
文章概述了本周网络安全动态,包括SharePoint漏洞紧急修复、白宫AI创新计划强调安全、CISA警告Interlock勒索软件风险、凭据与无凭据扫描调查结果、Q2勒索ware攻击下降但活跃团伙增加以及Q2最常见恶意软件排名。 2025-7-25 13:0:0 Author: www.tenable.com(查看原文) 阅读量:25 收藏
Check out the latest on attackers’ cyber siege of SharePoint servers. Plus, the White House releases plan to spur AI innovation. In addition, CISA alerts orgs about Interlock ransomware. And get the latest on Q2's top malware; ransomware trends; and credentialed scanning.
Here are six things you need to know for the week ending July 25.
1 - Urgent: Patch SharePoint ASAP to fix actively-exploited bugs
Chinese hacking groups are attacking on-premises versions of Microsoft’s SharePoint globally to exploit newly-disclosed vulnerabilities. Hundreds of organizations, including the U.S. National Nuclear Security Administration (NNSA), have reportedly been impacted.
Thus, organizations running SharePoint Server Subscription Edition, SharePoint Server 2019 and SharePoint 2016 – the three supported on-prem versions of this widely-used enterprise collaboration server – should immediately install Microsoft’s security updates.
The vulnerabilities in question have been identified as CVE-2025-49706, CVE-2025-49704, CVE-2025-53770 and CVE-2025-53771. SharePoint Online in Microsoft 365 isn’t affected.
For a deep dive into these SharePoint vulnerabilities, check out the Tenable Research Special Operations team’s blog “CVE-2025-53770: Frequently Asked Questions About Zero-Day SharePoint Vulnerability Exploitation.”

Chinese nation-state groups Linen Typhoon and Violet Typhoon are targeting these vulnerabilities in internet-facing SharePoint servers, while China-based actor Storm-2603 is exploiting these bugs to unleash the Warlock ransomware on victims, Microsoft said in a blog, adding that it continues investigating possible involvement by other hacking groups.
“With the rapid adoption of these exploits, Microsoft assesses with high confidence that threat actors will continue to integrate them into their attacks against unpatched on-premises SharePoint systems,” the Microsoft blog reads.
Speaking to Wired magazine, Tenable CSO and Head of Research Robert Huber warned that legacy SharePoint servers are hard to secure because they’re so intervowen with other systems.
“For on-premises software like SharePoint, which is deeply integrated into the Microsoft identity stack, there are multiple points of exposure that need to be continuously monitored in order to know, expose and close critical gaps,” Huber told Wired. For more on his thoughts, check out Huber's LinkedIn post about the exploited SharePoint vulnerabilities.
This week, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an alert with recommended actions for organizations using these SharePoint servers. The alert, titled “Microsoft Releases Guidance on Exploitation of SharePoint Vulnerabilities,” recommends applying the Microsoft security updates, as well as:
- Configuring SharePoint’s Antimalware Scan Interface, and running the anti-malware tool Microsoft Defender AV on all SharePoint servers
- Rotating ASP.NET machine keys, applying the Microsoft security updates, rotating the ASP.NET machine keys again and restarting the IIS web server
- Disconnecting from the internet the SharePoint Server versions that Microsoft is no longer providing security updates for
- Adopting comprehensive logging to flag exploitation activity
To get more information about these SharePoint vulnerabilities and the exploitation campaign:
- “Disrupting active exploitation of on-premises SharePoint vulnerabilities” (Microsoft)
- “Customer guidance for SharePoint vulnerability CVE-2025-53770” (Microsoft)
- “CVE-2025-53770: Frequently Asked Questions About Zero-Day SharePoint Vulnerability Exploitation” (Tenable)
- “SharePoint 0-day uncovered (CVE-2025-53770)” (Eye Security)
- “Hundreds of organizations breached by SharePoint mass-hacks” (TechCrunch)
2 - White House AI plan emphasizes cybersecurity
“America’s AI Action Plan,” a wide-ranging White House policy document that articulates the U.S. government’s AI strategy, links the future of AI innovation with robust cybersecurity.
