
超过20万WordPress网站使用Post SMTP插件的漏洞版本(CVE-2025-24000),允许黑客接管管理员账户。该漏洞源于REST API访问控制缺陷,低权限用户可获取敏感信息并重置管理员密码。尽管已修复并发布新版本(3.3.0),但仍有大量网站未更新,面临风险。 2025-7-26 18:15:24 Author: www.bleepingcomputer.com(查看原文) 阅读量:16 收藏

More than 200,000 WordPress websites are using a vulnerable version of the Post SMTP plugin that allows hackers to take control of the administrator account.
Post SMTP is a popular email delivery plugin for WordPress that counts more than 400,000 active installations. It’s marketed as a replacement of the default ‘wp_mail()’ function that is more reliable and feature-rich.
On May 23, a security researcher reported the vulnerability to WordPress security firm PatchStack. The flaw is now identified as CVE-2025-24000 and received a medium severity score of 8.8.
The security issue affects all versions of Post SMTP up to 3.2.0 and is due to a broken access control mechanism in the plugin’s REST API endpoints, which only verified if a user was logged in, without checking their permission level.
This means that low-privileged users, such as Subscribers, could access email logs containing full email content.
On vulnerable sites, a subscriber could initiate a password reset for an Administrator account, intercept the reset email via the logs, and gain control of the account.
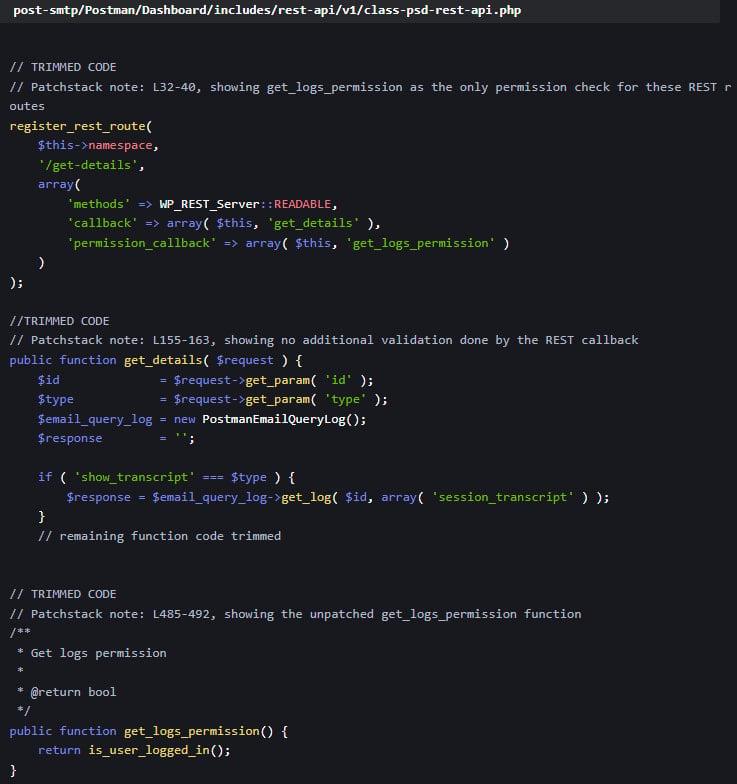
Source: PatchStack
The plugin’s developer, Saad Iqbal, was informed about the flaw and responded with a fix for Patchstack to review on May 26.
The solution was to incorporate additional privilege checks in the ‘get_logs_permission’ function that would validate a user’s permissions before giving access to sensitive API calls.
The fix was incorporated into Post SMTP version 3.3.0, which was published on June 11.
Download statistics on WordPress.org show that less than half of the plugin's user base (48.5%) has updated to version 3.3. This means that more than 200,000 websites are vulnerable to CVE-2025-24000.
A notable 24.2%, corresponding to 96,800 sites, still run Post SMTP versions from the 2.x branch, which is vulnerable to additional security flaws, leaving them open to attacks.
Cloud Detection & Response for Dummies
Contain emerging threats in real time - before they impact your business.
Learn how cloud detection and response (CDR) gives security teams the edge they need in this practical, no-nonsense guide.
如有侵权请联系:admin#unsafe.sh
