文章指出黑客激进分子正转向更复杂的网络攻击方式,包括关键基础设施破坏和勒索软件活动。2025年第一季度数据显示,支持俄罗斯的黑客团体最为活跃,主要针对北约国家及乌克兰支持者。能源、政府等关键行业成为主要目标。同时,多向量协同攻击增多,网络安全威胁加剧。 2025-4-15 08:30:59 Author: cyble.com(查看原文) 阅读量:16 收藏
Overview
According to a new Cyble report, hacktivists are increasingly moving beyond traditional activities like DDoS attacks and website defacements into more sophisticated critical infrastructure and ransomware attacks.
In a report for clients, Cyble said hacktivism has “transformed into a complex instrument of hybrid warfare” with the rise of groups that have adopted more sophisticated attack techniques more typically associated with nation-state actors and financially motivated threat groups.
Hacktivism “is no longer confined to fringe ideological outbursts,” the report said. “It is now a decentralized cyber insurgency apparatus, capable of shaping geopolitical narratives, destabilizing critical systems, and directly engaging in global conflicts through the digital domain.”
The Cyble report looked at the most active hacktivist groups in the first quarter of 2025, the most targeted nations and sectors, emerging attack techniques, and more.
Most Active Hacktivist Groups Target Critical Infrastructure
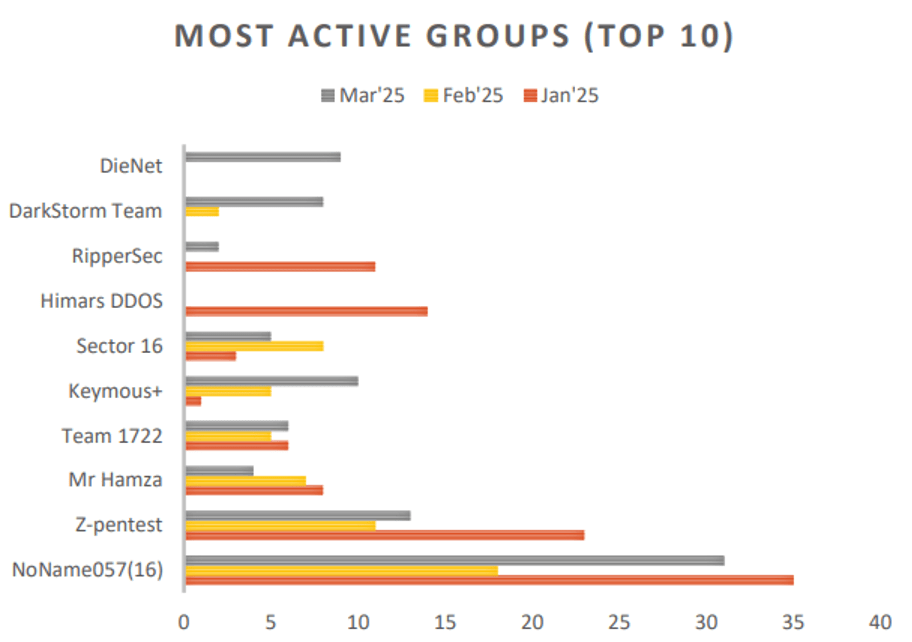
Pro-Russian hacktivists were the most active in the first quarter, led by NoName057(16), Hacktivist Sandworm, Z-pentest, Sector 16, and Overflame. The groups primarily targeted NATO-aligned nations and Ukraine supporters.
Russia-linked groups are increasingly targeting critical infrastructure. Hacktivist attacks on Industrial Control Systems (ICS) and Operational Technology (OT) surged 50% just in the month of March, Cyble said, as “Pro-Russian actors increasingly exploited internet-facing ICS/OT for wider political and economic impact.”
Multi-vector and coalition attacks have also become more common. Groups have combined DDoS, credential leaks, and ICS disruption to bypass single-layer defenses—an evolution Cyble predicted in its 2024 Annual Report.
