OverviewThe UAE Cyber Security Council (CSC) has disclosed that the country faces ove 2025-3-4 09:46:14 Author: cyble.com(查看原文) 阅读量:26 收藏
Overview
The UAE Cyber Security Council (CSC) has disclosed that the country faces over 200,000 cyberattacks daily, primarily targeting strategic sectors. These cyberterrorist attacks originate from 14 countries, with their perpetrators and attack launch sites identified and countered using advanced global cybersecurity measures.
These attacks aim to disrupt critical infrastructure, steal sensitive data, and undermine national security. The CSC has implemented state-of-the-art threat detection and mitigation strategies to safeguard essential services and institutions from these cyber threats.
Strategic Sectors Under Attack
The CSC has reported that cyberterrorist groups primarily focus their attacks on key industries, aiming to disrupt operations and steal sensitive information. Among the affected sectors, the government sector accounted for the highest share at 30%, followed by the financial and banking sector at 7% and the education sector at 7%. Other affected industries, including technology, aviation, and hospitals, each experienced 4% of the attacks, while the remaining 44% were distributed among various other sectors.
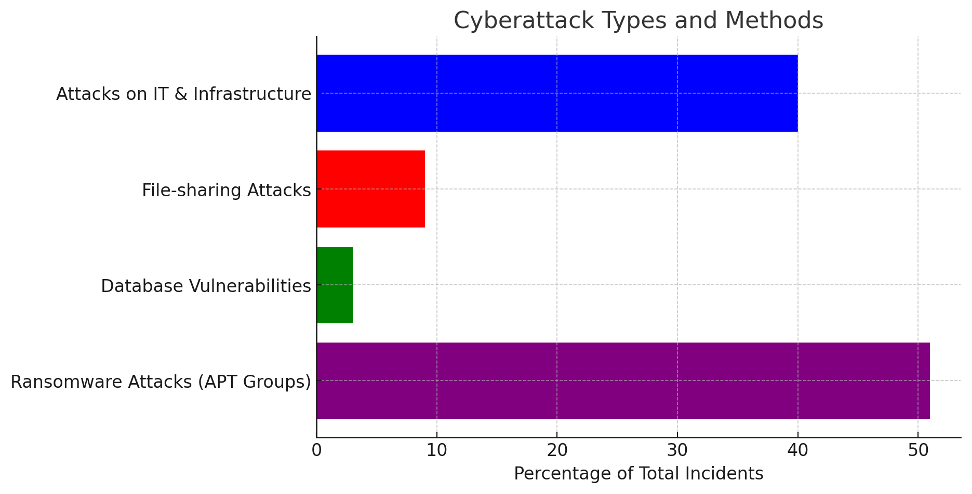
Cyberattack Types and Methods
Cyberattacks come in various forms, each posing unique threats to digital infrastructure. The CSC identified several key attack types:
- Attacks on Information Technology and Infrastructure – 40% of total incidents
- File-sharing Attacks – 9%
- Database Vulnerabilities – 3%
- Ransomware Attacks by Persistent Threat Groups (e.g., Blackcat) – 51% of ransomware cases
Below is the graphical representation of different types of cyberattacks and their proportions:

Common Vulnerabilities and Entry Points
The UAE’s national cybersecurity systems have pinpointed common vulnerabilities exploited by cyber terrorists:
- Incorrect configurations – 27% of incidents
- Malware infections – 22%
- Scanning and unauthorized login attempts – 15%
- Illegal activities and web attacks – 11%
- Phishing scams – 10%
These weaknesses highlight the need for organizations to adopt stringent cybersecurity protocols to safeguard their systems. Below is the graphical representation of common vulnerabilities exploited by cyber terrorists:

Most Dangerous Hacking Methods
The CSC has successfully countered several highly sophisticated cyberattack techniques used against the UAE’s key sectors. The most dangerous methods include:
- Denial-of-service (DoS) attacks – Targeting endpoint devices (39%)
- Encryption and data leakage attacks – (37%)
- Internet-connected application breaches – (24%)
- Ransomware attacks – (7%)
- Other cyber threats – (11%)
Artificial Intelligence and Cybersecurity Challenges
In addition to traditional cyber threats, AI-driven attacks have become a growing concern. The CSC has detected increasingly complex breach attempts leveraging AI technologies, which make attacks more sophisticated and harder to detect. These threats include:
- AI-enhanced malware, including ransomware
- Deepfake technology used for social engineering attacks
- Automated hacking techniques that bypass traditional security measures
The CSC warns that AI-driven cyber threats will continue to rise, making it imperative for organizations to implement advanced cybersecurity defenses.
Continuous Cybersecurity Efforts and Future Threats
The UAE Cyber Security Council emphasizes that cyberattacks are expected to persist and evolve throughout the year. With the rapid adoption of modern technologies, cybercriminals are refining their attack methods. While traditional threats like phishing and social engineering remain prevalent, emerging AI-driven attacks demand more sophisticated countermeasures.
To mitigate risks, the CSC urges all government and private entities to adhere to stringent cybersecurity standards and best practices. This includes implementing strong security protocols, conducting regular vulnerability assessments, and raising awareness about potential cyber threats.
Conclusion
Every day, as cybercriminals attempt to infiltrate, disrupt, and steal, the UAE Cyber Security Council stands as an impenetrable shield, stopping over 200,000 attacks with precision and expertise. This is not just a story of cyber resilience—it’s a testament to innovation, strategic defense, and a commitment to securing the nation’s digital future.
The cyber battlefield is evolving, from AI-driven threats to ransomware campaigns, but so is the UAE’s determination. The country is setting a new gold standard in cybersecurity by staying ahead of adversaries through cutting-edge technology, proactive security measures, and global cooperation.
References:
Related
Disclaimer: This blog is based on our research and the information available at the time of writing. It is for informational purposes only and does not constitute legal, financial, or professional advice. While we strive for accuracy, we do not guarantee the completeness or reliability of the content. If any sensitive information has been inadvertently included, please contact us for correction. Cyble is not responsible for any errors, omissions, or decisions made based on this content. Readers should verify findings and seek expert advice where necessary. All trademarks, logos, and third-party content belong to their respective owners and do not imply endorsement or affiliation. All content is presented “as is” without any guarantee that it is free of confidential, proprietary, or otherwise sensitive information. If you believe any portion of this content contains inadvertently shared or sensitive data, please contact us immediately so that we may address and rectify the issue. No Liability for Errors or Omissions Due to the dynamic nature of cyber threat activity, this [blog/report/article] may include partial, outdated, or otherwise incorrect information due to unverified sources, evolving security threats, or human error. We expressly disclaim any liability for errors or omissions or any potential consequences arising from the use, misuse, or reliance on this information.
如有侵权请联系:admin#unsafe.sh