
Python软件基金会警告称,黑客正通过仿冒PyPI网站的钓鱼攻击窃取用户凭证。部分开发者收到看似来自PyPI的邮件,要求验证邮箱并点击链接登录。该链接实为钓鱼网站,诱导用户提供凭据。建议用户不要点击链接,并立即删除邮件;若已泄露信息,请更改密码并检查账户安全。 2025-7-30 19:0:34 Author: www.bleepingcomputer.com(查看原文) 阅读量:17 收藏

The Python Software Foundation warned users this week that threat actors are trying to steal their credentials in phishing attacks using a fake Python Package Index (PyPI) website.
PyPI is a repository for Python packages, accessible at pypi.org, that offers a centralized platform for developers to distribute and install third-party software libraries. It hosts hundreds of thousands of packages and is the default source for Python's package management tools.
"PyPI has not been hacked, but users are being targeted by a phishing attack that attempts to trick them into logging in to a fake PyPI site. Over the past few days, users who have published projects on PyPI with their email in package metadata may have received an email titled '[PyPI] Email verification' from the email address [email protected]," the PyPI admin Mike Fiedler cautioned.
"This is not a security breach of PyPI itself, but rather a phishing attempt that exploits the trust users have in PyPI. The email instructs users to follow a link to verify their email address, which leads to a phishing site that looks like PyPI but is not the official site."
After opening the malicious website, the targeted users will be prompted to sign in, with the requests sent back to PyPI to trick the users into believing they have logged in to PyPI.
However, the attackers are instead harvesting their credentials, which will likely be used in future attacks to infect Python packages they've uploaded to PyPI with malware or to upload new malicious packages onto the platform.
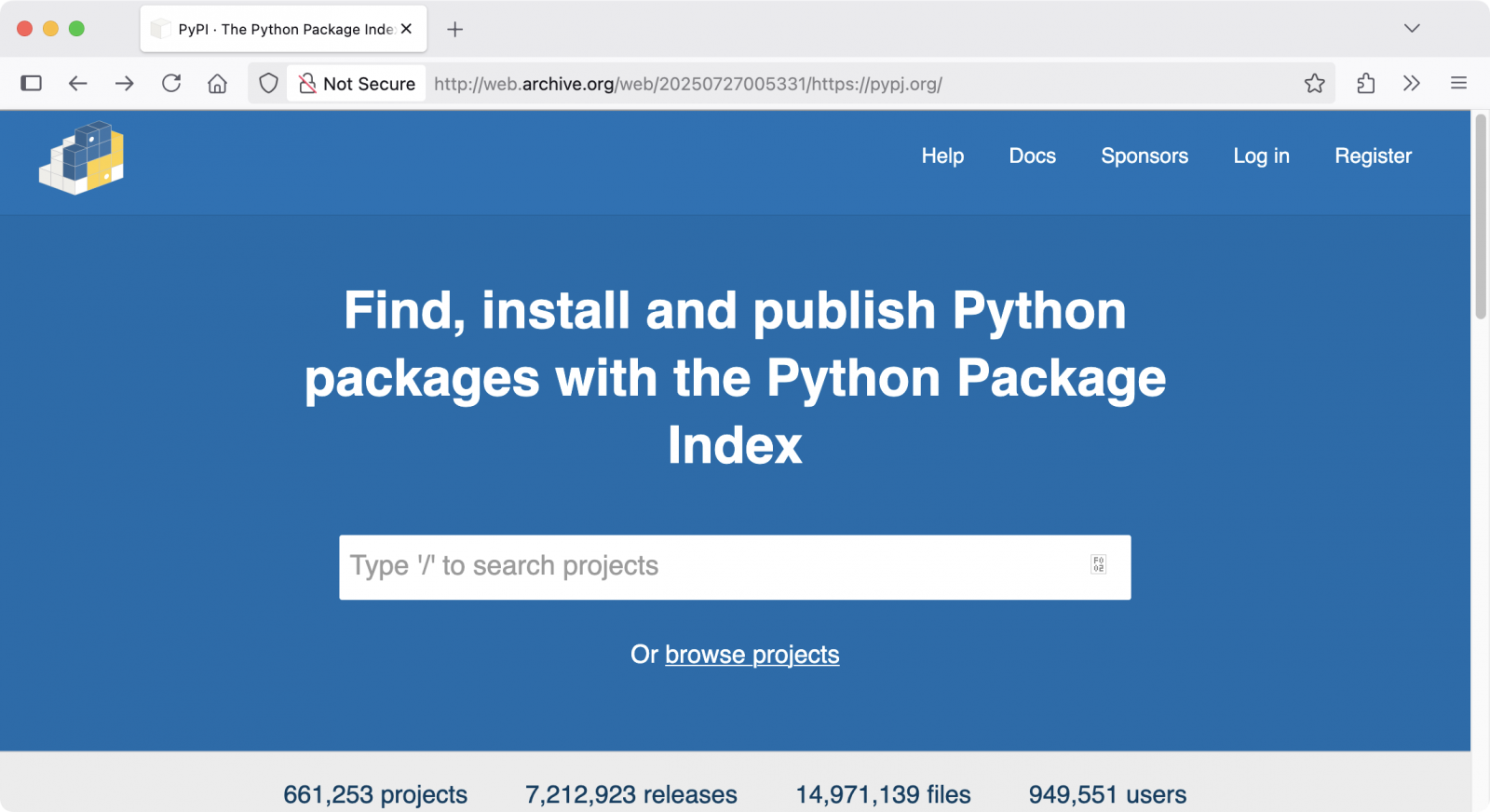
The PyPI admins have also added a banner to PyPI's homepage, warning users of this phishing attack, and are now working to find a way to disrupt this ongoing campaign.
"We are also waiting for CDN providers and name registrars to respond to the trademark and abuse notifications we have sent them regarding the phishing site," Fiedler added.
Python developers and PyPI users who have received these phishing emails are advised not to click the embedded links and to delete the email immediately.
Those who have already entered their credentials on the pypj[.]org phishing site, should immediately change their PyPI password and inspect their accounts' Security History for suspicious or unexpected activity.
In February, the Python Software Foundation introduced 'Project Archival,' a new system designed to help PyPI publishers archive their projects, indicating to users that no updates are expected.
PyPI was also forced to temporarily suspend user registration and the creation of new projects in March 2024 due to a malware campaign linked to threat actors who uploaded hundreds of new malicious packages masquerading as legitimate projects.
The Board Report Deck CISOs Actually Use
CISOs know that getting board buy-in starts with a clear, strategic view of how cloud security drives business value.
This free, editable board report deck helps security leaders present risk, impact, and priorities in clear business terms. Turn security updates into meaningful conversations and faster decision-making in the boardroom.
如有侵权请联系:admin#unsafe.sh