The 28-page document, published this week, outlines a multi-pronged approach to ensure that as the U.S. develops and adopts AI systems, it does so securely by focusing on key areas including:
- Leveraging AI to strengthen critical infrastructure by establishing an AI Information Sharing and Analysis Center (AI-ISAC) for quick threat intelligence sharing
- Adopting secure-by-design principles for AI apps, including embedding protections directly into AI models to defend against attacks like data poisoning or adversarial inputs
- Preparing for AI-related cyber incidents by updating CISA’s playbooks with AI-specific protocols and fostering public-private partnerships to develop clear response standards
- Facilitating the secure build-up of AI infrastructure by streamlining permits for data centers, semiconductor manufacturing facilities and energy infrastructure
- Building high-security data centers for the use of the military and intelligence communities
“Secure AI innovation has become critical to national security, and to a holistic exposure management program. Whether it’s a federal directive or an industry-led initiative, AI without built-in cybersecurity is a liability,” Tenable CSO and Head of Research Robert Huber said in a statement.
For more information about AI security trends:
- “Cybersecurity in 2025: Agentic AI to change enterprise security and business operations in year ahead” (SC World)
- “6 AI-Related Security Trends to Watch in 2025” (Dark Reading)
- “How AI agents could revolutionize the SOC — with human help” (Cybersecurity Dive)
- “2025 to be a Year of Reckoning for AI in Cybersecurity” (Infosecurity Magazine)
- “AI security issues dominate corporate worries, spending” (Cybersecurity Dive)
3 - CISA: Don’t get caught in Interlock ransomware’s grip
Businesses and critical infrastructure organizations in North America and Europe should take immediate action to defend themselves against the Interlock ransomware group.
The urgent warning comes from CISA, the Federal Bureau of Investigation (FBI) and others via the joint cybersecurity advisory “#StopRansomware: Interlock” issued this week.
“These actors are opportunistic and financially motivated in nature and employ tactics to infiltrate and disrupt the victim’s ability to provide their essential services,” the joint advisory reads.

This double-extortion ransomware group, active since September 2024, uses a variety of tactics for initial access, including less-common methods like drive-by-downloads from compromised legitimate websites and a social engineering technique called ClickFix.
Once inside a network, the attackers engage in a multi-stage process of reconnaissance, credential access, lateral movement and data exfiltration before finally deploying the ransomware and demanding payment.
Mitigation recommendations include:
- Prevent initial access: Implement robust DNS filtering and web access firewalls to block malicious sites. Train users to identify and avoid social engineering and phishing attempts.
- Manage vulnerabilities: Regularly patch and update operating systems, firmware and software to mitigate known vulnerabilities.
- Segment networks: Segment networks to limit the blast radius of a potential infection.
- Control access: Enforce strong identity, credential and access management policies, including the use of multi-factor authentication (MFA) and just-in-time access.
- Protect and recover data: Maintain offline backups of critical data and a well-documented and tested recovery plan.
- Secure endpoints: Utilize endpoint detection and response (EDR) tools to help detect and respond to suspicious activity on endpoints.
To get more details about Interlock’s tactics, techniques and procedures, and about its indicators of compromise, read the full “#StopRansomware: Interlock” advisory.
For more information about Interlock ransomware:
- “Meet Interlock — The new ransomware targeting FreeBSD servers” (BleepingComputer)
- “New Interlock Ransomware Group Targets US Healthcare Organizations” (The HIPAA Journal)
- “Interlock ransomware evolves tactics with ClickFix, infostealers” (SC Media)
- “How Interlock Ransomware Infects Healthcare Organizations” (The Hacker News)
- “Interlock Ransomware Targets US Healthcare, IT and Government Sectors” (Infosecurity Magazine)
4 - Poll: A look at credentialed and uncredentialed scanning
In our recent webinar “Tenable Vulnerability Management Customer Update, July 2025,” we polled attendees on the pros and cons of credentialed and uncredentialed vulnerability scans. Check out what they said.
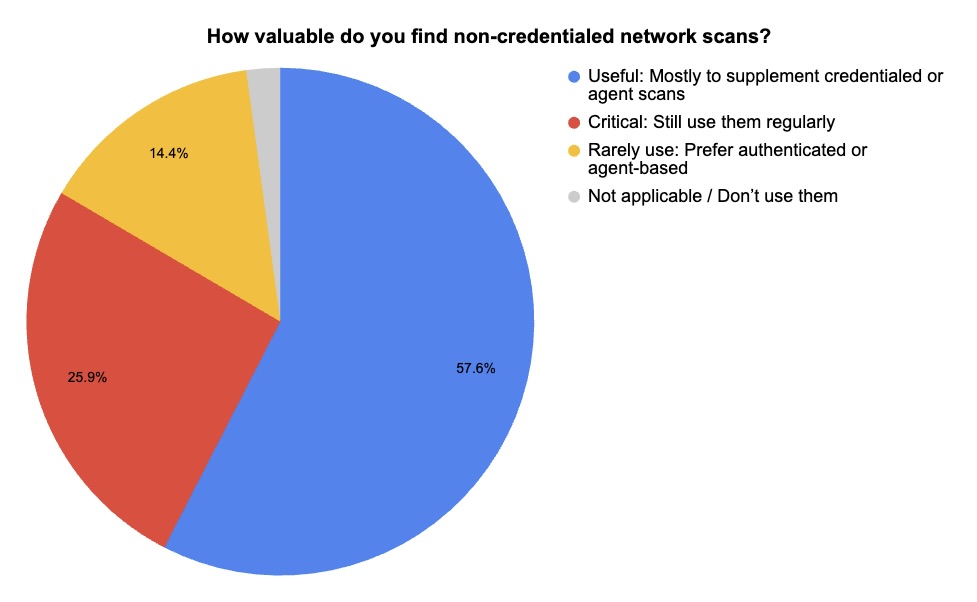
(139 webinar attendees polled by Tenable, July 2025)
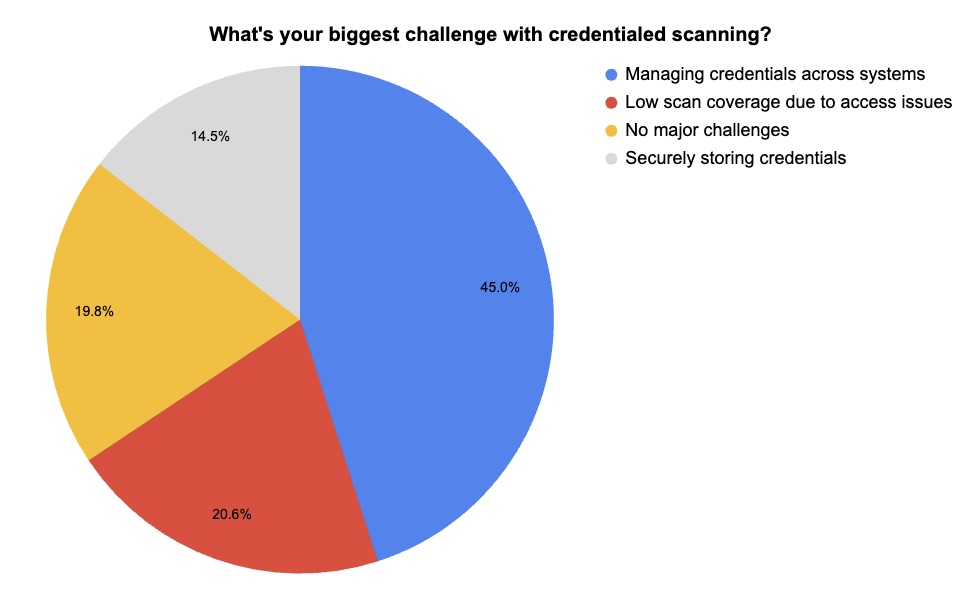
(131 webinar attendees polled by Tenable, July 2025)
These results highlight the central issue at hand: Credentialed scans provide deeper, more accurate data but come with the overhead of managing credentials securely.
Want to learn more about how to use managed credentials, and about what’s new in Tenable Vulnerability Management? Watch this webinar on-demand!
5 - Report: Ransomware attacks plummet, but active groups balloon
The number of ransomware attacks plunged 43% in the second quarter, compared with the first quarter, due to a seasonal lull and to law-enforcement actions. But don’t relax, NCC Group said in its “Cyber Threat Intelligence Report: Review of Q2 2025,” released this week.
Despite the drop in attacks, the ransomware ecosystem remains dynamic and dangerous. For example, ransomware’s use in cyber warfare is increasing. Plus, ransomware groups are multiplying and sharpening their social engineering methods.
So far this year, NCC Group has tracked 86 new and existing active ransomware groups, putting 2025 on pace to break last year’s record.
“The increased number of attackers means a broader range of attack methods that businesses need to be prepared for. Both organisations and nations should take this as a sign to remain vigilant,” Matt Hull, Global Head of Threat Intelligence at NCC Group, said in a statement.
6 - A look at the top malware of Q2 2025
Malware infections slid 18% in the second quarter of 2025, compared with the first quarter, but SocGholish retained its position as the most prevalent variant.
SocGholish, which attackers use in fake software-update attacks, has now ranked first on the Center for Internet Security’s top 10 list of malware incidents for eight straight quarters.
SocGholish’s two-year reign atop this list highlights how popular fake software-update attacks are among hackers.
In these attacks, users get tricked into installing a legitimate-looking update for one of their apps, typically their preferred browser. Instead, the downloaded “update” infects their computers with malware.
