KAWA4096, a ransomware whose name includes "Kawa", the Japanese word for "river", first emerged in June 2025. This new threat features a leak site that follows the style of the Akira ransomware group, and a ransom note format similar to Qilin’s, likely an attempt to further enrich their visibility and credibility. In this blog post, we’ll share key insights from an analyzed KAWA4096 sample to uncover how this ransomware operates and what sets it apart.
Ransomware has remained highly active throughout 2025, with dozens of new groups emerging and causing disruptions across all vertical sectors. SpiderLabs’ remains at the forefront of monitoring new ransomware activity, and this work has uncovered one such newcomer identified as KAWA4096.

Figure 1. Spiderlabs global ransomware attack heat map monitoring.
Since its emergence in June 2025, KAWA4096 has claimed at least 11 victims, with the United States and Japan among its primary targets. Notably, five of these victims remain undisclosed on the group’s leak site.

Figure 2. Heat map for Kawa4096.

Figure 3. KAWA4096’s number of attacks and most targeted regions.

Figure 4. KAWA4096’s top affected countries.
KAWA4096’s ransomware features several capabilities, including the use of semaphores for multithreaded synchronization and the ability to encrypt files on shared network drives, highlighting a focus on maximizing impact while evading detection. In the next section, we’ll share the technical breakdown of KAWA4096 ransomware, examining its functionality in detail.
Technical Analysis
The KAWA4096 ransomware loads its configuration directly within the binary using the LoadResource API. The configuration contains details of the ransomware’s behavior, including a list of applications and services to terminate.

Figure 5. The ransomware configuration of KAWA4096.
Below are the structure and contents of its config:
|
Field
|
Description
|
|
skip_exts
|
File extensions to skip encrypting
|
|
skip_dirs
|
Directories to skip encrypting
|
|
skip_files
|
File names to skip encrypting
|
|
specify_dirs
|
Directories to encrypt
|
|
kill_process
|
Processes to terminate
|
|
kill_service
|
Services to terminate
|
|
Cmd
|
cmd commands to execute
|
|
cmd_post
|
Files to execute
|
|
Msg
|
Ransom note contents
|
|
msg_file_name
|
Ransom note filename
|
|
local_drives
|
<boolean> encrypt local drives
|
|
net_shares
|
<boolean> encrypt shared drives
|
|
self_delete
|
<boolean> delete itself after execution
|
|
thread_num
|
Number of threads
|
|
partial
|
Partial encryption
|
|
icon
|
Base64 data for icon of encrypted files
|
|
wallpaper
|
Base64 data for wallpaper
|
*For boolean values, it accepts the following values as true: 1, t, T, y, Y
The ransomware also lists the accepted command-line parameters.

Figure 6. KAWA4096 usage
|
Parameter
|
Description
|
|
d=<directory>
|
Encrypt specific directory
|
|
-all
|
Encrypt all valid files
|
|
-dump
|
Dump crash logs
|
If the ransomware is executed without any command-line parameters, it spawns a new process of itself with an “-all” parameter and terminates the original process. This ensures that its full functionality is triggered by default.

Figure 7. Re-execution of ransomware with -all parameter.
It then creates a mutex named SAY_HI_2025 to ensure that only a single instance of the ransomware is running, preventing multiple executions of the same binary.

Figure 8. Mutex creation.
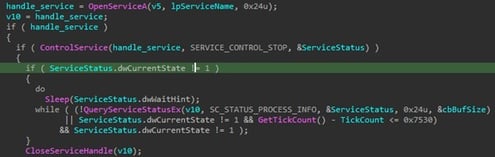
The ransomware also terminates specific services that are listed in its configuration. It uses Windows Service Control Manager (SCM) APIs to do this by opening the target service along with any of its dependent services. Then it sends a SERVICE_CONTROL_STOP command using the ControlService API to terminate it.

Figure 9. Termination of services.
Below is the list of services the ransomware attempts to terminate, which includes processes related to antivirus software, SQL servers, backup solutions, and SAP systems:
|
AcronisAgent
|
GxFWD
|
SAPHostControl
|
|
AcrSch2Svc
|
GXMMM
|
SAPHostExec
|
|
backup
|
GxVss
|
SAPService
|
|
BackupExecAgentAccelerator
|
GxVssHWProv
|
SavRoam
|
|
BackupExecAgentBrowser
|
Intuit.QuickBooks.FCS
|
sophos
|
|
BackupExecDiveciMediaService
|
memtas
|
sql
|
|
BackupExecJobEngine
|
mepocs
|
SQLWriter
|
|
BackupExecManagementService
|
MSExchange
|
stc_raw_agent
|
|
BackupExecRPCService
|
MSSQL$SQLEXPRESS
|
veeam
|
|
BackupExecVSSProvider
|
MVArmor
|
VeeamDeploymentService
|
|
CAARCUpdateSvc
|
MVarmor64
|
VeeamNFSSvc
|
|
CASAD2DWebSvc
|
mysql
|
VeeamTransportSvc
|
|
ccEvtMgr
|
PDVFSService
|
VMAuthdService
|
|
ccSetMgr
|
QBCFMonitorService
|
VSNAPVSS
|
|
DefWatch
|
QBDBMgrN
|
vss
|
|
GxBlr
|
QBFCService
|
WSBExchange
|
|
GxCIMgr
|
QBIDPService
|
YooBackup
|
|
GxClMgrS
|
RTVscan
|
YooIT
|
|
GxCVD
|
SAP
|
|
The ransomware also creates a dedicated thread that continuously monitors and terminates specific processes based on its configuration. If a matching process is found, it is terminated using the TerminateProcess API. This loop runs throughout the ransomware execution, preventing the victim from reopening any of the targeted applications while the malware is active.
Below is the list of applications the ransomware terminates:
|
agntsvc.exe
|
mspub.exe
|
sqlbrowser.exe
|
|
avagent.exe
|
mydesktopqos.exe
|
sqlservr.exe
|
|
avscc.exe
|
mydesktopservice.exe
|
sqlwriter.exe
|
|
bedbh.exe
|
notepad.exe
|
steam.exe
|
|
benetns.exe
|
ocautoupds.exe
|
synctime.exe
|
|
bengien.exe
|
ocomm.exe
|
tbirdconfig.exe
|
|
beserver.exe
|
ocssd.exe
|
TeamViewer.exe
|
|
CagService.exe
|
onenote.exe
|
TeamViewer_Service.exe
|
|
cvd.exe
|
oracle.exe
|
thebat.exe
|
|
cvfwd.exe
|
outlook.exe
|
thunderbird.exe
|
|
CVMountd.exe
|
powerpnt.exe
|
tv_w32.exe
|
|
CVODS.exe
|
pvlsvr.exe
|
tv_x64.exe
|
|
dbeng50.exe
|
QBCFMonitorService.exe
|
VeeamDeploymentSvc.exe
|
|
dbsnmp.exe
|
QBDBMgrN.exe
|
VeeamNFSSvc.exe
|
|
DellSystemDetect.exe
|
QBIDPService.exe
|
VeeamTransportSvc.exe
|
|
encsvc.exe
|
raw_agent_svc.exe
|
visio.exe
|
|
EnterpriseClient.exe
|
SAP.exe
|
vsnapvss.exe
|
|
excel.exe
|
saphostexec.exe
|
vxmon.exe
|
|
firefox.exe
|
saposcol.exe
|
winword.exe
|
|
infopath.exe
|
sapstartsrv.exe
|
wordpad.exe
|
|
isqlplussvc.exe
|
sqbcoreservice.exe
|
xfssvccon.exe
|
|
msaccess.exe
|
sql.exe
|
|
It also deletes shadow copies by using Windows Management Instrumentation (WMI) to run a command through Win32_Process::Create to execute the command specified in the ransomware’s configuration
vssadmin.exe Delete Shadows /all /quiet
wmic shadowcopy delete /nointeractive
Encryption
The ransomware utilizes semaphores and multi-threading to maximize its encryption efficiency across the infected system.
- It spawns multiple threads for file handling and encryption
- The number of threads depends on the value of “thread_num” in the ransomware configuration (in this sample, it is set to spawn 10 threads)

Figure 10. Creation of threads.
Once the threads are initialized, the ransomware recursively scans directories to identify files that match its encryption criteria.

Figure 11. Function used to recursively scan directories.
During scanning, it skips certain files based on the ransomware configuration. These include:
Files with the following extensions:
|
.ani
|
.ico
|
.mui
|
|
.bat
|
.ics
|
.nomedia
|
|
.cab
|
.idx
|
.ocx
|
|
.cmd
|
.iso
|
.prf
|
|
.cpl
|
.key
|
.rom
|
|
.cur
|
.ldf
|
.rtp
|
|
.dia2gcab
|
.lnk
|
.scr
|
|
.diagpkg
|
.mod
|
.shs
|
|
.dll
|
.mpa
|
.spl
|
|
.drv
|
.msc
|
.sys
|
|
.exe
|
.msi
|
.theme
|
|
.hlp
|
.msp
|
.themepack
|
|
.icl
|
.msstyles
|
.ttf
|
|
.icns
|
.msu
|
|
Files in specific directories:
All Users
PerfLogs
Program Files (x86)
Program Files
cpqsystem
Windows.old
Windows
ProgramData
$Recycle.bin
System Volume Information
Boot
Bootmgr
font
azagent
Packages
kworking
Files with the following filenames:
boot.ini
desktop.ini
ntuser.dat
ntuser.ini
bootmgr
thumbs.db
autorun.inf
After identifying valid files, the ransomware adds them to a shared queue. This queue is processed by a pool of worker threads, each responsible for retrieving file paths and passing it on to the encryption routine. A semaphore is used for synchronization among threads, ensuring efficient processing of the file queue.

