软件供应链攻击频发,涉及IT、电信等多个行业及美国、欧洲等多国。攻击者通过第三方服务或漏洞发起攻击,造成广泛影响。企业需加强网络微分段、访问控制和数据加密等措施以应对威胁。 2025-6-9 11:16:39 Author: cyble.com(查看原文) 阅读量:24 收藏
IT and software supply chain incidents have been trending higher in recent months, as threat actors have become more adept at exploiting the interconnected hardware, software, and services that comprise modern IT environments.
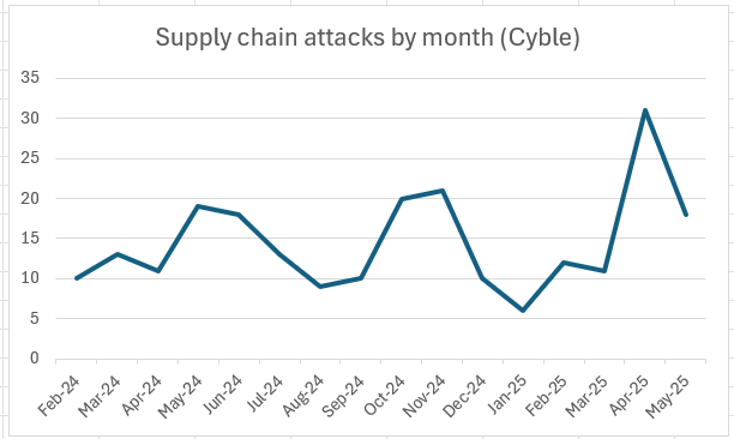
An analysis of Cyble data reveals that software supply chain attacks have increased from an average of just under 13 a month during the eight months of February-September 2024 to just over 16 a month from October 2024 to May 2025, an increase of 25% in the most recent eight-month period. The last two months have averaged nearly 25 cyberattacks with supply chain impact, representing a near-doubling of supply chain attacks if the recent trend continues (chart below).

However, monthly variations in supply chain attacks tend to be quite large, ranging from a low of 6 attacks in January 2025 to a high of 31 attacks in April 2025. So, some variability should be expected even as supply chain attacks generally trend higher.
The data for this article, from Cyble investigations and OSINT sources, is incomplete, as not every cyberattack or its source is always known.
An analysis of software supply chain attack trends follows, including targeted industries and countries, a closer look at 10 significant incidents, and steps organizations can take to protect themselves from supply chain threats.
Software Supply Chain Attacks: Targeted Industries and Countries
Looking at the 79 cyberattacks with supply chain implications documented by Cyble in the first five months of 2025, the majority (50, or 63%) directly targeted IT, technology, and telecommunications companies, which are rich potential targets for threat actors hoping to exploit downstream users.
Damage from a successful exploit in those areas can be widespread, as happened with the hundreds of CL0P ransomware victims from a single vulnerability.
Supply chain attacks hit 22 of the 24 sectors tracked by Cyble in the first five months of 2025 (chart below). Only the Mining and Real Estate industries remained untouched.

Within non-tech industries, supply chain attacks often stem from third parties and service providers, including industry-specific solutions.
Among targeted countries, the U.S. was a target in 31 of the 79 incidents. European countries were targeted in 27 incidents, with France (10 incidents) experiencing the highest number of European attacks.
26 of the incidents targeted APAC countries, led by India (9 incidents) and Taiwan (4). The Middle East and Africa were targets in 10 incidents, including four each in the UAE and Israel.
Supply Chain Incidents
Here are details of 10 supply chain incidents documented by Cyble in recent months. This week’s ransomware blog also listed an additional eight incidents with supply chain implications.
- Everest Ransomware claimed a ransomware attack on a Swiss banking technology solutions and services company. Included in the exfiltrated data were login credentials to various banking applications.
- An IT services subsidiary of a large international conglomerate confirmed that it was impacted by a ransomware incident believed to be the responsibility of the Akira ransomware group. The incident may have impacted multiple projects tied to government entities.
- A threat actor (TA) on the English-language cybercrime forum DarkForums offered for sale a large dataset allegedly pertaining to a high-throughput telecommunications satellite for Indonesia and some ASEAN countries. The TA claimed that the entire dataset is 92 GB in size and includes technical documents related to propulsion tests, launch analyses, ground systems, site vulnerabilities, and more.
- The Hellcat ransomware group allegedly compromised a China-based company specializing in display technologies and electronic solutions. The threat actor claims to have exfiltrated 166 GB of data, including blueprints, financial records, and internal correspondence.
- The DragonForce extortion group claimed responsibility for an attack on a U.S. company specializing in biometric recognition and identity authentication solutions, from which the group claims to have exfiltrated more than 200 GB of data.
- The VanHelsing ransomware group claimed responsibility for compromising a U.S.-based company specializing in enterprise security and identity access management (IAM) solutions. The nature of the exposed files suggests they may contain sensitive information linked to the company’s customers, potentially affecting sectors such as Banking, Financial Services, and Insurance (BFSI).
- A threat actor on the cybercrime forum Exploit claimed to offer unauthorized access with administrative privileges to the cloud infrastructure of an India-based fintech company specializing in SaaS-based payment service solutions.
- The extortion group Crypto24 claimed responsibility for a cyberattack on a Singapore-based technology company, alleging the theft of 3TB of data. According to the group, the compromised information includes customer records, database content, technical and project documentation, and other internal files from the company’s servers and NAS systems.
- Killsec hacking group claimed responsibility for compromising an Australia-based company that offers IT and telecom solutions. While the group did not disclose the volume of data exfiltrated, leaked content includes backup data, licensing and application configuration files, software license types, hashed credentials, and other critical infrastructure-related datasets.
- A threat actor on Darkforums claimed to offer unauthorized access to a portal belonging to an Australian telecommunications company. The TA claimed to have gained access to a portal that provided access to domain administration tools and other critical network information. The TA quoted USD $750 for access.
Protecting Against Supply Chain Attacks
Protecting against software supply chain attacks is challenging because these partners and suppliers are, by nature, trusted, so organizations should build in controls and resilience wherever possible to limit the extent of any attacks. Such controls include:
- Network microsegmentation
- Strong access controls, allowing no more access than is required, with frequent verification
- A strong source of user identity and authentication, including multi-factor authentication and biometrics, and machine authentication with device compliance and health checks
- Encryption of data at rest and in transit
- Ransomware-resistant backups that are immutable, air-gapped, and isolated as much as possible
- Honeypots that lure attackers to fake assets for early breach detection
- Proper configuration of API and cloud service connections
- Monitor for unusual activity with SIEM, Active Directory monitoring, and data loss prevention (DLP) tools
- Routinely assessing and confirming controls through audits, vulnerability scanning, and penetration tests
The most effective place to control software supply chain risks is in the continuous integration and development (CI/CD) process, so carefully vetting partners and suppliers and requiring good security controls in contracts are essential ways to improve third-party security. Services like Cyble’s third-party risk intelligence can help you get started on this process. By making security a buying criterion, vendors will be more likely to respond with better security controls and documentation.
Disclaimer: This blog is based on our research and the information available at the time of writing. It is for informational purposes only and does not constitute legal, financial, or professional advice. While we strive for accuracy, we do not guarantee the completeness or reliability of the content. If any sensitive information has been inadvertently included, please contact us for correction. Cyble is not responsible for any errors, omissions, or decisions made based on this content. Readers should verify findings and seek expert advice where necessary. All trademarks, logos, and third-party content belong to their respective owners and do not imply endorsement or affiliation. All content is presented “as is” without any guarantee that it is free of confidential, proprietary, or otherwise sensitive information. If you believe any portion of this content contains inadvertently shared or sensitive data, please contact us immediately so that we may address and rectify the issue. No Liability for Errors or Omissions Due to the dynamic nature of cyber threat activity, this [blog/report/article] may include partial, outdated, or otherwise incorrect information due to unverified sources, evolving security threats, or human error. We expressly disclaim any liability for errors or omissions or any potential consequences arising from the use, misuse, or reliance on this information.
如有侵权请联系:admin#unsafe.sh