
过去两周针对微软、谷歌和雅虎账户的钓鱼活动增加,攻击者利用非邮件通讯工具和地理位置相关URL提升可信度。涉及多个钓鱼网站案例,并建议封锁特定域名、加强安全意识及启用多因素认证以降低风险。 2025-2-28 03:1:4 Author: pixmsecurity.com(查看原文) 阅读量:35 收藏
Overview
Over the past two weeks, we observed a rise in phishing activity targeting Microsoft, Google, and Yahoo accounts. Attackers leveraged techniques to flank corporate email protection, like using non-email messenger apps and filesharing tools. They also put geographically targeted content into the URLs to increase their credibility to their target organizations. Below are key highlights and examples.
Phishing URLs
Here is a list of examples of phishing websites that we discovered that we recommend you update your threat intelligence with these URLs.
office365[.]dicoveryeducation[.]com/learn/videos/b4e519a8-c021-463a-b1bd-3a5d94e356c/
yc[.]mangropo[.]ru/RRMXKEXBJGRwc1rxzs03tm6y?PYHYYCKWANKEAJBW
kyschools[.]hostingclouddocs[.]com/aFS2u/
earley.hostingclouddocs.com/luh0G/
voicemailreceived[.]surge[.]sh/
a5nip2p6bz[.]loclx[.]io/login[.]html
celeberatewwithus[.]de/johs/invite/Yahoo[.]html
page[.]sign-in[.]attack-securecurrently[.]50-6-205-107[.]cprapid[.]com/security-check/signin/pwd
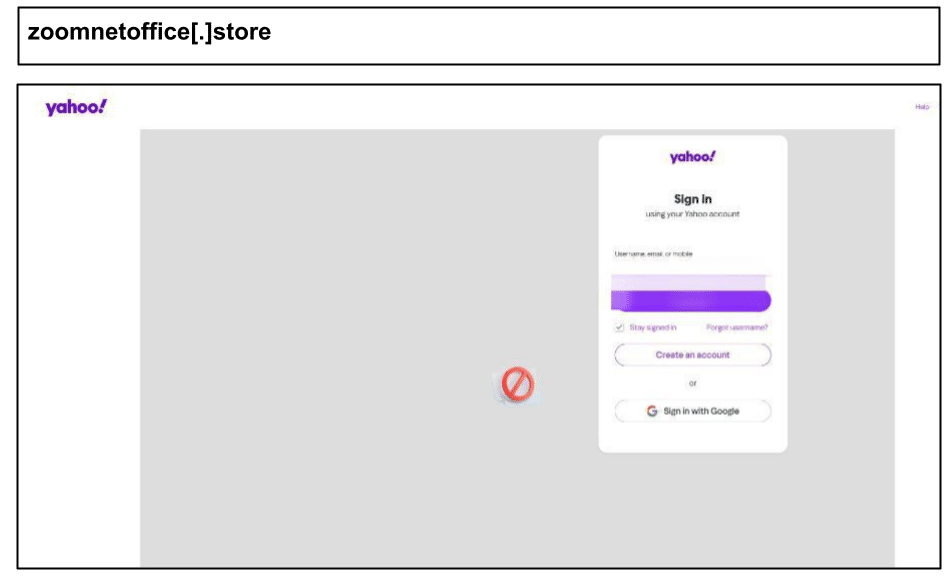
zoomnetoffice[.]store
unblocker[.]chesse[.]ip-ddns.com/
7f4f54-cloud[.]webnotifications[.]net/6448adaa99…
Microsoft Credential Harvesting Campaign
On February 5, a staff member at a Kentucky organization clicked a spearphishing link:

Hosted on Russian infrastructure, the link content suggests the use of a domain generator algorithm used to rapidly spin up and down similar websites.
Between February 6 and February 13, six additional staff members at another organization in Kentucky fell victim to a similar phishing attack:
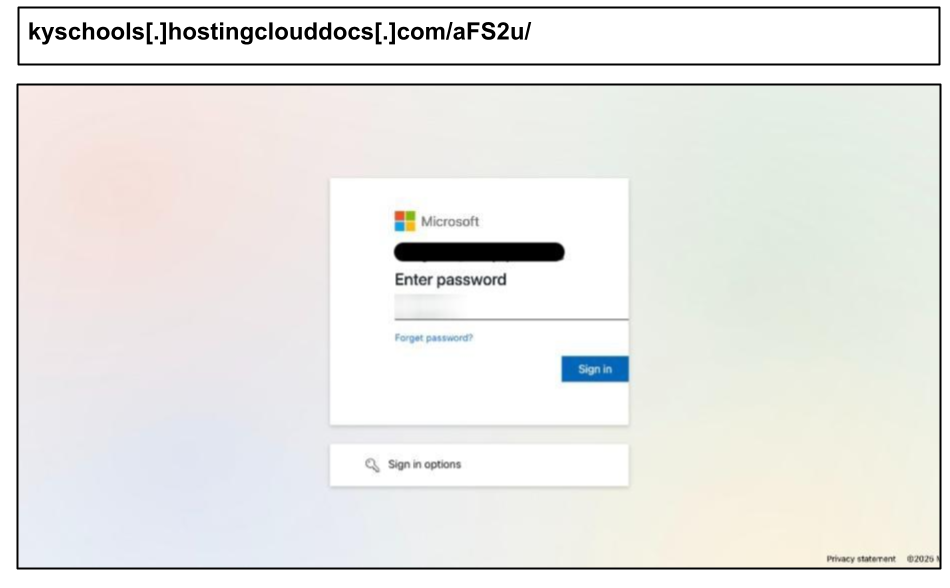
This attack included ‘kyschools’ in the domain to give credence to school-affiliated users in the region. An additional instance was observed when a different staff member at the same organization clicked: earley[.]hostingclouddocs[.]com/luh0G/. The reference to a cloud-based file service suggests the attack likely leveraged a fake document-sharing prompt to steal credentials.
