
FBI警告俄罗斯黑客利用旧Cisco漏洞攻击关键基础设施;MITRE更新硬件安全漏洞列表;NIST发布对抗深度伪造指南;CIS发布新安全基准;Tenable调查显示漏洞优先化趋势。 2025-8-22 13:0:0 Author: www.tenable.com(查看原文) 阅读量:13 收藏
Check out the FBI’s alert on Russia-backed hackers infiltrating critical infrastructure networks via an old Cisco bug. Plus, MITRE dropped a revamped list of the most important critical security flaws. Meanwhile, NIST rolled out a battle plan against face-morphing deepfakes. And get the latest on the CIS Benchmarks and on vulnerability prioritization strategies!
Here are five things you need to know for the week ending August 22.
1 - FBI: Russian hackers targeting industrial systems
Heads up, critical infrastructure orgs: Russia-backed hackers are gunning for industrial control systems (ICS) by breaching networks via a years-old Cisco bug.
For the past year, a Russian Federal Security Service unit has been hijacking network devices to surveil industrial networks. Its goal? To find a foothold in the operational technology (OT) that runs everything from power grids to manufacturing plants.
This intel comes from the Federal Bureau of Investigation (FBI), which this week said that the group, also known as Berserk Bear, Dragonfly and Static Tundra, is exploiting critical vulnerability CVE-2018-0171 in the Cisco Smart Install (SMI) software.
So far, the group has collected thousands of configuration files from hacked networking devices, while scanning critical infrastructure networks in search of ICS protocols and applications.
(Image created by Tenable using Google Gemini)
The group has been hacking networking devices for a decade. It targets devices that rely on older, unencrypted protocols.
For a deep dive into this threat, check out the blog “Russian state-sponsored espionage group Static Tundra compromises unpatched end-of-life network devices” from Cisco Talos, Cisco’s threat intelligence team.
It offers a detailed analysis of the threat, along with mitigation recommendations, including, of course, applying the patch for CVE-2018-0171 or disabling Smart Install.
In related news, Norway’s government officially blamed Russian hackers for the April hack of a dam’s water flow system and spilling about two million gallons of water into a river. Norwegian Police Security Chief Beate Gangås made the allegation during Norway’s annual national forum Arendalsuka. Russia has denied the charge.
For more information about securing OT systems in critical infrastructure environments, check out these Tenable resources:
- “How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform” (blog)
- “The Invisible Bridge: Recognizing The Risk Posed by Interconnected IT/OT/IoT Environments” (on-demand webinar)
- “How to Remediate Risk to Critical OT/IoT Systems without Disrupting Operations” (blog)
- “Blackbox to blueprint: a security leader’s guide to managing OT and IT risk” (ebook)
- “Identity Security Is the Missing Link To Combatting Advanced OT Threats” (blog)
- “Unlock advanced IoT visibility to better secure your OT environment” (on-demand webinar)
2 - MITRE updates list of top hardware security blunders
For the first time in almost five years, MITRE has revised its list of the main security weaknesses impacting hardware devices, giving security pros a refreshed roadmap to tackle today’s biggest hardware risks.
The "2025 CWE Most Important Hardware Weaknesses" (MIHW) list is the first to mesh comprehensive weakness data from the CVE program, security advisories, conferences and research papers with opinions from hardware security experts.
With the new list, MITRE aims to help organizations prevent hardware security issues through enhanced mitigation prioritization, design practices and decision-making throughout the hardware lifecycle.
“The 2025 CWE MIHW represents a refreshed and enhanced effort to identify and educate the cybersecurity community about critical hardware weaknesses,” reads a MITRE paper.
