
文章探讨了开源AI工具的风险与优势、英国NCSC关于先进加密技术的指南、ISACA呼吁组织向后量子密码学迁移、NCSC发布的软件安全行为准则、CISA警告针对关键基础设施的网络攻击以及CIS第一季度恶意软件排名,其中SocGholish居首。 2025-5-16 13:0:0 Author: www.tenable.com(查看原文) 阅读量:12 收藏
Check out a study that outlines the risks and benefits of open-source AI tools. Meanwhile, the NCSC unpacks use cases for new, alternative encryption technologies. Plus, ISACA urges orgs to begin their post-quantum cryptography migration. And get the latest on assessing software products’ security; cyber attacks against critical infrastructure; and more!
Dive into six things that are top of mind for the week ending May 16.
1 - Study: Orgs embrace open source AI, but cyber risk concerns loom
As organizations increasingly adopt open-source artificial intelligence (AI) technologies, they also worry about facing higher risks than those posed by proprietary AI products.
That’s according to the report “Open source technology in the age of AI” from McKinsey Co., the Patrick J. McGovern Foundation and Mozilla, based on a global survey of 700-plus technology leaders and senior developers.
Specifically, while respondents cite benefits like lower costs and ease of use, they consider open source AI tools to be riskier in areas like cybersecurity, compliance and intellectual property.
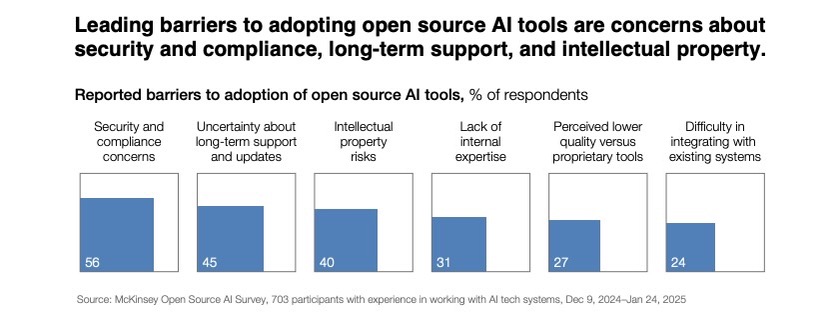
If your organization is looking at or already adopting open source AI products, here are risk mitigation recommendations from the report:
- Implement strong guardrails, such as automated content filtering, input / output validation and human oversight.
- Use standardized benchmarks to conduct regular risk assessments.
- Run AI models in trusted execution environments.
- Protect model repositories with strong access controls.
- Segment the networks of training and inference servers.
- Confirm models come from trusted repositories by using cryptographic hash verification.
For more information about AI security, check out these Tenable resources:
- “Securing the AI Attack Surface: Separating the Unknown from the Well Understood” (blog)
- “Know Your Exposure: Is Your Cloud Data Secure in the Age of AI?” (on-demand webinar)
- “Harden Your Cloud Security Posture by Protecting Your Cloud Data and AI Resources” (blog)
- “Tenable Cloud AI Risk Report 2025” (research report)
- “Never Trust User Inputs -- And AI Isn't an Exception: A Security-First Approach” (blog)
2 - NCSC offers primer on advanced cryptography
Organizations mulling the use of emerging cryptographic techniques may find a new white paper from the U.K. National Cyber Security Centre (NCSC) helpful.
Titled “Advanced Cryptography: Deciding when to use Advanced Cryptography to protect your data,” the document seeks to educate organizations about new, advanced cryptography options so that they can make informed decisions about how and whether to use them.
“These emerging techniques, collectively called Advanced Cryptography, can be used in scenarios where traditional cryptography may be insufficient,” the white paper reads.
Specifically, the NCSC defines advanced cryptography as “a range of techniques that use cryptographic methods to provide data-processing functionality” that goes beyond what’s possible with traditional cryptographic methods.
“Our white paper considers the new forms of cryptography that are emerging in academia (and are being developed by industry) to tackle problems that can’t be solved simply by encrypting, decrypting, signing, and verifying information,” an NCSC blog reads.

