
文章讨论了云安全风险、社交工程攻击、AI系统技术栈及配置管理等问题,并提到了Tenable报告揭示的云数据暴露问题、Google披露的俄罗斯赞助的社会工程攻击以及CISA警告的勒索软件利用SimpleHelp漏洞的情况。此外还涉及了CIS基准更新及JIT访问的应用情况。 2025-6-20 13:0:0 Author: www.tenable.com(查看原文) 阅读量:32 收藏
Check out highlights from Tenable’s “2025 Cloud Security Risk Report,” which delves into the critical risk from insecure cloud configurations. Plus, Google reveals a Russia-sponsored social engineering campaign that targeted prominent academics’ Gmail accounts. And get the latest on AI system security, just-in-time access, CIS Benchmarks and more!
Dive into six things that are top of mind for the week ending June 20.
1 - Tenable report: Oops, your cloud data and secrets might be lounging in public
Houston, we have a cloud data-security problem.
Tenable’s “2025 Cloud Security Risk Report,” published this week, found that 9% of publicly accessible cloud-storage resources hold sensitive data, almost all of which – 97% – is labeled as either restricted or confidential.
“This kind of exposure creates an ideal entry point for threat actors and poses a serious, immediate security risk,” reads the report, which provides in-depth coverage of cloud security issues including data and secrets exposure; identity management; cloud workload protection; and artificial intelligence (AI) defense.
The report, authored by the Tenable Cloud Research team, is based on workload telemetry analysis from public cloud and enterprise environments scanned with the Tenable Cloud Security cloud native application protection platform (CNAPP) between October 2024 and March 2025.
Other key findings include:
- 54% of the organizations using Amazon Web Services (AWS) Elastic Container Service (ECS) task definitions have at least one secret – meaning, a privileged credential – embedded in their configurations, which creates a direct attack path.
- 29% of organizations have at least one toxic cloud trilogy — meaning a cloud workload that is publicly exposed, critically vulnerable and highly privileged. This stat is down nine percentage points from the previous report, but it’s still too high.
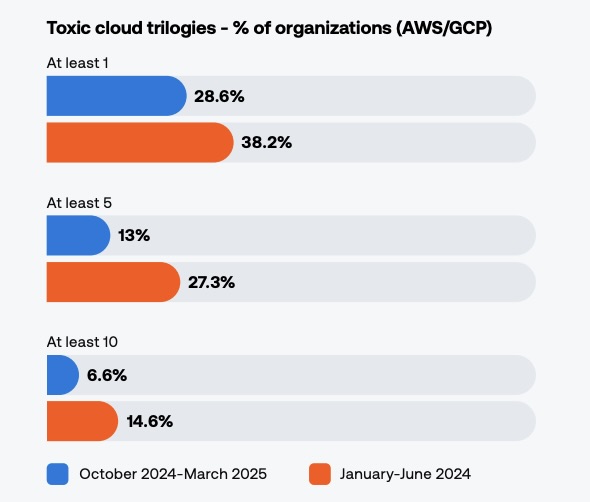
(Tenable’s “2025 Cloud Security Risk Report,” June 2025)
Here are some solid tips and best practices from the report:
- Continuously monitor for public access and automate detection of misconfigured storage services.
- Safeguard secrets by using the secrets-management tools that cloud service providers (CSPs) provide.
- Detect toxic cloud trilogies by correlating identity, vulnerability and network configuration data.
- Boost cloud identity security by adopting just-in-time access capabilities, which put a time limit on access granted to identities.
- Inventory, classify and track your sensitive data in your cloud environment.
To get more details, check out:
- The blog “Secrets in the Open: Cloud Data Exposures That Put Your Business at Risk”
- The announcement “Tenable Research Finds Pervasive Cloud Misconfigurations Exposing Critical Data and Secrets”
- The full report “2025 Cloud Security Risk Report”
- The upcoming webinar “Why Your Cloud Data May Not Be Secure After All: Insights from Tenable Research”
- The blog “Harden Your Cloud Security Posture by Protecting Your Cloud Data and AI Resources”
2 - Google: Academics and Russia critics targeted in social engineering impersonation campaign
A threat actor sponsored by the Russian government recently impersonated U.S. Department of State staff and gained persistent access to the email mailboxes of prominent academics and Russia critics.
That’s according to the Google Threat Intelligence Group, which detailed the social engineering impersonation scheme in a blog post this week.
The threat actor targeted its victims between April and early June of this year by establishing rapport with them and luring them to set application specific passwords (ASPs).
An ASP is a ransonly-generated 16-digit passcode that allows a Google user to grant access to their Google account to a third-party app or device that doesn’t support “Sign in with Google” authentication nor two-step verification.

In this case, the threat actor emailed victims a PDF document inviting them to access a fraudulent State Department cloud environment. The instructions prompted victims to create an ASP.
“Once the target shares the ASP passcode, the attackers establish persistent access to the victim’s mailbox,” reads the blog post, which cites research from Citizen Lab about this same campaign. Google has “re-secured” the Gmail accounts compromised during this social engineering campaign.
In the blog, Google states that using ASPs isn’t recommended and that they’re “unnecessary in most cases.” If a user generates an ASP, Google sends a notification to their Gmail account, recovery email address and any devices signed into the Google account. Users can revoke ASPs on demand.
For more information about preventing social engineering attacks:
- “How to avoid and prevent social engineering attacks” (TechTarget)
- “Understanding Social Engineering: Tactics, Threats, and Prevention” (CTO Magazine)
- “Phishing attacks: defending your organisation” (U.K. National Cyber Security Centre)
- “What are social engineering attacks?” (TechTarget)
- “How AI is making phishing attacks more dangerous” (TechTarget)
3 - Report breaks down AI system “tech stack” to help cyber defenders
Looking to boost your strategies and practices for securing your AI systems? A new report aims to unpack the technology layers that make up an AI system, hoping that a clearer understanding of this “tech stack” will lead to improved AI security.
The Paladin Global Institute’s “The AI Tech Stack: A Primer for Tech and Cyber Policy” report is aimed at cybersecurity practitioners, IT professionals and policy makers, because it’s critical for these three groups to have a solid grasp of how AI systems are built and deployed.
“This framing will give policymakers and tech innovators the tools to take an informed approach to AI security,” Kemba Walden, President of Paladin Global Institute, said in a statement.
The report outlines five core, interdependent layers of the AI “tech stack”:
- Governance: This layer includes a scaffolding of security protocols, legal requirements, ethical principles and policies for secure AI development and deployment.
- Application: This layer consists of the user interface via which AI capabilities are offered to users, including AI chatbots, search engines and voice assistants.
- Infrastructure: This layer is made up of the computational foundation powering AI systems, such as data centers, networks and energy systems.
- Model: This is the “core computational component” where data is processed according to sophisticated AI algorithms in order to pinpoint patterns, generate decisions and more.
- Data: Here resides the foundational raw information that fuels AI models.
“Robust security across this stack is a technical necessity and a strategic imperative,” the report reads.
As shown in the table below, the report explains the security risks in each layer of the AI “tech stack.”
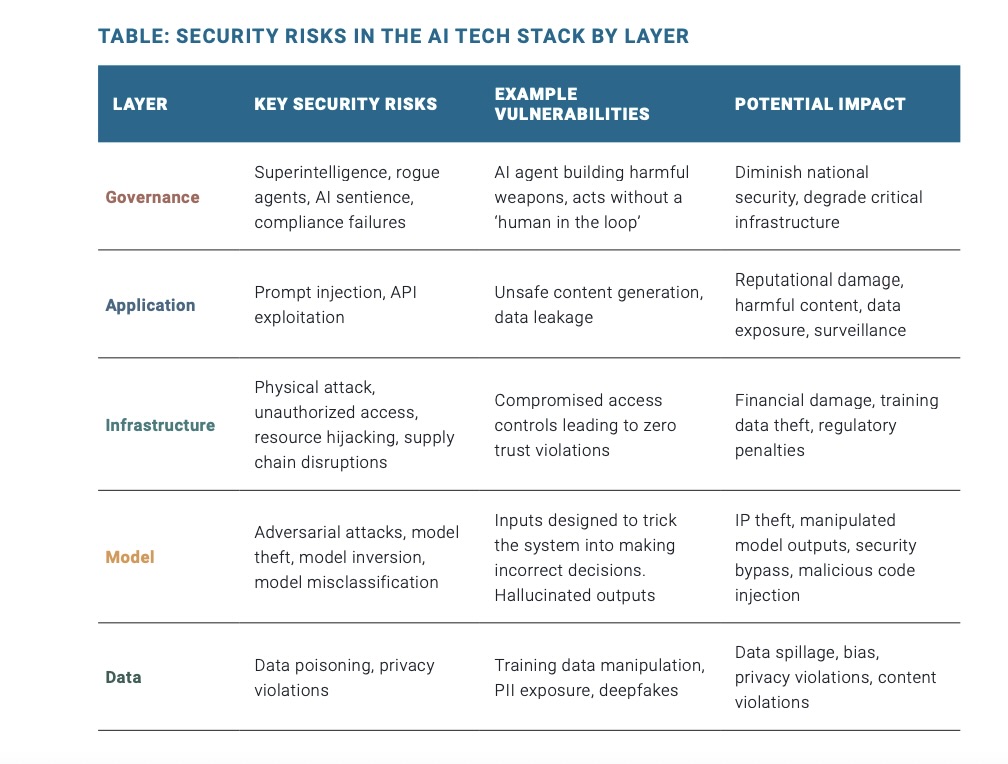
(Source: Paladin Global Institute’s “The AI Tech Stack: A Primer for Tech and Cyber Policy” report, June 2025)
The report also offers recommendations for preventing and mitigating the key cyber threats faced by AI systems. It argues that the right security strategy is to take a systemic approach, as opposed to isolated controls. The report also calls for embedding security starting in the early stages of AI system development.
Recommendations include:
- Securing the data layer with encryption and access controls
- Housing the model layer in environments protected with robust access controls and secure APIs
- Applying foundational cybersecurity practices to the infrastructure and application layers, as well as AI-specific protections
- Developing dynamic, interoperable standards in the governance layer, in order to boost trust in AI systems
For more information about AI security, check out these Tenable resources:
- “Know Your Exposure: Is Your Cloud Data Secure in the Age of AI?” (on-demand webinar)
- “Who's Afraid of AI Risk in Cloud Environments?” (blog)
- “Tenable Cloud AI Risk Report 2025” (research report)
- “2025 Cloud AI Risk Report: Helping You Build More Secure AI Models in the Cloud” (on-demand webinar)
- “How AI Can Boost Your Cybersecurity Program” (blog)
4 - Tenable webinar poll: Are you using JIT access and automating identity protection?
During our recent webinar “Tenable Cloud Security Customer Update, June 2025,” we polled attendees about their use of just-in-time (JIT) access and about how automated their detection of overprivileged identities is. Check out what they said.
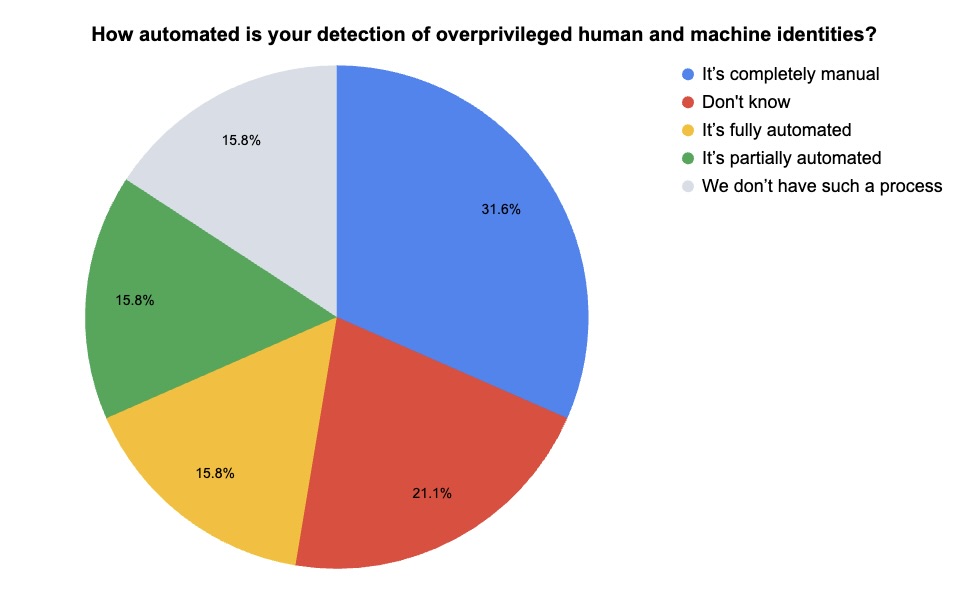
(19 webinar attendees polled by Tenable, June 2025)
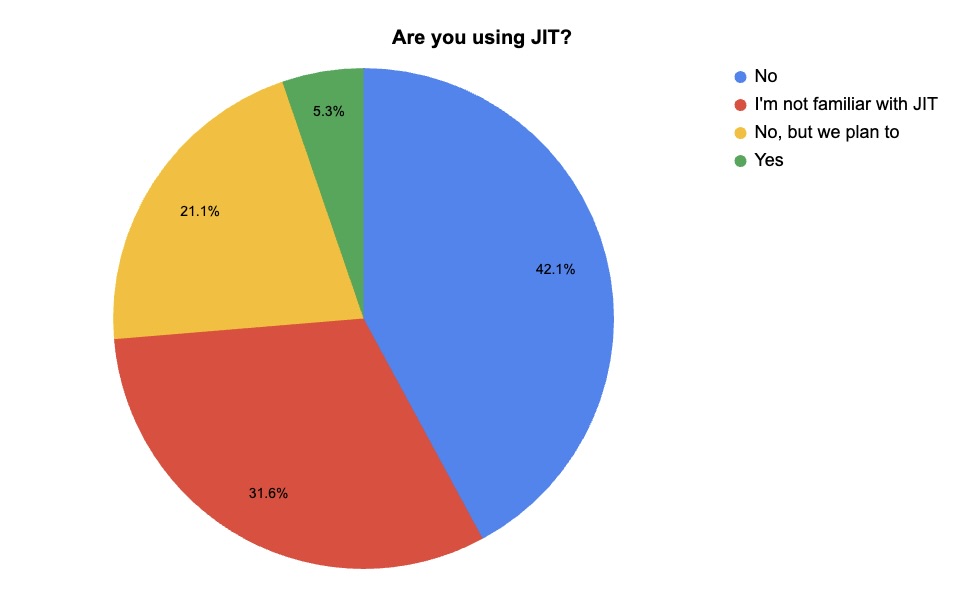
(19 webinar attendees polled by Tenable, June 2025)
Watch this on-demand webinar to learn about how JIT access can slash your exposures from compromised identities.
5 - CISA warns: Ransomware gangs exploiting SimpleHelp RMM vuln
Attackers are launching ransomware attacks by exploiting vulnerabilities in SimpleHelp’s eponymous remote monitoring and management product.
That’s the warning from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which added that victims include customers of a utility billing software provider.
