
Threat actors increasingly deployed web shells against vulnerable web applications and primarily exploited vulnerable or unpatched public-facing applications to gain initial access in Q4, a notable shift from previous quarters. The functionality of the web shells and targeted web applications varied across incidents, highlighting the multitude of ways threat actors can leverage vulnerable web servers as a gateway into a victim’s environment. Prior to this quarter, use of valid accounts had been Cisco Talos Incident Response (Talos IR)’s most observed method of initial access for over a year.
Ransomware made up a slightly smaller portion of threats observed this quarter than in the past. Notably, the end of the year saw a surge of ransomware and pre-ransomware incidents, primarily involving BlackBasta ransomware, suggesting this as a threat to monitor going into 2025.
Watch The Talos Threat Perspective for additional insights into the report, and recommendations for defenders
Web shells increasingly observed in adversaries’ post-compromise toolkits
In 35 percent of incidents in Q4, threat actors deployed a variety of open-source and publicly available web shells against vulnerable or unpatched web applications, a significant increase from less than 10 percent in the previous quarter. In one incident, Talos IR observed the adversary uploading a web shell with the file name “401.php”, which was also seen last quarter. This PHP web shell is based on the publicly available Neo-regeorg web shell on GitHub and has been leveraged in several adversaries’ attack chains, according to a CISA advisory. Another incident involved the web fuzzer Fuzz Faster U Fool, which is used to perform brute force attacks against web applications to discover usernames and passwords and perform directory and virtual host discovery.
Adversaries also leveraged older tools to support their post-compromise objectives, serving as a reminder for organizations to remain vigilant in adding applications to the allowlist/blocklist to control what software operates on their systems. In one incident, the attacker targeted a vulnerable server of JBoss using a tool called JexBoss, which was originally released on Github in 2014 and can be used to test and exploit vulnerabilities in Java platforms. The adversary saved JexBoss as a WAR file, and the contents included a malicious web shell named “jexws4.jsp”.
Ransomware trends
Ransomware, pre-ransomware, and data theft extortion accounted for nearly 30 percent of engagements this quarter, a slight decrease from the previous quarter, in which these types of engagements accounted for 40 percent. Talos IR observed Interlock ransomware for the first time, while also responding to previously seen ransomware variants BlackBasta and RansomHub. Talos IR was able to identify dwell times in the majority of engagements this quarter, which ranged from approximately 17 to 44 days. For example, in the Interlock ransomware incident, it took the adversary 17 days from the initial compromise stage until the deployment of the ransomware encryptor binary. Longer dwell times can indicate that an adversary is trying to expand their access, evade defenses, and/or identify data of interest for exfiltration. For example, in a RansomHub incident this quarter, operators had access to the compromised network for over a month before executing the ransomware and performed actions such as internal network scanning, accessing passwords for backups, and credential harvesting.
Operators leveraged compromised valid accounts in 75 percent of ransomware engagements this quarter to obtain initial access and/or execute ransomware on targeted systems, highlighting the risk of identity-based attacks and the need for secure authentication methods. In a BlackBasta incident, for example, operators posed as the targeted entity’s IT department and used social engineering to gain access to an employee’s account, which consequently facilitated lateral movement into the network. In a RansomHub engagement, affiliates leveraged a compromised Administrator account to execute the ransomware, dump credentials, and run scans using a commercial network scanning tool. Of note, all organizations impacted by ransomware incidents this quarter did not have multifactor authentication (MFA) properly implemented or MFA was bypassed during the attack.
As forecasted in last quarter’s IR quarterly trends report, this quarter featured two RansomHub incidents, in which affiliates leveraged newly identified tools and techniques. Talos IR observed affiliates leveraging a Veeam password stealer to target the Veeam data backup application, and KMS Auto, a tool designed to illicitly activate cracked Microsoft products. The operators also used a previously unseen persistent access technique, modifying Windows Firewall settings on targeted hosts to enable remote access. This activity occurred shortly before the ransomware was executed, potentially as a method to maintain direct access to the compromised systems.