However, because advanced cryptography techniques are newer, their security isn’t as well understood, and they may be slower and more expensive, according to the NCSC.
“When deciding whether to use Advanced Cryptography, start with a clear articulation of the problem, and use that to guide the development of an appropriate solution,” the document says.
For example, advanced cryptography techniques might be an appropriate option for securing data processing if the scenario involves all or most of these elements:
- Multiple parties must collaborate to accomplish the desired result.
- No trusted third party can perform the operation.
- The organization can accept a spike in computation costs, communications bandwidth or other performance overhead.
- Some participating parties may be unreliable or dishonest.
Advanced cryptography techniques discussed in the white paper include:
- Homomorphic encryption
- Multiparty computation
- Zero-knowledge proofs
- Attribute-based encryption
For more information about new, emerging forms of cryptography:
- “Understanding the Differences Between Fully Homomorphic Encryption and Confidential Computing” (Cloud Security Alliance)
- “What is Secure Multiparty Computation?” (Geeks for Geeks)
- “A Survey on the Applications of Zero-Knowledge Proofs” (University of Southern California)
- “Introduction to Zero-Knowledge Proofs” (Chainalysis)
- “Multi-authority Registered Attribute-Based Encryption” (University of Texas at Austin)
3 - ISACA: Orgs must get cracking on quantum-threat plans
Most organizations remain woefully unprepared for tackling the future threat that quantum computers will pose to the data they store and handle – and the clock is ticking.
That’s the key finding from ISACA’s “2025 Quantum Computing Pulse Poll,” which surveyed almost 2,700 cybersecurity, audit, risk and data-privacy professionals globally.
Specifically, 95% of respondent organizations haven’t drafted a roadmap for transitioning to post-quantum cryptography. Only 5% consider the quantum threat a high business priority today.
Here’s the issue: Quantum computers, expected to become available sometime between 2030 and 2040, will be able to decrypt data protected with today’s public-key cryptographic algorithms.

Thus, the consensus is that organizations need to start migrating now to post-quantum cryptography – also known as quantum-resistant cryptography – because the process is complex and requires careful planning and deployment.
To help organizations get started, ISACA is offering a roadmap template for adopting quantum-resistant cryptography, with specific actions to take now, including:
- Educate and raise awareness among stakeholders about quantum computing’s opportunities and threats; explain the risks of compromised data; and underscore the importance of adopting quantum-resistant encryption.
- Draft a post-quantum encryption strategy for both new and existing data, including updating compliance policies; and integrating quantum threats into existing risk assessments and security frameworks.
- Regularly assess and audit quantum security risks; test cryptographic resilience and update encryption practices accordingly; and monitor industry innovations and regulatory guidance.
In short, ISACA recommends that organizations plan to encrypt all new data using post-quantum cryptography; re-encrypt all existing data; and make this transition a priority today.
In March, NIST picked its fifth algorithm for post-quantum encryption, which it expects will be widely available for use in 2027. NIST released three quantum-resistant algorithm standards last year and expects to release a fourth one in 2026.
Other resources for helping organizations plan their migration to quantum-resistant cryptography include NIST’s draft white paper “Considerations for Achieving Crypto Agility,” and the U.K. National Cyber Security Centre’s “Timelines for migration to post-quantum (PQC) cryptography.”
To get more details about the ISACA survey, check out these resources:
- The survey’s announcement “Despite Rising Concerns, 95% of Organizations Lack a Quantum Computing Roadmap, ISACA Finds”
- A complementary infographic
- The roadmap for shifting to post-quantum cryptography
- The blog “Post-Quantum Cryptography: A Call to Action”
For more information about how to protect your organization against the quantum computing cyberthreat:
- “How to prepare for a secure post-quantum future” (TechTarget)
- “Moody’s sounds alarm on quantum computing risk, as transition to PQC ‘will be long and costly’” (Industrial Cyber)
- “Companies Prepare to Fight Quantum Hackers” (The Wall Street Journal)
- “US unveils new tools to withstand encryption-breaking quantum. Here's what experts are saying” (World Economic Forum)
- “Quantum is coming — and bringing new cybersecurity threats with it” (KPMG)
- “Quantum and the Threat to Encryption” (SecurityWeek)
4 - NCSC urges software vendors to tighten security
In an attempt to prompt software makers to build safer products, the U.K.’s National Cyber Security Centre (NCSC) has published a voluntary “Software Code of Practice” that outlines a baseline of cybersecurity, resilience and privacy features and controls that software should offer.
“It signals – to both software vendors and their customers – what can reasonably be expected from software suppliers and defines the minimum set of actions that should be in place to ensure products and services are resilient to a cyber attack from a commodity threat,” reads an NCSC blog.

