
文章探讨了网络安全专业人士面临的挑战,包括工具过多导致的数据过载、资源限制及团队协作问题。传统安全系统分散在孤岛中,缺乏上下文支持优先处理风险。暴露管理通过整合数据和提供清晰信号,帮助团队高效识别和修复关键风险。 2025-7-21 13:0:0 Author: www.tenable.com(查看原文) 阅读量:14 收藏
Each Monday, the Tenable Exposure Management Academy provides the practical, real-world guidance you need to shift from vulnerability management to exposure management. In this post, we look at the results of a survey taken during a recent Tenable webinar on the greatest cybersecurity challenges. You can read the entire Exposure Management Academy series here.
If you’re like most security professionals, you and your team have deployed more tools than ever. Maybe you’re still deploying or plan to deploy additional tools. Security tool sprawl is a natural response to the threats you face.
Maybe you thought those new tools would bring you peace of mind.
Roll them out one by one and you’ll soon see a torrent of data about potential risks that you’re probably not prepared for. But don’t feel bad. No one could handle that kind of volume. You’re not alone in this battle.
Many security leaders feel their teams are working harder than ever just to keep their heads above water. Like you, they struggle each day to translate mountains of data into tangible business risk reduction. Sound familiar? Like we said — you’re not the only one.
Confirmation came during a recent Tenable webinar, Security Without Silos: Gain Real Risk Insights with Exposure Management Upsized.
We polled the cybersecurity professionals in attendance about their greatest challenges. The results were revealing: your peers from around the globe confirm what you are probably already experiencing.
The greatest cybersecurity challenges
Question: Which of the following security challenges is your organization currently facing? 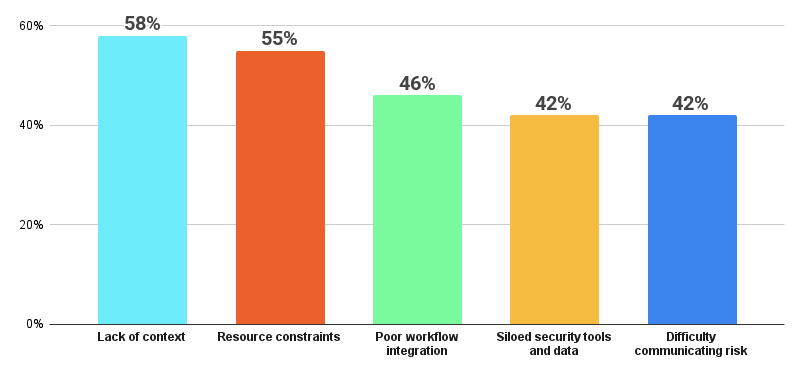
Source: Tenable webinar poll of 74 respondents, April 2025
When asked to share their greatest cybersecurity challenges (they were able to pick more than one response — because, frankly, they all have more than one challenge), practitioners gave us a startling picture of their concerns. The results are telling:
- 58% said that lack of context to prioritize risks was a primary challenge
- 55% cited resource constraints (budget, staffing)
- 46% pointed to poor workflow integration across teams
- 42% told us that siloed security tools and data was a significant issue
- 42% said they were having difficulty communicating risk to leadership
Although these are separate issues, they’re all related to the security tool sprawl we mentioned earlier. And they’re symptoms of a systemic problem that most organizations grapple with every day.
Legacy cybersecurity systems and the visibility plateau
How many times have we heard someone say, “If I only had the data”?
But the data itself, or lack of it, isn’t the root cause. Rather, it’s a flaw in the design of the legacy cybersecurity systems. Built separately over years or decades, security tools operate in disconnected silos, which creates something of a "visibility plateau."
The irony is, in an effort to stamp out vulnerabilities with data, this fragmented view created a critical vulnerability of its own.
As organizations add more scanners and agents for cloud, on-premises, identity and applications, they definitely get more data. But they don’t get something they urgently need: better insight.
Each tool generates its own alerts and reports, which creates a cacophony that security and IT teams have to sift through manually to find the true exposures. This is clearly inefficient and directly adds to the resource constraints pointed out by more than half of the poll respondents.
The irony is, in an effort to stamp out vulnerabilities with data, this fragmented view created a critical vulnerability of its own. And, although those security teams and tools operate in silos, attackers don’t. The bad guys scan your environment as a single, interconnected attack surface.
If you think this is all in the abstract and not the real world, consider this. One financial institution with a very mature and well-funded cybersecurity program deployed dozens of tools and had dedicated staff in place. Even so, it was still breached, with an impact of $650 million.
The organization probably knew it had a misconfigured web application firewall in one of its tools. But that finding by itself was medium to low risk and the firm lacked the context it needed to correlate that misconfiguration to an attack path. So threat actors were able to gain access to crown jewels and 100 million customers were left exposed.
The lesson here: A threat actor who looks hard enough can find a misconfiguration in a cloud service, use a compromised identity and exploit a traditional vulnerability on an internal server to achieve their goal.
Sadly, that’s because they can connect the dots that siloed tools can’t.
The more tools you have operating in isolation, the less likely you are to have the contextual prioritization needed to stop these advanced attacks. This creates unseen and unobserved exposures that can pose significant risks to the organization.
Enter exposure management
An exposure management platform can help bridge the gap by giving your teams the critical context they need to prioritize true business exposure. It can turn all that data coming from your various security tools into clean, clear signals that give you the visibility you need to proactively find and fix what matters most to your organization.
As a result, your security teams can focus on more strategic tasks, all while being more efficient and less reactive.
But how do you get there? As we shared in What Is Exposure Management and Why Does It Matter?, five steps can help you improve your security posture:
- Understand your attack surface: With exposure management, you’ll gain a holistic view of all assets, including cloud, IT, OT, IoT, identities and apps.
- Pinpoint preventable risks: Because exposure management can detect vulnerabilities, misconfigurations and excessive privileges, you’ll quickly identify high-risk assets.
- Connect with business goals: Exposure management uses asset tagging so you can group assets by business function and track exposure changes with cyber exposure scores.
- Target true exposure: Exposure management can prioritize remediation by mapping attack paths to critical assets, separating noise from material risks.
- Optimize security spend: Exposure management helps quantify cyber exposure, compares your organization to peers and can justify budget by answering a critical question: "Are we secure?"
Takeaways
You might be ready to get started. Or maybe you’ve already planned your first steps and are well on your way.
But some questions remain. Is your program ad-hoc, with limited tools and processes? Or is it advanced, with unified data and automated prioritization? To help you see where you are on this journey, we developed an exposure management maturity assessment. In less than 10 minutes, you’ll have your answer.
Learn more
- Check out the Tenable exposure management resource center to discover the value of exposure management and explore resources to help you stand up a continuous threat exposure management program.
如有侵权请联系:admin#unsafe.sh