最近网络钓鱼攻击增多,利用邮件营销平台(如Klaviyo和Drip Global)、亚马逊AWS和Cloudflare服务进行隐藏。攻击者结合CAPTCHA、编码脚本等新手段逃避检测。Trustwave的PageML系统通过机器学习和规则框架有效识别此类威胁。 2025-8-28 15:53:46 Author: www.trustwave.com(查看原文) 阅读量:6 收藏
4 Minute Read
In recent months, Trustwave SpiderLabs, A LevelBlue Company, saw a significant increase in phishing URLs containing familiar patterns, similar phishing templates, and a resurgence in the use of email marketing platforms. The use of URL redirectors, along with the abuse of Amazon Web Hosting and Cloudflare services, was also widely observed. Trustwave operates a URL-scanning system that we call PageML. It is a hybrid system with machine learning and deep learning components supplemented by a URL intelligence and rules framework. It looks at URL structure and web page content in real-time and makes a prediction as to whether a web page is phishing/malicious or benign. Let’s take a look at some interesting phishing campaigns we observed recently. Last year, we observed and wrote about the different platforms being used in phishing. Since then, we’ve uncovered more email marketing platforms and their URLs being abused via phishing redirection. One such abused email marketing domain is ‘klclick3.com’, which is associated with Klaviyo, an email marketing and SMS automation platform. It is primarily used as a click-tracking domain to monitor user interactions with links in marketing and transactional emails sent via Klaviyo. In the first example, several phishing emails were seen using the subject ‘New Voicemail’ as a lure containing a phishing URL redirection that abuses the domain *.klclick3.com. The phishing email contains an exact URL link, hxxps://ctrk[.]klclick3[.]com/l/01JZH3WKJF7QV2A7B61MMD0G50_0/#Y2VsbGFyZG9vckBwYXJrZX Jjb29uYXdhcnJhZXN0YXRlLmNvbS5hdQ, that redirects to hxxps://arangogarcia[.]com/V-mailgoogleh/fwdevoice/payvefiyasgstafrom/#(email address), which is the final phishing page that targets a specific company of the victim. Upon checking the source code of the final phishing page, we found it uses the Chameleon phishing technique, wherein it fetches the domain of the email address and captures company information including the logo of the company to make it more convincing. Also, we note that using Clearbit URLs for images is quite alarming because this is commonly seen in phishing kits. Another red flag is that it also contains a method “addEventListener” that targets the event of “contextmenu” to disable right-clicking on the page. Another email marketing platform we found being abused was ‘dripemail2.com’, a domain owned by Drip Global. Similar to ‘klclick3.com’, it is primarily used as a click-tracking domain to monitor user interactions with links in emails sent through Drip’s platform. In this sample, the phishing email mimics DocuSign and contains a phishing link abusing ‘dripemail2.com’. The initial URL, hxxps://t[.]dripemail2[.]com/c/eyJhbGciOiJIUzI1NiJ9.eyJhdWQiOiJkZXRvdXIiLCJpc3MiOiJtb25vbGl0aCIsInN…{truncated}, redirects to a fake Microsoft Security page. After examining the source code, we found it contained a suspicious Base64-encoded hash that, when decoded, reveals a redirect to another phishing site. The final landing page is a phishing site that imitates Microsoft’s sign-in page. At the time of our analysis, VirusTotal showed that only Trustwave detected the phishing URLs, which leveraged email marketing platform services. In the second example, we observed phishing email samples using “Payment” or “Account Payable” lures targeting specific companies. The emails contain fake image attachments that contain clickable links that redirect to the final phishing site. The Reply-To header also contains a different email address not related to the company. The phishing email contains a malicious URL link, hxxps://oweqwe[.]s3.us-east-1[.]amazonaws[.]com/index.html#{Base64-encoded email address}, that redirects to a phishing page that mimics a Roundcube Webmail log-in page. The source code of this phishing page contains a Cloudflare Turnstile URL and uses an AJAX template for the submission of stolen credentials. This kind of HTML content structure is now mostly seen on phishing pages where they abuse Cloudflare services to avoid immediate detection. Once again, according to VirusTotal, only Trustwave detected this phishing URL abusing the Amazon Web Service domain. Recently, we also observed an increase in phishing URLs using compromised domains and CAPTCHA to evade automated detection. This example of a compromised URL, hxxps://airswift[.]ae/xxdocuslgn09600349.html, uses “Secure Document” to lure victims to input their email address. However, the source code reveals that this phishing page contains another phishing URL redirection. It also checks human verification using a Cloudflare service upon redirection. Finally, the code redirects to a fake Microsoft log-in page. Its source code contains highly encoded scripts. A closer look at the initial domain ‘airswift.ae’ shows it is benign and related to freight services. Threat actors tend to compromise legitimate domains to avoid being easily detected and to deceive victims into thinking that the login page is related to the domain or company. Last June, we also observed other compromised domains hosting “Secure Document” phishing pages linked to the Mamba2FA phishing service and more details on our X post. Unfortunately, phishing attacks are increasing, but they often use older, well-known techniques like compromised domains and redirectors. However, attackers now combine these tactics with new evasion methods such as CAPTCHA and encoded scripts. Cloudflare Turnstile is frequently abused for redirection as well. These phishing pages are very challenging to detect due to their constantly changing content. With Trustwave URL scanner, the combination of machine learning and domain expert rules is quite effective in identifying such threats.Email Marketing Platforms Seen on Phishing Emails

Figure 1. Screenshot of the phishing email sample that uses voicemail as a lure.
Figure 2. Screenshot of the phishing URL targeting the company of the victim.
Figure 3. Snippet of the source code of the phishing URL.
Figure 4. Screenshot of the phishing email sample that poses as a Docusign document as a lure.
Figure 5. Screenshot of the first phishing URL redirection.
Figure 6. Snippet of the source code of the initial phishing URL.
Figure 7. Screenshot of the decoded URL from Base64-encoded string.
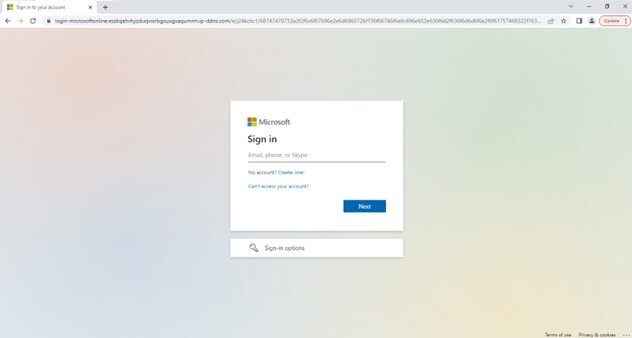
Figure 8. Screenshot of the final landing page that mimics the Microsoft sign-in page.
Figure 9. Screenshot of Trustwave’s detection in VirusTotal of the phishing URL abusing klclick3.com
Figure 10. Screenshot of Trustwave’s detection in VirusTotal of the phishing URL abusing dripemail2.comAmazon Web Services Used in Phishing

Figure 11. Screenshot of the phishing email sample that also contains a fake remittance image.
Figure 12. Screenshot of the phishing URL that mimics a Roundcube Webmail log-in page.
Figure 13. Snippet of the source code of the phishing URL.
Figure 14. Screenshot of Trustwave's detection in VirusTotal of the phishing URL abusing amazonaws.comCompromised Domains in Phishing Attacks

Figure 15. Screenshot of the initial phishing URL.
Figure 16. Snippet of the source code that contains phishing redirection.
Figure 17. Screenshot of the URL redirection to Cloudflare's human verification CAPTCHA.
Figure 18. Screenshot of the final landing page of the fake Microsoft log-in page.
Figure 19. Snippet of the obfuscated source code of the final phishing page.
Figure 20. Screenshot of the benign home page domain.
如有侵权请联系:admin#unsafe.sh