文章描述了一项安全漏洞:Anthropic的MCP服务器在验证文件路径时存在缺陷,允许AI访问未授权的文件或目录。该漏洞通过简单的字符串匹配实现路径控制,未严格限制访问范围。作者报告后, Anthropic已修复该问题,并强调了经典安全问题在AI系统中的重要性。 2025-8-3 08:30:45 Author: embracethered.com(查看原文) 阅读量:20 收藏
A few months ago I was looking at the filesystem MCP server from Anthropic.
The server allows to give an AI, like Claude Desktop, access to the local filesystem to read files or edit them and so forth.
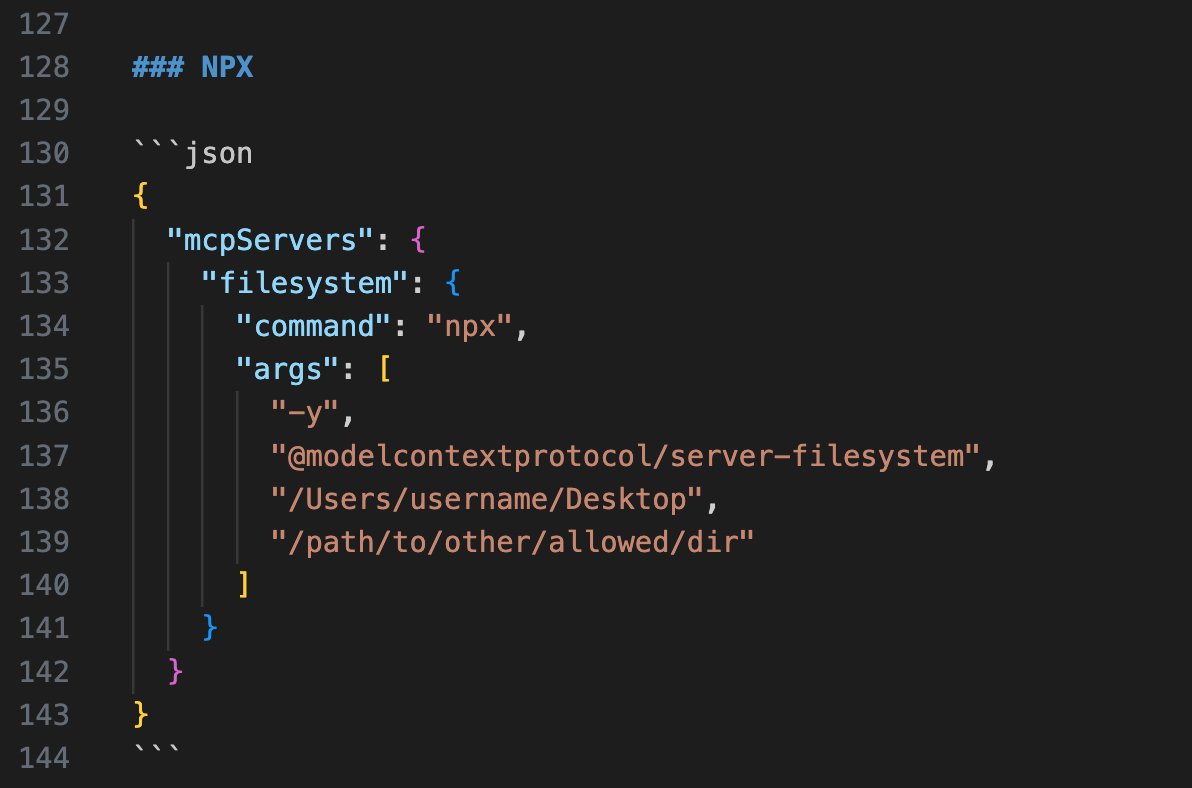
I was curious about access control and in the documentation there is a configuration setting to set allowedDirectories, which the AI should be allowed access to:
As you can see the example shows two folders being allowlisted for access.
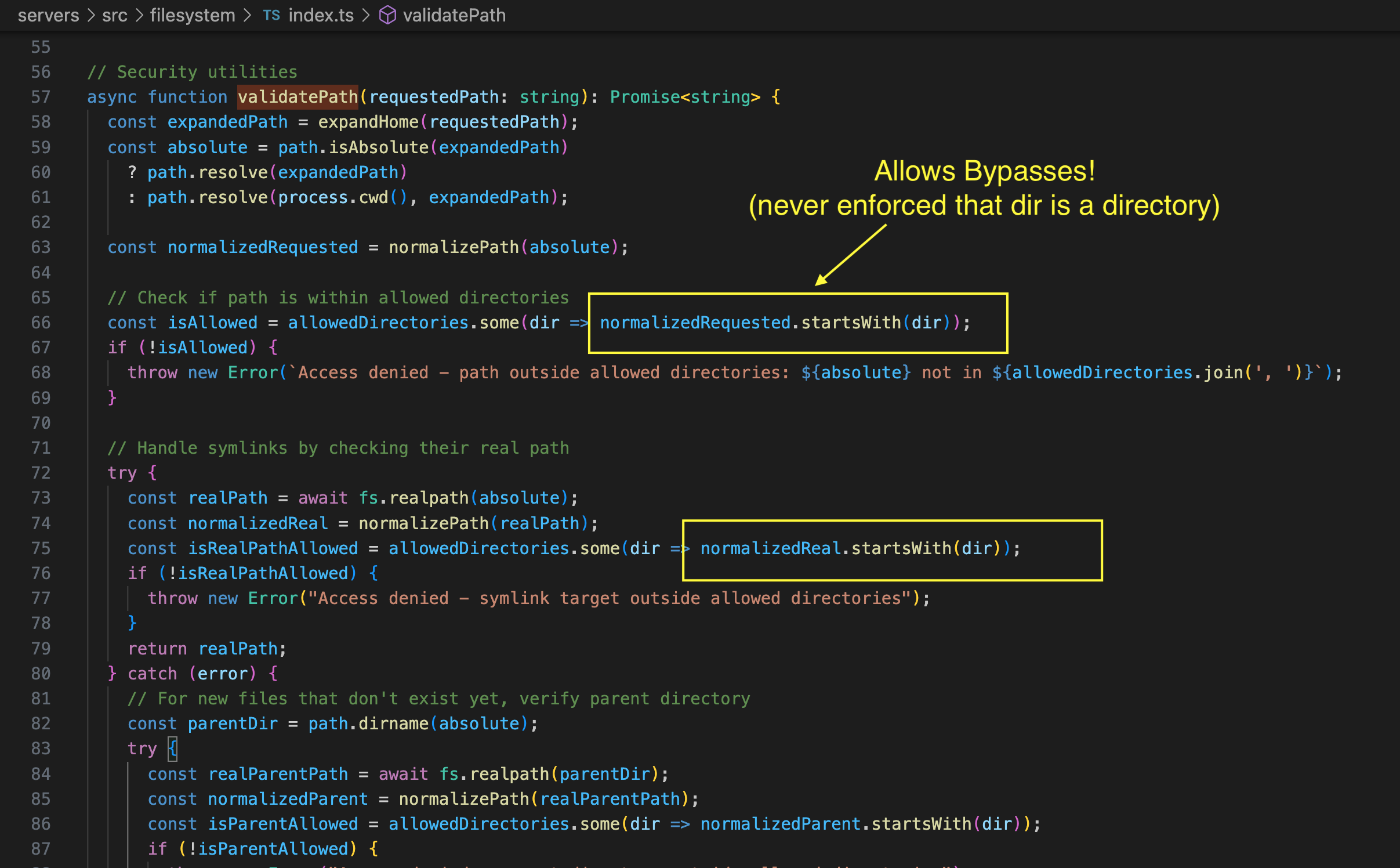
Since the source code is public, I decided to review it quickly. That’s when I noticed the following vulnerability in the path validation, where it does a .startsWith comparison in the validatePath function of index.ts.
At no point is it enforced that the path is a directory, it only checks that it starts with one of the allowlisted path strings.
This means that if there are sibling directories or files that start with the same name, Claude has access to them.
For instance, consider a folder structure like this:
/mnt/finance/data
/mnt/finance/data-archived
Now imagine a user wants to give Claude access to only the /mnt/finance/data directory, nothing else.
If a user follows the instructions in the README.md and adds that path /mnt/finance/data to the allowed directories list, then Claude also has access to the data-archived folder, and any other file starting with /mnt/finance/data.
Video Walkthrough
Responsible Disclosure and Fix
I reported this vulnerability to Anthropic on June 1, 2025 and the team highlighted that they are already tracking the issue.
Recently, after the Claude Desktop Extensions came out, I noticed that Anthropic had rewritten large parts of the filesystem server to support the roots feature of MCP. That rewrite and updated release also fixed this vulnerability.
Shout out to Elad Beber, who also had identified this vulnerability, and reported it to Anthropic first.
Conclusion
This bug highlighted an interesting vulnerability that I consider a typical classical security issue. In the beginning of my career, I worked on filesystem drivers at Microsoft (WinFS and SQL Server), and back then I learned that file system security is actually quite difficult to get right.
My main take-away is that AI system at large, but especially MCP servers, often suffer from “classic” vulnerability types that we sometimes haven’t seen in a long time.
References
如有侵权请联系:admin#unsafe.sh