These are MITRE’s top hardware security weaknesses, with new ones in bold:
- CWE-226: Sensitive Information in Resource Not Removed Before Reuse
- CWE-1189: Improper Isolation of Shared Resources on System-on-a-Chip (SoC)
- CWE-1191: On-Chip Debug and Test Interface With Improper Access Control
- CWE-1234: Hardware Internal or Debug Modes Allow Override of Locks
- CWE-1247: Improper Protection Against Voltage and Clock Glitches
- CWE-1256: Improper Restriction of Software Interfaces to Hardware Features
- CWE-1260: Improper Handling of Overlap Between Protected Memory Ranges
- CWE-1262: Improper Access Control for Register Interface
- CWE-1300: Improper Protection of Physical Side Channels
- CWE-1421: Exposure of Sensitive Information in Shared Microarchitectural Structures during Transient Execution
- CWE-1423: Exposure of Sensitive Information caused by Shared Microarchitectural Predictor State that Influences Transient Execution
In a separate list labeled “Expert Insights: Weaknesses Beyond Data Trends,” MITRE highlights five additional weaknesses that experts believe also warrant special attention:
- CWE-1231: Improper Prevention of Lock Bit Modification
- CWE-1233: Security-Sensitive Hardware Controls with Missing Lock Bit Protection
- CWE-1244: Internal Asset Exposed to Unsafe Debug Access Level or State
- CWE-1272: Sensitive Information Uncleared Before Debug/Power State Transition
- CWE-1431: Driving Intermediate Cryptographic State/Results to Hardware Module Outputs
Here’s a table correlating the hardware weaknesses with MITRE’s hardware categories.
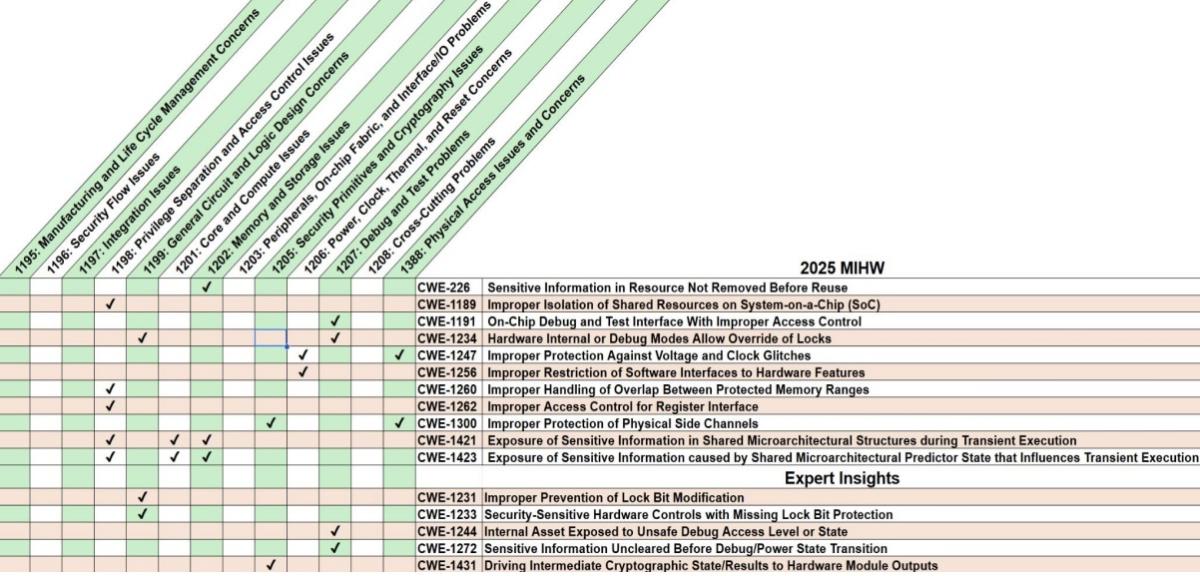
(Source: MITRE, August 2025)
The list can be useful for a variety of security stakeholders, including:
- Security architects and designers to prioritize key weaknesses
- Design teams to build review checklists
- Test engineers to focus testing efforts
- Security researchers to direct their investigative and mitigation efforts
- Electronic design automation tool vendors to enhance tool support for industry-prioritized weaknesses
- Educators to align course materials with major, real-world hardware vulnerabilities
To get more details, check out the “CWE Most Important Hardware Weaknesses” home page.
For more information about hardware security flaws:
- “Hardware Security Failure Scenarios” (NIST)
- “39 hardware vulnerabilities: A guide to the threats” (CSO)
- “Hardware Hacking? New Study Raises Alarm On 98 Cyber Risks” (Forbes)
- “New CISA advisories urge swift action on ICS flaws impacting energy, manufacturing, transportation systems” (Industrial Cyber)
3 - NIST: How to unmask face-morphing identity threats
Is your organization prepared to detect identity scams perpetrated via face morphing — a growing deepfake threat?
It should, according to the National Institute of Standards and Technology (NIST), which this week published guidelines to combat identity fraud that uses this image-manipulation technique.