Talos IR observed operators leveraging remote access tools in 100 percent of ransomware engagements this quarter, a significant uptick from last quarter, when it was only seen in 13 percent of ransomware or pre-ransomware engagements. Commercial remote desktop software Splashtop in particular was involved in 75 percent of ransomware engagements this quarter, and other observed remote access tools included Atera, Netop, AnyDesk, and LogMeIn. In at least 50 percent of engagements, these tools were used to facilitate lateral movement, as actors used this remote access to pivot to other systems in the environment.
Looking forward: Talos IR saw BlackBasta ransomware in one engagement that closed this quarter, as well as in a number of engagements that kicked off near the end of the year. In the observed attack chain, BlackBasta operators impersonate IT personnel to conduct double extortion attacks, which involves exfiltration of sensitive information that is then encrypted to pressure victims into paying. Our observations and corresponding public reporting on the group’s recent uptick in activity since December indicate that this is a ransomware threat to monitor going into the new year.
Targeting
Organizations in the education vertical were most affected for the second quarter in a row, accounting for nearly 30 percent of engagements. This is also consistent with Talos IR Q1 2024 (January–March) targeting trends, where the education sector was tied for the top targeted industry vertical.
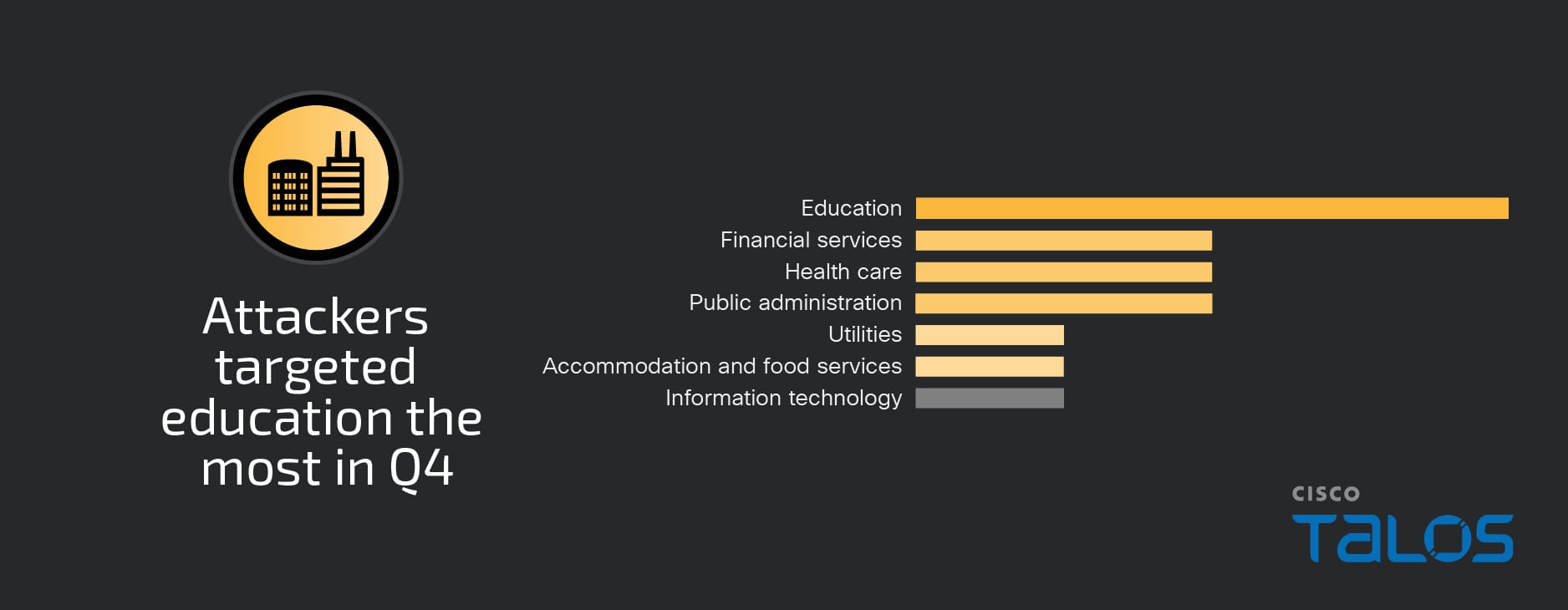
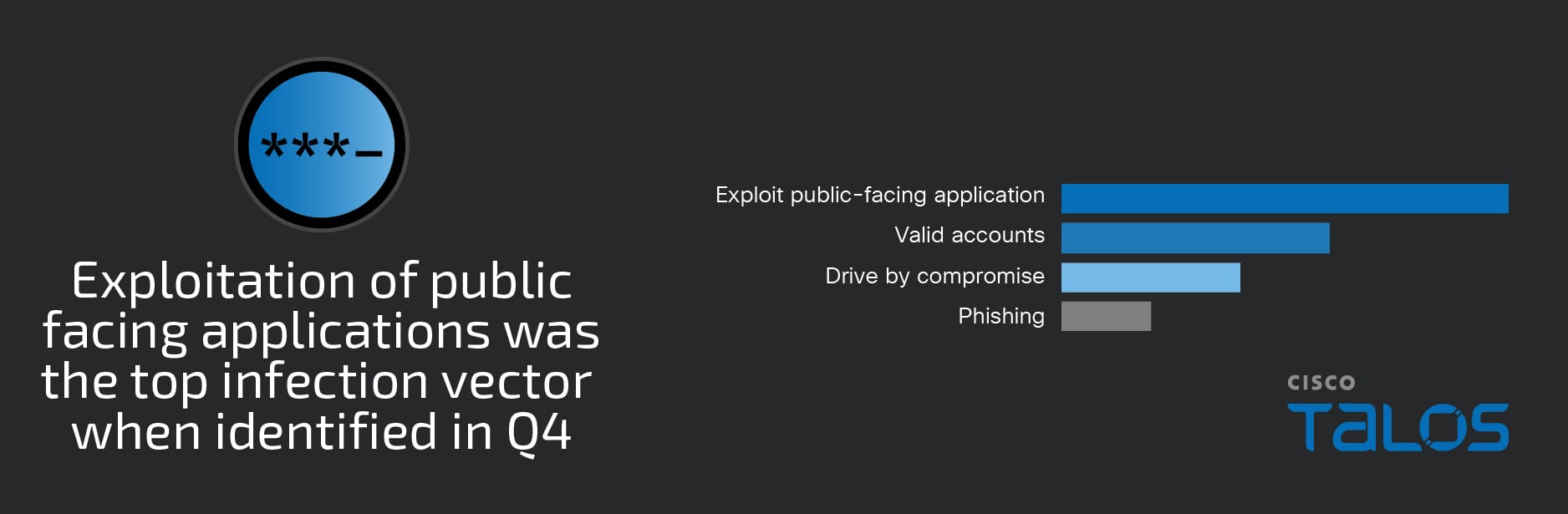
Initial access
For the first time in over a year, the most observed means of gaining initial access was the exploitation of public-facing applications, accounting for nearly 40 percent of engagements when initial access could be determined. This is a significant departure compared to previous quarters, where the use of valid accounts was consistently a top observed technique leveraged for initial access. While we still observed adversaries leverage compromised credentials and valid accounts to gain access, this shift is likely largely due to the number of web shell and ransomware incidents that took advantage of poorly patched or publicly exposed applications.
