
Check out fresh insights on AI data security from IBM’s “Cost of a Data Breach Report 2025.” Plus, O 2025-8-1 13:0:0 Author: www.tenable.com(查看原文) 阅读量:24 收藏
Check out fresh insights on AI data security from IBM’s “Cost of a Data Breach Report 2025.” Plus, OWASP issues guide on securing Agentic AI apps. In addition, find out how to protect your org against the Scattered Spider cyber crime group. And get the latest on zero-trust microsegmentation; containing and evicting network intruders; and Tenable’s Black Hat plans!
Here are six things you need to know for the week ending August 1.
1 - IBM data breach report: AI security lags AI adoption
In the artificial intelligence gold rush, a majority of organizations are rolling out AI systems and tools without having appropriate AI security and policies – and it’s costing them a pretty penny.
That’s a key finding from IBM’s “Cost of a Data Breach Report 2025,” which was released this week.
“This year's results show that organizations are bypassing security and governance for AI in favor of do-it-now AI adoption. Ungoverned systems are more likely to be breached—and more costly when they are,” reads an IBM statement.
Specifically, the report found that:
- A whopping 63% of surveyed organizations lack AI governance policies.
- 13% of organizations suffered an AI-related security incident to their models or applications that resulted in a breach. Among these organizations, 97% lacked proper AI access controls.
- 60% of AI-related security incidents led to compromised data and 31% led to operational disruption.
- Attackers weaponized AI in 16% of all data breaches.
The report also sheds light on the problem of shadow AI – the unapproved use of AI by employees. Specifically, shadow AI caused a breach at 20% of organizations. And companies with a high incidence of shadow AI experienced higher data breach costs and larger amounts of compromised personal information and intellectual property.
In short: Cyber attackers are starting to exploit many organizations’ lack of basic AI access controls and AI governance, which leaves AI system data and AI models vulnerable to breaches.
Impacts of security incidents on authorized AI
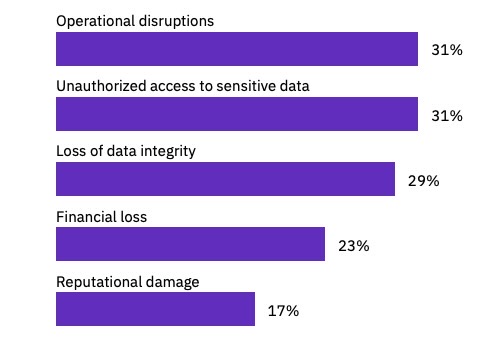
(From organizations that reported a security incident involving an AI model or application; more than one response permitted. Source: IBM’s “Cost of a Data Breach Report 2025,” July 2025)
Beyond AI, the report found that the global average cost of a data breach dropped 9% to $4.4 million, compared with 2024. IBM attributes this decrease – the first in five years – to faster identification and containment of breaches.
The global average mean time to identify and contain a breach, as well as to restore impacted services, fell to 241 days – a drop of 17 days compared with last year. Unfortunately, this downward trend didn’t extend to the U.S., where the average cost of a data breach reached a record $10.2 million.
The report, now in its 20th year, is based on the study of data breaches that impacted 600 organizations between March 2024 and February 2025. Almost 3,500 security and C-level executives with first-hand knowledge of these breaches were interviewed.
To get more details, check out:
- The report’s announcement
- The report’s home page
- The companion IBM blog “2025 Cost of a Data Breach Report: Navigating the AI rush without sidelining security”
For more information about AI data security, check out these Tenable resources:
- “Harden Your Cloud Security Posture by Protecting Your Cloud Data and AI Resources” (blog)
- “Tenable Cloud AI Risk Report 2025” (report)
- “Who's Afraid of AI Risk in Cloud Environments?” (blog)
- “Tenable Cloud AI Risk Report 2025: Helping You Build More Secure AI Models in the Cloud” (on-demand webinar)
- “Securing the AI Attack Surface: Separating the Unknown from the Well Understood” (blog)
2 - OWASP: How to safeguard agentic AI apps
Agentic AI apps are all the rage because they’re able to act autonomously without human intervention. But they’re also a major security challenge. If an AI app can act on its own, how do you stop it from going rogue or being hijacked?
If you’re building or deploying AI apps that can make their own decisions, check out a new publication from OWASP titled “Securing Agentic Applications Guide.”
OWASP, which published the guide this week, describes its aim as providing “practical and actionable guidance for designing, developing, and deploying secure agentic applications powered by large language models (LLMs).”

