这篇文章介绍了如何使用Scapy工具在Kali Linux上进行IP地址欺骗技术的学习与应用。通过创建和发送带有伪造源地址的数据包,安全专业人士可以进行合法的渗透测试和拒绝服务攻击漏洞评估。文章详细讲解了Scapy的安装、配置以及基本和高级的IP地址欺骗技巧,并强调了在实际应用中需遵循的安全测试最佳实践和伦理法律要求。 2025-7-3 17:40:41 Author: www.blackmoreops.com(查看原文) 阅读量:13 收藏
Learning to spoof IP address techniques represents a fundamental skill in cybersecurity testing and network analysis. Using Scapy on Kali Linux, security professionals can craft packets with customised source addresses for legitimate penetration testing and DoS vulnerability assessment. This comprehensive guide explores how to spoof IP address configurations safely and ethically for educational security testing purposes.
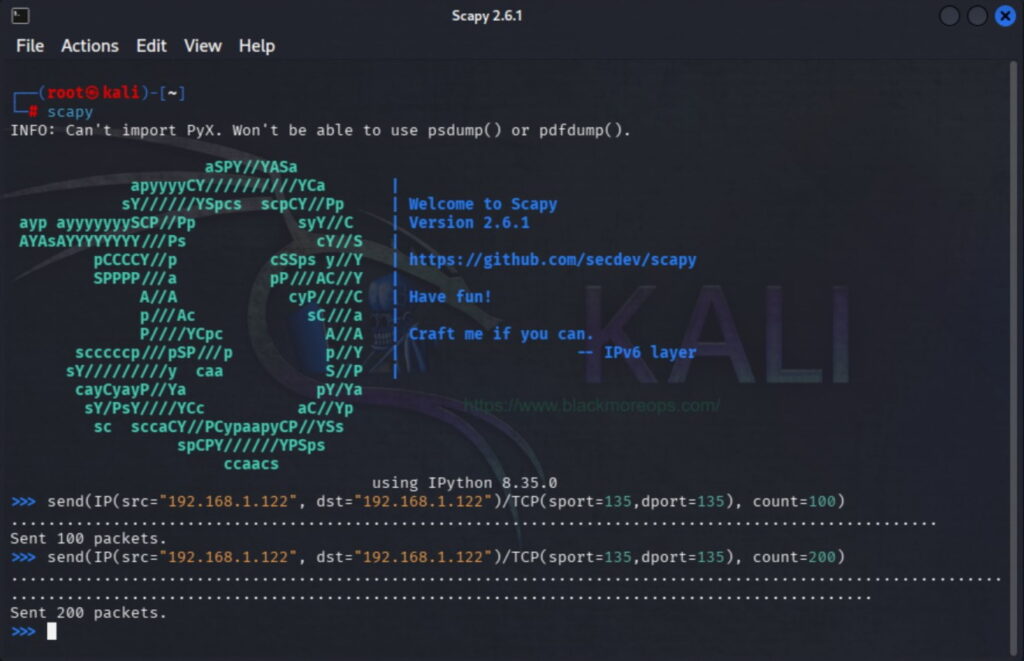
Screenshot showing IP addressing spoofing with scapy on Kali Linux and Denial of Service (DoS) attack on a destination IP address.
Why Spoof IP Address
The ability to spoof IP address settings provides crucial advantages in hacking and cyber security testing scenarios. Unlike traditional tools such as Nmap and Hping3, Scapy offers virtually unlimited customisation capabilities for address spoofing and packet manipulation. When you spoof IP address information correctly, you can simulate various attack vectors, test firewall configurations, and assess network security implementations.
Understanding how to spoof IP address techniques enables security professionals to identify vulnerabilities that might otherwise remain hidden. The learning curve for mastering address spoofing may seem steep initially, but the investment proves worthwhile. Where traditional C programs might require 60 lines to describe a spoofed packet, Scapy accomplishes the same in a single line. In fact, 90% of network probing tools can be rewritten in just 2 lines of Scapy code when implementing address spoofing techniques.
