文章介绍了反向代理的作用与工作原理,列举了Traefik、Nginx Proxy Manager等常见工具,并探讨了其在SSL终止、负载均衡、访问管理等方面的优势,同时提供了实施建议与最佳实践,帮助读者优化网络架构与安全性。 2025-8-17 17:40:28 Author: www.blackmoreops.com(查看原文) 阅读量:11 收藏
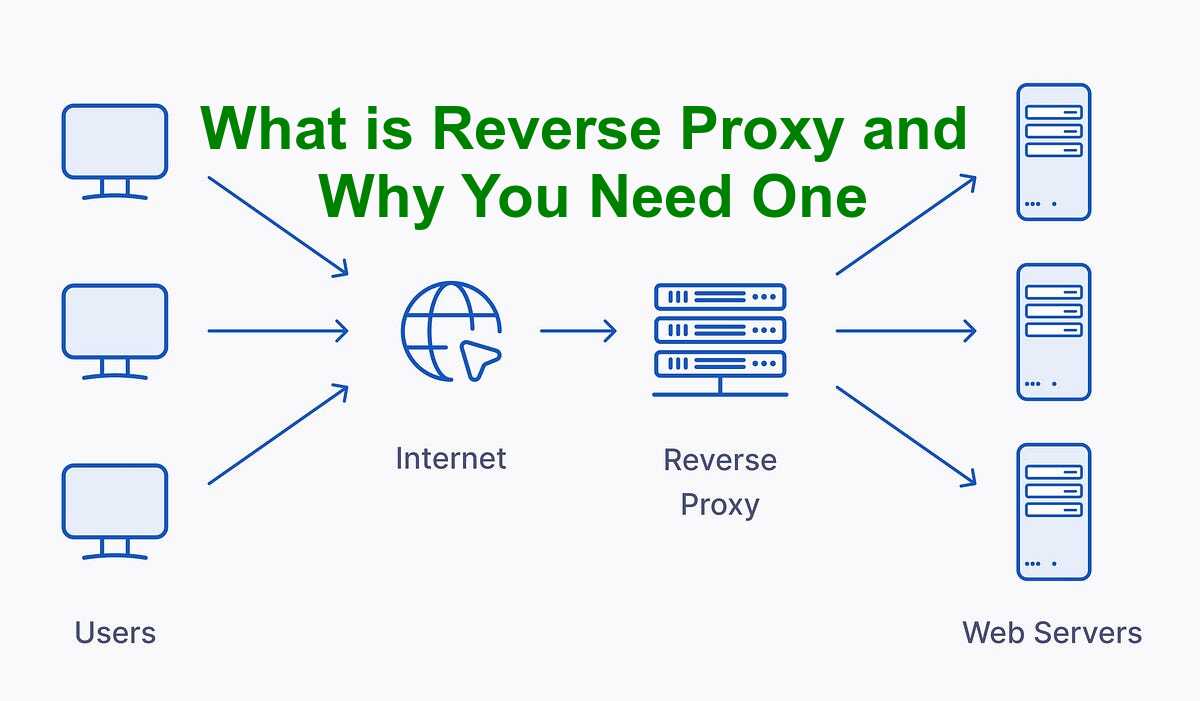
A reverse proxy acts as an intermediary between clients and backend servers, forwarding client requests to the appropriate backend services and returning responses back to clients. Unlike traditional forward proxies that represent clients, a reverse proxy represents servers, making it an essential component in modern web infrastructure and home lab environments.
Basic reverse proxy architecture demonstrating request flow from clients through the proxy to backend services
Think of a reverse proxy like that helpful friend who knows where everything is in your house. When visitors arrive asking for specific things, your friend directs them to the right room without the visitors needing to memorise your entire floor plan. In the same way, a reverse proxy receives incoming requests and forwards them to the right backend services based on rules you’ve set up.
How Reverse Proxy Works in Practice
When you implement a reverse proxy in your setup, here’s what actually happens behind the scenes:
How Requests Flow Through Your Reverse Proxy
- Someone visits your site: A user types
jellyfin.yourdomain.comin their browser - DNS does its thing: The domain points to your reverse proxy server’s IP address
- Proxy examines the request: Your reverse proxy looks at the request headers, especially the Host header
- Traffic gets routed: Based on your rules, the proxy sends the request to the right backend service
- Response comes back: The backend service responds through the proxy back to the user
Think of this like instead of having to go get a toy on the shelf yourself, you can ask a parent to get the toy for you. You just tell your parent ‘Car!’ and they know exactly where to find it and bring it to you.
Popular Reverse Proxy Options You Can Use
Traefik
Traefik offers dynamic configuration discovery, making it particularly suitable for containerised environments. It automatically detects new services and configures routing rules based on labels or annotations.
Nginx Proxy Manager
Nginx Proxy Manager provides a user-friendly web interface for managing Nginx configurations, making it accessible for users who prefer graphical interfaces over command-line configurations.
Cloudflare Tunnel
Cloudflare Tunnel creates secure connections between your servers and Cloudflare’s network without exposing your origin server’s IP address to the internet.
For more detailed configuration guides, check out our Docker container management tutorials which cover reverse proxy implementations in containerised environments.
Key Benefits of Reverse Proxy Implementation
SSL Termination and Security
A reverse proxy handles SSL certificates centrally, eliminating the need to configure SSL for each individual service. This approach provides several security advantages:
- Centralised Certificate Management: One location for all SSL certificates
- Enhanced Security: Backend services can operate over HTTP internally while presenting HTTPS externally
- Port Consolidation: Only ports 80 and 443 need external exposure
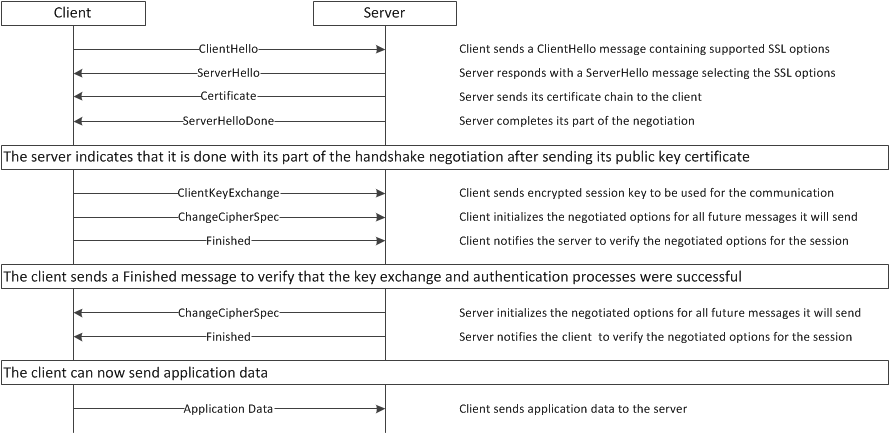
Image Courtesy: Troubleshooting SSL/TLS handshake failures https://my.f5.com/manage/s/article/K15292
Load Balancing and High Availability
Reverse proxies distribute incoming requests across multiple backend servers, ensuring optimal resource utilisation and service availability. This capability proves essential for high-traffic applications requiring redundancy.
Simplified Access Management
Instead of remembering complex port numbers like 192.168.1.100:8096 for Jellyfin or 192.168.1.100:8123 for Home Assistant, users access services through memorable subdomain names like jellyfin.yourdomain.com and homeassistant.yourdomain.com.
Internal vs External Reverse Proxy Configurations
Internal Network Setup
For home lab environments, implementing an internal reverse proxy eliminates the need for port numbers when accessing local services. Configure your DNS server (such as Pi-hole) to resolve service domains to your reverse proxy’s internal IP address.
jellyfin.yourdomain.com → 192.168.1.50 (reverse proxy) homeassistant.yourdomain.com → 192.168.1.50 (reverse proxy)
External Access Integration
Many users combine internal reverse proxies with external solutions like Cloudflare Tunnel. External requests flow through Cloudflare’s network, while internal requests route directly through the local reverse proxy, optimising performance and security.
For comprehensive network security strategies, explore our cybersecurity guides covering advanced proxy configurations and security hardening techniques.
Docker Integration and Container Orchestration
Modern reverse proxy solutions integrate seamlessly with Docker environments. Container labels define routing rules automatically, eliminating manual configuration for new services.
