全球网络攻击激增,每天超6亿次。应对需全行业协作,从传统安全转向多层次防御策略,并利用AI与自动化实现主动防护。文章推荐构建统一安全运营中心,整合数据与AI能力,提升威胁预防、检测与响应效率,降低风险。 2025-7-7 16:0:0 Author: www.microsoft.com(查看原文) 阅读量:6 收藏
The sheer volume of cyberattacks continues to increase at a breathtaking scale worldwide, with customers facing more than 600 million cybercriminal and nation-state attacks every day.1 To stem the growing tide of malicious cyber activity takes a commitment from all of us—individuals from operations to the executive level, security teams, organizations, industry leaders, and governments. It also requires a shift from traditional security approaches to a defense-in-depth strategy that deploys security tools that natively work together to coordinate defense across security layers.
Organizations also need to embrace AI and automation, moving away from manual, reactive security to an automated, proactive defense. But the transition is easier said than done. For most organizations, this transition will require significant effort that spans not just technology, but people and processes too. To help organizations make the move beyond silos to an integrated, defense-in-depth approach, we’re sharing a new e-book—our introduction to building a coordinated defense. In this post, we walk through the key content you can find in the e-book and share more resources on integrated cyberthreat protection.
Recommendations built on real-world lessons
Bad actors are increasingly adept at finding and exploiting weaknesses, especially in legacy infrastructure. The Coordinated Defense e-book was crafted through our own lessons learned in real-world scenarios, as well as our work to help customers defend their own organizations. The e-book can help security teams better understand how a unified solution can improve their ability to defend their increasingly complex and diverse digital environments and:
- Stop fighting fires and become more proactive through streamlined threat hunting, triage, and investigation.
- Adopt a continuous threat exposure management approach that addresses the most critical security domains, including endpoints, identities, and cloud-native applications.
- Accelerate security operations (SecOps) to lower mean time to resolution (MTTR).
Unified security operations
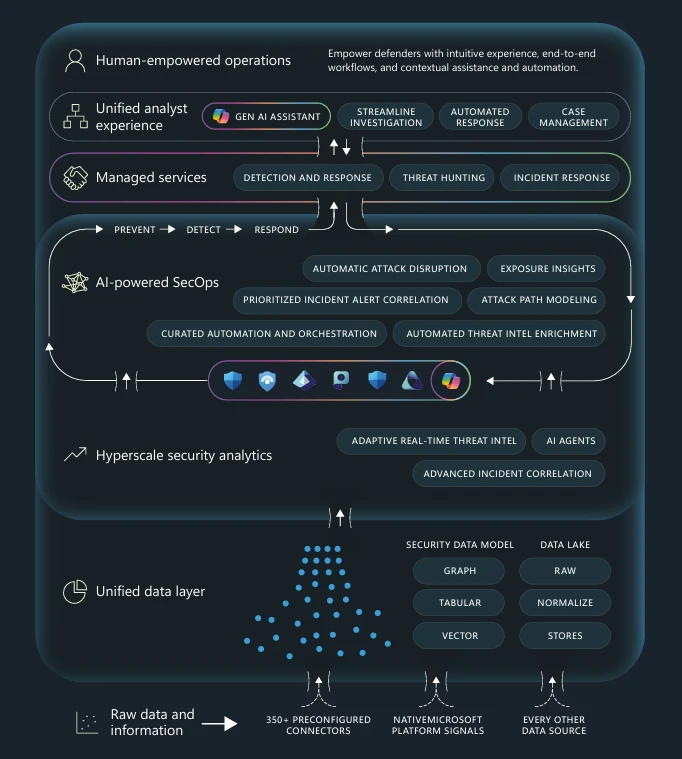
In the e-book, we expand on a new pre-breach/post-breach paradigm that helps organizations shift from reactive and manual processes to an AI-powered, continuous, and autonomous security posture as they prevent, detect, and respond to cyberthreats—unified security operations.
By integrating endpoints, identities, email, apps, data, and cloud environments with the critical security operations functions, including posture management, detection and response, and threat intelligence, security teams can shift from reactive to proactive security. The e-book outlines the unified architecture that can transform security operations by centralizing data and leveraging AI to enhance existing human expertise.

Figure 1. Diagram of unified security operations center (SOC) architecture that integrates data, AI, and human expertise to empower security teams to prevent, detect, and respond to threats seamlessly across the entire lifecycle.
Addressing the complete threat lifecycle
From preventing initial compromise, to detecting and disrupting active cyberattacks, to investigating and responding to incidents, the e-book explains how unifying security operations allows teams to build a closed-loop approach that improves business resiliency and continuously lowers the risk of a breach. The benefits span the lifecycle and include:
- Prevent—Prioritized risk mitigation, reduced attack surface, proactive gap identification, and enhanced resilience.
- Detect—Rapid ransomware response, real-time threat isolation, predictive threat intelligence, and more.
- Respond—A single, prioritized incident queue, automatically correlated alerts, and relevant threat intelligence that helps prioritize cyberthreats based on severity.
Read the e-book to learn more about how AI assistants like Microsoft Security Copilot can enhance unified security by providing valuable insights, automating routine tasks, and correlating alerts into comprehensive incidents.
Tackling your most critical security domains
Unifying security across all areas of your environment can strengthen defenses in each area. To create a truly effective security posture, organizations need to protect endpoints and identities, secure cloud-native applications, protect the entire organization with both security information and event management (SIEM) and extended detection and response (XDR), and protect the data. In the e-book, each domain is discussed in detail with a scenario that models cyberattacker actions, the response of a unified security approach, and the improved outcomes. The e-book also includes information on:
- Endpoint protection—Critical trends shaping endpoint security and strategies to counter ransomware and malware threats.
- Identity protection—Emerging identity-based cyberthreats and how united defenses can prevent account takeovers.
- Securing cloud-native applications—Insights into cloud vulnerabilities and best practices for securing modern application environments.
- Integrating SIEM and XDR—Integrated tools that help address advanced, persistent threats and reduce false positives.
- Protecting your data—Key challenges in safeguarding sensitive data and mitigating insider risks effectively.
Getting started
A unified SOC architecture is imperative to help organizations face the current and future security challenges. Shifting to a proactive, integrated defense means breaking down the barriers between security functions and working across silos. It means embracing and enabling AI-powered automation across your environment. And it allows for a continuous loop of protection and improvement that security teams need to operate faster, smarter, and more resiliently. To get started on a more integrated, defense-in-depth approach to security, read the Coordinated Defense: Building an AI-powered, unified SOC e-book now.
Learn more about AI-powered, unified SecOps from Microsoft to improve your security posture across hybrid environments with unified exposure management and built-in, natively integrated security controls.
Discover even more resources: Integrated Cyberthreat Protection Resources.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and X (@MSFTSecurity) for the latest news and updates on cybersecurity.
如有侵权请联系:admin#unsafe.sh