Understanding IP Address Spoofing Fundamentals
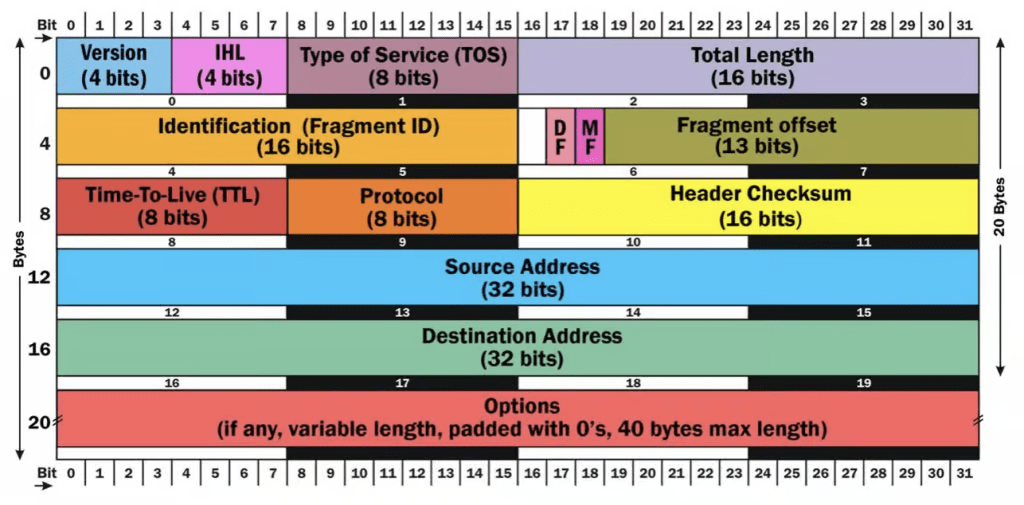
Before implementing techniques to spoof IP address configurations, understanding TCP/IP fundamentals proves crucial. The IP header structure described RFC 791 in contains vital fields that enable address manipulation, including version, header length, type of service, total length, identification, flags, fragment offset, time to live (TTL), protocol, header checksum, source address, and destination address.
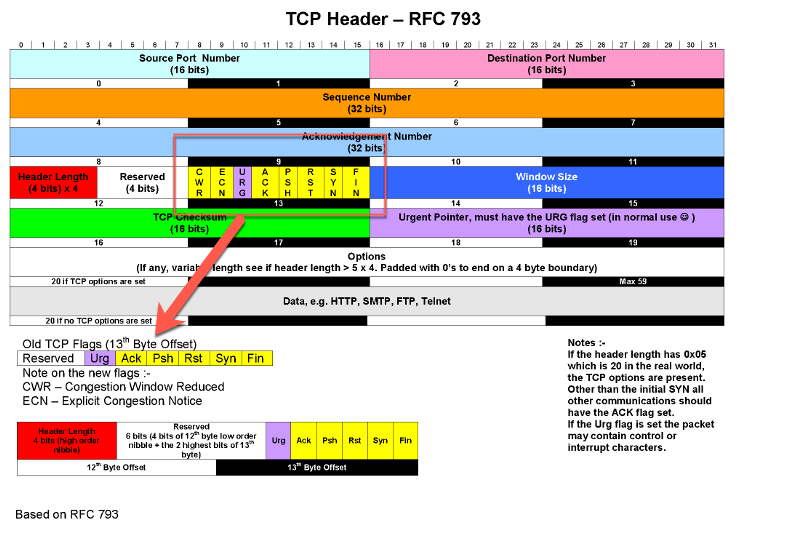
When you spoof IP address information, you’re essentially modifying the source address field to appear as though packets originate from different systems. This technique becomes particularly important when testing how network security devices respond to traffic from various sources. Similarly, the TCP header described in RFC 793 encompasses sequence numbers, acknowledgement numbers, header length, flags (URG, ACK, PSH, RST, SYN, FIN), window size, checksum, urgent pointer, and options. Mastering these structures enables effective address spoofing for sophisticated security testing scenarios.
Getting Started with Scapy
Installation and Initial Setup
Launch Kali Linux and open a terminal to begin your Scapy packet manipulation:
┌──(root㉿kali)-[~]
└─# scapy
INFO: Can't import PyX. Won't be able to use psdump() or pdfdump().
aSPY//YASa
apyyyyCY//////////YCa |
sY//////YSpcs scpCY//Pp | Welcome to Scapy
ayp ayyyyyyySCP//Pp syY//C | Version 2.6.1
AYAsAYYYYYYYY///Ps cY//S |
pCCCCY//p cSSps y//Y | https://github.com/secdev/scapy
SPPPP///a pP///AC//Y |
A//A cyP////C | Have fun!
p///Ac sC///a |
P////YCpc A//A | We are in France, we say Skappee.
scccccp///pSP///p p//Y | OK? Merci.
sY/////////y caa S//P | -- Sebastien Chabal
cayCyayP//Ya pY/Ya |
sY/PsY////YCc aC//Yp
sc sccaCY//PCypaapyCP//YSs
spCPY//////YPSps
ccaacs
using IPython 8.35.0
>>>
The triple-angle prompt (>>>) indicates Scapy’s interactive mode, where all subsequent commands will be interpreted by the Scapy engine.
Exploring Configuration Settings
View Scapy’s configuration by typing:
>>> conf ASN1_default_codec = <ASN1Codec BER[1]> ASN1_default_long_size = 0 AS_resolver = <scapy.as_resolvers.AS_resolver_multi object at 0x7fe6fdc5d940> BTsocket = <BluetoothRFCommSocket: read/write packets on a connected L2CAP... L2listen = <L2ListenSocket: read packets at layer 2 using Linux PF_PACKET ...
This configuration output reveals Scapy’s extensive settings, including socket configurations, protocol definitions, and interface parameters essential for advanced Scapy packet manipulation.
Basic IP Address Spoofing and Packet Creation
Creating Your First Spoofed Packet
To spoof IP address information effectively, begin with creating custom packets where the source address differs from your actual system address. The fundamental principle involves defining a variable representing your packet, then configuring specific spoofed attributes layer by layer. Scapy’s flexible architecture allows stacking any protocols in any combination, even unconventional configurations like 802.1q layers over TCP.
>>> x=IP(ttl=64) >>> x <IP ttl=64 |>
This creates an IP packet with a Time To Live (TTL) value of 64. Now spoof IP address information by setting custom source and destination addresses:
>>> x.src="192.168.1.101" >>> x.dst="192.168.1.122" >>> x <IP ttl=64 src=192.168.1.101 dst=192.168.1.122 |>
Your spoofed packet now contains:
- TTL: 64
- Spoofed Source IP: 192.168.1.101
- Destination IP: 192.168.1.122
This demonstrates the basic technique to spoof IP address information, making packets appear to originate from 192.168.1.101 regardless of your actual system’s IP address.
Advanced IP Address Spoofing Techniques
Scapy excels at advanced methods to spoof IP address information in complex multi-layer packets. For instance, creating additional packets with different spoofed sources:
>>> IP() <IP |> >>> a=IP(dst="172.16.1.40") >>> a <IP dst=172.16.1.40 |> >>> a.dst '172.16.1.40' >>> a.ttl 64
Create sophisticated spoofed packet combinations targeting multiple destinations with varying TTL values:
>>> Ether(dst="ff:ff:ff:ff:ff:ff")/IP(dst=["sample.com","test.com"],ttl=(1,9))/UDP()
This single line generates 18 packets (2 destinations × 9 TTL values), demonstrating Scapy’s power for efficient address spoofing and packet generation.