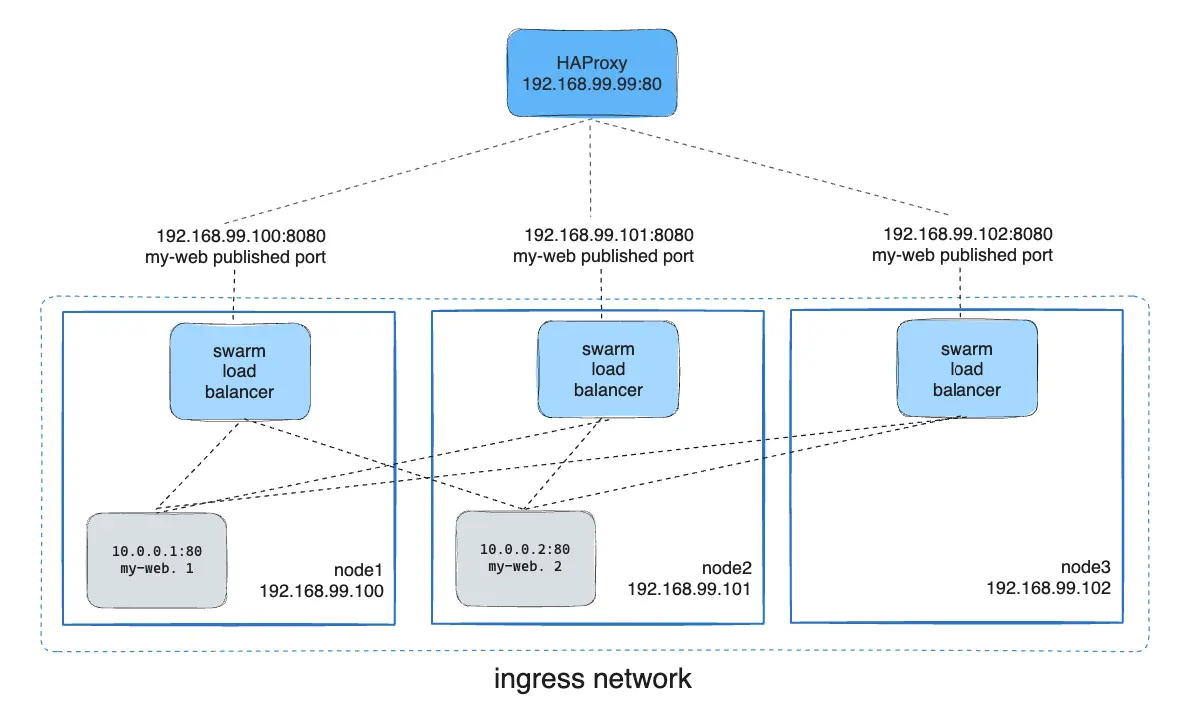
Example, you could configure HAProxy to balance requests to an nginx service published to port 8080. Reference: https://docs.docker.com/engine/swarm/ingress/
Network Architecture Considerations
When implementing reverse proxy in Docker environments, network configuration becomes crucial. Create dedicated networks for proxy communication while maintaining service isolation for security.
Advanced Features and Middleware
Authentication and Authorisation
Reverse proxies can implement authentication layers, adding SSO (Single Sign-On) capabilities across all backend services. This centralised approach simplifies user management and enhances security.
Rate Limiting and DDoS Protection
Implement rate limiting rules to prevent abuse and protect backend services from overwhelming traffic. Configure geographic restrictions and IP-based filtering for enhanced protection.
Monitoring and Analytics
Modern reverse proxy solutions provide comprehensive logging and monitoring capabilities. Integration with tools like Crowdsec and Fail2ban enables automated threat detection and response.
Implementation Best Practices
DNS Configuration Strategy
Implement split-horizon DNS to ensure internal requests bypass external routing. Configure your local DNS server to resolve service domains to internal IP addresses while maintaining external accessibility.
Security Hardening
- Firewall Configuration: Close unnecessary ports and restrict access to backend services
- Regular Updates: Maintain current versions of proxy software and dependencies
- Access Logging: Enable comprehensive logging for security monitoring and troubleshooting
For additional security considerations, refer to OWASP’s Application Security Guidelines and Cloudflare’s Security Documentation.
Performance Optimisation
Configure caching strategies to reduce backend load and improve response times. Implement connection pooling and keepalive settings for optimal resource utilisation.
Troubleshooting Common Issues
IPv6 Considerations
Users often encounter SSL errors when IPv6 addresses bypass internal proxy configurations. Ensure both IPv4 and IPv6 addresses point to your reverse proxy for consistent behaviour.
Certificate Management
Automate certificate renewal using Let’s Encrypt and ACME challenges. Wildcard certificates simplify management for multiple subdomains under a single domain.
Backend Health Monitoring
Implement health checks to detect backend service failures and automatically route traffic to healthy instances.
Conclusion
A reverse proxy serves as a powerful gateway that simplifies service access, enhances security, and provides centralised management capabilities. Whether you’re managing a home lab with services like Jellyfin and Home Assistant or operating enterprise infrastructure, implementing a reverse proxy offers significant benefits in terms of security, usability, and maintenance efficiency.
The choice between solutions like Traefik, Nginx Proxy Manager, or cloud-based options like Cloudflare Tunnel depends on your specific requirements, technical expertise, and infrastructure complexity. Start with simpler solutions like Nginx Proxy Manager for basic needs, then consider migrating to more advanced options like Traefik as your requirements grow.
Understanding reverse proxy fundamentals enables you to make informed decisions about your infrastructure architecture while providing users with seamless, secure access to your services without the complexity of remembering port numbers and IP addresses.
如有侵权请联系:admin#unsafe.sh