Aimed primarily at software developers, AI/ML engineers, security architects and security engineers, the guide’s agentic AI topics include:
- Technical security controls and best practices
- Secure architectural patterns
- Common threat mitigation strategies
- Guidance across the development lifecycle (design, build, deploy, operate).
- Security considerations for components such as LLMs, orchestration, memory, tools and operational environments
The guide also includes examples of how to apply security principles in different agentic architectures.
For more information about agentic AI security:
- “Frequently Asked Questions About Model Context Protocol (MCP) and Integrating with AI for Agentic Applications” (Tenable)
- “Cybersecurity in 2025: Agentic AI to change enterprise security and business operations in year ahead” (SC World)
- “How AI agents could revolutionize the SOC — with human help” (Cybersecurity Dive)
- “Three Essentials for Agentic AI Security” (MIT Sloan Management Review)
- “Beyond ChatGPT: The rise of agentic AI and its implications for security” (CSO)
3 - Alert: Scattered Spider spins new web of attack methods
Maintain offline data backups stored separately from their source production systems. Adopt and enforce phishing-resistant multi-factor authentication. Implement application controls.
Those are some of the concrete steps that cybersecurity teams should take immediately to prevent attacks from the cyber criminal group Scattered Spider – masters of disguise that impersonate your IT help desk to trick employees and gain network access.
The alert comes from law enforcement and cybersecurity agencies in Australia, Canada, the U.K. and the U.S. which have updated a joint cybersecurity advisory first issued in 2023.
The updated advisory, published this week, adds new information about Scattered Spider’s tactics, techniques and procedures; social engineering methods; and malware and ransomware variants.

(Image generated by Tenable using Google Gemini)
Scattered Spider, also known as UNC3944, Scatter Swine, Oktapus, Octo Tempest, Storm-0875, and Muddled Libra, employs a variety of social engineering techniques to deceive employees and gain initial access to corporate networks.
The group utilizes phishing, smishing (SMS phishing), and vishing (voice phishing) to impersonate IT and help desk personnel, tricking victims into divulging credentials or installing malicious remote access tools. Scattered Spider’s tactics have also included SIM swapping and multi-factor authentication (MFA) fatigue.
Once inside a network, Scattered Spider leverages legitimate remote access software and custom malware to establish persistence, escalate privileges, and exfiltrate sensitive data.
The advisory highlights a concerning evolution in the group's methods, noting a shift towards more targeted spearphishing campaigns and the ability to steal vast quantities of data from cloud storage platforms such as Snowflake and Amazon S3.
Scattered Spider has also recently begun deploying ransomware, including a strain known as "DragonForce," to encrypt their victims' systems and demand hefty ransoms. This move from data theft to active extortion marks a new and more destructive phase in the group's operations.
Additional mitigation recommendations include:
- Updating and patching all operating systems, software and firmware on a timely basis, especially internet-facing systems with known exploited vulnerabilities
- Segmenting your network to limit lateral movement
- Training employees to recognize and report social engineering attempts,
- Securing remote access tools via methods including:
- Auditing them and reviewing their logs to detect anomalous use
- Adopting security tools that can detect remote access software loaded only in memory
- Blocking inbound and outbound connections on common remote access software ports and protocols
- Strictly limiting the use of Remote Desktop Protocol (RDP) and other remote desktop services
To get more details, check out:
- The announcement “CISA and Partners Release Updated Advisory on Scattered Spider Group”
- The full advisory “Scattered Spider”
For more information about Scattered Spider:
- “What we know about the cybercrime group Scattered Spider” (Cybersecurity Dive)
- “Scattered Spider: Hacker Collective Ensnaring Industry-Specific Targets” (Coalition Insurance)
- “Scattered Spider” (MITRE ATT&CK)
- “Scattered Spider weaves web of social-engineered destruction” (CyberScoop)
- “The Scattered Spider ransomware group is infiltrating Slack and Microsoft Teams to target vulnerable employees” (ITPro)
4 - CISA spotlights zero-trust microsegmentation
How do you contain a breach before it spreads across your entire network? A new guide points to microsegmentation in zero trust architectures. Think of it like digital bulkheads on a ship: by dividing your network into small, isolated zones, you can contain the "blast radius" of an attack.
“Microsegmentation in Zero Trust Part One: Introduction and Planning,” released this week by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), unpacks the main pillars of microsegmentation and outlines key challenges and benefits. A second part to be published later will focus on implementation.
“Microsegmentation works by protecting a smaller group of resources, thereby reducing the attack surface, limiting lateral movement and increasing visibility for better monitoring of the microsegmented environment,” the 24-page document reads.