Exploring Built-in Functions
Scapy provides numerous built-in functions that demonstrate its comprehensive packet manipulation capabilities. View the complete function library:
>>> lsc() IPID_count : Identify IP id values classes in a list of packets arp_mitm : ARP MitM: poison 2 target's ARP cache arpcachepoison : Poison targets' ARP cache arping : Send ARP who-has requests to determine which hosts are up arpleak : Exploit ARP leak flaws, like NetBSD-SA2017-002 bind_layers : Bind 2 layers on some specific fields' values bridge_and_sniff : Forward traffic between interfaces if1 and if2, sniff and return
These functions showcase Scapy’s versatility, enabling everything from basic network discovery to sophisticated multi-layer protocol analysis. Notable functions include sr() for send-and-receive operations, sniff() for packet capture, traceroute() for path analysis, and wrpcap() for saving packet captures.
Advanced Packet Transmission Techniques
Basic Packet Transmission
Transmit your crafted packet using the send() function:
>>> send(x) . Sent 1 packets.
This demonstrates successful Scapy packet manipulation by sending your custom packet to the specified destination address (192.168.1.122) with the configured TTL and source address.
Scapy’s Decoding Philosophy: Raw Facts in Address Spoofing
A crucial advantage when learning to spoof IP address information lies in Scapy’s commitment to providing raw facts rather than potentially biased interpretations. Traditional tools often confuse decoding with interpreting—stating “port 80 is closed” instead of “received TCP Reset on port 80.” While interpretations might seem helpful for beginners, they introduce bias and potential inaccuracies, particularly when analysing responses to spoofed traffic.
For instance, some scanners report “filtered TCP port” when receiving ICMP destination unreachable packets. This interpretation may be correct in firewall scenarios but wrong when no host exists to forward packets—especially relevant when testing with spoofed source addresses. Techniques to spoof IP address information avoid such assumptions, delivering complete decoded information that enables users to form their own conclusions about spoofed traffic responses.
This approach proves invaluable for experienced security professionals who need complete packet information when implementing address spoofing. Rather than reverse-engineering tool interpretations to determine underlying facts, Scapy provides comprehensive raw data from spoofed packet interactions from the outset. You can examine TCP port scan results using spoofed sources for both connectivity status and packet characteristics like TTL values or Ethernet padding without additional probing.
Creating DoS Attack Scenarios with IP Spoofing
For educational purposes, learning to spoof IP address configurations enables simulation of various DoS attack scenarios that test system responses. The tool’s flexibility allows creation of precisely crafted packets using spoofed addresses that target specific vulnerabilities:
>>> send(IP(src="192.168.1.101", dst="192.168.1.122")/TCP(sport=135,dport=135), count=2000)
This command demonstrates advanced techniques to spoof IP address information by creating a “land attack”—packets with identical spoofed source and destination addresses and ports. This particular method to spoof IP address characteristics has historically proven effective against certain Windows Server 2003 systems. The command structure includes:
-
send: The packet transmission functionIP(src="192.168.1.101", dst="192.168.1.122"): IP layer where we spoof IP address to match destinationTCP(sport=135,dport=135): TCP layer with identical port numbers
count=2000: Quantity of spoofed packets to transmit
When directed at vulnerable systems, these spoofed packets can cause significant performance degradation or system crashes, demonstrating why understanding how to spoof IP address techniques proves crucial for security testing.
Session Management and Packet Persistence
Scapy packet manipulation includes sophisticated session management capabilities. You can save and restore working sessions, maintaining packet definitions across multiple analysis sessions:
# ./run_scapy -s mysession New session [mysession] Welcome to Scapy (2.4.0) >>> target="www.target.com/30" >>> ip=IP(dst=target) >>> ip <IP dst=<Net www.target.com/30> |> >>> [p for p in ip] [<IP dst=207.171.175.28 |>, <IP dst=207.171.175.29 |>, <IP dst=207.171.175.30 |>, <IP dst=207.171.175.31 |>]
This functionality enables complex multi-stage testing scenarios where packet definitions can be refined and reused across multiple testing sessions.