Instagram Phishing Attacks
On February 9, a staff member at a Georgia organization clicked a phishing link impersonating Instagram:
This attack was likely clicked in Instagram’s native messenger app, falling entirely outside the scope of traditional security architecture.
Similar cases targeting personal accounts were observed targeting Yahoo and Google accounts on work devices.
Yahoo Credential Harvesting
On February 12, a staff member at a Kentucky organization clicked a spearphishing link mimicking a Yahoo login page:
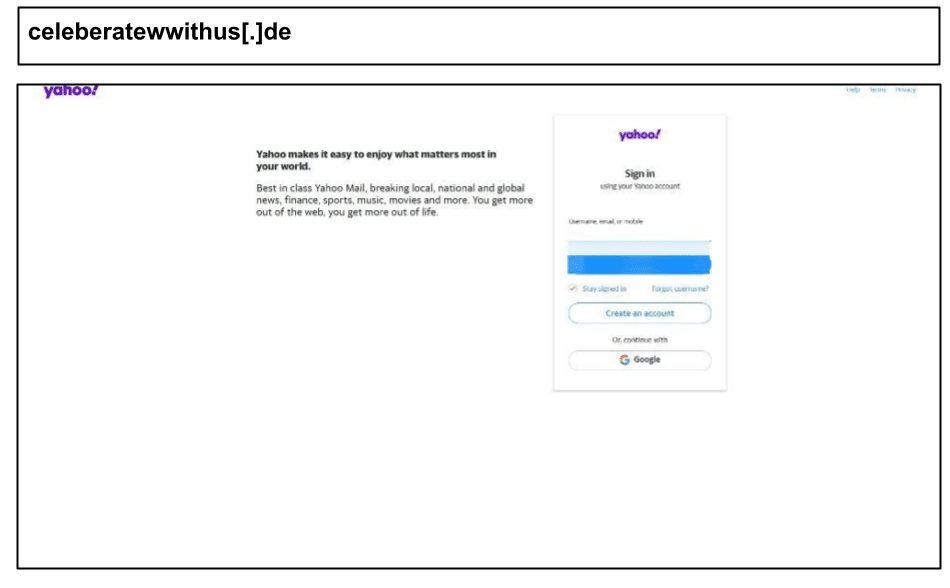
Even five days later, the attack remained undetected by VirusTotal. Additionally, on the same day, another phishing link targeting Yahoo users was clicked:
Google Account Phishing
On February 12, a phishing attack targeting Google accounts was clicked by a staff member in Kentucky:
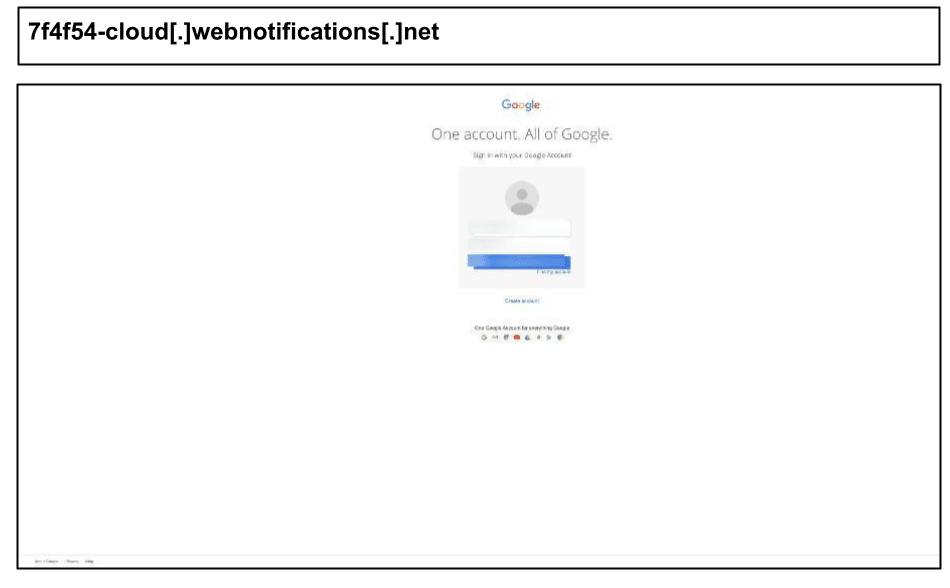
The URL structure suggests an attempt to mimic a security alert or cloud-based notification, increasing the likelihood of engagement.
Suggested Actions
- Block the specified domains on corporate firewalls and endpoint security solutions.
- Increase awareness on credential phishing targeting personal applications like Instagram, Google, and Yahoo logins.
- Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.
If you would like a demo of Pixm to learn more about our AI technology and how we can help protect your customers, sign up here.
Questions or Feedback
PIXM Threat Research Team
[email protected]
如有侵权请联系:admin#unsafe.sh
