability necessitates immediate attention and remediation.
Strobes Recommendation
Organizations utilizing Azure OpenAI services should promptly apply the security patches released by Microsoft in August 2025. Additionally, reviewing and tightening network access controls to internal endpoints can help mitigate the risk associated with this vulnerability.
Bottomline
Critical SSRF vulnerability in Azure OpenAI services. Potential for unauthorized access and privilege escalation. Patch available; immediate application recommended. No public exploit reported.
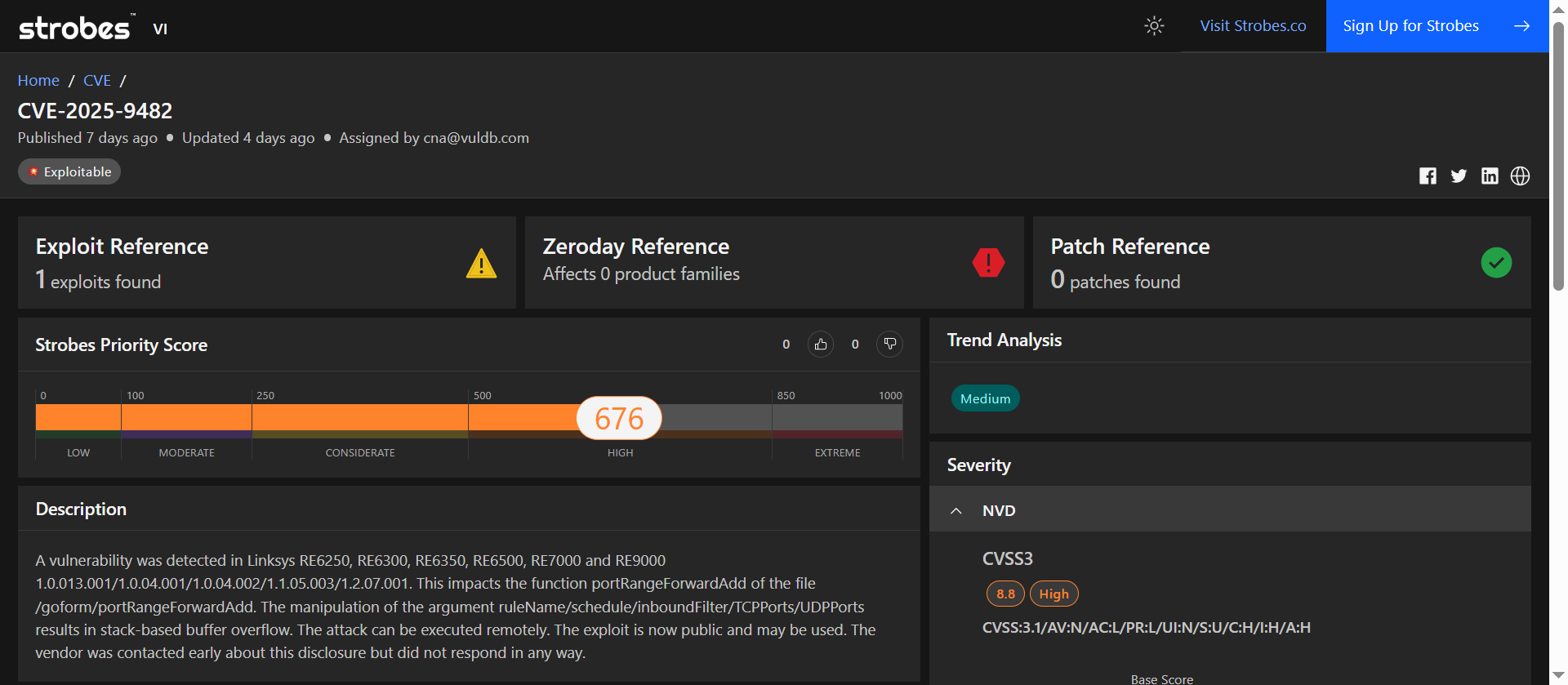
4. CVE-2025-9482: Stack-based Buffer Overflow in Linksys RE Series Range Extenders
CVE-2025-9482 has been flagged as high risk due to its stack-based buffer overflow vulnerability in Linksys RE series range extenders, which leads to potential remote code execution and device compromise with no patch currently available.