Meanwhile, pro-Ukrainian, pro-Palestinian, and anti-establishment hacktivists targeted Russia, Israel, and the United States, often aligning their campaigns with conflict developments, elections, or other events.
A look at the most active hacktivist groups in the first quarter also shows consistent activity by Mr Hamza, Team 1722, and Keymous+ (chart below).

Most Targeted Sectors and Countries
The sectors most targeted by hacktivists in the first quarter of 2025 were government and law enforcement, banking and financial services, telecom, and energy and utilities. NoName057(16) “continued to orchestrate and instigate attacks on multiple sectors,” Cyble said.
The energy and utilities sector was the dominant target for ICS attacks, with notable attacks on energy distribution and water utilities, “reflecting a strategic focus to disrupt infrastructure tied to national resilience and service delivery,” the report said.
India experienced the highest number of incidents in January, with reduced levels in subsequent months. These attacks likely align with the country’s growing strategic visibility and regional rivalries.
Israel remained a persistent target, with a major spike in March, largely driven by pro-Palestinian hacktivist groups responding to continued hostilities in Gaza and broader Middle Eastern unrest.
The U.S. experienced a noticeable increase in attacks in March, correlated with early actions by the new Trump Administration that have included U.S. strikes in Yemen and import tariffs.
NATO countries, most notably France, Italy, and Spain, faced sustained attacks by hacktivists. Spain’s sharp increase in attacks in March reflects a broader trend of hacktivist reprisals against NATO members for their continued political, financial, and military support for Ukraine.
Ransomware, SQL Injection Attacks Among Hacktivist Activities
Cyble observed at least eight hacktivist groups and their allies “embracing ransomware as a tool for ideological disruption” in the first quarter. Among the incidents were:
Ukraine-aligned group BO Team conducted a ransomware attack on a Russian industrial manufacturer allegedly linked to the Ministry of Defense. The operation encrypted over 1,000 hosts and 300TB of data, culminating in a $50,000 Bitcoin ransom payment. The incident “highlights the growing overlap between hacktivist motivation and cybercriminal methodology,” Cyble said.
Yellow Drift targeted Russian government platforms and claimed several attacks during the quarter. Notably, the group compromised over 250TB of government data from the Tomsk region and 550TB from the national e-procurement system.
The pro-Ukrainian hacktivist group known as C.A.S. carried out a coordinated cyber operation against a Russian technology firm. The attackers claim to have exfiltrated approximately 3 terabytes of internal corporate data, including source code, accounting records, employee documents, and internal network documentation. The group reported that they partially destroyed the company’s infrastructure, targeting Windows and Linux Mint workstations, database servers, development environments, and backup systems.
Moroccan Dragons announced the development of a proprietary ransomware program named M-DragonsWare. The statement was shared via their Telegram channels, though no technical specifications or intended deployment targets have been disclosed.
Cyble also observed several hacktivist groups engaged in more sophisticated website attacks, including SQL Injection attacks, brute forcing internet-exposed web panels to gain illicit access to data, exploiting OWASP vulnerabilities in web panels to steal data, and Dorking to discover misconfigured or internet-exposed databases. ParanoidHax, THE ANON 69, Indohaxsec, and Defacer Kampung were observed promoting data leaks on their Telegram channels.
Conclusion
The growing sophistication of hacktivist groups is narrowing the gap between nation-state and financially motivated threat actors and increasing risk for organizations in regions with geopolitical conflicts, such as the U.S., Europe, Asia, and the Middle East.
To guard against these growing risks, organizations should implement cybersecurity best practices such as network segmentation, Zero Trust, risk-based vulnerability management, ransomware-resistant backups, protecting web-facing assets, and network, endpoint, and cloud monitoring.
Cyble’s comprehensive attack surface management solutions can help by scanning network and cloud assets for exposures, prioritizing fixes, and monitoring for leaked credentials and other early warning signs of major cyberattacks.
如有侵权请联系:admin#unsafe.sh