
文章探讨了从漏洞管理转向暴露管理的重要性,强调通过主动缩小攻击面、提供业务上下文和统一安全工具来提升组织的安全效果。作者提供了三个关键建议:平衡主动与被动安全态势、突出孤立安全的风险、以及展示暴露管理如何弥补上下文差距。最终目标是帮助领导者推动组织向更高效、统一的安全模式转型。 2025-6-30 13:0:0 Author: www.tenable.com(查看原文) 阅读量:10 收藏
Each Monday, the Tenable Exposure Management Academy provides the practical, real-world guidance you need to shift from vulnerability management to exposure management. In this post, we share some tips on how to lead the move to exposure management. You can read the entire Exposure Management Academy series here.
For years, organizations poured resources into reactive defenses, scrambling to contain breaches once they were already underway. Yet, breaches continue at an alarming rate. There must be a better way. There must be a more proactive way to shrink the attack surface, prioritize true business exposure and reduce the burden on security teams.
This is the promise of exposure management. And it's rapidly changing the game. As with most change, there is great opportunity ahead. The impact of exposure management on reactive security effectiveness and efficiency will be considerable. We believe that the vulnerability management leaders who drive the move to exposure management today will become the CISOs of tomorrow.
Change often requires evolution beyond our traditional roles, responsibilities and workflows. Is everyone on board for change? Not always. Maybe your boss or peers need some enlightenment on the value exposure management can offer them and the organization. We know that the move from heavy reliance on traditional threat and incident response to a more proactive, preventive approach requires rethinking existing priorities as they relate to roles, responsibilities and investments.
In this post, we thought we’d share some tips on how you can join the exposure management discussion as a driver of change rather than just a passenger on the journey.
Tip 1: Talk about the benefits of balancing your reactive and proactive security posture
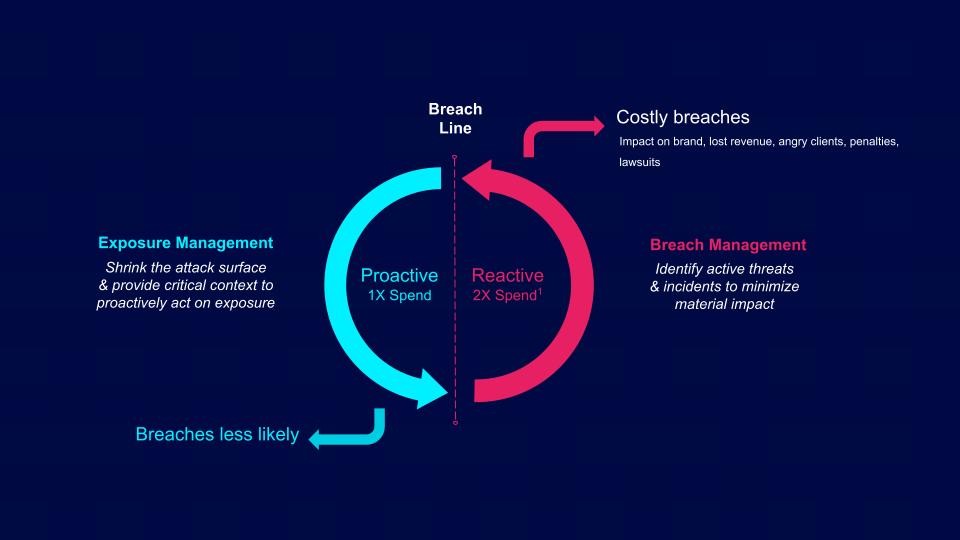
Source: Tenable, 2025
Let’s start with the cybersecurity continuum, with the breach line in the middle. To the right lies reactive security, a world of active threats and incidents. The goal there is to minimize impact after an attack has begun.
Historically, this is where most security expenditures have gone, and for good reason. Breaches used to be the purview of security teams. But now, multiple regulations require breach disclosure. These greater visibility and disclosure requirements can lead to revenue, reputational and customer trust fallout — as well as lawsuits and penalties.
So how can we prevent those breaches from ever happening? That's the role of proactive exposure management, which has two core objectives:
- Shrink the attack surface: Exposure management actively identifies the viable pathways attackers can exploit to gain access and move laterally.
- Provide critical context: Exposure management gives teams the insights they need to prioritize and protect the critical assets and business functions that matter most.
Key points to convince your boss:
- Suggest starting small: Mention that many exposure management programs evolve from traditional vulnerability management — and many organizations begin by expanding the scope of visibility and context of their vulnerability management team over time to include externally facing assets, cloud, OT and IoT.
- Highlight deep insights: Talk about how exposure management can help them quantify and align exposure scores to specific business services or units, which makes it easier to communicate risk posture with lines of business, executives and the board of directors. The ability to quantify and align risk posture to what matters is also central to driving investment decisions because you can now understand where you have higher risk, what its impact might be and then justify your resources requirements..
Tip 2: Highlight the limitations and risks of siloed security
Most organizations operate with multiple security domains or silos. Each operates in isolation, with data trapped in one or even many individual tools. Teams frequently end up having little to no visibility into what’s happening elsewhere.
And, while your vulnerability management program maturity may be robust, your cloud or identity security might be lagging, or vice versa. Bringing every silo up to snuff requires a people, budget and time investment few organizations can realize in short order. And even if you could undertake that monumental task, you’d still be unable to solve the fundamental problem of siloed security — that it doesn't reflect how attackers operate in the real world.
Attackers don't respect your carefully constructed security boundaries. They seek out any vulnerability, misconfiguration or access privilege to gain a foothold, move laterally across silos and escalate their privileges.
Their goals are simple: They want to disrupt your services, hold your operations for ransom or steal sensitive data. Or all of the above. Yet, today, most organizations have no unified view of their attack surface — and siloed security teams are stuck working with tools that tell them very little about how attackers might exploit the attack surface across domains to achieve their goal.
In the face of this threat, the glaring weakness of siloed security comes to light: a lack of context.
Siloed tools don’t offer the technical context of asset identity and risk relationships across domains that attackers exploit. They also don’t offer business context to help you evaluate the potential impact on your "crown jewel" assets and mission-critical services. Legacy cybersecurity tools generate a veritable Mount Everest of noisy findings.
Amid the noise, there’s no clear way to isolate true exposures, let alone quantify or business-align them for prioritization. This works to an attacker’s advantage. And it isn't just an exposure problem. It’s also an ROI challenge. Constantly adding point solutions and people in a chase for visibility that might never come will quickly hit a value and scalability plateau. Without a unified approach and the context that comes with it, you’ll quickly start to see staff churn, miss critical exposures and realize sub-optimal return on your existing security investments.
Key points to convince your boss:
- Quantify your current environment: Estimate the human hours lost to manual tasks and cross-silo inefficiencies, such as reporting, and share that with your boss.
- Catalog current struggles: Survey your different siloed teams to gain insights into their daily struggles, such as noise and pushback from IT teams, then communicate that to your boss.
- Take inventory: Consider the potential for shadow IT caused by rapid digital transformation with multi-cloud, IT/OT convergence, IoT and BYOD — and what risks may be going unseen or unmanaged due to an inability to keep pace with a rapidly evolving attack surface and no unified inventory. Connecting that to how exposure management can better protect those assets will be a great proofpoint.
Tip 3: Share how exposure management closes the context gap by driving better outcomes
Overcoming the context gap demands a unified approach.
Exposure management scales security horizontally by extending visibility across all assets and risks in your attack surface, actively closing hidden gaps. Then, it adds critical technical and business context to shed light on what truly matters to your organization. These targeted insights enable you to not only effectively remedy exposure but also to prioritize investments that directly align with your business objectives.