“This incident reflects a broader pattern of ransomware actors targeting organizations through unpatched versions of SimpleHelp RMM since January 2025,” reads CISA’s cybersecurity advisory.

SimpleHelp’s versions 5.5.7 and earlier contain several vulnerabilities, including the path traversal vulnerability CVE-2024-57727, which is likely the one the ransomware attackers are exploiting, according to CISA.
Recommended mitigations include:
- Vulnerable third-party vendors:
- Immediately upgrade from SimpleHelp versions 5.5.7 or earlier to the latest version of the product.
- Direct your downstream customers to secure their endpoints and conduct threat hunting on their network.
- Vulnerable downstream customers and end users:
- Determine if you’re running an unpatched SimpleHelp version directly or embedded in third-party software.
- Immediately upgrade to the latest version of the product.
- Downstream customers and end users with systems encrypted via ransomware:
- Take the compromised system offline.
- Reinstall the operating system using a bootable USB drive or DVD
- Wipe the system and restore data exclusively from a clean backup.
CISA also offers proactive mitigation recommendations, such as:
- Keep an update inventory of all your software and hardware assets.
- Back up your system on a daily basis to a separate offline device.
- If possible, don’t expose remote access services to the web.
To get more details, read:
- The CISA advisory “Ransomware Actors Exploit Unpatched SimpleHelp Remote Monitoring and Management to Compromise Utility Billing Software Provider”
- The CISA alert “CISA Releases Cybersecurity Advisory on SimpleHelp RMM Vulnerability”
6 - CIS updates Benchmarks for AWS, GCP, Microsoft products
If your organization uses the CIS Benchmarks to tighten up software configurations, this one's for you.
The Center for Internet Security (CIS) has updated 12 of its CIS Benchmarks secure configuration guidelines, including those for Amazon Elastick Kubernetes Service, Microsoft 365 and Google Cloud Platform.
Specifically, these CIS Benchmarks were updated:
- CIS Amazon Elastic Kubernetes Service (EKS) Benchmark v1.7.0
- CIS Cisco IOS XE 17.x Benchmark v2.2.0
- CIS Google Cloud Platform Foundation Benchmark v4.0.0
- CIS Microsoft 365 Foundations Benchmark v5.0.0
- CIS Microsoft SQL Server 2019 Benchmark v1.5.0 — Final Update
- CIS Microsoft SQL Server 2022 Benchmark v1.2.0
- CIS Microsoft Windows 10 Enterprise Benchmark v4.0.0
- CIS Microsoft Windows 11 Stand-alone Benchmark v4.0.0
- CIS Microsoft Windows Server 2022 Benchmark v4.0.0
- CIS Oracle Cloud Infrastructure Container Engine for Kubernetes (OKE) Benchmark v1.7.0
- CIS SUSE Linux Enterprise 12 Benchmark v3.2.1
- CIS VMware ESXi 7.0 Benchmark v1.5.0

In addition, CIS released these three brand new Benchmarks:
- CIS Apple MacOS 14.0 Sonoma Intune Benchmark v1.0.0
- CIS Apple MacOS 15.0 Sequoia Intune Benchmark v1.0.0
- CIS Ubuntu Linux 22.04 LTS STIG Benchmark v1.0.0
You can use the CIS Benchmarks’ configuration recommendations to harden products against attacks. There are more than 100 Benchmarks for 25-plus vendor product families. Product categories covered by the CIS Benchmarks include cloud platforms; databases; desktop and server software; mobile devices; operating systems; and more.
To get more details, read the CIS blog “CIS Benchmarks June 2025 Update.” For more information about the CIS Benchmarks list, check out its home page and FAQ, as well as:
- “Getting to Know the CIS Benchmarks” (CIS)
- “Security Via Consensus: Developing the CIS Benchmarks” (Dark Reading)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)

Juan Perez
Senior Content Marketing Manager
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh