过去两周网络钓鱼活动激增,攻击者利用云平台托管钓鱼页面绕过检测机制。目标包括Instagram、微软和花旗银行等平台,并出现大量恶意软件。建议封锁相关域名并加强员工安全意识教育。 2025-2-6 02:31:48 Author: pixmsecurity.com(查看原文) 阅读量:42 收藏
Overview
The past two weeks saw a spike in phishing activity targeting platforms like Instagram, Microsoft and Chase Bank. Attackers leveraged sophisticated tactics, including hosting phishing pages on legitimate cloud platforms, enabling them to bypass traditional detection mechanisms. We also saw a massive surge in malware hosted on Azure infrastructure. Below are key highlights and examples of recent phishing activity.
Phishing URLs
Here is a list of examples of phishing websites that we discovered that we recommend you update your threat intelligence with these URLs.
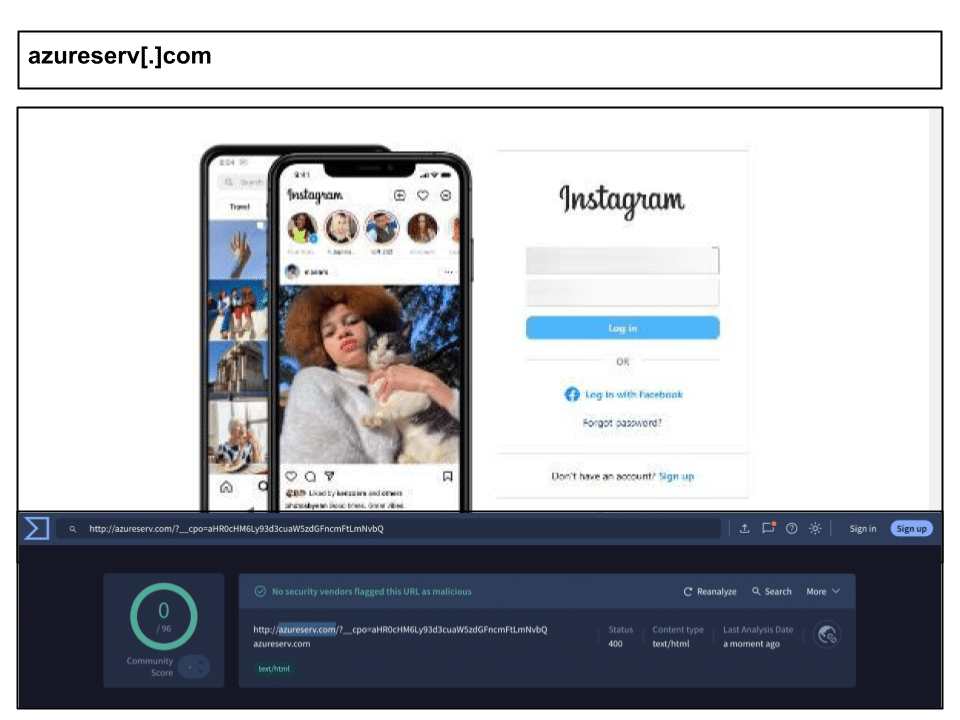
azureserv[.]com/?__cpo=aHR0cHM6Ly93d3cuaW5zdGFncmFtLmNvbQ
wittrams[.]com
skspofficelogin[.]richargest[.]cloud/?QvZli=YQbr&sso_reload=true
screetru[.]es/?auth&apitoken=rylae2be63wttzu
superdemolink00010[.]z13[.]web[.]core[.]windows[.]net
mexapvpqbu[.]life/script/iprp[.]php?t=1
track2.111cvm51-s9z-19[.]com
e-connexioninfosclients[.]duckdns[.]org/
seashell-app-eigd4[.]ondigitalocean[.]app/
orca-app-9mwg9[.]ondigitalocean[.]app/
king-prawn-app-3aosz[.]ondigitalocean[.]app/
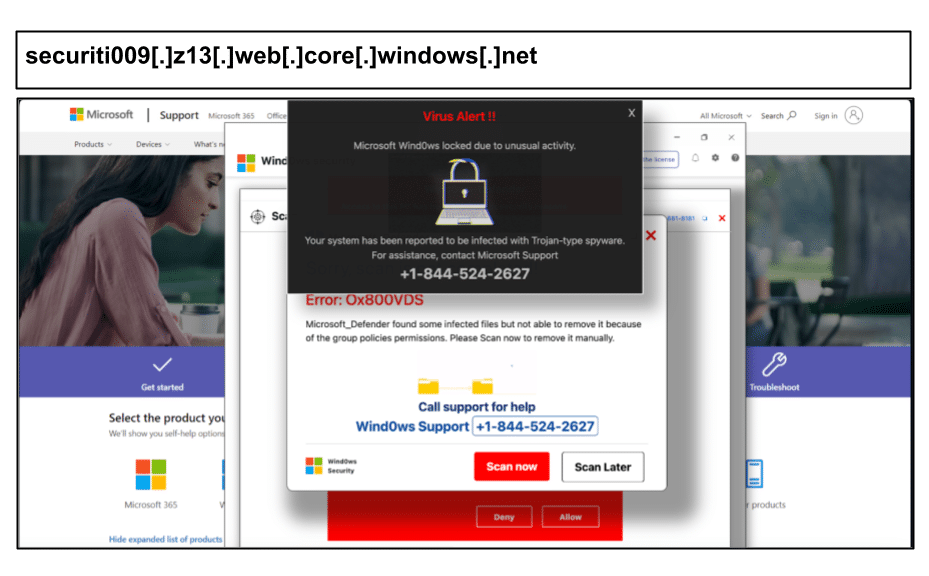
securiti009[.]z13[.]web[.]core[.]windows[.]net
securitu014[.]z13[.]web[.]core[.]windows[.]net
securitl111[.]z13[.]web[.]core[.]windows[.]net/?gad_source=5
securitj107[.]z13[.]web[.]core[.]windows[.]net
securitj105[.]z13[.]web[.]core[.]windows[.]net
Instagram Zero-Day
On January 15, an employee clicked a zero day Instagram phishing page. Even two weeks after PIXM discovered it, the URL remains 100% clean on VirusTotal.
What often makes social media cases like this difficult to report is that they are often clicked via native messaging apps like Facebook or Instagram Messenger, so they are outside the scope of traditional email based security architecture.
We further saw a streak of Microsoft credential harvesters clicked at organizations across Washington and Kentucky, like the below example.
![wittrams[.]com](https://pixmsecurity.com/wp-content/uploads/2025/02/wittrams.com_.png)
Microsoft and Apple Support Phishing
In the second half of January, PIXM witnessed a massive surge in malware sites impersonating Microsoft and Apple support like the below example.
At one Texas organization, between Jan 15 and 31, 23 different users clicked similar phishing links hosted on windows[.]net or other URLs re-directing to phishing pages on that domain. Cleverly, the support phishing attacks, which prompt users to call a phone number or install malware, customize at the time of click to Apple or Windows logos depending on the device on which the URLs are accessed.
Suggested Actions
- Add the specified domains to your block lists.
- Focus awareness efforts on high-risk credentials.
- Educate users that social media phishing can pose serious organization risks, particularly when accessed on work devices
- Remind users never to dial a support number received via an email. Instead, search Google for the intended support number
If you would like a demo of Pixm to learn more about our AI technology and how we can help protect your customers, sign up here.
Questions or Feedback
PIXM Threat Research Team
[email protected]
如有侵权请联系:admin#unsafe.sh