过去两周零日钓鱼攻击激增,主要针对微软、Outlook等平台的凭证。攻击者利用云存储服务隐藏恶意活动,传统安全软件未能检测。建议封锁域名、提醒用户风险、教育验证支持号码及启用多因素认证。 2025-3-19 02:3:52 Author: pixmsecurity.com(查看原文) 阅读量:26 收藏
Discover Pixm’s Latest Zero-Day Threat Intelligence Report
Wondering how we gather this critical information? Take a look at this video we’ve prepared to give you an inside view of how Pixm catches zero-day threats that evade traditional security measures like Bitdefender and Malware Bytes.
The past two weeks saw a record surge in zero-day spearphish targeting credentials from Microsoft and Outlook, as well as personal e-commerce, streaming and financial platforms like Amazon, Chase Bank, USAA, PayPal, and Netflix. Attackers employed sophisticated tactics, including delivering phishing links through fileshares and leveraging legitimate cloud hosting services like Backblaze. Consequently, the majority of cases remained entirely undetected by vendors on VirusTotal. Below are key highlights and examples of recent phishing activity.
Phishing URLs
Here is a list of examples of phishing websites that we discovered that we recommend you update your threat intelligence with these URLs.
lol[.]helivaroth[.]ru
live[.]microsoftreviews[.]org
cms-veps[.]com
share1nvite[.]es
authentication-logsid[.]jotacicli[.]com[.]br
beddube[.]s3[.]us-east-005[.]backblazeb2[.]com
r-0lm5-ld-k99z[.]com/chs/
chicagoiron[.]com/USAA/login[.]html
secureverisec[.]com
prime-siginapps[.]ecsauthsgonl[.]website
resolve-reportbillingnetflix-verificationcenter[.]cricketshoe[.]com
office[.]brasbaitss[.]store
v2k5c45hh7c[.]prenniumofs[.]com
i9sro5j6psl[.]prenniumofs[.]com
moreton[.]insurance42[.]site
canvas[.]cloudquell[.]de
websyncs[.]live/services[.]html
Microsoft and Outlook Credentials
A Microsoft credential harvester hosted on Backblase infrastructure was clicked by a staff member at a Texas organization on March 8, which was 100% undetected by VirusTotal vendors.
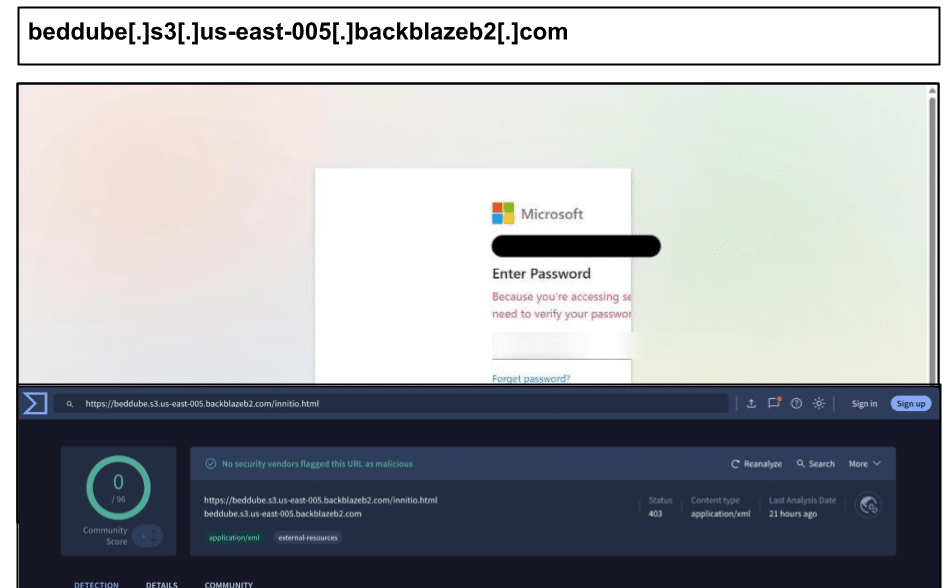
This credential harvester leveraged the reputation of a trusted cloud storage provider to remain undetected during this phishing attack. Earlier that week at the same organization, another staff member clicked the below Outlook credential harvester in a document share application.
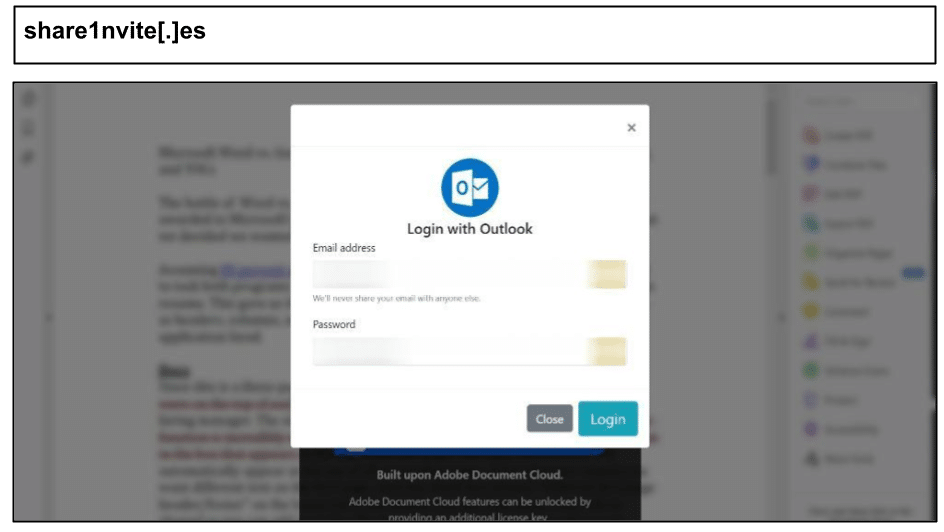
Examples like this are difficult to detect with traditional security architecture, because they are delivered and clicked outside the scope of corporate email protection. Overall, the period saw a record surge in clicks of zero day credential harvesters targeting Microsoft credentials by users in Texas, Kentucky, Florida, Washington, and Idaho.


In particular, on March 12 multiple users at a Washington organization clicked on phishing links hosted the domain prenniumofs[.]com. Other Microsoft credential harvesters clicked during the same period were hosted on Russian infrastructure.
Financial Services Phishing
This period saw a record surge in zero day phishing targeting financial services accounts like Chase, PayPal, and USAA.

Since these phishing links were delivered through personal email, they are outside the scope of corporate email protection. The Paypal phishing case includes a number of malicious scripts, a “vishing” component, and an attached error message: “Your account has been blocked due to some suspicious login attempts.” Cases like this scare recipients into taking action by claiming that their accounts are under threat.
E-Commerce and Streaming Phishing
The same period saw a steady stream of Amazon and Netflix phishing targeting users in Florida and Kentucky.

Suggested Actions
- Block the specified domains on corporate firewalls and endpoint security solutions.
- Remind users of phishing risks for their personal accounts they access even if they are on corporate devices
- Educate users to find the valid support number for their financial service institution via Google and not to call the number provided on an unverified web page
- Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.
If you would like a demo of Pixm to learn more about our AI technology and how we can help protect your customers, sign up here.
Questions or Feedback
PIXM Threat Research Team
[email protected]
如有侵权请联系:admin#unsafe.sh