
德国游戏外设公司Endgame Gear警告称,在其官网提供下载的OP1w 4k v2鼠标配置工具中发现恶意软件。该工具于2025年6月26日至7月9日期间被感染。受影响文件大小异常且显示为“Synaptics Pointing Device Driver”。恶意软件被识别为XRed后门程序,具有键盘记录、远程控制和数据窃取功能。公司已移除恶意软件,并建议用户删除相关文件并重新下载干净版本。 2025-7-28 19:0:31 Author: www.bleepingcomputer.com(查看原文) 阅读量:10 收藏

Gaming peripherals maker Endgame Gear is warning that malware was hidden in its configuration tool for the OP1w 4k v2 mouse hosted on the official website between June 26 and July 9, 2025.
The infected file was hosted on 'endgamegear.com/gaming-mice/op1w-4k-v2,' so users downloading the tool from that page during this period were infected.
Endgame Gear is a German PC gaming peripherals firm known for its pro-gaming gear, including the XM and OP1 series mice, which are highly regarded among reviewers and competitive players.
Although not as big as brands like Logitech, Razer, and HyperX, it is a respected entity in the space and one of the key emerging firms in the ultra-light gaming mouse segment.
Last week, the company announced that its "Endgame_Gear_OP1w_4k_v2_Configuration_Tool_v1_00.exe" tool on its website had been compromised with malware without providing specifics about how the breach took place.
"During the period of June 26th to July 9th, a version of the Configuration Tool for the Endgame Gear OP1w 4k v2 wireless mouse, available for download on the OP1w 4k v2 product page, was found to contain malware," reads the announcement.
Endgame Gear says the malware has since been removed, and those downloading the tool from its main downloads page at (endgamegear.com/downloads), GitHub, or Discord were not impacted, as those channels delivered a clean version.
Reports about malware on OP1's configuration tool surfaced on Reddit nearly two weeks ago, with users highlighting several key differences suggesting that the vendor's site hosted a trojanized installer.
Two key differences are an inflated size of 2.8MB (from 2.3MB in the clean version), and "Synaptics Pointing Device Driver" shown in file properties (instead of the legitimate "Endgame Gear OP1w 4k v2 Configuration Tool").
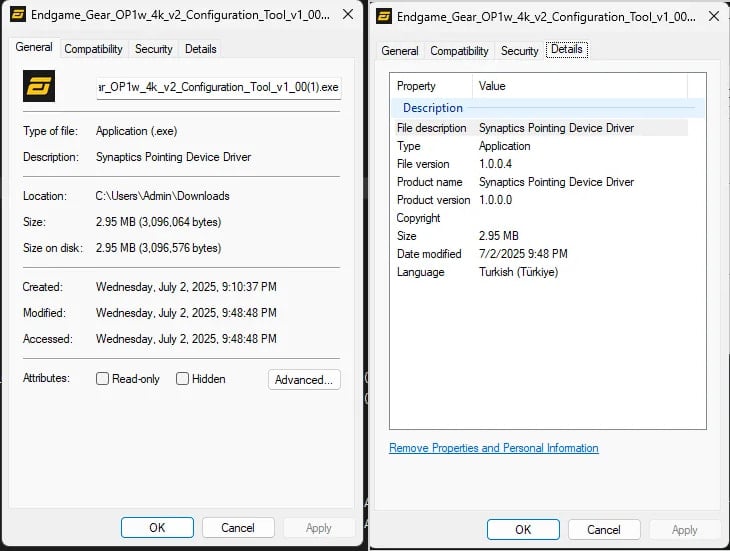
Source: Admirable-Raccoon597 | Reddit
The malware family was identified as the XRed backdoor in user scans, but Endgame Gear stated that it's still analyzing the payload and has not confirmed its type.
XRed was previously observed by cybersecurity firm eSentire impersonating a Synaptics Pointing Device Driver in February 2024. The malware was also distributed through trojanized software that shipped with USB-C hubs on Amazon.
Endgame Gear recommends that people who downloaded a trojanized version of the installer delete everything from 'C:\ProgramData\Synaptics' and re-download a clean version of the tool from this page.
As the malware contains keylogging functionality, the ability to open a remote shell, and data exfiltration, infected users should run a full system scan using an up-to-date antivirus to ensure all malware remnants are removed.
Furthermore, passwords should be changed at all sensitive accounts, such as financial institutions, email providers, and work accounts.
Going forward, Endgame Gear will discontinue separate download pages and will add SHA hash verification and digital signing for all hosted files to confirm file integrity and publisher authenticity.
Cloud Detection & Response for Dummies
Contain emerging threats in real time - before they impact your business.
Learn how cloud detection and response (CDR) gives security teams the edge they need in this practical, no-nonsense guide.
如有侵权请联系:admin#unsafe.sh
