OtterCookie是一种由朝鲜威胁组织WaterPlum开发的高级恶意软件,在多次升级后增强了跨平台能力和凭证窃取功能。该恶意软件主要针对全球金融机构、加密货币运营商和金融科技公司,并通过多个版本持续改进其攻击手段。 2025-5-8 20:18:14 Author: cybersecuritynews.com(查看原文) 阅读量:6 收藏
A sophisticated malware known as OtterCookie, attributed to the North Korean threat actor WaterPlum (also called Famous Chollima or PurpleBravo), has received significant upgrades that enhance its cross-platform capabilities and credential theft functions.
First observed in September 2024, this malware has evolved through multiple versions with the latest iteration appearing in April 2025, demonstrating the threat actor’s continued focus on targeting financial institutions, cryptocurrency operators, and FinTech companies worldwide.
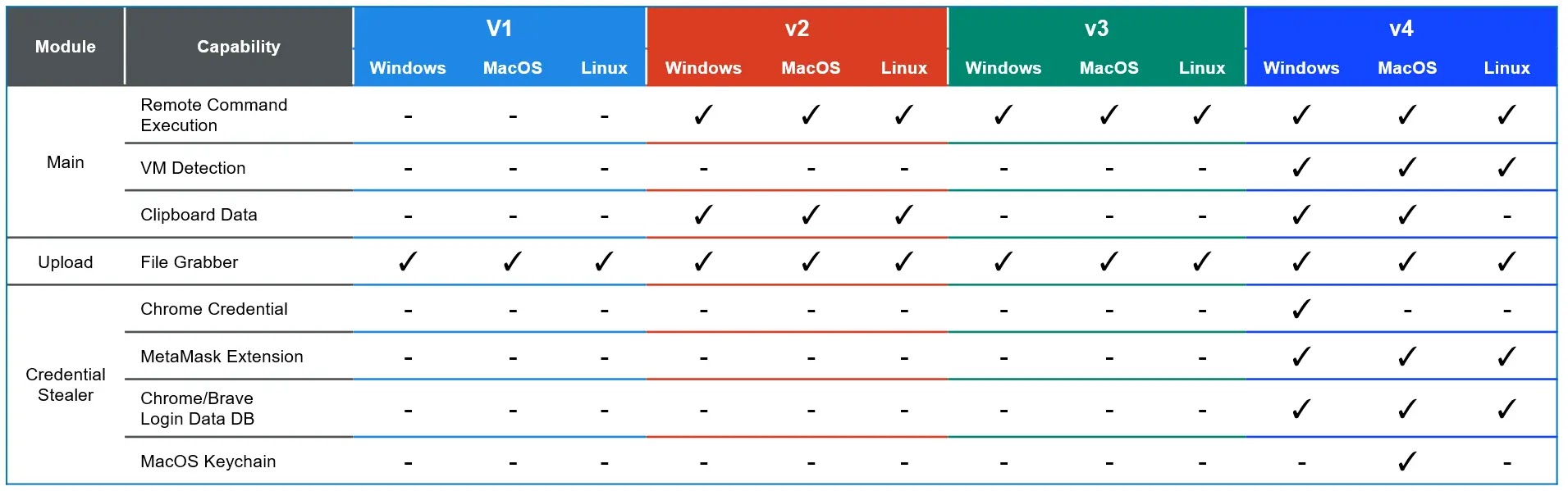
The malware’s evolution has been methodical, with researchers tracking its development through four distinct versions.
Initially deployed as part of the “Contagious Interview” campaign that began in 2023, WaterPlum transitioned from using BeaverTail malware to OtterCookie in late 2024, signaling a strategic shift in their attack methodology.
The ongoing development of this malware indicates the group’s persistent efforts to circumvent security measures and maintain persistence within compromised environments.
NTT Security researchers identified this threat through continuous monitoring of WaterPlum’s activities, noting that the threat actor is actively upgrading the malware’s capabilities while maintaining operations.
According to their analysis, the transition timeline shows version migration occurring approximately every two to three months, with both v3 and v4 currently active in the wild as of May 2025.
The latest incarnations of OtterCookie demonstrate enhanced cross-platform versatility, with tailored modules designed to function across Windows, macOS, and Linux environments.
This multi-platform approach represents a significant evolution in the threat landscape, as many malware variants typically focus on a single operating system environment.
Credential Theft Mechanisms
The most notable enhancement in OtterCookie v4 is its sophisticated credential stealing capabilities.
.webp)
The malware now incorporates specialized Stealer modules that specifically target browser credentials and cryptocurrency wallets.
One module focuses on decrypting Google Chrome’s stored passwords using Windows Data Protection API (DPAPI), extracting login credentials, and storing them temporarily in a local database file (“\AppData\Local\1.db”) for exfiltration.
Interestingly, the second Stealer module takes a different approach, collecting encrypted credential data from Google Chrome, Brave browser, and the MetaMask cryptocurrency wallet extension without decrypting it locally.
This difference in implementation suggests multiple developers may be involved in the malware’s creation, as noted by the NTT researchers in their technical analysis.
The module also targets the macOS Keychain, demonstrating the threat actor’s comprehensive approach to credential theft across platforms.
.webp)
The malware further enhances its operational security through new virtual environment detection capabilities, allowing it to identify when it’s running in a security sandbox and potentially alter its behavior accordingly.
Additionally, clipboard monitoring functionality has been refined to use native operating system commands rather than third-party libraries, making detection more difficult.
Are you from the SOC and DFIR Teams? – Analyse Real time Malware Incidents with ANY.RUN -> Start Now for Free.
如有侵权请联系:admin#unsafe.sh

.png
)