Cyble发现名为“SikkahBot”的安卓恶意软件自2024年7月起活跃于孟加拉国学生群体中。该恶意软件伪装成教育委员会应用以分发虚假奖学金信息,并通过收集敏感数据、滥用无障碍服务及执行USSD交易进行金融诈骗。其传播途径包括短链接和可疑APK下载网站,并利用Firebase服务器进行C2通信。尽管检测率低且变种频繁更新,建议用户提高警惕并采取安全措施以防范此类威胁。 2025-8-28 14:30:54 Author: cyble.com(查看原文) 阅读量:16 收藏
Executive Summary
Cyble Research and Intelligence Labs (CRIL) has uncovered an ongoing Android malware tracker named “SikkahBot,” active since July 2024 and explicitly targeting students in Bangladesh. Disguised as applications from the Bangladesh Education Board, the malware lures victims with promises of scholarships, coerces them into sharing sensitive information, and grants high-risk permissions. Once installed, SikkahBot harvests personal and financial data, intercepts SMS messages, abuses the Accessibility Service, and executes automated banking transactions, including USSD-based operations.
Key Takeaways
- SikkahBot targets Bangladesh explicitly by impersonating the Bangladesh Education Board to distribute fraudulent scholarship apps.
- It is distributed via shortened links that redirect to redirecticious APK download sites, which we suspect are being circulated via smishing attacks.
- It harvests sensitive personal details and payment information (wallet number, PIN, payment type).
- Victims are coerced into granting high-risk permissions, such as Accessibility Service, SMS access, call management, and overlay permissions, which enable deep device control.
- The malware intercepts bank-related SMS, abuses Accessibility Service to autofill credentials in banking apps (bKash, Nagad, DBBL) and executes automated USSD-based transactions.
- Active since July 2024, the malware maintains low detection rates on VirusTotal, while newer variants showcase enhanced automation features, highlighting the threat actors‘ ongoing development.
Overview
Cyble Research and Intelligence Labs (CRIL) has identified a new Android malware, “SikkahBot,” active since July 2024, that specifically targets students in Bangladesh. The malware poses as the Bangladesh Education Board to harvest banking information and carry out unauthorized transactions on infected devices. It is distributed through short links that redirect victims to malicious download URLs, which we suspect are being circulated via smishing attacks. The download URLs associated with this campaign are listed below.
- hxxps://bit[.]ly/Sikkahbord
- hxxps://bit[.]ly/Education-2025
- hxxps://bit[.]ly/Educ-govt
- hxxps://bit[.]ly/app-upobitti
- hxxps://bit[.]ly/D43SJ
- hxxp://sbs[.]short[.]gy/
- hxxps://apped[.]short[.]gy/
- hxxps://downloadapp[.]website/tyup[.]apk
- hxxps://appsloads[.]top/govt[.]apk
Upon installation, SikkahBot prompts users to enter sensitive information and then requests multiple permissions, including enabling the Accessibility Service, to facilitate financial fraud. Its primary techniques include phishing combined with SMS harvesting and automated USSD-based transactions. The technical analysis section provides a detailed breakdown of the malware’s operation.
The initial samples suggested that malware relied on phishing and SMS interception to carry out financial fraud. However, starting this month, we observed that the threat actors have enhanced it with Accessibility Service abuse to enable automated transactions. The figure below highlights the differences between the earlier and the latest variant. (see Figure 1)

Although SikkahBot has been active since July 2024, both recent and older variants remain largely undetected on VirusTotal. Our analysis uncovered more than 10 samples linked to this, suggesting ongoing iterations and development. (see Figure 2)

Technical Analysis
Upon installation, SikkahBot prompts students to sign in using either Google or Facebook. Regardless of the chosen login method, the app then requests the student’s personal details, such as name, department, and institute name, as shown in the figure below. (see Figure 3)
After the student’s details are entered, the application moves on to request payment information, including wallet number, wallet PIN, and payment type. Once this data is provided, the user receives a message stating that a representative will contact them soon. (see Figure 4)
After registration, SikkahBot presents a settings screen prompting the user to grant several permissions, including Accessibility Service, SMS access, call management, and the ability to display over other apps. Once these permissions are approved, the victim is redirected to a home page that shows fake banners showcasing other students supposedly receiving scholarships. (see Figure 5)
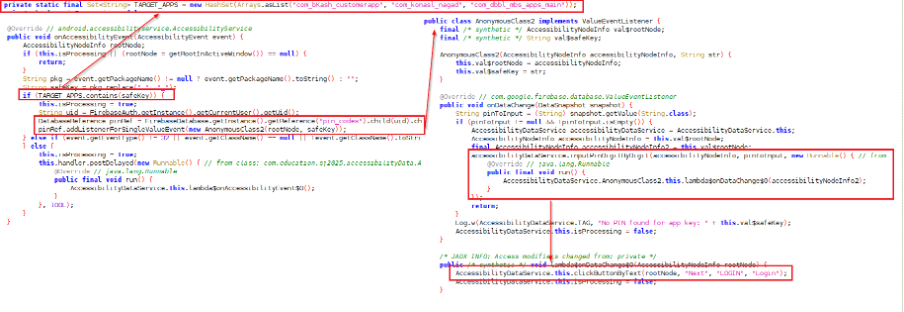
It then registers an SMSBroadcast receiver to monitor all incoming text messages on the compromised device. It maintains a list of keywords that include bank names such as “bKash,” “NAGAD,” and “MYGP,” along with specific numbers like “16216,” “26969,” and “009638543210.” If an incoming SMS contains any of these keywords, the message is captured and forwarded to the attacker’s server at hxxps://update-app-sujon-default-rtdb[.]firebaseio.com. (see Figure 6)
Similarly, SikkahBot exploits the Accessibility Service to track user activity on three banking applications, “BKash,” “Nagad”, and “Dutch-Bangla Bank” in Bangladesh. When it detects that the user is interacting with any of these apps, it retrieves a PIN from the Firebase server. It attempts to automatically enter it into the login fields, bypassing user input. (see Figure 7)

If the user is not engaging with targeted banking applications, it switches to executing USSD calls to carry out transactions. It receives the USSD code and SIM slot details from the Firebase server and initiates the call. When the USSD response dialog appears, the malware automatically fills in the required fields and attempts to click buttons labelled “SEND,” “send,” or “ok.” This technique enables the malware to perform transactions without an active internet connection. (see Figure 8 and Figure 9)

The combination of phishing, automated banking activity, and offline USSD exploitation makes it a highly effective tool for financial fraud against unsuspecting students.
Conclusion
The SikkahBot Android malware we identified targeting Bangladesh users leverages phishing, SMS interception, Accessibility Service abuse, and offline USSD automation to execute unauthorized transactions. As the primary targets, students face a heightened risk of identity theft and financial fraud. Its ability to remain undetected and multiple active variants highlight the sophistication and persistence of the threat actors.
Reinforcing the imperative to strengthen mobile security controls, enhance threat visibility, and adopt proactive defense strategies is critical to mitigating this threat.
Cyble’s Threat Intelligence Platforms continuously monitor such emerging threats, phishing infrastructure, and malware activity across diverse sources. This proactive intelligence empowers organizations with early detection, brand and domain protection, infrastructure mapping, and attribution. Altogether, these capabilities provide a critical head start in mitigating and responding to evolving cyber threats.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers.
- Install Apps Only from Trusted Sources:
Download apps exclusively from official platforms like the Google Play Store. Avoid third-party app stores or links received via SMS, social media, or email. - Be Cautious with Permissions:
Never grant accessibility services or overlay permissions unless you’re certain of an app’s legitimacy. - Watch for Phishing Pages:
Always verify the URL and avoid suspicious links and websites that ask for sensitive information. - Enable Multi-Factor Authentication (MFA): Use MFA for banking and financial apps to add an extra layer of protection, even if credentials are compromised.
- Report Suspicious Activity: If you suspect you’ve been targeted or infected, report the incident to your bank and local authorities immediately. Reset credentials and perform a factory reset if needed.
- Use Mobile Security Solutions:Install a mobile security application that includes real-time scanning.
- Keep Your Device Updated: Ensure your Android OS and apps are updated regularly. Security patches often address vulnerabilities exploited by malware.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Procedure |
| Initial Access (TA0027) | Phishing (T1660) | Malware is distributed via phishing sites |
| Defense Evasion (TA0030) | Masquerading: Match Legitimate Name or Location (T1655.001) | Malware pretending to be a genuine application |
| Defense Evasion (TA0030) | Input Injection (T1516) | Malware can mimic user interaction, perform clicks and various gestures, and input data |
| Collection (TA0035) | Protected User Data: SMS Messages (T1636.004) | Collects SMSs |
| Command and Control (TA0037) | Application Layer Protocol: Web Protocols (T1437.001) | Malware uses FCM for C&C communication |
| Exfiltration (TA0036) | Exfiltration Over C2 Channel (T1646) | Sending exfiltrated data over the C&C server |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| hxxps://downloadapp[.]website/tyup[.]apk hxxps://downloadapp[.]website/Educationa[.]apk hxxps://downloadapp[.]website/education-bangla[.]apk hxxp://downloadapp[.]website/education2025[.]apk hxxps://downloadapp[.]website/govt[.]apk hxxps://appsloads[.]top/govt[.]apk hxxps://appsloads[.]top/education2025[.]apk hxxp://appsloads[.]top/sikkahbord[.]apk hxxps://appsloads[.]top/educationapp[.]apk hxxp://appsloads[.]top/edu[.]apk | URL | Download URLs |
| hxxps://bit[.]ly/Sikkahbord hxxps://bit[.]ly/Education-2025 hxxps://bit[.]ly/Educ-govt hxxps://bit[.]ly/app-upobitti hxxps://bit[.]ly/D43SJ hxxp://sbs[.]short[.]gy/ hxxps://apped[.]short[.]gy/ | URL | URL shorteners |
| a808219e6f4b5f8fb42635e070174d43d5a9314c1b45dcc3434ee106582bbdf8 c75aa842bdd107cc6483b4a119cf4b008abc745dcd04f06e39e60579798d7581 881ec7f704a8aa63139040e27b8bbe55c326ef117935cf1dceac4f2012f5919f 0b7a72b4a7bd307636cf9d7c92798796e255f4fd2735c77294a782959a390fe2 b785fcc27aa5efee480a321c6bb8f935f684da6c514470c9c1ce9003b05ab45e 1051fadcae01d6100ad89eb4badc4b9e36726c4812766359e5df62a540f9c312 4c2c270dc07a49a4e38f826bc2ca276e15be10528e97cca3163ac9bfa211294b a6f94cc3720aac3beed82e94fc7822e9b861b6cecaa5b396bd8b79b6c5a402bc d856625e6a7bcd8d771605a6f88b934a17baf755f390234404963909c6653d24 432d22f2bc4a6b63f8e3b7a6563b1756629d1b8da8feb918ab4859045b1dce72 72f167b9ed0e40c0cb96b4dabf644dad4fd02a0d67a3cd492482c75de57695db 04feff4706190410a08ad9b35c76118ebefc01c987a0efd7bdf6162c4ec09299 20509a69e2dfe16f9d13f27b1f7c1b2f55e83317eb42301eb5b4f7953248605e | SHA256 | Malicious APK files |
| hxxps://update-app-sujon-default-rtdb[.]firebaseio[.]com hxxps://smsrecived-3d4ed-default-rtdb[.]firebaseio[.]com hxxps://educa-41b35-default-rtdb[.]firebaseio[.]com | URL | Attacker Server |
如有侵权请联系:admin#unsafe.sh