
Tenable Research发布检测插件,用于识别攻击者利用的远程监控和管理(RMM)工具风险,并提供防御策略和多种插件支持。 2025-5-12 15:0:0 Author: www.tenable.com(查看原文) 阅读量:14 收藏

Following up on last year’s LOLDriver plugin, Tenable Research is releasing detection plugins for the top Remote Monitoring and Management (RMM) tools that attackers have been more frequently leveraging in victim environments.
Background
In August 2024, Tenable Research released a detection plugin for Nessus, Tenable Security Center and Tenable Vulnerability Management to help customers identify risky third-party Windows drivers utilized by attackers for privilege escalation on victim hosts. As part of our continued research into living off the land (LOTL) tooling utilized by attackers, we’re releasing new detection plugins for popular Remote Monitoring and Management (RMM) applications.
Increased risk from RMM tools
IT operations and information security staff often need to remotely connect to machines dozens, perhaps even hundreds, of times per day to troubleshoot a problem or make a system function well. An administrator or support technician must reach a terminal on a server in a datacenter a continent away, or a user’s workstation in their home. As the role of the remote worker has dramatically expanded across organizations over the last 20 years, it has led to the introduction of RMM products in enterprise environments.
The architecture of these products is fairly straightforward: a listener on the user’s machine, often referred to as an agent, host, or server, and an application to connect to, and control, the machine, often referred to as a viewer or client. In many cases this connection is facilitated by a proxy system, which maintains an inventory of the available machines in the environment, allowing an administrator to select one from a list, use stored credentials and track the health of the listeners. This proxy system might be on-premises, in the cloud, or hosted by the RMM vendor as a SaaS application.
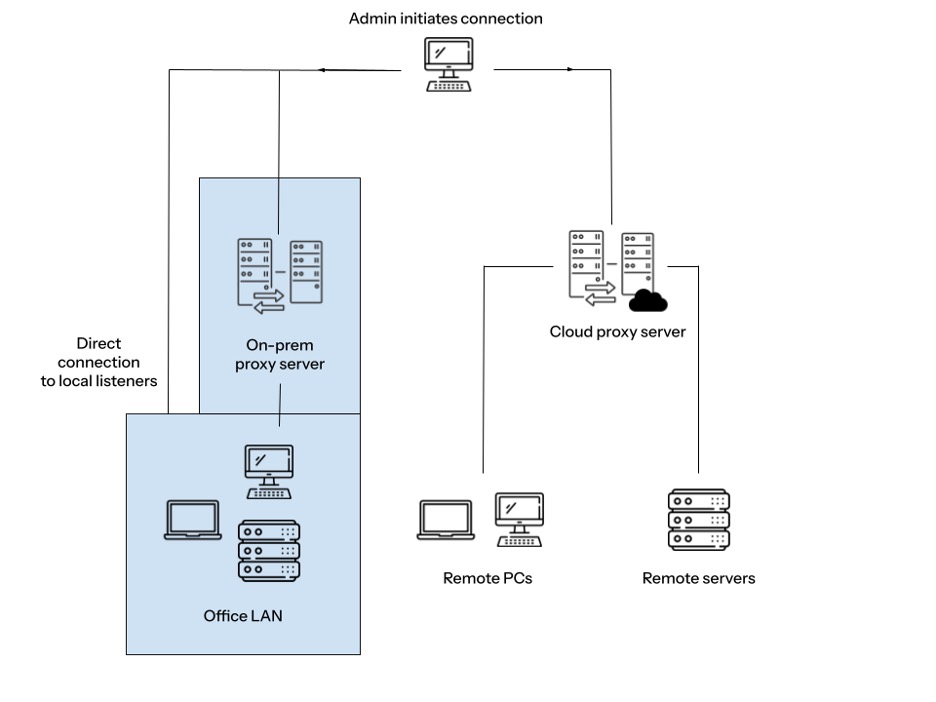
While these tools may sound handy, attackers also know that these tools are present. They can use them for direct graphical control of a victim’s machines, often at a privilege level that is elevated by design. So, how do attackers get their hands on such a valuable resource?
Attack scenarios for RMM tools
There are several ways an attacker can obtain access to an organization’s RMM tools:
- Credential reuse. The attacker steals credentials belonging to a privileged user, either through social engineering, theft from the user’s workstation or control of an identity service. These credentials are used to authenticate to the RMM central service or to simply connect directly to a listener.
- Exploitation of a vulnerability in the RMM product. Many RMM applications have highly publicized vulnerabilities that allow elevation of privilege or remote code execution.