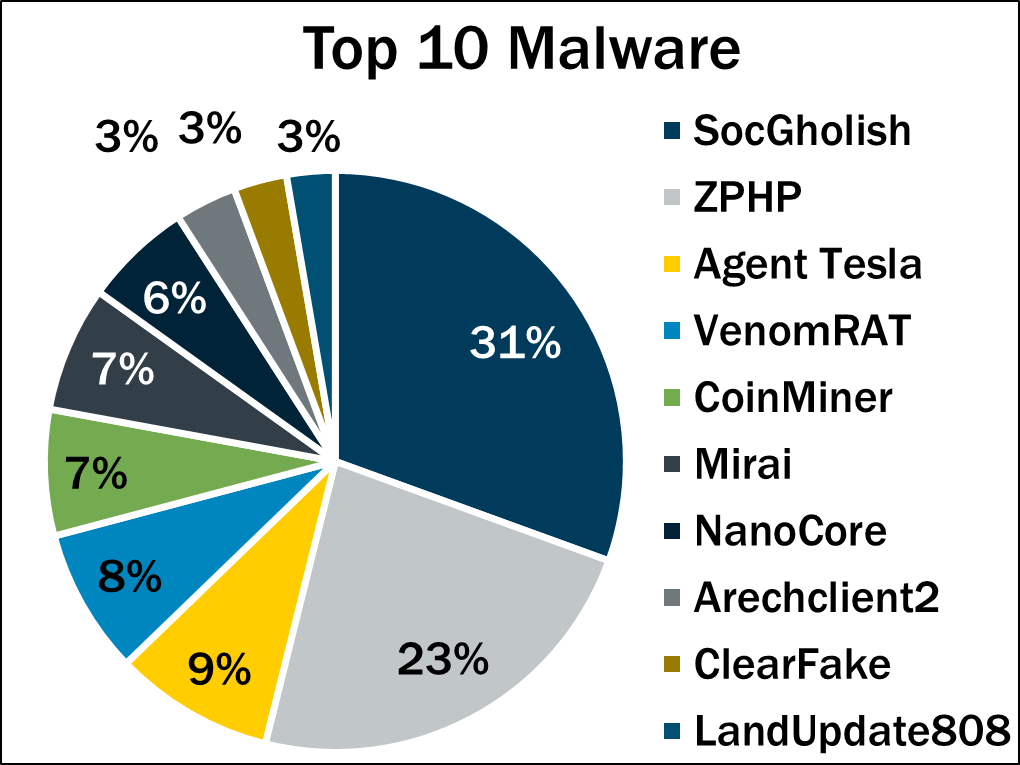
(Source: “Top 10 Malware Q2 2025” report from the Center for Internet Security, July 2025)
Here’s the full list of the most prevalent malware variants in the second quarter of 2025, in descending order:
- SocGholish, a downloader distributed through malicious websites that tricks users into downloading it by offering fake software updates
- ZPHP, a JavaScript downloader that’s distributed via fake browser updates
- Agent Tesla, a RAT that captures credentials, keystrokes and screenshots
- VenomRAT, an open-source malware with multiple versions whose features include keylogging, data exfiltration and screen capturing
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI)
- Mirai, a malware botnet used to compromise IoT devices to conduct distributed denial of service (DDoS) attacks
- NanoCore, a RAT that spreads via malspam as a malicious Excel spreadsheet
- Arechclient2, also known as SectopRAT, is a .NET remote access trojan (RAT) whose capabilities include multiple stealth functions
- ClearFake, a JavaScript downloader distributed via fake browser updates
- LandUpdate808, a JavaScript downloader distributed through malicious or compromised websites via fake browser updates
Meanwhile, the primary method of infection in Q2 was malvertising, where malicious ads on websites lead to malware downloads.
To get more information, check out the CIS blog “Top 10 Malware Q2 2025,” where you’ll find more details, context and indicators of compromise for each malware strain.
For details on fake software-update attacks:
- “The Fake Browser Update Scam Gets a Makeover” (Krebs on Security)
- “Watch Out: Attackers Are Hiding Malware in 'Browser Updates'” (Dark Reading)
- “Hackers Use Fake Browser Updates for AMOS Malware Attacks Targeting Mac Users” (MSSP Alert)
- “Malware crooks find an in with fake browser updates, in case real ones weren't bad enough” (The Register)
- “Hackers have been spreading malware via fake Chrome updates” (TechRadar)
VIDEO
Fake Chrome Update Malware (The PC Security Channel)

Juan Perez
Senior Content Marketing Manager
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh