
微软在2025年7月的补丁更新中修复了128个CVE漏洞,其中包括一个零日信息泄露漏洞(CVE-2025-49719),影响SQL Server。此外还修复了多个关键远程代码执行(RCE)和权限提升(EoP)漏洞,并建议用户尽快更新以降低风险。 2025-7-8 17:47:41 Author: www.tenable.com(查看原文) 阅读量:42 收藏

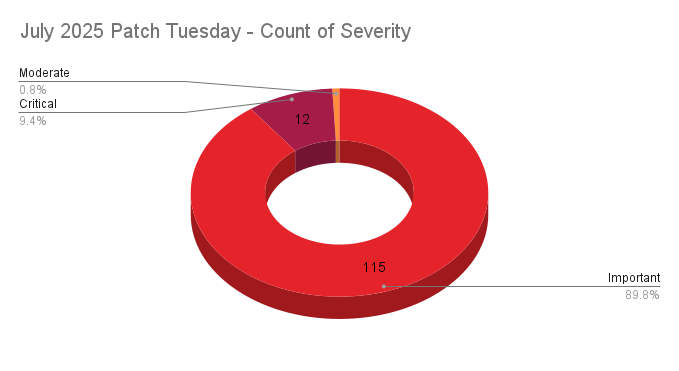
- 12Critical
- 115Important
- 1Moderate
- 0Low
Microsoft addresses 128 CVEs, including one zero-day vulnerability that was publicly disclosed.
Microsoft addresses 128 CVEs in its July 2025 Patch Tuesday release, with 12 rated critical, and 115 rated important and one rated as moderate. Our counts omitted nine vulnerabilities reported by AMD and MITRE.
This month’s update includes patches for:
- Azure Monitor Agent
- Capability Access Management Service (camsvc)
- HID class driver
- Kernel Streaming WOW Thunk Service Driver
- Microsoft Brokering File System
- Microsoft Graphics Component
- Microsoft Input Method Editor (IME)
- Microsoft Intune
- Microsoft MPEG-2 Video Extension
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office PowerPoint
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft PC Manager
- Microsoft Teams
- Microsoft Windows QoS scheduler
- Microsoft Windows Search Component
- Office Developer Platform
- Remote Desktop Client
- Role: Windows Hyper-V
- SQL Server
- Service Fabric
- Storage Port Driver
- Universal Print Management Service
- Virtual Hard Disk (VHDX)
- Visual Studio
- Visual Studio Code Python extension
- Windows Ancillary Function Driver for WinSock
- Windows AppX Deployment Service
- Windows BitLocker
- Windows Connected Devices Platform Service
- Windows Cred SSProvider Protocol
- Windows Cryptographic Services
- Windows Event Tracing
- Windows Fast FAT Driver
- Windows GDI
- Windows Imaging Component
- Windows KDC Proxy Service (KPSSVC)
- Windows Kerberos
- Windows Kernel
- Windows MBT Transport driver
- Windows Media
- Windows NTFS
- Windows Netlogon
- Windows Notification
- Windows Performance Recorder
- Windows Print Spooler Components
- Windows Remote Desktop Licensing Service
- Windows Routing and Remote Access Service (RRAS)
- Windows SMB
- Windows SPNEGO Extended Negotiation
- Windows SSDP Service
- Windows Secure Kernel Mode
- Windows Shell
- Windows SmartScreen
- Windows StateRepository API
- Windows Storage VSP Driver
- Windows TCP/IP
- Windows TDX.sys
- Windows Universal Plug and Play (UPnP) Device Host
- Windows Update Service
- Windows User-Mode Driver Framework Host
- Windows Virtualization-Based Security (VBS) Enclave
- Windows Visual Basic Scripting
- Windows Win32K GRFX
- Windows Win32K ICOMP
- Workspace Broker
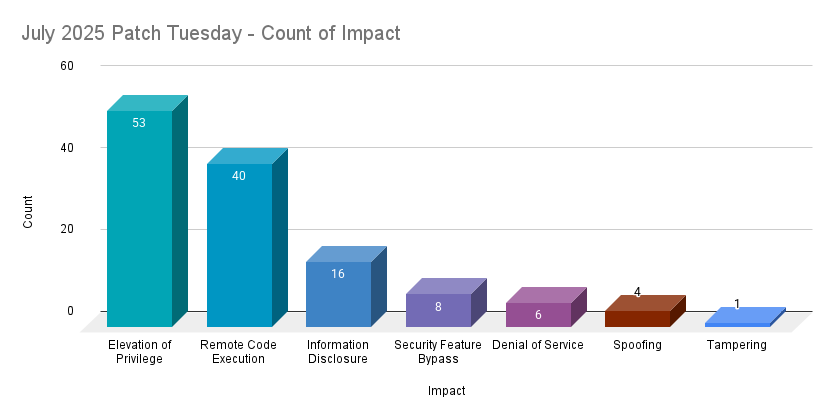
Elevation of Privilege (EoP) vulnerabilities accounted for 41.4% of the vulnerabilities patched this month, followed by Remote Code Execution (RCE) vulnerabilities at 31.3%.
