恶意APK通过品牌仿冒和流量变现进行攻击,涉及广告欺诈、凭证窃取、数据收集等行为,并具备沙盒检测和加密通信能力。 2025-7-18 13:0:0 Author: www.trustwave.com(查看原文) 阅读量:11 收藏
6 Minute Read
Malicious APKs (Android Package Kit files) continue to serve as one of the most persistent and adaptable delivery mechanisms in mobile threat campaigns. Threat actors routinely exploit social engineering and off-market distribution to bypass conventional security controls and capitalize on user trust to steal a variety of data, such as log in credentials. In a recent investigation, Trustwave SpiderLabs identified an active Android malware cluster that systematically blends brand impersonation with traffic monetization, operating at scale across multiple regions. While some variants in this campaign focus on local data collection or generating fraudulent ad traffic, others demonstrate more advanced capabilities. These include credential theft, sandbox detection, and encrypted command-and-control (C2) communications. Victims are typically tricked into downloading seemingly legitimate APKs, often disguised as trusted services, promotional apps, or well-known brands. The infection method is straightforward: users are lured (via phishing messages or malicious web content) to manually install APKs from untrusted sources. Once installed, these apps abuse Android’s permissive permission model to access sensitive content, persist in the background, and hijack network traffic for monetization purposes. This often involves simulating user activity to inflate ad metrics or redirect users through affiliate funnels. Our analysis revealed a wide range of APK samples, each exhibiting varying degrees of complexity but sharing ties to the same threat cluster. Notable categories include: Despite functioning differently, these APKs share flexible payload designs capable of adapting behavior at runtime based on locale, language settings, or virtualized environments. Some samples performed basic anti-analysis checks, such as detecting emulators or delaying execution. Others featured UI elements that convincingly impersonated login portals of popular services. A common tactic observed was traffic redirection through parked or monetized domains, often before leading the user to a legitimate website. This behavior mimics real user interaction and enables large-scale click fraud and affiliate revenue generation. A subset of APKs impersonate well-known services such as banks or social platforms. These apps trick users into submitting login credentials, which are then exfiltrated without visible indicators. Masquerading as benign utilities, these apps quietly collect sensitive data in the background. The permissions that are requested often far exceed their stated functionality. These apps promise monetary rewards in exchange for ad engagement or app installations. In practice, they often subject users to excessive ads, harvest data, and embed hidden fees or subscriptions. The “rewards” are frequently difficult to redeem or entirely illusory. Another group of apps advertise fast cash and entertainment but often operate in legal gray zones. Some access personal data and financial details, while others manipulate in-app transactions or skirt local regulations. Some of the most advanced and polished variants in this campaign impersonated globally recognized apps such as TikTok and Facebook. Among the latest samples distributed by this threat cluster was a spoofed Facebook APK (6e47540ee83e8f0f886d24f5a948e47bdbe8cfc69b05c20e1ff2328f53d2d160) distributed via a Facebook Ads-themed landing page (fb20-11-en[.]9jtfb7jt[.]vip). This fake app was delivered through social engineering, typically via direct messages or lure websites containing persuasive calls-to-action such as “Create Your Ad Campaign” or “Start Now”. Once clicked, the malicious APK was automatically downloaded to the user’s device. Upon installation, the app requests a broad set of permissions, ranging from legitimate Android permissions such as ACCESS_FINE_LOCATION and CAMERA to custom, spoofed permissions designed to mimic Facebook components, including com.facebook.batana_com.facebook.orca.provider.ACCESS. The app closely mimicked Facebook’s UI, reusing its iconography and visual style. Immediately upon launch, without any user interaction, the app issues a background HTTP GET request to retrieve a configuration file. The file Base64-encoded and encrypted using AES in ECB mode with a hardcoded key, is retrieved from an object storage bucket. Once decrypted, the file exposes a set of C2 API endpoints and operational URLs. The app then makes follow-up POST requests using this configuration data. Further investigation into the infrastructure uncovered a broader set of configuration files hosted under the same domain, ranging from fb.kodownapp[.]top/fbc003.txt through .../fbc039.txt. Each of these followed a similar encryption scheme and structural format, pointing to a modular backend infrastructure designed to support multiple campaigns. In addition to the primary domain, we identified subdomains such as apk.kodownapp[.]top, ko.kodownapp[.]top, and tk.kodownapp[.]top, which likely support segmented operations, including those impersonating TikTok. This modularity and segmentation extends into the app’s technical design as well. To enable more advanced functionality while maintaining stealth, the malware goes beyond simple visual impersonation. It leverages the open-source tool ApkSignatureKillerEx to subvert Android’s native signature verification process, allowing the injection of a secondary payload (origin.apk) into the application’s directory. This effectively reroutes execution to malicious code while preserving the app’s appearance as a legitimate, properly signed package, both to the operating system and users. The app also implements sandbox evasion techniques beyond basic detection. It includes dedicated logic for identifying Genymotion, a popular research-focused emulator, as well as broader heuristics to detect generic emulated or virtualized environments. If emulation is confirmed, based on system properties, build fingerprints, or kernel parameters, the app does not terminate, but alters internal behavior to evade analysis. When primary C2 endpoints fail, the malware employs a fallback channel labeled as a crash reporting API: https://fb.fb07shdajkshdl[.]cc/open_api/crash_log. Despite its label, the domain facilitates exfiltration of telemetry and device metadata. Payloads captured from the TabTextApi() method include: This mechanism ensures that even if primary communication channels failed (e.g., fb.kodownapp[.]top became inaccessible), the malware still transmits useful telemetry for profiling, debugging, and command redirection. Following successful C2 communication, no immediate malicious activity was observed. This suggests that subsequent stages of the attack may be manually triggered by the operator, likely based on a real-time assessment of the infected device’s environment or perceived value. Such behavior is consistent with threat campaigns designed to evade automated sandbox analysis, reduce exposure, and selectively engage only with high-value targets. Further static code analysis revealed embedded references to cryptocurrency wallets and credential storage functions. However, none of these are actively used during dynamic testing. Some infrastructure endpoints remain responsive, while others appear offline, suggesting either temporary dormancy, geographic targeting, or staged activation tied to operator availability. Despite these limitations, the malware’s extensive permission abuse, modular backend design, and adaptive runtime behavior support a dual-purpose intent: monetizing traffic through ad fraud while silently collecting user and device intelligence for possible future exploitation. While we did not establish any confirmed link to a known threat group or specific active entity, several technical and contextual clues suggest a possible connection to Chinese-speaking operators. This remains a working hypothesis, not a definitive attribution. Supporting indicators include the consistent use of Simplified Chinese in source code and backend panel artifacts, infrastructure hosted by providers frequently seen in Chinese-origin threat activity (e.g., Alibaba Cloud, Zhejiang Taobao Network Co., Ltd.), and a development and monetization model consistent with Android ad fraud kits historically associated with financially motivated actors from the region. This activity also appears to align with a broader, well-established underground economy operating across Chinese-language darknet and clearnet platforms. Within this ecosystem, actors routinely exchange: Notably, many of these operators do not develop their capabilities independently. Instead, they rely on shared toolkits, malware-as-a-service offerings, and rented infrastructure, allowing them to scale quickly, operate discreetly, and obscure attribution. Such widespread availability of shared tools and services further complicates efforts to identify the origin or control structure behind campaigns like this one. The same service-based ecosystem that enables this kind of operational flexibility also allows a wide range of threat actors to launch impactful mobile malware campaigns without requiring advanced development capabilities. In this specific Android malware cluster, actors leverage low-friction distribution, brand impersonation, and aggressive permission abuse to deliver attacks that were both scalable and persuasive. Despite relying on relatively simple technical components, the campaign demonstrates adaptive behavior, enabling credential theft, sandbox evasion, and background data exfiltration. To mitigate such risks, users and organizations should enforce strict controls around app installation, limiting it to trusted sources such as the Google Play Store. Users should remain wary of unsolicited APKs delivered through messaging platforms, QR codes, or deceptive promotions, particularly those impersonating well-known brands or offering financial incentives. Ultimately, maintaining visibility into the mobile app supply chain and investing in user awareness are essential elements of a strong mobile security posture.Categories of Malicious APKs

Figure 1. Traffic redirection chain post-installation, via a fake Google Chrome browser app.
Figure 2. Credential-stealing apps mimicking legitimate services.
Figure 3. Local data harvesters requesting excessive permissions.
Figure 4. Task-based reward apps with monetization abuse.
Figure 5. Gambling apps exploiting legal and privacy loopholes. Brand Impersonation at Scale

Figure 6. Spoofed lure page triggering APK download.
Figure 7. Extract from AndroidManifest listing both real and spoofed permissions.
Figure 8. Screenshot of the impersonated Facebook UI post-installation.
Figure 9. Base64-encoded, AES-encrypted C2 configuration file.%20method.jpg?width=546&height=316&name=Figure%2010.%20Static%20key%20decryption%20logic%20inside%20AeTs.decryptA()%20method.jpg)
Figure 10. Static key decryption logic inside AeTs.decryptA() method
Figure 11. Decoded configuration file showing C2 infrastructure.%20is%20in%20Simplified%20Chinese%20and%20translates%20.jpg?width=568&height=468&name=Figure%2012.%20The%20warning%20message%20(%E7%94%A8%E6%88%B7%E4%BF%A1%E6%81%AF%E4%B8%BA%E7%A9%BA)%20is%20in%20Simplified%20Chinese%20and%20translates%20.jpg)
Figure 12. The warning message (用户信息为空) is in Simplified Chinese and translates to "User information is empty" / "No user information available".
Figure 13. Code reference to ApkSignatureKillerEx.
Figure 14. Sandbox detection functions adjusting internal behavior.

Figure 15. Code snippet illustrates fallback data exfiltration structure.
Figure 16. C2 response comparison between sandboxed and physical environments.Clues and Attribution

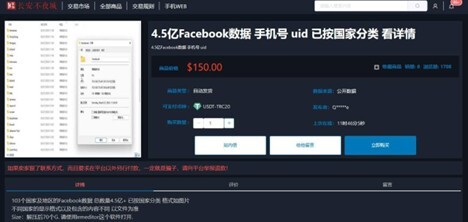
Figure 17. Chinese-language forum advertisement offering 450 million Facebook records.

Figure 18. Example of a mobile data dump shared by a Chinese-speaking underground actor.Conclusion and Recommendations
如有侵权请联系:admin#unsafe.sh