Versatile Applications of IP Address Spoofing
The ability to spoof IP address information extends far beyond basic packet creation, serving as a comprehensive technique for multiple specialised security testing scenarios. Scapy can effectively facilitate address spoofing for hping, arpspoof, arp-sk, arping, p0f, and portions of Nmap, tcpdump, and tshark functionality. This versatility makes techniques to spoof IP address invaluable for:
- ARP Spoofing and Cache Poisoning: Advanced techniques combining VLAN hopping with spoofed ARP manipulation
- Wireless Security Testing: Injecting custom 802.11 frames using spoofed MAC and IP addresses
- VoIP Analysis: Decoding voice communications with spoofed addressing even on WEP-encrypted channels
- Invalid Frame Injection: Testing system responses to malformed packets with spoofed origins
- Multi-technique Combinations: Sophisticated attack chains using spoofed addresses that traditional tools cannot execute
- Custom Protocol Development: Creating bespoke network protocols with flexible address spoofing
The “Probe Once, Interpret Many” Philosophy
Unlike traditional tools that provide limited interpretations, methods to spoof IP address information follow a “probe once, interpret many” approach. After conducting a scan or traceroute using spoofed addresses, you receive complete decoded packets before any interpretation occurs. This enables multiple analyses of the same spoofed traffic dataset from different perspectives—examining a TCP port scan for both port status and TTL patterns without additional probing.
Intelligent Default Values for Address Spoofing
Scapy employs sensible defaults to streamline packet creation when implementing techniques to spoof IP address information:
- IP source addresses automatically selected based on routing tables (unless explicitly spoofed)
- Checksums computed automatically for spoofed packets
- Source MAC addresses chosen according to output interfaces
- Ethernet types and IP protocols determined by upper layers
- TCP defaults: source port 20, destination port 80
- UDP defaults: source and destination ports 53
- ICMP defaults: echo request type
Security Testing Best Practices for IP Address Spoofing
When implementing techniques to spoof IP address information for security testing, always:
- Obtain Proper Authorisation: Ensure written permission before testing any network with spoofed traffic
- Use Isolated Environments: Conduct spoofing tests in controlled lab environments
- Document All Activities: Maintain detailed logs of address spoofing procedures and results
- Follow Ethical Guidelines: Adhere to responsible disclosure practices when discovering vulnerabilities
- Understand Legal Implications: Comply with local cybersecurity laws regarding traffic spoofing
- Validate Spoofing Success: Verify that packets actually contain spoofed addresses as intended
- Monitor Network Impact: Ensure spoofed traffic doesn’t cause unintended network disruption
Advanced IP Spoofing Techniques and Future Learning
Mastering methods to spoof IP address information opens doors to sophisticated security testing methodologies. Advanced practitioners can explore custom protocol development with spoofed addressing, complex multi-stage attacks using address spoofing, and automated vulnerability assessment frameworks that leverage IP spoofing capabilities.
The tool’s Python foundation enables integration with other security frameworks, creating powerful automated testing suites that incorporate address spoofing. As network protocols evolve, Scapy’s flexibility ensures continued relevance in cybersecurity testing scenarios requiring the ability to spoof IP address information.
Conclusion
Learning to spoof IP address techniques using Scapy provides security professionals with unparalleled flexibility for network analysis and penetration testing. While the initial learning curve for address spoofing may appear challenging, the investment in mastering how to spoof IP address capabilities yields substantial returns in cybersecurity expertise.
Understanding both theoretical TCP/IP fundamentals and practical techniques to spoof IP address information creates a solid foundation for advanced network security testing. Whether conducting vulnerability assessments, developing custom security tools with spoofed traffic, or analysing network behaviour responses to address spoofing, Scapy remains an essential component of the modern cybersecurity toolkit.
Remember that with the power to spoof IP address information comes great responsibility. Use address spoofing techniques ethically, legally, and always with proper authorisation to contribute positively to cybersecurity advancement. The ability to spoof IP address configurations should only be employed for legitimate security testing and educational purpose.
如有侵权请联系:admin#unsafe.sh