CVE-2025-49719 | Microsoft SQL Server Information Disclosure Vulnerability
CVE-2025-49719 is a zero-day information disclosure vulnerability in Microsoft SQL Server. It was assigned a CVSSv3 score of 7.5 and is rated important. An unauthenticated attacker could exploit this vulnerability to obtain uninitialized memory. It is assessed as “Exploitation Less Likely” according to Microsoft’s Exploitability Index.
According to Microsoft, this vulnerability was publicly disclosed prior to patches being available. Users of SQL Server are advised to update to the latest version, which includes driver fixes. If users are running their own applications or software from another vendor that uses SQL Server, it is advised to update to Microsoft OLE DB Driver for SQL Server version 18 or 19. However, it is important to ensure compatibility before updating. For more information on general distribution release (GDR) or cumulative update (CU) versions, please refer to the advisory.
CVE-2025-47981 | SPNEGO Extended Negotiation (NEGOEX) Security Mechanism Remote Code Execution Vulnerability
CVE-2025-47981 is a RCE in the SPNEGO Extended Negotiation (NEGOEX) Security Mechanism. It was assigned a CVSSv3 score of 9.8 and is rated critical. It is assessed as "Exploitation More Likely." An unauthenticated, remote attacker could exploit this flaw by sending a specially crafted message to a vulnerable server. Successful exploitation could grant an attacker RCE privileges. Microsoft states that this vulnerability only affects Windows machines 10 version 1607 and above because of a specific group policy object (GPO) enabled by default in these versions, Network security: Allow PKU2U authentication requests to this computer to use online identities.
This is only the third vulnerability in SPNEGO NEGOEX since 2022, but it is the second in 2025, as CVE-2025-21295 was addressed in the January 2025 Patch Tuesday release. Both CVE-2025-47981 and CVE-2025-21295 were disclosed by security researcher Yuki Chen.
CVE-2025-49701 and CVE-2025-49704 | Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2025-49701 and CVE-2025-49704 are RCE vulnerabilities in Microsoft SharePoint. They were both assigned a CVSSv3 score of 8.8 and CVE-2025-49704 was rated as critical while CVE-2025-49701 was rated as important. To exploit these flaws, an attacker would need to be authenticated with Site Owner privileges at minimum. Once authenticated, an attacker could write arbitrary code to a vulnerable SharePoint Server to gain RCE.
So far in 2025, there have been 16 vulnerabilities disclosed in Microsoft SharePoint, including CVE-2025-49706, a spoofing flaw that was disclosed alongside CVE-2025-49701 and CVE-2025-49704. There were 20 SharePoint vulnerabilities in 2024, 25 in 2023, and 20 in 2022.
CVE-2025-49735 | Windows KDC Proxy Service (KPSSVC) Remote Code Execution Vulnerability
CVE-2025-49735 is an RCE vulnerability affecting Windows Kerberos Key Distribution Center (KDC) proxy service, an authentication mechanism used for KDC servers over HTTPS. It was assigned a CVSSv3 score of 8.1 and rated critical. An unauthenticated attacker could exploit this vulnerability utilizing a crafted application to exploit a cryptographic protocol vulnerability in order to execute arbitrary code.
According to the advisory, this only impacts Windows Servers that have been “configured as a [MS-KKDCP]: Kerberos Key Distribution Center (KDC) Proxy Protocol server.” While the advisory does mention that exploitation requires the attacker to win a race condition, this vulnerability was still assessed as “Exploitation More Likely.”
This is the second month in a row that Microsoft has patched a KDC Proxy Service (KPSSVC) RCE vulnerability, as it was preceded by CVE-2025-33071 in the June Patch Tuesday release. Both flaws are credited to security researcher “ʌ!ɔ⊥ojv” with Kunlun Lab.
CVE-2025-49724 | Windows Connected Devices Platform Service Remote Code Execution Vulnerability
CVE-2025-49724 is a RCE vulnerability in the Windows Connected Devices Platform Service. It was assigned a CVSSv3 score of 8.8 and is rated important. An unauthenticated, remote attacker could exploit this vulnerability by sending specially crafted data packets to a system with the “Nearby Sharing” feature enabled. Microsoft’s advisory notes that the “Nearby Sharing” feature is not enabled by default.
This is the third vulnerability in the Windows Connected Devices Platform Service since 2022. Earlier this year, Microsoft patched CVE-2025-21207, a denial of service flaw in the service. In 2022, Microsoft patched CVE-2022-30212, an information disclosure flaw as part of its July 2022 Patch Tuesday release.
Tenable Solutions
A list of all the plugins released for Microsoft’s July 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's July 2025 Security Updates
- Tenable plugins for Microsoft July 2025 Patch Tuesday Security Updates
Join Tenable's Research Special Operations (RSO) Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

Research Special Operations
The Research Special Operations (RSO) team serves as Tenable’s Forward Logistics Element in the threat landscape, providing customers with the analyses and contextualized exposure intelligence required to manage risks to critical business assets. With over 150 years of collective expertise, this hand-picked group of world-class security researchers is united with one mission: to cut through the noise and deliver critical intelligence about the most dangerous cyber threats emerging right now. Uniting the missions of the Tenable Security Response, Zero-Day Research, and Decision Science Operations teams, RSO disseminates timely, accurate, and actionable information about the latest threats and exposures.
- Exposure Management
- Vulnerability Management
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
如有侵权请联系:admin#unsafe.sh