
威胁行为者利用ConnectWise ScreenConnect安装程序创建恶意软件,通过修改隐藏设置实现远程访问。攻击者使用钓鱼邮件或伪装页面传播恶意程序,并将其伪装成合法软件以绕过检测。G DATA发现此类攻击并分析其技术细节,指出需警惕此类伪装攻击,并建议仅从官方渠道获取软件以避免感染风险。 2025-6-25 22:0:31 Author: www.bleepingcomputer.com(查看原文) 阅读量:6 收藏

Threat actors are abusing the ConnectWise ScreenConnect installer to build signed remote access malware by modifying hidden settings within the client's Authenticode signature.
ConnectWise ScreenConnect is a remote monitoring and management (RMM) software that allows IT admins and managed service providers (MSPs) to troubleshoot devices remotely.
When a ScreenConnect installer is built, it can be customized to include the remote server the client should connect to, what text is shown in the dialog boxes, and logos that should be displayed. This configuration data is saved within the file's authenticode signature.
This technique, called authenticode stuffing, allows for the insertion of data into a certificate table while keeping the digital signature intact.
ScreenConnect abused for initial access
Cybersecurity firm G DATA observed malicious ConnectWise binaries with identical hash values across all file sections except for the certificate table.
The only difference was a modified certificate table containing new malicious configuration information while still allowing the file to remain signed.
G DATA says the first samples were found in the BleepingComputer forums, where members reported being infected after falling for phishing attacks. Similar attacks were reported on Reddit.
These phishing attacks utilized either PDFs or intermediary Canva pages that linked to executables hosted on Cloudflare's R2 servers (r2.dev).
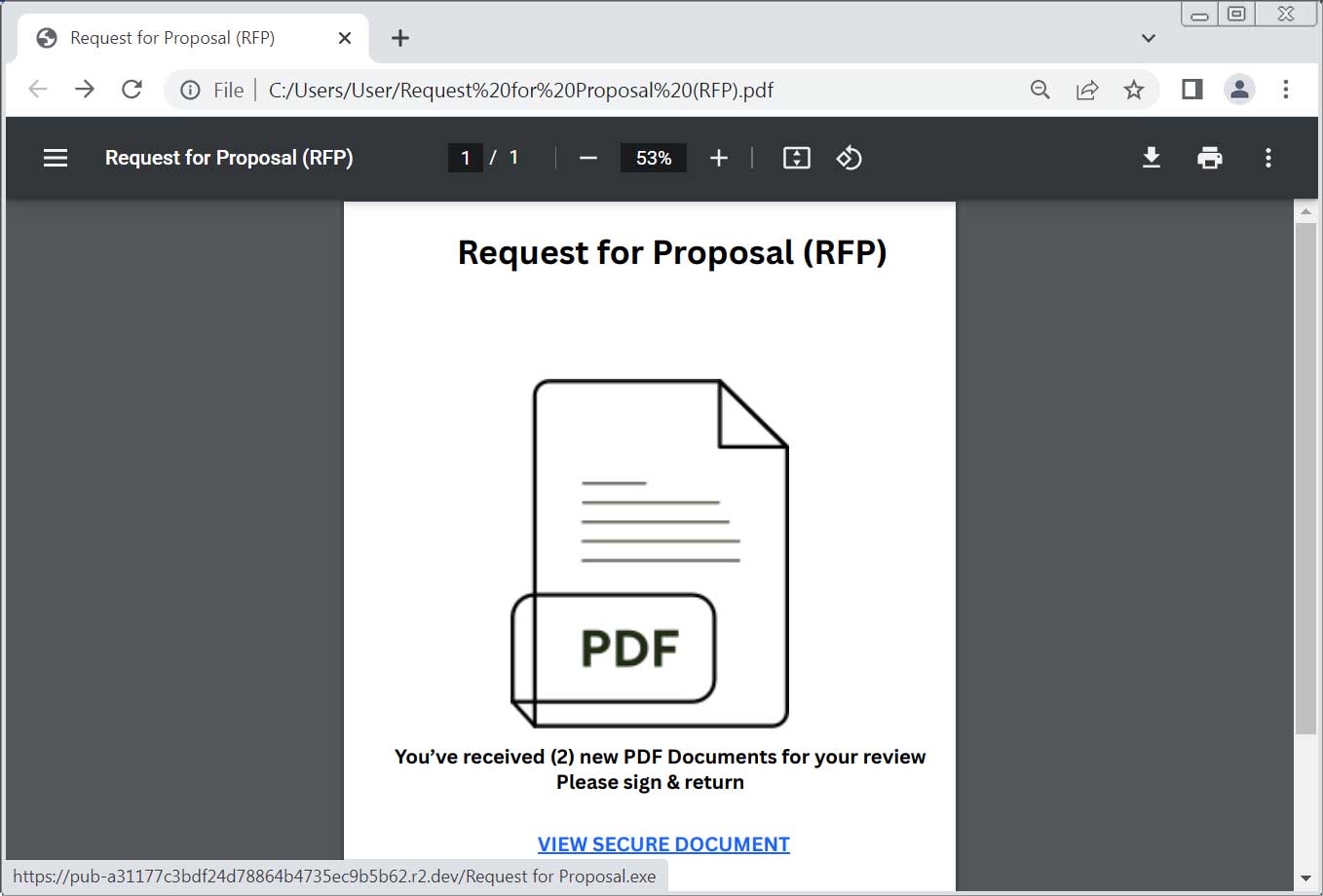
Source: BleepingComputer