- Elevation of privilege. An attacker may gain control of a workstation or server used by an administrator and launch the RMM client application from there using the legitimate access of that administrator.
And, of course, attackers with sufficient privileges can simply deploy a RMM tool of their choice on a compromised asset, allowing them to achieve persistence and remote command and control. The nature of modern RMM tool design allows attackers, in some cases, to do monitor and control an asset without formally installing a software package, which might trigger an alert to the organization’s security team.
Defensive strategies for unauthorized RMM tool use
A mature security program will update the organization’s protective, monitoring and response approach to address the risk presented by RMM tools. Some of these strategies include:
- Selecting an authorized RMM product or suite for the organization. This will allow security teams that inventory software on their assets to quickly spot the use of unauthorized RMM tools, which might have been introduced by an attacker.
- Auditing the use of the authorized RMM product. Have administrators that use the tools regularly review reports of sessions performed to ensure no unauthorized activity has occurred. Investigate these unauthorized sessions as soon as possible after detection.
- Reviewing network traffic between assets (especially remote assets) and the internet. Identify connections to known RMM tool websites, e.g., downloading of the tools or access to a proxy or management site.
- Scanning the environment to look for listening services. This strategy can be used to identify services belonging to RMM tools.
How can Tenable customers mitigate the risk of RMM tools?
Tenable has several existing plugins that can detect several different varieties of RMM tools. These include:
- Intelligent Platform Management Interface (IPMI) tools like iDRAC, iLO, ILOM and CIMC, as well as broader detection for any service running the IPMI protocol
- Systems management suites like Microsoft Configuration Manager, BigFix, Altiris, Tanium, LanDesk / Ivanti EM, Workspace ONE UEM / AirWatch, ManageEngine Endpoint Central and JAMF.
- Collaboration tools (yes, attackers use these, too) like Zoom, Teams and WebEx.
Tenable is also releasing a number of Nessus plugins to detect many commonly used commercial and open source RMM or Remote Access Tool products:
| Product | Plugins |
| TeamViewer | 52715, 206009 105111,121245 |
| RemotePC | 232745, 232746, 232747 |
| Pritunl | 232836, 232837, 232838, 232839 |
| Google Chrome Remote Desktop | 232692, 232693, 232694 |
| Duet Display | 232296, 232295 |
| Connectwise ScreenConnect | 192391, 190883, 190894 |
| Apache Guacamole | 232291 |
| JumpDesktop | 232297, 232298 |
| TSplus Remote Access | 232591 |
| AnyViewer | 232316, 232315 |
| Parsec Remote Access | 232649, 232651, 232650, |
| VNC Connect | 232582, 232580, 232581 |
| Termius | 232292, 232293, 232294 |
| LogMeIn | 232654, 122754 |
| GoodAccess | 233552, 233553, 233554 |
| ISL Light | 232853, 232854, 232855 |
| OpenVPN | 154346, 191048, 125356, 56022, 107073, 232856, 232857 |
| NoMachine Remote Access | 233323, 233324, 233325 |
| RustDesk Remote Desktop | 233292, 233291, 233288, 233289, 233290 |
| Remote Utilities | 233555, 233556, 233557 |
| WinGate | 234718 |
| AirDroid | 233774, 233775, 233776 |
| AnyDesk | 189953, 189955, 189973 |
There are also Nessus Web App Scanning plugins for many of these applications, which can help detect the applications’ web UI when detecting the service locally isn’t an option.
A new scan template, Remote Monitoring and Management, has been created in Tenable Nessus to check for this set of RMM products. Customers can use the scan template to ensure that the instances they find are authorized for use in the organization. It is strongly recommended to scan with credentials, so that more exhaustive searches for these products can be performed.
Future development
IT operations and support teams will continue to rely on RMM tools for productivity benefits even as attackers increasingly exploit them. Tenable anticipates that new RMM solutions will emerge and major systems management suites will further integrate remote-control capabilities directly into their platforms.
Meanwhile, vulnerability and threat intelligence researchers will keep their focus on the tools, identifying weaknesses and opportunities for exploitation as well as attacker-usage of such tools. As additional vulnerabilities are discovered and new threat intelligence reports reveal usage of new and existing tools, Tenable plans to publish detection and vulnerability plugins to find them. Given this growing space, organizations must remain vigilant, ensuring continuous monitoring, timely patching and strong security practices around RMM tools.
- Exposure Management
- Vulnerability Management
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
如有侵权请联系:admin#unsafe.sh