read file error: read notes: is a directory 2025-8-11 10:56:50 Author: payatu.com(查看原文) 阅读量:14 收藏
Introduction
The rollout of WPA3 was hailed as the long-awaited fix for the well-known weaknesses of WPA2, a modern standard designed to secure wireless communications in an increasingly connected world. With stronger encryption, resistance to offline attacks, and forward secrecy, WPA3 promises a more robust defence against Wi-Fi intrusion.
But here’s the catch: no protocol is foolproof, and WPA3 is no exception.
Despite its improvements, WPA3 still faces implementation flaws, backward compatibility issues, and real-world deployment challenges that attackers can exploit. In fact, some of the most effective attacks today don’t break the protocol itself but bypass or undermine it through other means, from rogue access points to misconfigured devices and insecure fallback modes.
This article breaks down why WPA3, while a step forward, doesn’t spell the end of Wi-Fi hacking, and what organizations and users must consider to truly secure their wireless networks.
In our previous posts, we explored how Wi-Fi hacking often targets weaknesses around the protocol itself. Take a look at Part 1 and Part 2 if you have not referred already. In this blog, we’ll see how even WPA3’s advanced features can be undermined in practice from Dragonblood flaws to downgrade attacks, rogue access points, and other vulnerabilities discovered so far.
| Feature | WPA2 | WPA3 |
| Encryption | Uses AES-CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol), which is secure but aging. | Upgrades to AES-GCMP (Galois/Counter Mode Protocol), offering faster, more secure encryption with improved integrity protection. |
| Authentication | Relies on Pre-Shared Key (PSK), where all users share the same password, making it vulnerable to key-sharing and dictionary attacks | Introduces Simultaneous Authentication of Equals (SAE), a more secure handshake resistant to offline attacks, even with weak passwords. |
| Offline Attack Resistance | Low resistance attackers can capture handshake packets and perform offline brute-force attacks to guess passwords | SAE protects against offline brute-force attacks by requiring real-time interaction for each guess |
| Forward Secrecy | No forward secrecy, meaning if a key is compromised, past session data can be decrypted | Provides forward secrecy, ensuring that even if the current key is exposed, previous sessions remain secure |
| Open Wi-Fi Security | Offers no encryption on open networks (e.g., cafes, airports), leaving data vulnerable | Supports Opportunistic Wireless Encryption (OWE), encrypting traffic even on open networks, no password needed, but data stays private. |
| Management Frame Protection | Optional, making it easier for attackers to spoof or manipulate Wi-Fi control signals (like de-authentication). | Mandatory, protecting management frames from tampering and improving overall connection reliability and security |
While WPA3 is a significant step forward in wireless security, its real-world effectiveness depends on more than just adopting the protocol. In practice, several operational, technical, and compatibility challenges continue to undermine its full potential. Below are the key security concerns that organisations must navigate when deploying WPA3:
Vulnerability to Implementation Flaws:
WPA3 is a strong standard on paper, but its security depends entirely on how well it’s implemented in firmware and software. Device manufacturers often rush to support new standards, sometimes leading to programming errors, incomplete implementations, or non-compliance with best practices.
Such flaws open the door for side-channel attacks (like those in the Dragonblood family), unintended fallback behaviours, and other exploitable bugs. As seen with earlier versions of WPA2, even a small coding mistake in a widely used chipset can impact millions of devices. The complexity of protocols like WPA3 means they must be implemented with extreme care, something not all vendors prioritise.
Transition Mode (Mixed WPA2/WPA3) Weakness:
To ease the shift to WPA3, many networks enable a transition or mixed mode, where both WPA2 and WPA3 connections are accepted. While this improves compatibility, it creates a significant security loophole.
Attackers can force a WPA3-capable client to fall back to WPA2, which is more vulnerable to dictionary attacks and handshake interception by spoofing access points or manipulating connection attempts. Essentially, the presence of legacy support nullifies the primary benefits of WPA3, unless administrators take strict steps to lock down downgrade paths.
Inconsistent Device Support:
A major roadblock to full WPA3 adoption is that not all devices support it. Older smartphones, tablets, network printers, and especially IoT devices often lack WPA3 compatibility. Some newer devices may technically support WPA3 but only partially implement it or have it disabled by default.
This forces organisations to continue supporting older protocols, like WPA2-PSK, across their networks to maintain device connectivity. Unfortunately, this also means keeping legacy vulnerabilities alive, increasing the attack surface and complicating network segmentation.
Cost and Operational Complexity:
Upgrading to WPA3 isn’t just a software toggle; it often requires significant infrastructure investment. Older wireless access points may not support WPA3 and need to be replaced. Likewise, endpoint devices (like employee laptops or mobile devices) must be updated or replaced to take advantage of the new protocol.
Beyond the hardware, IT teams must manage network configuration changes, security policy updates, and user training, especially in large organisations. All of this comes with logistical and financial costs, which can delay or deter widespread WPA3 deployment, especially in budget-conscious environments like schools or small businesses.
Human Error in Configuration:
No matter how secure a protocol is, human error remains a leading cause of security breaches. Misconfigured access points, improperly set encryption modes, or failure to disable outdated options can easily weaken WPA3’s protections.
For example, using WPA3-Personal but allowing WPA2 fallback, or not enforcing strong passwords, can give users a false sense of security. Even skilled IT staff can overlook critical settings if vendor interfaces are unclear or if defaults are insecure. As always, misconfiguration is the silent threat behind many technical vulnerabilities.
Patch Management Gaps:
Keeping device firmware and software up to date is critical to maintaining WPA3 security, especially as new vulnerabilities are discovered and patched over time. However, many organisations fall behind in patch management due to:
- Lack of centralised update systems
- Outdated hardware no longer supported by vendors
- Limited IT resources to track and apply patches across all devices
Unpatched devices are low-hanging fruit for attackers, particularly in environments with a mix of new and legacy equipment. Even if a vulnerability is known and fixed, failure to apply the update keeps the door wide open.

Dragonblood Family of Exploits:
The Dragonblood vulnerabilities, disclosed by Mathy Vanhoef and Eyal Ronen in 2019, target WPA3 networks, specifically the SAE (Simultaneous Authentication of Equals) handshake. SAE is used in WPA3-Personal mode and is based on Dragonfly Key Exchange.
Despite SAE’s goal to prevent offline password cracking, Dragonblood exploits side-channel leaks and downgrade possibilities to undermine its protection.
Types of Attacks in the Dragonblood Family
CVE-2019-13377 – Dragonblood Attack (Timing Side-Channel)
The first variant of the Dragonblood attack targets how devices process passwords during the SAE handshake. When a device authenticates a user, it evaluates the password in a specific sequence. By precisely measuring how long the device takes to respond to authentication attempts, an attacker can gain insight into which password guesses are closer to the correct one. This is called a timing-based side-channel attack.

Fig: Timing Attack against WPA3
The figure illustrates how timing differences in the SAE handshake reveal information about password validity. The left-shifted blue curve shows responses for password guesses with many correct elements, while the right-shifted orange curve represents guesses with few or no correct elements demonstrating how attackers use response time to distinguish valid from invalid passwords in a timing-based side-channel attack.
Impact: Attackers can perform offline dictionary attacks by measuring the response time from the target AP during SAE processing.
CVE-2019-13456 – Cache-Based Side-Channel Attack
A second vulnerability lies in how the CPU handles password data during the authentication process. Known as a cache-based side-channel attack, this exploit is particularly dangerous in shared or virtualised environments, such as cloud services or multi-user systems. When the CPU processes a password, it accesses certain memory areas (cache). Malicious actors can monitor these memory access patterns to extract sensitive information, like cryptographic keys or password fragments.

Fig: Timing Attack Against an EAP-pwd Client
The graph shows how password processing affects CPU response times across multiple iterations, with each peak representing a distinct number of memory accesses. Attackers can analyse these timing differences and memory access patterns to infer sensitive information, demonstrating how cache-based side-channel attacks can leak password fragments or keys, especially in shared or virtualised environments.
Impact: On shared systems (like in virtualised environments), attackers can extract keys based on cache behaviour.
CVE-2019-9494 & CVE-2019-9495 – WPA2/WPA3 Transition Mode Downgrade
Perhaps the most concerning Dragonblood technique is the downgrade attack. WPA3 networks often support mixed-mode operation, allowing devices that don’t support WPA3 to fall back to WPA2 for compatibility. Attackers can exploit this by interfering with the handshake process and forcing a device to connect using the older, less secure WPA2-PSK method.
Impact: Enables standard WPA2 attacks even when WPA3 is enabled.

Fig: Evil Twin De-Authentication Attack Exploiting WPA3-Transition Mode Vulnerability
Rogue Access Points and Evil Twin Scenarios:
One of the oldest and most persistent Wi-Fi attacks is the Evil Twin, a type of rogue access point set up to mimic a legitimate Wi-Fi network. Even in WPA3 environments, this technique is still effective when combined with downgrade tactics.
In these attacks, the adversary sets up a fake Wi-Fi access point that broadcasts the same SSID as a trusted WPA3 network but only offers WPA2 encryption. If a user’s device is set to connect automatically to known networks and supports fallback to WPA2 (as many still do), it may unknowingly connect to the rogue AP.
Once connected over WPA2, the attacker can capture the 4-way handshake, allowing them to perform offline dictionary attacks to recover the Wi-Fi password. Even if the network is “technically” WPA3-enabled, the existence of WPA2 compatibility opens the door for this deception.
Group Downgrade Weaknesses:
WPA3 uses Elliptic Curve cryptography in its Simultaneous Authentication of Equals (SAE) handshake, which relies on cryptographic groups (sets of parameters used to perform key exchange). However, not all groups are equally secure.
If a device or access point supports multiple cryptographic groups some strong, some weak an attacker can manipulate the negotiation process during handshake setup. This is known as a group downgrade attack. The client may end up using a weaker group, significantly reducing the strength of the handshake’s encryption.
This attack doesn’t require breaking the handshake itself; instead, it tricks devices into lowering their cryptographic standards, making it easier to crack the session or perform further exploits. Unless group negotiation is tightly restricted by both client and server, this can become a silent yet dangerous vulnerability
Other Vulnerabilities to be Highlighted:
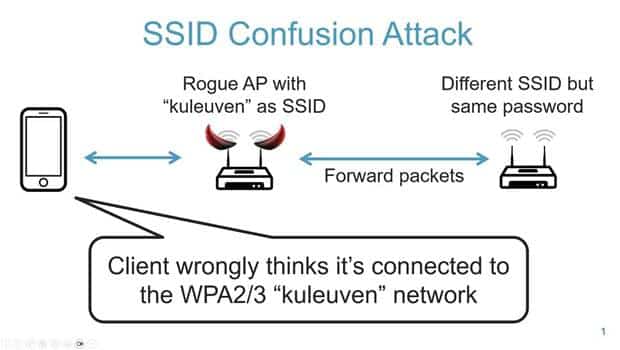
CVE‑2023‑52424 – “SSID Confusion Attack”
This vulnerability targets a fundamental flaw in the IEEE 802.11 standard, specifically how WPA3 handles SSIDs during the SAE handshake. The root issue lies in the fact that SSIDs are not cryptographically bound to the handshake or derived keys.
An attacker can exploit this by setting up a rogue access point that broadcasts the same SSID as a legitimate WPA3 network, tricking nearby clients into connecting even when those clients expect secure WPA3 connections. Because the SSID isn’t integrated into the Pairwise Master Key (PMK), the victim device cannot verify that it’s communicating with the real network.
Unless SSID protection is explicitly enforced or supplemented with additional validation mechanisms, WPA3-using devices may fall prey to these types of impersonation attacks, compromising the confidentiality of the session.

Fig: SSID Confusion Attack in WPA3 Networks
CVE‑2025‑27558 – FragAttacks in Mesh Networks (WPA3, WPA2, WEP)
Discovered in early 2025, this critical vulnerability affects mesh Wi-Fi networks, including those using WPA3. It builds on earlier fragmentation attack techniques (FragAttacks) and stems from an incorrect fix for CVE‑2020‑24588.
The vulnerability allows attackers to inject forged data frames into wireless traffic in mesh environments. Specifically, devices that improperly process non-SSP A-MSDU frames can be tricked into accepting malicious packets, even when encryption is enabled. As a result, attackers could execute remote code, exfiltrate data, or manipulate traffic all within networks presumed to be protected by WPA3.
This is a serious threat in enterprise and IoT-heavy environments, where mesh networks are commonly deployed for wide-area coverage.
Off-Path TCP Hijacking via Frame‑Size Side‑Channel (2024)
Though not a flaw in WPA3 itself, this advanced side-channel attack demonstrates how even encrypted Wi-Fi traffic can be exploited. Researchers have shown that by sniffing encrypted traffic and analysing packet sizes, attackers can infer the behaviour of upper-layer protocols like TCP, SSH, or HTTP.
By observing patterns in the length and timing of encrypted frames, an attacker positioned nearby without needing to decrypt any packets can hijack TCP sessions or inject malicious responses. This technique, known as off-path TCP injection, highlights the fact that traffic analysis alone can reveal more than expected, even on WPA3-protected networks.
Such attacks reinforce the importance of end-to-end encryption (e.g., TLS 1.3), traffic obfuscation, and packet size randomisation in environments where passive surveillance is a realistic threat.
Best Practices for WPA3 Deployment
To truly benefit from WPA3’s improved security, organisations must go beyond the protocol and adopt layered defences, secure configurations, and best operational practices that address real-world risks.
Implement Zero-Trust Network Segmentation:
Relying solely on encryption at the Wi-Fi layer is a mistake. If a device on your network is compromised via stolen credentials, insecure fallback, or side-channel attacks, the attacker could move laterally through the network.
To prevent this, adopt Zero-Trust Network Architecture (ZTNA) principles, which assume no device or user should be trusted by default, even inside the network perimeter. Segment your network into isolated zones, such as separating IoT devices, guest clients, and sensitive enterprise resources, using VLANs, firewalls, or SDN-based micro segmentation. Each segment should have its own access controls and monitoring.
Even if a single device is compromised, the attacker’s access is contained, limiting the scope of any breach
Strengthen Endpoint Security:
Even with flawless WPA3 implementation, a compromised endpoint can completely bypass security. Malware, outdated operating systems, or stolen credentials render network-level protections meaningless.
To mitigate this:
- Ensure all devices have up-to-date antivirus and EDR (Endpoint Detection and Response) solutions.
- Enforce full-disk encryption and multi-factor authentication (MFA) for network access.
- Implement mobile device management (MDM) for monitoring and enforcing security policies on BYOD and mobile devices.
- Use network access control (NAC) to restrict device access based on posture checks (e.g., patch level, OS version, antivirus status).
A secure network begins with secure devices.
Deploy Monitoring & Intrusion Detection Tools:
Passive network security is insufficient. Organisations need real-time visibility into wireless activity to catch attacks before they cause damage.
Key strategies include:
- Use Wireless Intrusion Detection/Prevention Systems (WIDS/WIPS) to detect rogue access points, evil twin attacks, and unauthorised associations.
- Monitor for downgrade attempts, such as devices switching from WPA3 to WPA2 unexpectedly.
- Collect and analyse authentication logs and connection attempts using SIEM tools.
- Set alerts for abnormal behaviours, such as a single user trying to authenticate with multiple passwords in rapid succession.
This proactive monitoring approach helps detect issues before they escalate into full-blown breaches.
Conduct Ongoing User Training:
Humans are often the weakest link in any security chain. Phishing attacks, public Wi-Fi use, and insecure behaviours can all lead to credential theft or malware infections, even on otherwise secure networks.
Mitigate human risk through:
- Regular security awareness training on topics like safe Wi-Fi usage, identifying fake access points, and resisting phishing attempts.
- Clear guidance against connecting to open or suspicious Wi-Fi networks, especially while handling sensitive data.
- Empowering users to report unusual network behaviour or connection issues.
Educated users act as an early warning system and are less likely to fall victim to social engineering.
Align with Compliance & Security Policy Requirements:
Lastly, adopting WPA3 isn’t just a technical decision; it must align with broader regulatory and organisational security policies.
To ensure compliance:
- Map your network security strategy to relevant frameworks such as NIST, ISO 27001, GDPR, HIPAA, or PCI-DSS depending on your industry.
- Maintain documentation showing protocol configurations, patch management, monitoring procedures, and training programs.
- Conduct periodic audits and risk assessments to verify that WPA3 and supporting controls meet both internal policies and external compliance mandates.
Security is not just a technical goal, it’s also a governance and accountability process.

Conclusion
WPA3 represents a meaningful advancement in wireless security, addressing many of WPA2’s long-standing flaws with stronger encryption, better authentication, and protections against offline attacks. But the reality is clear: protocol improvements alone won’t stop Wi-Fi hacking.
From implementation flaws and downgrade attacks to rogue access points and endpoint compromise, attackers continue to find and exploit the soft edges around the protocol. Worse, transitional deployments and mixed-mode compatibility often undo the very benefits WPA3 was designed to deliver.
Securing a wireless network in 2025 and beyond requires more than turning on WPA3. It demands a layered defence strategy: strict configuration, zero-trust segmentation, endpoint hardening, real-time monitoring, regular patching, and user training. Without these, even a WPA3-enabled network can still be breached through the same old tricks.
In short, WPA3 is the current and future of Wi-Fi security, but it’s not the finish line. Treat it as a foundation, not a firewall.
References
- https://wpa3.mathyvanhoef.com
- https://www.bleepingcomputer.com/news/security/wpa3-wi-fi-standard-affected-by-new-dragonblood-vulnerabilities/
- https://www.redlegg.com/blog/wpa3-evil-twin-attack
- https://cyberinsider.com/breaking-wpa3-security-with-downgrade-attacks-and-social-engineering/
- https://arxiv.org/pdf/2412.15381.pdf
- https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lan-wlan/212576-configure-802-11w-management-frame-prote.html
- https://wlan1nde.wordpress.com/2014/10/21/protected-management-frames-802-11w/
- Dragonblood: Attacks on WPA3s Dragonfly Handshake | jabbaw0nky
如有侵权请联系:admin#unsafe.sh