Looking forward: Since early December 2024, Talos IR has observed a surge in password-spraying attacks, leading to user account lockouts and denied VPN access. These attacks are often characterized by large volumes of traffic. For example, one organization reported nearly 13 million attempts were made in 24 hours against known accounts, indicating the adversary was likely running automated attacks. This activity primarily affected organizations in the public administration sector and was likely random and opportunistic. Although adversaries have been using password-spraying attacks for credential access for years, the sheer volume of authentication attempts in quick succession is a reminder that organizations should continue to stress the importance of MFA and strong password policies to limit unauthorized access attempts.
Recommendations for addressing top security weaknesses
Implement MFA and other identity and access control solutions
Talos IR recommends ensuring MFA is enforced on all critical services, including all remote access and identity and access management (IAM) services. In addition, to defend against MFA bypass via social engineering where prompts are accepted by a legitimate user, regular cybersecurity awareness training should cover relevant and updated social engineering topics.
We continue to see a significant number of compromises involving misconfigured, weak, or lack of MFA. This issue was present in nearly 40 percent of total engagements this quarter and, as mentioned above, 100 percent of organizations impacted by ransomware incidents did not have MFA properly implemented or it was bypassed via social engineering.
Since compromised accounts remains a top initial access vector, consider investing in IAM sevices and User Behavior Analytics (UBA), which can help identity suspicious account usage.

Patch regularly and replace end-of-life assets
Talos IR also strongly recommends organizations ensure all operating systems and software in the environment are currently supported and replace those that have reached end-of-life. Unpatched and/or vulnerable software helped facilitate initial access across several incidents this quarter, and nearly 15 percent of incidents suffered from outdated and end-of-life software.
If patching is not possible consider other mitigations, such as monitoring, especially for typical post-exploitation tools and behaviors; improving segmentation through firewalls, switch VLANs, subnetting, etc.; and disabling access to administrative shares. In 40 percent of the web shell engagements, poor network segmentation and access to administrative shares resulted in adversaries moving laterally.
Implement properly configured EDR solution
Implement properly configured EDR and other security solutions. If an organization lacks the resources to successfully implement these solutions, they can consider outsourcing to a Managed XDR vendor to ensure proper configuration and 24/7 monitoring by security experts.
Misconfigured or missing EDR solutions affected over 25 percent of all incidents for the quarter.
Top-observed MITRE ATT&CK techniques
The table below represents the MITRE ATT&CK techniques observed in this quarter’s Talos IR engagement. Given that some techniques can fall under multiple tactics, we grouped them under the most relevant tactic in which they were leveraged. Please note this is not an exhaustive list.
Key findings from the MITRE ATT&CK framework include:
- The use of remote access tooling, such as Splashtop or AteraAgent, was leveraged in nearly 40 percent of engagements, compared to 5 percent in the previous quarter.
- Remote access tooling was leveraged in 100 percent of the ransomware incidents observed in Q4, a significant shift compared to that of the previous quarter.
- This is the first quarter in well over a year in which the use of valid accounts was not the top initial access technique. Instead, exploitation of public-facing applications, largely contributed by the high number of web shell incidents, was the top means of gaining access this quarter.
|
Reconnaissance (TA0043) |
T1589.001 Gather Victim Identity Information: Credentials |
Adversaries may gather credentials that can be used during their attack. |
|
T1598.003 Phishing for Information: Spearphishing Link |
Adversaries may send a spearphishing email with a link to a credential harvesting page to collect credentials for their attack. |
|
|
T1595.002 Active Scanning: Vulnerability Scanning |
Adversaries may run vulnerability scans against an organization’s public-facing infrastructure to identify potential vulnerabilities to exploit. |
|
|
T1598 Phishing for Information |
Threat actor sent phishing messages to elicit sensitive information that can be used during targeting. |
|
|
T1598.004 Phishing for Information: Spearphishing Voice |
After clicking a malicious link contained within a trusted third-party site, the user was directed to call a fake Microsoft support site. After the user did so, they received repeated vishing calls for further information. |
|
|
Initial Access (TA0001) |
T1190 Exploit in Public-Facing Application |
Adversaries may exploit a vulnerability to gain access to a target system. |
|
T1078 Valid Accounts |
Adversaries may use compromised credentials to access valid accounts during their attack. |
|
|
T1189 Drive-by Compromise |
Uses compromised websites or ads to lure victims into downloading a malicious installer. |
|
|
T1566 Phishing Link |
Adversary sends a phishing email which contains a malicious link. |
|
|
Execution (TA0002) |
T1059.001 Command and Scripting Interpreter: PowerShell |
Adversaries may abuse PowerShell to execute commands or scripts throughout their attack. |
|
T1204.001 User Execution: Malicious Link |
The victim clicked on a malicious link in a phishing email. |
|
|
T1059.006 Command and Scripting Interpreter: Python |
Adversary used Python commands for execution. |
|
|
T1059.003 Command and Scripting Interpreter: Windows Command Shell |
Adversaries may abuse Windows Command Shell to execute commands or scripts throughout their attack. |
|
|
T1047 Windows Management Instrumentation |
Adversaries may use Windows Management Instrumentation (WMI) to execute malicious commands during the attack. |
|
|
T1059.004 Command and Scripting Interpreter: Unix Shell |
The adversary executed shell commands. |
|
|
Persistence (TA0003) |
T1505.003 Server Software Component: Web Shell |
Deploy web shells on vulnerable systems. |
|
T1136 Create Account |
Adversaries may create a new account to maintain persistence in a target environment. |
|
|
T1053.005 Scheduled Task/Job: Scheduled Task |
Adversaries may abuse the Windows Task Scheduler to perform task scheduling for recurring execution of malware or malicious commands. |
|
|
Privilege Escalation (TA0004) |
T1078.002 Valid Accounts: Domain Accounts |
Adversaries may abuse their access to valid accounts allowing access to privileged resources of the domain. |
|
Defense Evasion (TA0005) |
T1562.001 Impair Defenses: Disable or Modify Tools |
Adversaries may disable or uninstall security tools to evade detection. |
|
T1027.010 Obfuscated Files or Information: Command Obfuscation |
Adversaries may obfuscate commands to evade detection during their attack. |
|
|
T1070.004 Indicator Removal: File Deletion |
Adversaries may delete files to cover their tracks during the attack. |
|
|
T1484.001 Domain or Tenant Policy Modification: Group Policy Modification |
Modify GPOs to push out malicious scheduled tasks. |
|
|
T1070.001 Indicator Removal: Clear Windows Event Logs |
Adversaries may clear the Windows event logs to cover their tracks and impair forensic analysis. |
|
|
T1036 Masquerading |
The attacker deployed a ransomware encryptor binary with the file name “conhost.exe”, masquerading as a legitimate file onto the victim machine. |
|
|
T1070.002 Indicator Removal: Clear Linux or Mac System Logs |
Log clearing via sudo. |
|
|
T1218.014 System Binary Proxy Execution: MMC |
Adversaries abuse MMC to carry out malicious activities, such as execute malicious files. |
|
|
T1112 Modify Registry |
Adversary used some registry modifications to get privilege escalation. |
|
|
Credential Access (TA0006) |
T1003 OS Credential Dumping |
Adversaries may dump credentials from various sources to enable lateral movement. |
|
T1110.003 Brute Force: Password Spraying |
Adversaries use a list of usernames and passwords to try and gain access to user accounts. |
|
|
T1621 Multi-Factor Authentication Request Generation |
Adversaries may generate MFA push notifications causing an MFA exhaustion attack. |
|
|
T1555.003 Credentials from Password Stores: Credentials from Web Browsers |
Adversaries may obtain credentials from the victim’s Chrome browser. |
|
|
T1558.003 Steal or Forge Kerberos Tickets: Kerberoasting |
Use Kerberoasting PowerShell commands for credential access. |
|
|
Discovery (TA0007) |
T1046 Network Service Discovery |
Adversaries may use tools like Advanced Port Scanner for network scanning. |
|
T1069.002 Permission Groups Discovery |
Adversary identified domain admins in the environment. |
|
|
T1018 Remote System Discovery |
Adversaries may attempt to discover information about remote systems with commands, such as “net view”. |
|
|
T1082 System Information Discovery |
Adversary performed large scale host enumeration |
|
|
T1083 File and Directory Discovery |
Adversary enumerated files and directories to identify certain key files. |
|
|
T1033 System Owner / User Discovery |
Adversaries may attempt to discover information about the logged in user of a compromised account with commands, such as “whoami”. |
|
|
T1016 System Network Configuration Discovery |
Adversaries may use commands, such as ifconfig and net use, to identify network connections. |
|
|
T1087.001 Account Discovery: Local Account |
Enumerate user accounts on the system. |
|
|
T1135 Network Share Discovery |
Enumerate network shares on a host. |
|
|
Lateral Movement (TA0008) |
T1021.001 Remote Services: Remote Desktop Protocol |
Adversaries may abuse valid accounts using RDP to move laterally in a target environment. |
|
T1021.004 Remote Services: SSH |
Adversaries may abuse valid accounts using SSH to move laterally in a target environment. |
|
|
T1550.002 Use Alternative Authentication Material: Pass the Hash |
Adversaries may bypass access controls by using stolen password hashes. |
|
|
T1570 Lateral Tool Transfer |
Adversary transfers tools and files between systems in a compromised environment |
|
|
Collection (TA0009) |
T1005 Data from Local System |
Adversaries may collect information from an infected system |
|
T1074 Data Staged |
Adversary collected data in a central location prior to exfiltration |
|
|
T1560 Archive Collected Data |
Adversaries may archive staged data using tools, such as WinRAR. |
|
|
T1530 Data from Cloud Storage |
Collect files from cloud services. |
|
|
Command and Control (TA0011) |
T1219 Remote Access Software |
Adversaries may abuse remote access software, such as AnyDesk, to establish an interactive C2 channel during their attack. |
|
T1105 Ingress Tool Transfer |
Adversaries may transfer tools from an external system to a compromised system. |
|
|
T1071.001 Application Layer Protocol: Web Protocols |
Communicate between compromised hosts and attacker-controlled servers via HTTP POST/GET requests. |
|
|
T1090 Proxy |
An adversary used a tool called Invoke-SocksProxy, intended for command and control. |
|
|
T1102 Web Service |
Adversary performed reconnaissance and made network connections to a Discord IP address. |
|
|
Exfiltration (TA0010) |
T1567.002 Exfiltration Over Web Service: Exfiltration to Cloud Storage |
Exfiltrate data to web server. |
|
T1537 Transfer Data to Cloud Account |
Adversary exfiltrated data to an attacker-controlled cloud account. |
|
|
Impact (TA0040) |
T1486 Data Encrypted for Impact |
Adversaries may use ransomware to encrypt data on a target system. |
|
T1490 Inhibit System Recovery |
Adversaries may disable system recovery features, such as volume shadow copies. |
|
|
Software/Tool |
S0029 PsExec |
Free Microsoft tool that can remotely execute programs on a target system. |
|
S0349 LaZagne |
A post-exploitation, open-source tool used to recover stored passwords on a system. |
|
|
S0357 Impacket |
An open-source collection of modules written in Python for programmatically constructing and manipulating network protocols. |
|
|
S0002 Mimikatz |
Credential dumper that can obtain plaintext Windows logins and passwords. |
|
|
S0154 Cobalt Strike |
Adversary simulation tool. |
|
|
S0552 AdFind |
Freely available command-line query tool used for gathering information from Active Directory. |
|
|
S0097 Ping |
An operating system utility commonly used to troubleshoot and verify network connections. |
|
|
S0225 Sqlmap |
An open-source penetration testing tool used to automate the process of detecting and exploiting SQL injection flaws. |