Overview
| Field | Details |
| CVSS v3.1 | 8.8 (High) |
| Strobes Priority Score | 676 / 1000 (High) |
| Exploit Availability | 1 known public exploit |
| Patch Available | No patch available |
| Trend Analysis | High (actively exploited, ongoing attacks) |
| Vulnerability Type | Stack-based buffer overflow |
| Affected Versions | RE6250, RE6300, RE6350, RE6500, RE7000, RE9000 |
Vulnerability Breakdown
CVE-2025-9482 exists in the Linksys RE series range extenders due to improper handling of user-supplied input parameters in the /goform/portRangeForwardAdd endpoint. The overflow allows attackers to overwrite adjacent memory, potentially leading to arbitrary code execution.
Key Details:
- No authentication is required to exploit this vulnerability.
- Attackers can send crafted HTTP requests to the vulnerable endpoint.
- Malicious input can overwrite memory, enabling remote code execution.
- The flaw has a high potential for exploitation due to the lack of authentication and the ease of an attack vector.
Impact of Exploitation
If exploited, CVE-2025-9482 could result in:
- Remote Code Execution: Attackers can execute arbitrary code on the affected device.
- Device Compromise: Full control of the affected device, allowing attackers to perform malicious actions or further network attacks.
- Network Disruption: Exploitation can cause network service disruptions, particularly in environments with vulnerable devices.
- Data Breach: Attackers can access sensitive data from the compromised device, impacting confidentiality and trust.
As the device is often deployed in consumer or enterprise networks, exploitation could lead to lateral movement across internal systems.
Mitigation & Patching
| Mitigation Step | Status |
| Patch Availability | No patch released as of September 2025 |
| Exploit Activity | Public exploit available, actively exploited |
| Immediate Workaround | Isolate vulnerable devices from critical network segments |
| Hardening Tip | Use firewalls to block access to vulnerable ports and endpoints |
| Detection | Monitor for unusual requests to /goform/portRangeForwardAdd endpoint |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-9482 scores a significant 676 on the Strobes Priority Scale due to its potential for remote code execution with minimal attacker effort.
What Drove the High Score:
- Unauthenticated Exploitation: No need for authentication to exploit this vulnerability.
- High Impact: Full device compromise leading to a potential network breach.
- Available Exploit: An active public exploit is already available, increasing the likelihood of attacks.
- No Vendor Patch: No patch has been released, leaving devices exposed to attacks.
- Wide Exposure: Linksys RE series range extenders are common in both consumer and small enterprise networks, increasing the attack surface.
Strobes Recommendation
If you’re using a Linksys RE series range extender (RE6250, RE6300, RE6350, RE6500, RE7000, RE9000), immediately isolate affected devices from your network. Employ network segmentation and monitor for exploit attempts. Until a vendor patch is available, assume exposure and treat the devices as compromised.
Bottomline
Stack-based buffer overflow in Linksys RE range extenders. Active exploit with no patch. Remote code execution is possible. Device compromise is imminent without mitigation.
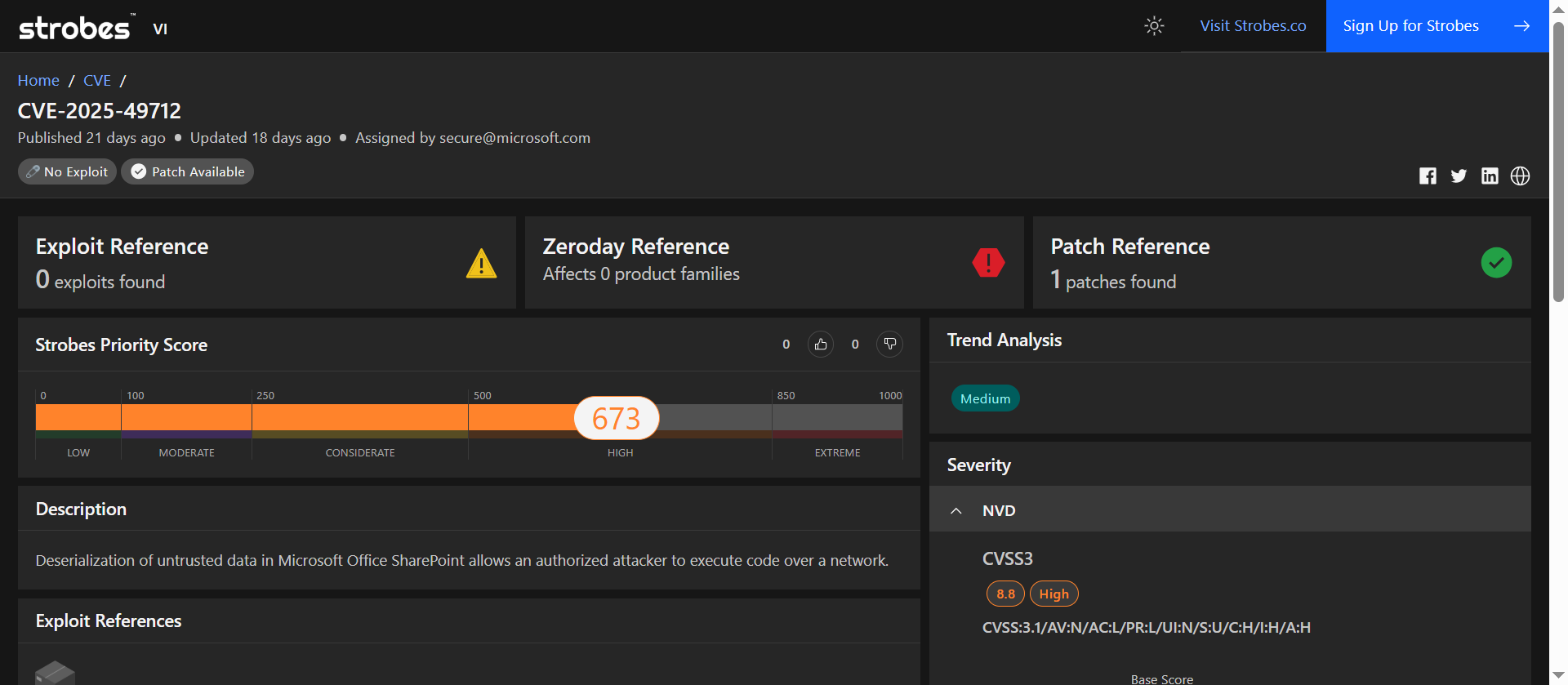
5. CVE-2025-49712: Remote Code Execution via Deserialization in Microsoft SharePoint
CVE-2025-49712 is a high-severity vulnerability in Microsoft SharePoint that allows authenticated attackers to execute arbitrary code remotely through improper deserialization of untrusted data. This flaw was disclosed as part of Microsoft’s August 2025 Patch Tuesday updates.
Overview
| Field | Details |
| CVSS v3.1 | 8.8 (High) |
| Strobes Priority Score | 673 / 1000 (High) |
| Exploit Availability | No public exploit reported |
| Patch Available | Yes (August 2025 Patch Tuesday) |
| Vulnerability Type | Deserialization of untrusted data |
| Affected Versions | SharePoint Server 2016, 2019 |
Vulnerability Breakdown
CVE-2025-49712 arises from SharePoint’s failure to properly validate data during deserialization processes. An authenticated attacker with Site Owner privileges can exploit this vulnerability to inject malicious code, leading to remote code execution on the affected SharePoint server.
Impact of Exploitation
If exploited, this vulnerability could lead to:
- Remote Code Execution: Attackers can execute arbitrary code on the affected SharePoint server.
- Privilege Escalation: Gain elevated privileges within the SharePoint environment.
- Data Compromise: Access to sensitive information stored within SharePoint.
- Network Propagation: Potential to move laterally within the network from the compromised server.
Given SharePoint’s role in enterprise collaboration, exploitation could have widespread organizational impacts.
Mitigation & Patching
| Mitigation Step | Status |
| Patch Availability | Security updates released on August 12, 2025 |
| Exploit Activity | No public exploit reported |
| Immediate Workaround | Apply the security updates promptly |
| Hardening Tip | Restrict Site Owner privileges to trusted users |
| Detection | Monitor for unusual activities in SharePoint logs |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-49712 has a CVSS score of 8.8, indicating high severity. The vulnerability’s impact is significant due to the potential for remote code execution and the critical role of SharePoint in organizational operations. While no public exploit has been reported, the existence of a patch underscores the importance of timely remediation.
Strobes Recommendation
Organizations utilizing affected versions of SharePoint should prioritize applying the security updates provided in the August 2025 Patch Tuesday. Additionally, reviewing and restricting Site Owner privileges can further mitigate the risk. Regular monitoring of SharePoint logs for anomalous activities is also recommended to detect potential exploitation attempts.
Bottomline
Deserialization vulnerability in Microsoft SharePoint. Remote code execution is possible. Patch available in August 2025 updates. Apply updates promptly to mitigate risks.
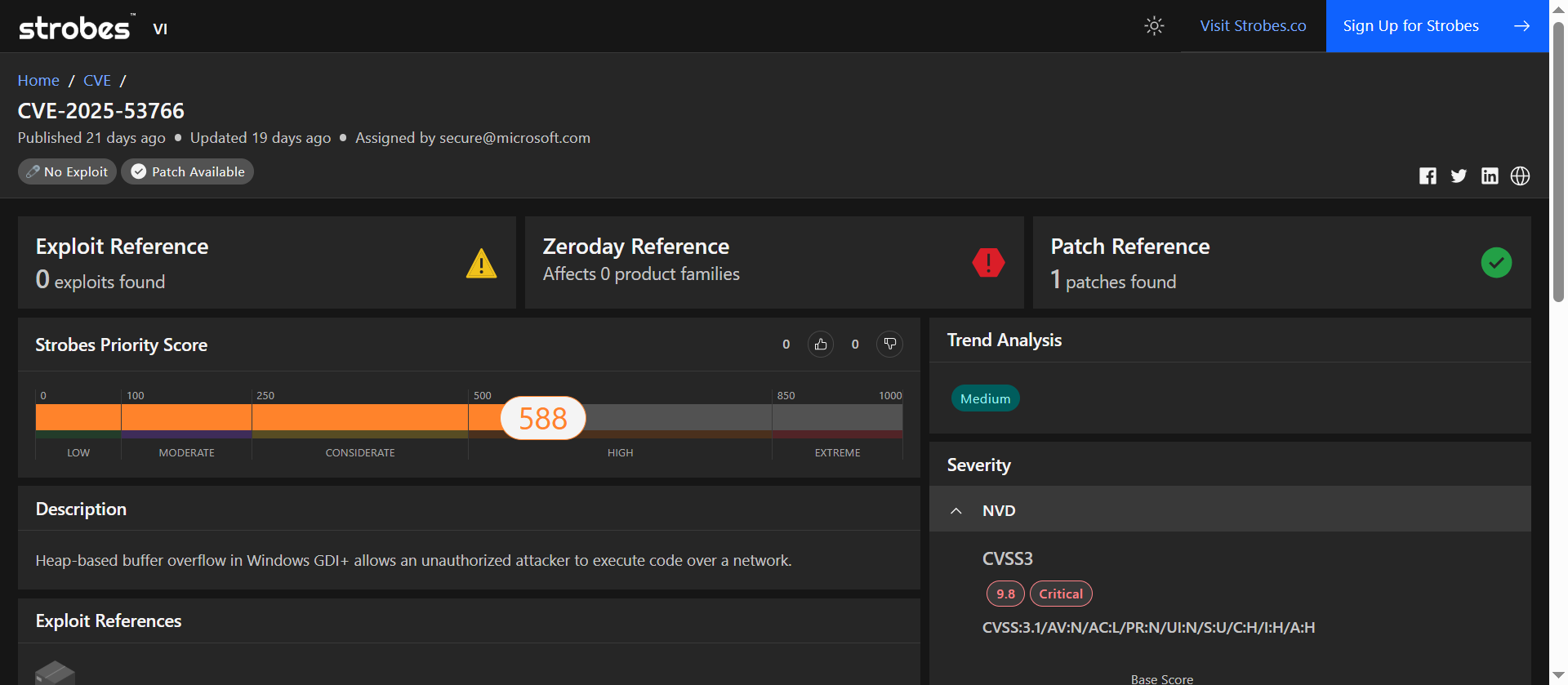
6. CVE-2025-53766: Heap-Based Buffer Overflow in Windows GDI+
CVE-2025-53766 is a critical heap-based buffer overflow vulnerability in Windows GDI+ that allows unauthenticated remote attackers to execute arbitrary code over a network connection without user interaction. This vulnerability was disclosed in August 2025 and affects various versions of Microsoft Windows, including Windows Server editions and Windows 10 through Windows 11.