The Software Code of Practice outlines 14 principles grouped into four core areas:
- Secure design and development
- Follow the practices and guidelines of a secure development framework.
- Understand the software product’s components, and assess the risk of third-party components.
- Establish a process for testing the software product and its updates.
- Apply secure-by-design principles across the product’s software development lifecycle.
- Security of the build environment
- Prevent unauthorized access to the build environment.
- Control and log changes.
- Secure deployment and maintenance
- Secure the software distribution process.
- Adopt and disclose a vulnerability disclosure policy.
- Establish processes for detecting and managing software component vulnerabilities, and for prioritizing their remediation.
- Report vulnerabilities to all relevant stakeholders.
- Offer security updates, patches and notifications promptly to customers.
- Customer communications
- Inform customers about the level of support and maintenance for the software product.
- Give customers at least one year in advance that a software product will no longer be supported.
- Notify customers about significant incidents that may impact their organizations.
For more information about how to assess the security of commercial software products:
- “Secure by Demand Guide: How Software Customers Can Drive a Secure Technology Ecosystem” (CISA)
- “Choosing secure and verifiable technologies” (Australian Cyber Security Centre)
- “Secure software procurement in 2025: A call for accountability” (ComputerWeekly)
- “Vet Technologies Before Adding Them to Your Network” (CISA)
- “Vet software security as part of enterprise procurement, NIST says” (Cybersecurity Dive)
5 - CISA warns of “unsophisticated” cyber attacks against critical infrastructure
Inexperienced hackers are successfully targeting operational technology (OT) systems of critical infrastructure organizations using simple attack methods that exploit weak cyber hygiene.
That’s the warning from CISA, which is urging critical infrastructure organizations to implement basic, foundational cybersecurity measures that’ll help them fend off these unsophisticated attackers.
“Although these activities often include basic and elementary intrusion techniques, the presence of poor cyber hygiene and exposed assets can escalate these threats,” reads a CISA statement.
Specifically, these “low-hanging fruit” breaches can open the door for website defacements, configuration changes, operational disruptions and physical damage.

In a new fact sheet titled “Primary Mitigations to Reduce Cyber Threats to Operational Technology,” CISA offers mitigation recommendations, including:
- Unplug OT devices from the public internet because their authentication and authorization methods fall short against modern attacks.
- Replace default passwords with complex, unique ones, especially in devices exposed to the internet that can control OT systems and processes.
- Harden remote access to OT assets by, for example, switching them to a private IP network connection using virtual private networks with multifactor authentication.
- Segment IT and OT networks.
- Ensure you can operate OT systems manually in the event of a cyber attack.
For more information about OT security, check out these Tenable resources:
- “Mind the Gap: A Roadmap to IT/OT Alignment” (white paper)
- “Unlock Advanced IoT Visibility in your OT Environment Security” (on-demand webinar)
- “How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform” (blog)
- “Blackbox to blueprint: The security leader’s guidebook to managing OT and IT risk” (white paper)
- “Fortifying Your OT Environment: Vulnerability and Risk Mitigation Strategies” (on-demand webinar)
6 - Variant used in fake-update attacks tops CIS Q1 malware rankings
For the seventh straight quarter, SocGholish, which powers fake-software update attacks, has ranked as the most prevalent malware variant, a sign that this type of attack remains a top moneymaker for hackers.
That’s according to the Center for Internet Security’s “Top 10 Malware Q1 2025” list of the malware variants responsible for the most infections.
Specifically, SocGholish accounted for 48% of all malware infections during 2025’s first quater.
In a fake software-update attack, the victim is tricked into installing what appears as a legitimate update for, say, their preferred browser. In reality, the downloaded software is laced with malware.

(Source: Center for Internet Security, May 2025)
Here’s the full list of the most prevalent malware variants in the first quarter of 2025, in descending order:
- SocGholish, a downloader distributed through malicious websites that tricks users into downloading it by offering fake software updates
- ZPHP, a JavaScript downloader that’s distributed via fake browser updates
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI)
- Agent Tesla, a remote access trojan (RAT) that captures credentials, keystrokes and screenshots
- TeleGrab, an infostealer that swipes data such as chat histories and contacts from Telegram’s desktop and web versions
- Arechclient2, also known as SectopRAT, is a .NET remote access trojan (RAT) whose capabilities include multiple stealth functions
- LandUpdate808, a JavaScript downloader distributed through malicious or compromised websites via fake browser updates
- VenomRAT, an open-source malware with multiple versions whose features include keylogging, data exfiltration and screen capturing
- DarkGate, a downloader and keylogger that steals financial data and personally identifiable information (PII), and delivers other malware
- Ratenjay, a RAT that executes commands remotely and features keylogging capabilities
To get more information, check out the CIS blog “Top 10 Malware Q1 2025,” where you’ll find more details, context and indicators of compromise for each malware strain.
For details on fake update attacks:
- “The Fake Browser Update Scam Gets a Makeover” (Krebs on Security)
- “Watch Out: Attackers Are Hiding Malware in 'Browser Updates'” (Dark Reading)
- “Hackers Use Fake Browser Updates for AMOS Malware Attacks Targeting Mac Users” (MSSP Alert)
- “Malware crooks find an in with fake browser updates, in case real ones weren't bad enough” (The Register)
- “Hackers have been spreading malware via fake Chrome updates” (TechRadar)
VIDEOS
Fake Chrome Update Malware (The PC Security Channel)
Beware Google Chrome fake update browser pop ups that bring malware (Windows, Computers and Technology)

Juan Perez
Senior Content Marketing Manager
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh