
微软在4月修复了121个CVE漏洞,包括一个被利用的零日,涉及Windows组件、Office套件及Azure服务等,其中40.5%为权限提升,25.6%为远程代码执行,重点修复了Windows CLFS驱动、远程桌面服务及LDAP相关漏洞,Tenable建议尽快修补并定期扫描环境以确保安全。 2025-4-8 18:36:40 Author: www.tenable.com(查看原文) 阅读量:154 收藏

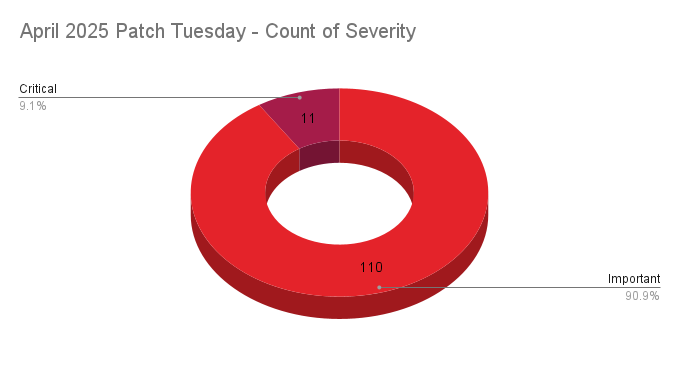
- 11Critical
- 110Important
- 0Moderate
- 0Low
Microsoft addresses 121 CVEs including one zero-day which was exploited in the wild.
Microsoft patched 121 CVEs in its April 2025 Patch Tuesday release, with 11 rated critical and 110 rated as important.
This month’s update includes patches for:
- ASP.NET Core
- Active Directory Domain Services
- Azure Local
- Azure Local Cluster
- Azure Portal Windows Admin Center
- Dynamics Business Central
- Microsoft AutoUpdate (MAU)
- Microsoft Edge (Chromium-based)
- Microsoft Edge for iOS
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office OneNote
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft Streaming Service
- Microsoft Virtual Hard Drive
- OpenSSH for Windows
- Outlook for Android
- Power Automate
- RPC Endpoint Mapper Service
- Remote Desktop Client
- Remote Desktop Gateway Service
- System Center
- Visual Studio
- Visual Studio Code
- Visual Studio Tools for Applications and SQL Server Management Studio
- Windows Active Directory Certificate Services
- Windows BitLocker
- Windows Bluetooth Service
- Windows Common Log File System Driver
- Windows Cryptographic Services
- Windows DWM Core Library
- Windows Defender Application Control (WDAC)
- Windows Digital Media
- Windows HTTP.sys
- Windows Hello
- Windows Hyper-V
- Windows Installer
- Windows Kerberos
- Windows Kernel
- Windows Kernel Memory
- Windows Kernel-Mode Drivers
- Windows LDAP - Lightweight Directory Access Protocol
- Windows Local Security Authority (LSA)
- Windows Local Session Manager (LSM)
- Windows Mark of the Web (MOTW)
- Windows Media
- Windows Mobile Broadband
- Windows NTFS
- Windows Power Dependency Coordinator
- Windows Remote Desktop Services
- Windows Resilient File System (ReFS)
- Windows Routing and Remote Access Service (RRAS)
- Windows Secure Channel
- Windows Security Zone Mapping
- Windows Shell
- Windows Standards-Based Storage Management Service
- Windows Subsystem for Linux
- Windows TCP/IP
- Windows Telephony Service
- Windows USB Print Driver
- Windows Universal Plug and Play (UPnP) Device Host
- Windows Update Stack
- Windows Virtualization-Based Security (VBS) Enclave
- Windows Win32K - GRFX
- Windows upnphost.dll
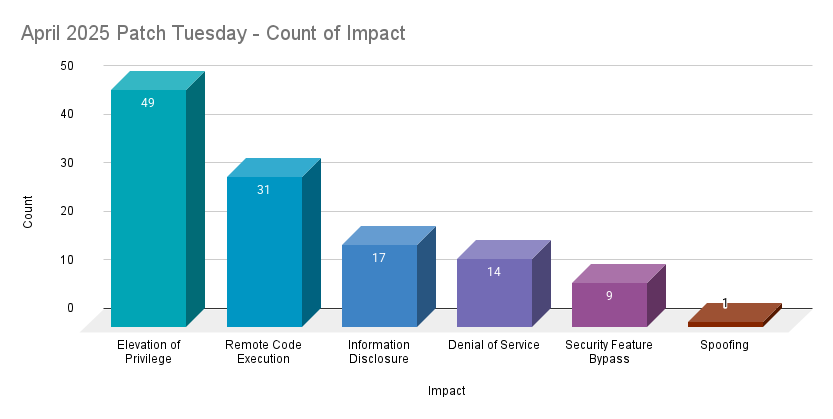
Elevation of privilege (EoP) vulnerabilities accounted for 40.5% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 25.6%.
CVE-2025-29824 | Windows Common Log File System Driver Elevation of Privilege Vulnerability
CVE-2025-29824 is an EoP vulnerability in the Windows Common Log File System (CLFS) Driver. It was assigned a CVSSv3 score of 7.8 and is rated as important. It was exploited in the wild as a zero-day. Microsoft identified this vulnerability in ransomware deployed by the PipeMagic malware via the group tracked as Storm-2460.
This is the second EoP vulnerability in the Windows CLFS driver patched in 2025. In 2024, there were eight CLFS vulnerabilities patched, including one zero-day vulnerability in the CLFS driver that was exploited (CVE-2024-49138) and patched in the December 2024 Patch Tuesday release. Microsoft has patched an average of 10 vulnerabilities per year in the CLFS driver since 2022. Windows CLFS continues to be a popular attack vector for ransomware.
CVE-2025-26671, CVE-2025-27482 and CVE-2025-27480 | Windows Remote Desktop Services Remote Code Execution Vulnerability
CVE-2025-26671, CVE-2025-27480 and CVE-2025-27482 are RCE vulnerabilities in Windows Remote Desktop Gateway Service. Each was assigned a CVSSv3 score of 8.1 and two were rated as critical, with CVE-2025-26671 having a rating of Important. To exploit these flaws, an attacker must be able to win a race condition. Despite this requirement, Microsoft assessed CVE-2025-27482 and CVE-2025-27480 as “Exploitation More Likely” according to Microsoft’s Exploitability Index.
Microsoft also patched an RCE vulnerability in Remote Desktop Client (CVE-2025-27487).
CVE-2025-26663 and CVE-2025-26670 | Multiple Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerabilities
CVE-2025-26663 and CVE-2025-26670 are critical RCE vulnerabilities affecting Windows Lightweight Directory Access Protocol (LDAP) and LDAP Client respectively. These vulnerabilities were assigned a CVSSv3 score of 8.1, rated as critical and assessed as “Exploitation More Likely" according to Microsoft. Successful exploitation of either requires winning a race condition via a specially crafted request resulting in a use after free. If successful, the attacker could achieve RCE on an affected host.
Microsoft also patched CVE-2025-26673 and CVE-2025-27469, two denial of service (DoS) vulnerabilities in LDAP. These were assessed as Important and “Exploitation Less Likely.”
CVE-2025-27740 | Active Directory Certificate Services Elevation of Privilege Vulnerability
CVE-2025-27740 is an EoP vulnerability affecting Active Directory Certificate Services. It was assigned a CVSSv3 score of 8.8 and is rated as important. According to Microsoft, successful exploitation would allow an attacker to gain domain administrator privileges by manipulating computer accounts. This vulnerability is assessed as “Exploitation Less Likely.”
A publicly disclosed zero-day vulnerability in Active Directory Certificate Services was also patched in November, 2024 (CVE-2024-49019). Active Directory remains a popular target for attackers.
CVE-2025-29793 and CVE-2025-29794 | Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2025-29793 and CVE-2025-29794 are RCE vulnerabilities affecting Microsoft SharePoint Server. The most severe of these vulnerabilities was assigned a CVSSv3 score of 8.8 and both were rated as important. Successful exploitation would grant an attacker the ability to execute arbitrary code. According to Microsoft, an attacker would need to be authenticated in order to exploit this vulnerability.
Microsoft has patched four vulnerabilities in SharePoint already this year, including three RCE vulnerabilities, and 20 vulnerabilities impacting SharePoint in 2024.
Tenable Solutions
A list of all the plugins released for Microsoft’s April 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's April 2025 Security Updates
- Tenable plugins for Microsoft April 2025 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
![]()
Tenable Security Response Team
Tenable Security Response Team
The Tenable Security Response Team (SRT) tracks threat and vulnerability intelligence feeds to ensure our research teams can deliver sensor coverage to our products as quickly as possible. The SRT also works to analyze and assess technical details and writes white papers, blogs and additional communications to ensure stakeholders are fully informed of the latest risks and threats. The SRT provides breakdowns for the latest vulnerabilities on the Tenable blog.
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
如有侵权请联系:admin#unsafe.sh