Overview
| Field | Details |
| CVSS v3.1 | 9.8 (Critical) |
| Strobes Priority Score | 588 / 1000 (High) |
| Exploit Availability | No known public exploits |
| Patch Available | Yes (August 2025 Patch Tuesday) |
| Vulnerability Type | Heap-based buffer overflow |
| Affected Versions | Windows Server 2008 SP2, 2016, 2019, 2022, 2025; Windows 10 versions 1507–22H2; Windows 11 versions 22H2–24H2; Microsoft Office for Universal and Android versions prior to 16.0.14326.22618 and 16.0.19127.20000, respectively. |
Vulnerability Breakdown
CVE-2025-53766 arises from a heap-based buffer overflow in Windows GDI+, which can be triggered by processing specially crafted metafiles embedded in documents. An attacker can exploit this vulnerability by convincing a user to download and open a malicious document, leading to remote code execution without requiring user interaction. Notably, the Preview Pane is not an attack vector for this vulnerability.
Impact of Exploitation
If exploited, this vulnerability could lead to:
- Remote Code Execution: Attackers can execute arbitrary code on the affected system.
- System Compromise: Full control over the affected system, allowing for further malicious activities.
- Data Breach: Potential unauthorized access to sensitive information.
- Network Propagation: Exploitation can facilitate lateral movement within the network.
Given the critical nature of this vulnerability, it poses significant risks to the confidentiality, integrity, and availability of affected systems.
Mitigation & Patching
| Mitigation Step | Status |
| Patch Availability | Microsoft released a patch on August 12, 2025. |
| Exploit Activity | No known public exploits; however, the high CVSS score and active exploitation potential warrant immediate attention. |
| Immediate Workaround | Apply the security update provided by Microsoft. |
| Hardening Tip | Ensure that all systems are updated with the latest security patches and consider implementing application whitelisting to prevent unauthorized code execution. |
| Detection | Monitor for unusual document processing activities and unauthorized access attempts to sensitive systems. |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-53766 is a high-severity vulnerability with a CVSS score of 9.8, indicating its critical nature. The potential for remote code execution without user interaction makes it particularly dangerous. Although there are no known public exploits, the widespread use of the affected components and the severity of the vulnerability necessitate prompt remediation. The Strobes Priority Score of 588 reflects its significant risk profile.
Strobes Recommendation
Organizations should immediately apply the security update provided by Microsoft to mitigate the risks associated with CVE-2025-53766. Regularly updating systems and implementing security best practices are essential to protect against such vulnerabilities. Given the critical nature of this vulnerability, it is advisable to treat affected systems as compromised until the patch is applied and the system is verified to be secure.
Bottomline
Heap-based buffer overflow in Windows GDI+. Remote code execution is possible without user interaction. Patch available in August 2025. Immediate update required
The post Top CVEs & Vulnerabilities of August 2025- Risks, Impacts & Fixes appeared first on Strobes Security.
*** This is a Security Bloggers Network syndicated blog from Strobes Security authored by Shubham Jha. Read the original post at: https://strobes.co/blog/top-cves-vulnerabilities-of-august-2025/
如有侵权请联系:admin#unsafe.sh