The file, called "Request for Proposal.exe," seen by BleepingComputer, is a malicious ScreenConnect client [VirusTotal] configured to connect to the attacker's servers at 86.38.225[.]6:8041 (relay.rachael-and-aidan.co[.]uk)
G DATA built a tool to extract and review the settings found in these campaigns, where the researchers found significant modifications, such as changing the installer's title to "Windows Update" and replacing the background with a fake Windows Update image shown below.
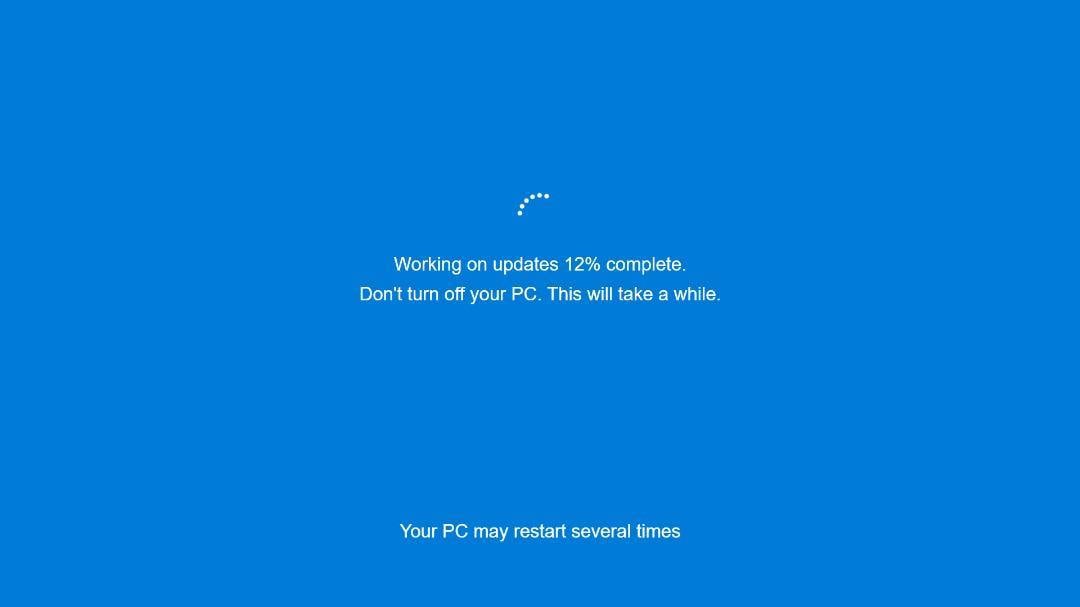
Source: G DATA
Essentially, the threat actors converted the legitimate ConnectWise ScreenConnect client into malware that allows them to stealthily gain access to infected devices.
After contacting G DATA, ConnectWise revoked the certificate used in these binaries, and G DATA is now flagging these samples as Win32.Backdoor.EvilConwi.* and Win32.Riskware.SilentConwi.*.
G DATA says they never received a reply from ConnectWise about this campaign and their report.
Another campaign is also enterprise software, this time distributing trojanized versions of the SonicWall NetExtender VPN client to steal usernames, passwords, and domain information.
According to an advisory from SonicWall, these modified versions send captured credentials to an attacker-controlled server, making it critical for users only to obtain software clients from official sites.
Why IT teams are ditching manual patch management
Patching used to mean complex scripts, long hours, and endless fire drills. Not anymore.
In this new guide, Tines breaks down how modern IT orgs are leveling up with automation. Patch faster, reduce overhead, and focus on strategic work -- no complex scripts required.
如有侵权请联系:admin#unsafe.sh