As the document highlights, microsegmentation isn't a replacement for existing security practices. Instead, it enhances them, allowing for more targeted, risk-appropriate protections for specific systems and data.
The document recommends a phased approach to adopting microsegmentation, including steps such as identifying potential segmentation resources and crafting segmentation policies. It also proposes planning considerations in areas like the handling of OT, IoT and legacy environments and devices.
CISA ends the guide by offering three real-life microsegmentation projects:
- The re-architecture of an on-premises enterprise
- Adoption as part of an environment transition to the cloud
- Adoption in a distributed enterprise
For more information about microsegmentation:
- “Microsegmentation Technical Deep Dive into Network Security” (Cybersecurity News)
- “Flat networks, fast hackers: Microsegmentation gets a security comeback” (SC World)
- “What are the benefits and challenges of microsegmentation?” (TechTarget)
- “Microsegmentation: Implementing Zero Trust at the Network Level” (GigaOM)
5 - How to kick hackers out for good
What is the most effective way to contain and evict intruders from your networks and devices?
This is the question that prompted CISA to create the “Eviction Strategies Tool,” a web app with a database of post-incident actions designed to match incident findings with appropriate countermeasures.
Offering more than simple malware removal, the tool focuses on helping cyber defenders plan and carry out a comprehensive containment and eviction process that prevents an adversary’s return.

(Image generated by Tenable using Google Gemini)
The “Eviction Strategies Tool” features two open-source components:
- Playbook-NG: This stateless web-based application allows security teams to create customized incident response playbooks. Defenders can input specific threat actor behaviors, either through MITRE ATT&CK technique IDs or free-text descriptions, and the tool will generate a set of recommended countermeasures.
- COUN7ER: This is a comprehensive database of post-compromise actions and mitigations that are mapped to known adversary tactics, techniques, and procedures (TTPs). It serves as a reference for Playbook-NG, providing the specific, actionable steps needed to address a given threat.
“Together, Playbook-NG and COUN7ER create a systematic, tailored eviction plan that leverages distinct countermeasures to effectively contain and evict adversarial intrusions,” reads a CISA statement.
Via a structured and repeatable process, the “Eviction Strategies Tool” seeks to help organizations accelerate their incident response and reduce adversary dwell time.
To get more details, check out:
- The CISA announcement “Eviction Strategies Tool Released”
- The “Eviction Strategies Tool” site
- The “Eviction Strategies Tool” GitHub page
For more information about incident response:
- “Cybersecurity Incident Response” (CISA)
- “Incident response tabletop exercises: Guide and template” (TechTarget)
- “Incident Response” (SANS Institute)
- “13 incident response best practices for your organization” (TechTarget)
6 - Meet Tenable at Black Hat 2025: Let's Get It Together
Heading to Vegas for Black Hat USA 2025? Swing by the Tenable booth (#2440)! We’re at the center of the expo hall with a packed schedule of lightning talks, six demo stations and – wait for it – a bar for designing your own custom Tenable One t-shirt.
Our theme for the conference is “Get It Together” because unified visibility, better insights and preemptive action are the key for preventing and addressing today’s most dangerous exposures. Check out how we help security teams unify data, tools, and teams to turn vulnerability management into true exposure management.

In addition, don’t miss our main stage session “Don’t Let AI Divide Your Defenses” by Tenable VP of Product Management Tomer Avni on Wed. Aug. 6 at 11:20 am in Business Hall Theater A.
To get more details, check out our Black Hat USA 2025 page.

Juan Perez
Senior Content Marketing Manager
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh