Citrix NetScaler ADC 和 NetScaler Gateway 存在缓冲区溢出漏洞(CVE-2025-5777),影响多个版本。该漏洞因输入验证不足导致攻击者可读取服务器内存中的敏感信息,引发数据泄露和系统控制风险。建议用户升级至最新版本并终止相关会话以缓解风险。 2025-7-3 12:25:37 Author: horizon3.ai(查看原文) 阅读量:32 收藏
Citrix NetScaler Buffer Overread Vulnerability
CVE-2025-5777 is a buffer overread vulnerability discovered in Citrix NetScaler ADC and NetScaler Gateway. This critical vulnerability is due to insufficient input validation, allowing an unauthenticated attacker to reflect memory contents from the server to the client. This can enable the attacker to read sensitive information directly from the server’s memory.
The vulnerability affects NetScaler ADC and NetScaler Gateway versions 14.1 BEFORE 14.1-43.56, 13.1 BEFORE 13.1-58.32, 13.1-FIPS and NDcPP BEFORE 13.1-37.235-FIPS and NDcPP, and 12.1-FIPS BEFORE 12.1-55.328-FIPS. Additionally, NetScaler ADC and NetScaler Gateway versions 12.1 and 13.0, which are End Of Life (EOL), are also vulnerable. Secure Private Access on-prem or Hybrid deployments using NetScaler instances are also impacted. Exploitation requires NetScaler to be configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or an AAA virtual server. This vulnerability is classified as CWE-125: Out-of-bounds Read and has a CVSSv4 Base Score of 9.3.
Impact
Successful exploitation of this vulnerability can lead to:
- Unauthorized access to sensitive information from the server’s memory.
- Potential for further attacks due to exposed sensitive data.
- Complete control over the affected system, including accessing sensitive data, modifying or deleting system resources, and potentially installing malware or creating backdoors.
Mitigations
- It is strongly recommended to install the relevant updated versions as soon as possible:
- NetScaler ADC and NetScaler Gateway 14.1-43.56 and later releases
- NetScaler ADC and NetScaler Gateway 13.1-58.32 and later releases of 13.1
- NetScaler ADC 13.1-FIPS and 13.1-NDcPP 13.1-37.235 and later releases
- NetScaler ADC 12.1-FIPS 12.1-55.328 and later releases
Rapid Response N-Day Testing
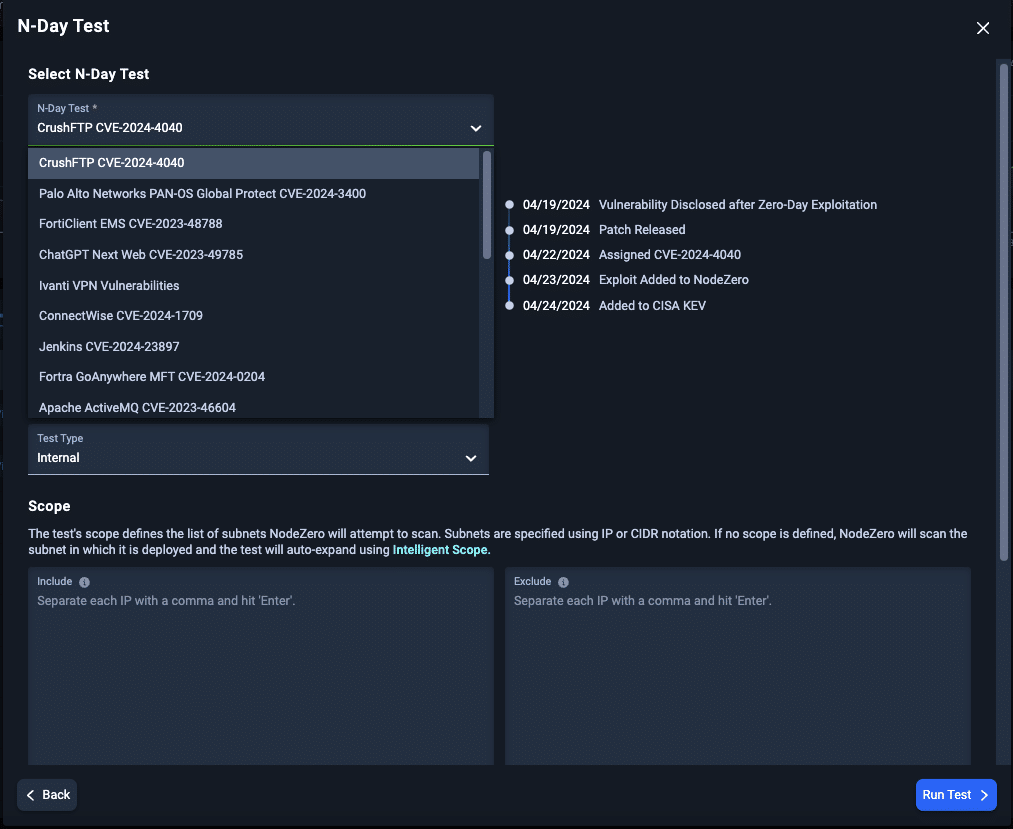
After upgrading all NetScaler appliances in an HA pair or cluster, it is also recommended to terminate all active ICA and PCoIP sessions by running the commands kill icaconnection -all and kill pcoipConnection -all.
Read about other CVEs
NodeZero® Platform
Implement a continuous find, fix, and verify loop with NodeZero
The NodeZero® platform empowers your organization to reduce your security risks by autonomously finding exploitable weaknesses in your network, giving you detailed guidance around how to priortize and fix them, and having you immediately verify that your fixes are effective.
Recognized By
如有侵权请联系:admin#unsafe.sh