Face morphing is the combination of two facial photographs — one of the legitimate owner of, say, a passport or an employee ID card, and the other of a fraudster.
Face-morphing software aims to produce a synthesized image that will resemble the fraudster enough to deceive face-recognition systems and humans tasked with verifying the person’s identity.

(Image created by Tenable using Google Gemini)
That way, the “morphed” image can be used in multiple passports, employee ID cards, drivers’ licenses and more.
“The main threat associated with morphs is that if the submitted photograph is put on an identity document such as a passport, then both individuals will be able to use that document,” reads NIST’s 26-page document “Face Analysis Technology Evaluation (FATE) MORPH.”
Sometimes a morphed image is generated from photos of more than two people.
NIST’s publication aims to offer practical guidance for organizations to adopt and use morph-detection methods in scenarios such as passport application reviews and border crossings.
“It’s important to know that morphing attacks are happening, and there are ways to mitigate them,” NIST official Mei Ngan said in a statement.
Modern morph-detection algorithms have improved significantly, according to NIST. The guidelines detail two primary methods of detection:
- Single-image morph attack detection (S-MAD), which analyzes a single suspicious photo
- Differential morph attack detection (D-MAD), which compares the questionable photo with a known genuine image of the individual
S-MAD can be highly accurate if the software has been trained on the specific morphing tool used to create the image. However, its effectiveness can decrease substantially when encountering images created with unfamiliar software. In contrast, D-MAD provides more consistent accuracy, with success rates ranging from 72% to 90%.
Meanwhile, human examiners that suspect a morph can perform several checks:
- Visual inspection: Look for inconsistencies or anomalies around the eyes, nose, and mouth, as well as in skin texture and color.
- Feature comparison: Compare the suspected morph with a trusted photo, looking for the absence or difference of features like scars, moles, or ear structures.
- Metadata analysis: Inspect the image file's metadata for clues, such as the software used to create or modify the image.
The NIST publication also recommends ways to configure detection software for different situations and offer procedures for investigating flagged photos. The ideal approach involves a combination of automated tools and human review.
A key preventative measure is to stop morphed photos from entering systems. “The most effective way is to not allow users the opportunity to submit a manipulated photo for an ID credential in the first place,” Ngan said.
For more information about detecting deepfakes:
- “Prevent Cyber Attacks with Deepfake Detection Technology – A Complete Guide” (Cyberdefense Magazine)
- “Why detecting dangerous AI is key to keeping trust alive in the deepfake era” (World Economic Forum)
- “A Framework for Detection in an Era of Rising Deepfakes” (Carnegie Mellon University)
- “Deepfake disruption: A cybersecurity-scale challenge and its far-reaching consequences” (Deloitte)
- “Deepfakes and LLMs: The Cybersecurity Frontier We Can't Ignore” (ISC2)
4 - Tenable webinar polls: How your peers prioritize vulnerabilities
During our recent webinar “Tenable Announces AI-Powered Breakthrough in Vulnerability Prioritization,” we polled attendees on their preferred vulnerability prioritization criteria. We also asked them which new Tenable Vulnerability Priority Rating (VPR) drivers they expect to use the most. Check out what they said.
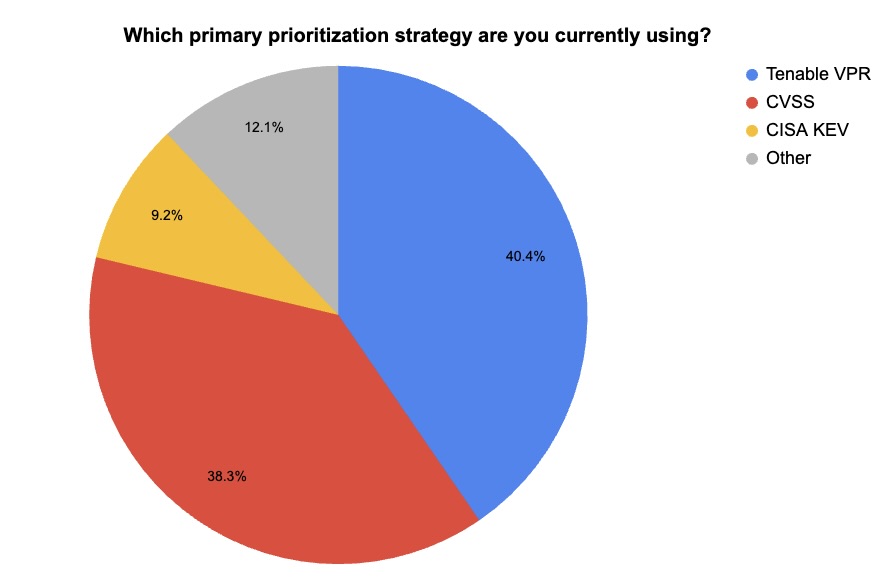
(141 webinar attendees polled by Tenable, August 2025)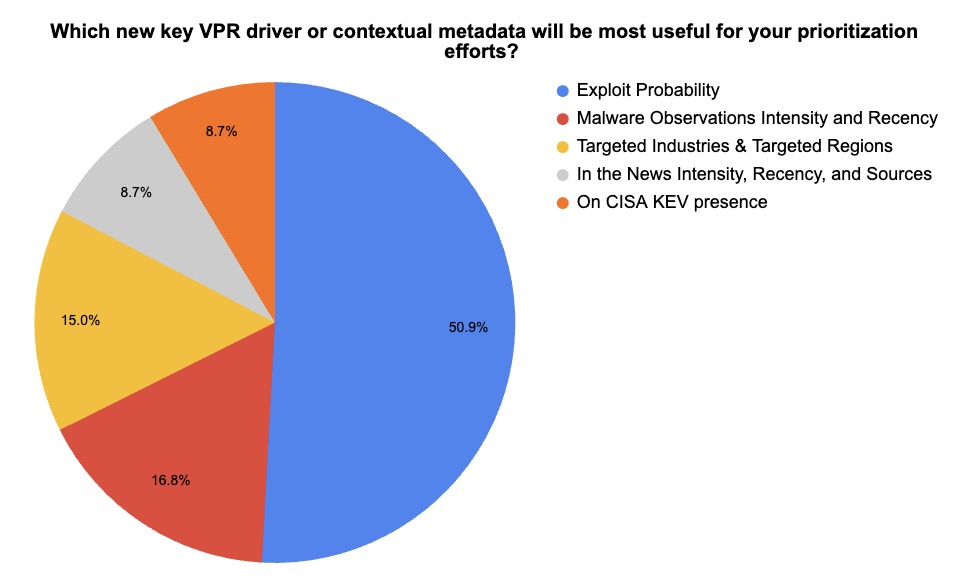
(101 webinar attendees polled by Tenable, August 2025)
Watch the on-demand webinar to learn how Tenable Vulnerability Management’s AI-powered, context-rich approach transforms risk scoring, enhances prioritization, improves efficiency and boosts clarity.
5 - Fresh CIS Benchmarks are here for Microsoft, Cisco, AWS products
Time for a configuration check-up. The Center for Internet Security (CIS) just dropped a batch of new and updated Benchmarks to help you harden key systems against attack.
Specifically, these secure-configuration recommendations were updated in July:
- CIS AWS End User Compute Services Benchmark v1.2.0
- CIS Cisco IOS XE 17.x Benchmark v2.2.1
- CIS Docker Benchmark v1.8.0
- CIS ExtremeNetworks SLX-OS-20.X.X Benchmark v1.0.1
- CIS Microsoft Windows Server 2019 Stand-alone Benchmark v3.0.0
- CIS Microsoft Windows Server 2019 STIG Benchmark v4.0.0

In addition, CIS released these brand new Benchmarks: CIS Cisco NX OS Switch RTR STIG Benchmark; CIS DigitalOcean Foundations Benchmark v1.0.0; and CIS DigitalOcean Services Benchmark v1.0.0.
Organizations can use the CIS Benchmarks’ secure-configuration guidelines to harden products against attacks. Currently, the guidelines include more than 100 Benchmarks for 25-plus vendor product families in categories including:
- cloud platforms
- databases
- desktop and server software
- mobile devices
- operating systems
To get more details, read the CIS blog “CIS Benchmarks August 2025 Update.”
For more information about the CIS Benchmarks list, check out its home page, as well as:
- “Getting to Know the CIS Benchmarks” (CIS)
- “Security Via Consensus: Developing the CIS Benchmarks” (Dark Reading)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)

Juan Perez
Senior Content Marketing Manager
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh