
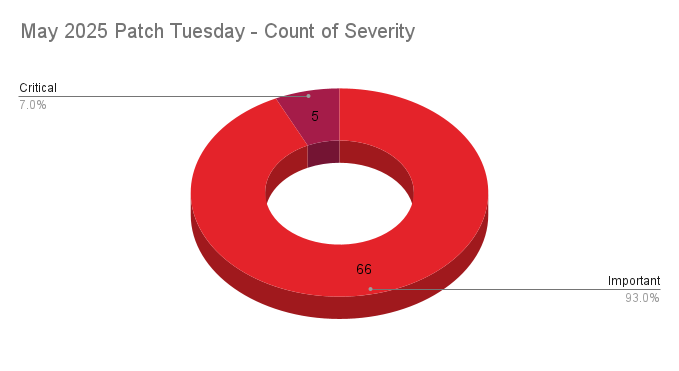
- 5Critical
- 66Important
- 0Moderate
- 0Low
Microsoft addresses 71 CVEs including seven zero-days, five of which were exploited in the wild.
Microsoft patched 71 CVEs in its May 2025 Patch Tuesday release, with five rated critical and 66 rated as important.
This month’s update includes patches for:
- .NET, Visual Studio, and Build Tools for Visual Studio
- Active Directory Certificate Services (AD CS)
- Azure
- Azure Automation
- Azure DevOps
- Azure File Sync
- Azure Storage Resource Provider
- Microsoft Brokering File System
- Microsoft Dataverse
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Edge (Chromium-based)
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office PowerPoint
- Microsoft Office SharePoint
- Microsoft PC Manager
- Microsoft Power Apps
- Microsoft Scripting Engine
- Remote Desktop Gateway Service
- Role: Windows Hyper-V
- Universal Print Management Service
- UrlMon
- Visual Studio
- Visual Studio Code
- Web Threat Defense (WTD.sys)
- Windows Ancillary Function Driver for WinSock
- Windows Common Log File System Driver
- Windows Deployment Services
- Windows Drivers
- Windows DWM
- Windows File Server
- Windows Fundamentals
- Windows Hardware Lab Kit
- Windows Installer
- Windows Kernel
- Windows LDAP - Lightweight Directory Access Protocol
- Windows Media
- Windows NTFS
- Windows Remote Desktop
- Windows Routing and Remote Access Service (RRAS)
- Windows Secure Kernel Mode
- Windows SMB
- Windows Trusted Runtime Interface Driver
- Windows Virtual Machine Bus
- Windows Win32K - GRFX
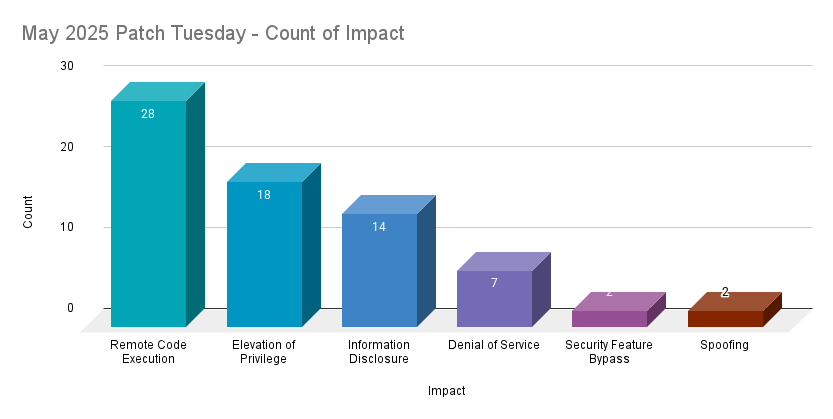
Remote code execution (RCE) vulnerabilities accounted for 39.4% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 25.4%.
CVE-2025-30385, CVE-2025-32701 and CVE-2025-32706 | Windows Common Log File System Driver Elevation of Privilege Vulnerabilities
CVE-2025-30385, CVE-2025-32701 and CVE-2025-32706 are EoP vulnerabilities in the Windows Common Log File System (CLFS) Driver. Each was assigned a CVSSv3 score of 7.8 and are rated as important. Both CVE-2025-32701 and CVE-2025-32706 were exploited in the wild as zero-days while CVE-2025-30385 is assessed as “Exploitation More Likely” according to Microsoft’s Exploitability Index.
Prior to this month's release, Microsoft has patched two other EoP vulnerabilities in the Windows CLFS driver in 2025, including CVE-2025-29824, exploited as a zero-day vulnerability in the April 2025 Patch Tuesday release. In 2024, there were eight CLFS vulnerabilities patched, including one zero-day vulnerability in the CLFS driver that was exploited (CVE-2024-49138) and patched in the December 2024 Patch Tuesday release. Windows CLFS continues to be a popular attack vector for attackers and has been exploited by ransomware gangs.
CVE-2025-30400 | Microsoft DWM Core Library Elevation of Privilege Vulnerability
CVE-2025-30400 is an EoP vulnerability in the Windows Desktop Windows Manager (DWM) Core library. It was assigned a CVSSv3 score of 7.8 and is rated as important. Microsoft notes that it was exploited as a zero-day. Successful exploitation would allow an attacker to elevate their privileges by exploiting a use after free flaw.
This is the seventh EoP vulnerability in DWM Core Library patched this year. Eight DWM vulnerabilities were patched in 2024, including one zero-day vulnerability that was actively exploited (CVE-2024-30051) and patched in the May 2024 Patch Tuesday release.
CVE-2025-30397 | Scripting Engine Memory Corruption Vulnerability
CVE-2025-30397 is a memory corruption vulnerability in Microsoft Scripting Engine that can be exploited to achieve arbitrary code execution on a target machine. It was assigned a CVSSv3 score of 7.5 and is rated as Important. The attack complexity is rated as high, and Microsoft notes the target must first be running Microsoft Edge in Internet Explorer mode. Successful exploitation requires the user to click on a crafted URL. This vulnerability was reportedly exploited in the wild as a zero-day.
CVE-2025-26685 | Microsoft Defender for Identity Spoofing Vulnerability
CVE-2025-26685 is a spoofing vulnerability in Microsoft Defender for Identity. It was assigned a CVSSv3 score of 6.5 and is rated as Important. This vulnerability allows an unauthenticated attacker with Local Area Network (LAN) access to perform a spoofing attack. According to Microsoft, this vulnerability was disclosed prior to patches being made available.
CVE-2025-32709 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
CVE-2025-32709 is a EoP vulnerability in the Windows Ancillary Function Driver for WinSock. It was assigned a CVSSv3 score of 7.8 and rated as Important. An authenticated attacker can leverage this vulnerability to elevate their privileges to administrator by exploiting a user after free condition. Microsoft notes that this vulnerability was exploited in the wild as a zero-day, the second to be exploited in 2025, preceded by CVE-2025-21418 which was addressed in February’s Patch Tuesday release.
CVE-2025-32702 | Visual Studio Remote Code Execution Vulnerability
CVE-2025-32702 is a RCE vulnerability in Visual Studio. It was assigned a CVSSv3 score of 7.8 and rated as Important. Microsoft notes that the attack vector for this vulnerability is local, and that an unauthenticated attacker could exploit this flaw in order to execute code. This is the third RCE vulnerability in Visual Studio that was patched in 2025.
Tenable Solutions
A list of all the plugins released for Microsoft’s May 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's May 2025 Security Updates
- Tenable plugins for Microsoft May 2025 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
![]()
Tenable Security Response Team
Tenable Security Response Team
The Tenable Security Response Team (SRT) tracks threat and vulnerability intelligence feeds to ensure our research teams can deliver sensor coverage to our products as quickly as possible. The SRT also works to analyze and assess technical details and writes white papers, blogs and additional communications to ensure stakeholders are fully informed of the latest risks and threats. The SRT provides breakdowns for the latest vulnerabilities on the Tenable blog.
- Exposure Management
- Vulnerability Management
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