Delivering transformational outcomes
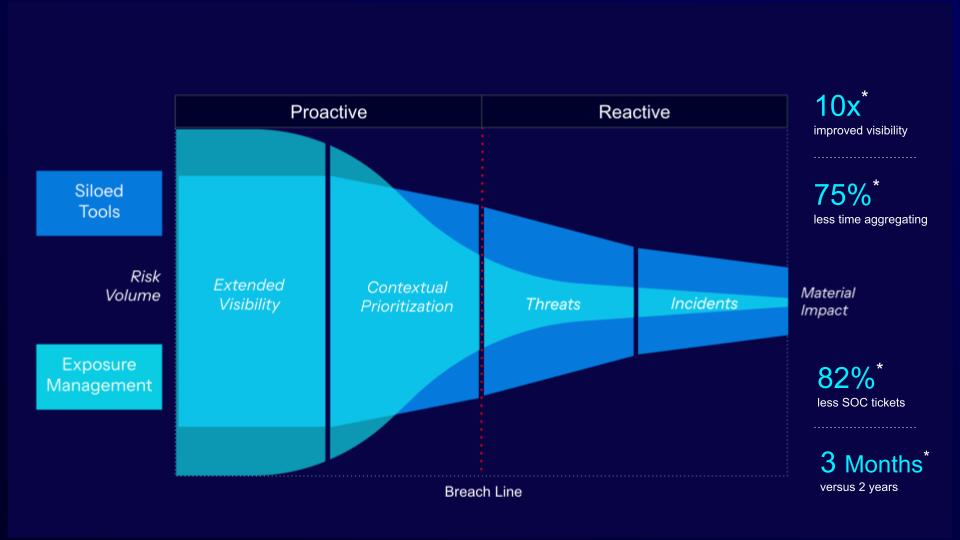
Source: Tenable customer case studies, 2025
As the image above demonstrates, companies that move to exposure management can reap significant benefits. Siloed tools lack critical technical context (attack path relationships) and business context (an understanding of the impact on mission-critical data, applications and revenue streams) across domains. Exposure management fills in gaps that siloed tools can miss, and delivers the context that both proactive and reactive security teams need to do their jobs more effectively. The benefits don’t end there.
One customer, TB Consulting (TBC), saw a tenfold increase in visibility into the number of assets tracked — identifying assets formerly not seen or managed, such as containers and Kubernetes environments. With a unified exposure management platform, TBC reduced the time it takes to gather data across multiple siloed tools by 75%.
With added technical and business context for prioritization and related automations, the company reduced the volume of tickets it was generating from its SOC by 82% — from 1,700 to 300.
With exposure management, the team sped up delivery of required capabilities — completing in three months what they’d been trying to build in-house for 24 months.
Numbers like these are always compelling. And the impact on your work will be even more profound.
Because you can see asset identity, risk relationships and their impact on your most vital assets, you can focus on true exposure rather than getting buried in the noise. You’ll narrow the attack surface for your reactive security teams while adding rich context to identify real threats and incidents so you can break attack paths before they cause material damage.
Key points to convince your boss:
- Talk about closing visibility gaps: Share how you’ll be able to discover previously unseen assets like containers, Kubernetes, OT and IoT identities.
- Underscore the value of unification on scale and productivity: An exposure management platform can gather all your security data into a single store. Once there, you can automate analysis, instead of relying on manual aggregation and ineffective prioritization. This is something your boss will value.
- Focus on what matters: Let your boss know that exposure management will mean reduced exposure and security incidents for the business. SOC will be able to quickly visualize attack paths and potential impact to the organization and break attack chains, rather than sifting through all the noise.
Takeaways
Exposure management is about balancing proactive and reactive security to get ahead of attackers.
It aligns resources with the things that matter most to the business, and provides quantifiable data points that enable wise, informed investment decisions. Exposure management is not just a vision. It’s how many security leaders are driving greater value from their existing security programs today.
More importantly, it's a path forward that you can help chart for your leadership team and organization as a whole. Exposure management provides a natural progression path for you from domain practitioner to future security leader.
Tell your boss that the future of cybersecurity is proactive, unified and business-aligned. The future is exposure management and you can help drive that transformation for your organization

Pierre Coyne
Director of Product Marketing
Pierre Coyne is a visionary marketing leader with over 25 years of experience at the forefront of innovation in the high-tech industry. He has played a pivotal role in shaping go-to-market strategies across cutting-edge markets, including continuous threat exposure management(CTEM), cloud security (CNAPP), multi-cloud platforms and container orchestration with Kubernetes. As Director of Product Marketing at Tenable, Pierre drives thought leadership for Tenable One, the world’s only AI-powered exposure management platform, empowering security leaders to enhance visibility, optimize resource efficiency and minimize operational costs. Prior to Tenable, Pierre led IBM's GTM strategy for its multi-billion-dollar cloud platform and contributed to the success of several trailblazing tech companies, including Armis, Micromuse, CA, Platinum and others.
如有侵权请联系:admin#unsafe.sh