Figure 12. Function for worker threads.
The ransomware also changes the icons of encrypted files to one that is similar to the “SQL Monitor” icon. It also has the capability to modify the victim's desktop wallpaper, potentially displaying a ransom note or warning. However, the analyzed sample sets the wallpaper to just a solid black screen based on its configuration.

Figure 13. Sample of encrypted files.
If self delete is set to true, it will delete itself using the following command after encryption:
cmd.exe /C ping 127.0.0.1 -n 2 > nul && del /F <ransom filepath>
Ransom Note and Data Leak Site
Kawa4096 drops the following ransom note. Notably, the contents are nearly identical to the ransom note used by the Qilin ransomware, with only minor changes to the formatting and text.
%20vs%20QILIN%20(right)%20ransom%20note.jpg?width=661&height=204&name=Figure%2014.%20KAWA4096%20(left)%20vs%20QILIN%20(right)%20ransom%20note.jpg)
Figure 14. KAWA4096 (left) vs QILIN (right) ransom note.
On its data leak site, KAWA4096 adopts a design and content structure that closely mirrors the Akira ransomware group’s site. The site features a green-on-black terminal style interface with the opening statements almost identical to Akira’s, with only minor wording and formatting differences. These design and content similarities are likely aimed at boosting the group’s visibility and credibility by modeling themselves after established ransomware operations.
%20vs%20AKIRA%20(right)%20data%20leak%20site.jpg?width=624&height=188&name=Figure%2015.%20KAWA4096%20(left)%20vs%20AKIRA%20(right)%20data%20leak%20site.jpg)
Figure 15. KAWA4096 (left) vs AKIRA (right) data leak site.
Although no clear information on its TTPs or connections to other known ransomware groups is currently available, organizations should continue to apply strong security practices and monitor the behaviors and techniques uncovered in this analysis.
Trustwave Detection of KAWA4096
Trustwave ISA and Trustwave SpiderLabs provide a set of detection rules capturing impact and defense evasion techniques listed in this blog as well as other common methods used by ransomware operators. Here are some of the procedures that can be detected by these use cases:
vssadmin.exe Delete Shadows /all /quiet
wmic shadowcopy delete /nointeractive
wevtutil cl Application
wevtutil cl system
wevtutil cl security
Additionally, Trustwave's Advanced Continual Threat Hunt (ACTH) with a new patent-pending methodology enables Trustwave to conduct threat hunts for potential malware and malicious activities.
IOCs
|
Name
|
Type
|
Hash
|
|
C3CE46D40.exe
|
Win64 EXE
|
sha1: bd30c87774c083a1003c0b9fb0a922b702302272
sha256: f3a6d4ccdd0f663269c3909e74d6847608b8632fb2814b0436a4532b8281e617
md5: c3ce46d40b2893e30bf00fce72c2e1fa
|
|
kawa.exe
|
Win64 EXE
|
sha1: b8c32444ceef027fb65d9cf1c823ad3c9c59acea
sha256: fadfef5caf6aede2a3a02a856b965ed40ee189612fa6fde81a30d5ed5ee6ae7d
md5: 64756bf452baa4da411e3a835c08d884
|
TOR
hxxp://kawasa2qo7345dt7ogxmx7qmn6z2hnwaoi3h5aeosupozkddqwp6lqqd[.]onion/
Email: [email protected]
QTox ID
6A340207246B47E37F6D094D2236E5C6242B6E4461EEF8021FED2C9855240C3E11AEE886FAAF













%20vs%20QILIN%20(right)%20ransom%20note.jpg?width=661&height=204&name=Figure%2014.%20KAWA4096%20(left)%20vs%20QILIN%20(right)%20ransom%20note.jpg)
%20vs%20AKIRA%20(right)%20data%20leak%20site.jpg?width=624&height=188&name=Figure%2015.%20KAWA4096%20(left)%20vs%20AKIRA%20(right)%20data%20leak%20site.jpg)