
网络犯罪分子滥用Meta广告平台发布虚假免费TradingView Premium应用广告,传播Brokewell恶意软件。该恶意软件针对安卓用户窃取敏感数据并实现远程控制。 2025-9-1 13:0:23 Author: www.bleepingcomputer.com(查看原文) 阅读量:13 收藏

Cybercriminals are abusing Meta’s advertising platforms with fake offers of a free TradingView Premium app that spreads the Brokewell malware for Android.
The campaign targets cryptocurrency assets and has been running since at least July 22nd through an estimated 75 localized ads.
Brokewell has been around since early 2024 and features a broad set of capabilities that include stealing sensitive data, remote monitoring and control of the compromised device.
Taking over the device
Researchers at cybersecurity company Bitdefender investigated the ads in the campaign, which use the TradingView branding and visuals and lure potential victims with the promise of a free premium app for Android.
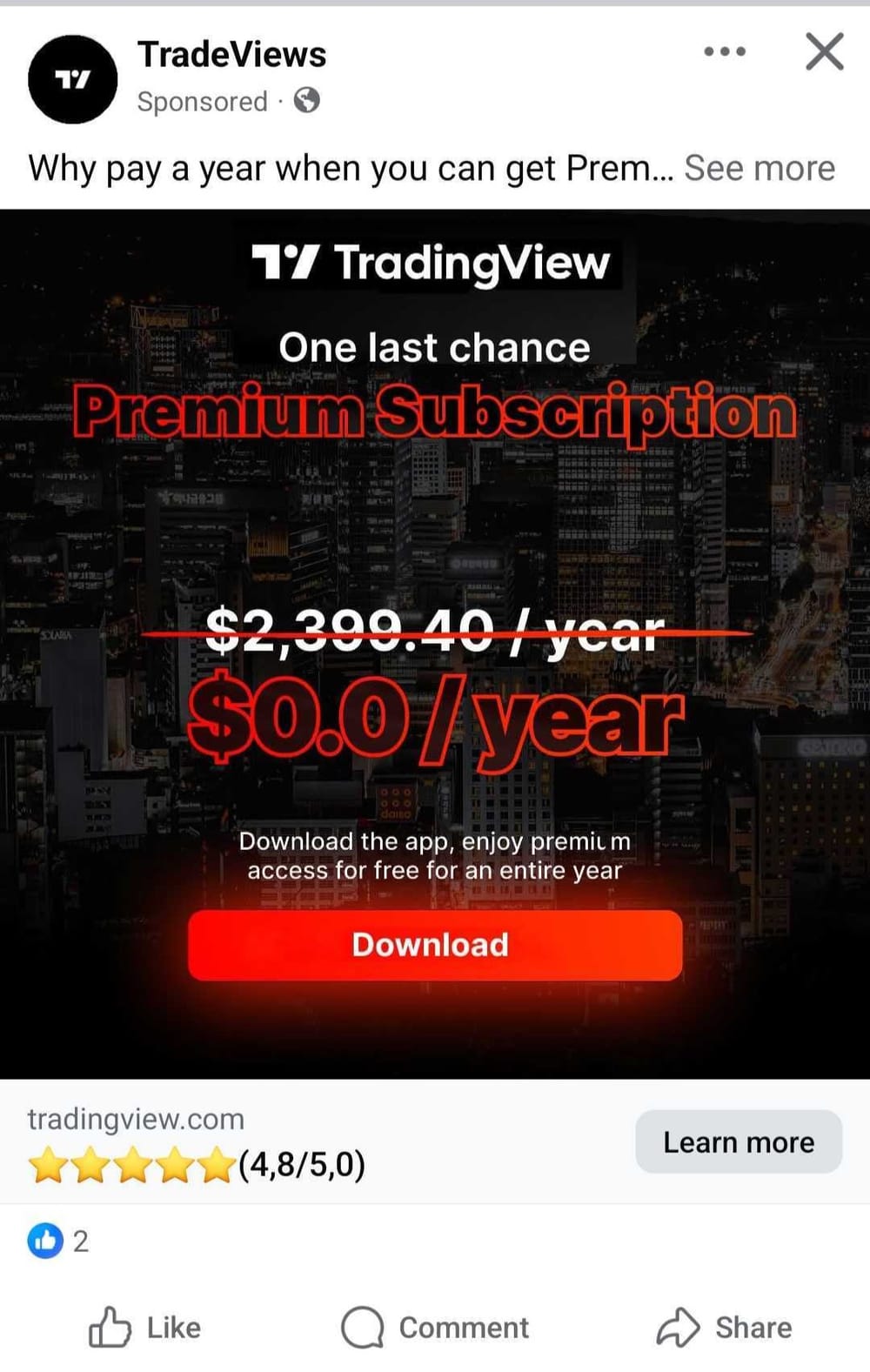
sourcce Bitdefender
They note that the campaign was specifically designed for mobile users, as accessing the ad from a different operating system would lead to harmless content.
Clicking from Android, however, redirected to a webpage mimicking the original TradingView site that provided a malicious tw-update.apk file hosted at tradiwiw[.]online/
“The dropped application asks for accessibility, and after receiving it, the screen is covered with a fake update prompt. In the background, the application is giving itself all the permissions it needs,” the researchers say in a report this week..
Furthermore, the malicious app also tries to obtain the PIN for unlocking the device by simulating an Android update request that needs the lockscreen password.
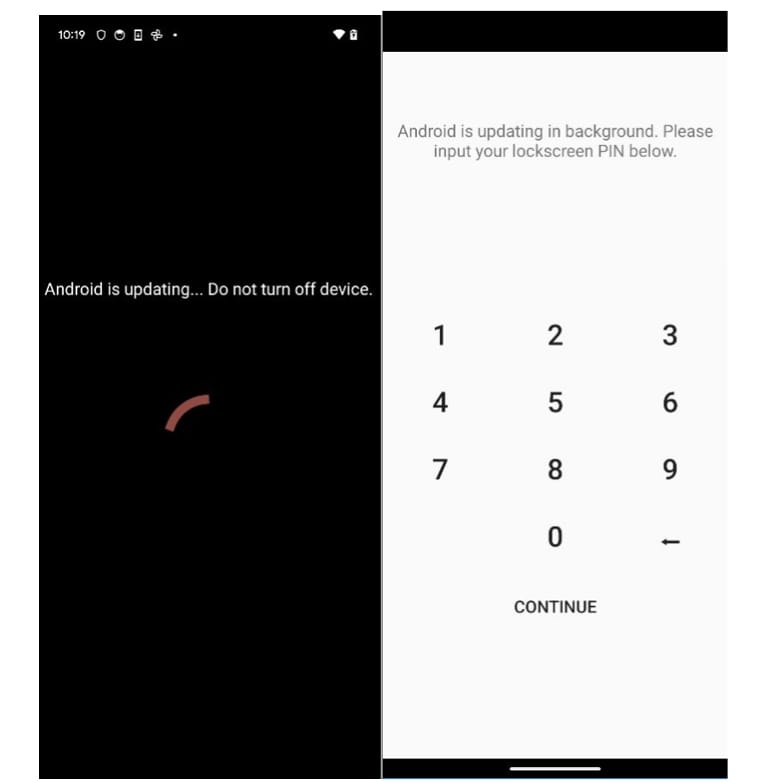
source: Bitdefender
According to Bitdefender, the fake TradingView app is “an advanced version of the Brokewell malware” that comes “with a vast arsenal of tools designed to monitor, control, and steal sensitive information:”
- Scans for BTC, ETH, USDT, bank account numbers (IBANs)
- Steals and exports codes from Google Authenticator (2FA bypass)
- Steals account by overlaying fake login screens
- Records screens and keystrokes, steals cookies, activates the camera and microphone, and tracks the location
- Hijacks the default SMS app to intercept messages, including banking and 2FA codes
- Remote control – can receive commands over Tor or Websockets to send texts, place calls, uninstall apps, or even self-destruct
The researchers provide a technical overview of how the malware works and an extended list of supported commands that includes more than 130 rows.
Bitdefender says that this campaign is part of a larger operation that initially used Facebook ads impersonating “dozens of well-known brands” to target Windows users.
如有侵权请联系:admin#unsafe.sh
