The Tycoon 2FA phishing kit employs advanced evasion techniques, including invisible Unicode characters for JavaScript obfuscation, a custom HTML5 canvas CAPTCHA to bypass detection, and anti-debugging scripts to hinder analysis. These methods enhance stealth, prolong campaign lifespans, and challenge defenders' ability to detect and respond effectively. 2025-4-10 16:34:24 Author: www.trustwave.com(查看原文) 阅读量:9 收藏
3 Minute Read
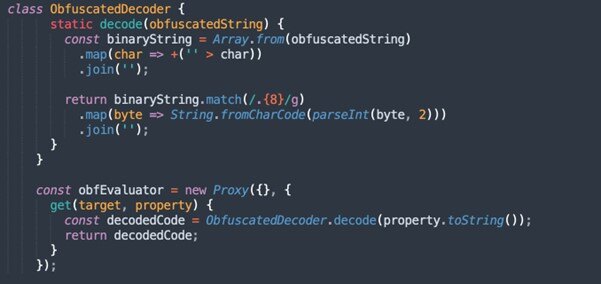
The Tycoon 2FA phishing kit has adopted several new evasion techniques aimed at slipping past endpoints and detection systems. These include using a custom CAPTCHA rendered via HTML5 canvas, invisible Unicode characters in obfuscated JavaScript, and anti-debugging scripts to thwart inspection. This blog takes a closer look at these methods to better understand how this kit is evolving and what defenders should be aware of. Lately, the Tycoon 2FA landing pages have incorporated a clever obfuscation technique using invisible Unicode characters. This technique, when paired with JavaScript Proxy objects, is designed to complicate static analysis and defer script execution until runtime. This behavior is demonstrated in a real-world Tycoon 2FA phishing landing page, as shown in this Urlscan.io session: https://urlscan.io/result/0195c73f-bfd0-7000-8386-94b11ace6088/dom/ Tycoon is using specific invisible Unicode characters to encode binary data: The screenshot below shows how these invisible Unicode characters are converted into their escaped Unicode representations using CyberChef: In figure 3, the encoded characters are joined into a binary string, which is then split into 8-bit segments (bytes). Each byte is then converted into its corresponding character. When an attacker wants to execute a script, they encode it using these invisible Unicode characters to represent binary. Here's the decoding mechanism: As you can see in figure 4, the property name on the obfEvaluator proxy becomes the carrier of the payload. Once accessed, it triggers the decoder and dynamically evaluates the reconstructed JavaScript code. This method: Combined with other evasion layers, this approach adds a frustrating layer of indirection for analysts and defenders. Previously, many phishing kits — including Tycoon 2FA — leaned on third-party CAPTCHA services like Cloudflare Turnstile. These services offered basic anti-bot protection, but they also introduced a weak point for defenders. Security teams could more easily fingerprint and block phishing pages using recognizable third-party elements. Tycoon has now pivoted to a custom CAPTCHA solution, likely in an attempt to reduce its detectability and increase friction for automated analysis tools. The CAPTCHA is rendered using an HTML5 canvas element with randomized characters, background noise, and slight distortions. Here's a simplified breakdown of how it works: If CAPTCHA verification fails, a new one is generated. If successful, it sends form data and fetches instructions from an attacker-controlled server. If the server responds with an error or a non-expected value, it injects a webpage using base64-decoded HTML, loading a decoy page. This technique is more than cosmetic; it helps Tycoon blend into legitimate login workflows while allowing the attacker to dynamically serve decoys or reroute victims. Tycoon 2FA also includes anti-debugging scripts to hinder researchers and slow down detection: This script: These layers of obfuscation and evasion make dynamic analysis harder and extend the lifespan of phishing campaigns. The recent updates to the Tycoon 2FA kit show a clear move toward stealth and evasion. While none of these techniques are groundbreaking individually, their combined use can complicate detection and response. Security teams should consider behavior-based monitoring, browser sandboxing, and a deeper inspection of JavaScript patterns to stay ahead of these tactics.1. Obfuscation Using Invisible Unicode Characters and Proxies

Figure 1. Tycoon 2FA using invisible Unicode characters to encode JavaScript code. The obfuscation is actually quite simple but clever.
0x3164E3 85 A4
Figure 2. Escaping the invisible Unicode characters in this sample reveals a series of UTF-16 values ‘\uFFA0’ for binary 0 and ‘\u3164’ for binary 1.
Figure 3. Diagram of the decoding process.
Figure 4. Snippet of the decoding mechanism.
2. From Cloudflare Turnstile to Custom CAPTCHA

Figure 5. Tycoon2FA new custom CAPTCHA solution.
Figure 6. Simplified version of the CAPTCHA mechanism.
Figure 7. Screengrab of the decoy page.3. Anti-Debugging JavaScript

Figure 8. Anti-debugging routine of the Tycoon 2FA phishing landing page.
What This Means for Defenders
YARA Detection Rule

Figure 9. YARA detection rule.CyberChef Recipe to Decode the Tycoon2FA Javascript

Figure 10. CyberChef Recipe to Decode the Tycoon2FA Javascript.
Figure 11. To use the recipe, click on "Load Recipe" and copy/paste the Recipe to the Recipe Form.
Figure 12. Paste the Tycoon2FA phishing landing page HTML source code to the CyberChef input form.
Sign up to receive the latest security news and trends straight to your inbox from Trustwave.Stay Informed
如有侵权请联系:admin#unsafe.sh