Recent regulations require organizations to demonstrate they are resilient to cyber-attacks. These regulations impact regulated organizations and those in the supply chain, as modern threat actors target vulnerabilities across the entire ecosystem.
Cybersecurity has become a boardroom, high-priority agenda item with heightened legal exposure, increases in supply chain attacks, and reported vulnerabilities.
Cybersecurity incidents are expensive. According to IBM’s 2024 data, the average cost of a data breach was $4.88 million. Beyond this, poor cybersecurity ratings can negatively impact credit scores, increasing borrowing costs and adding financial strain to already constrained organizations.
Cyber-resilient regulations span the globe, many carrying significant consequences for non-compliance. For example:
- Failure to comply with The Digital Operational Resilience Act (DORA), governing EU financial institutions and third-party suppliers, could result in a €10 million fine or 5% of annual sales. DORA is a European Union (EU) regulation that aims to improve the cybersecurity and operational resilience of financial institutions. This regulation goes into effect in January 2025.
- Non-compliance with NIS2, a regulation that came into force in January 2023 could result in administrative fines of €10 million or 2% of annual sales of the prior year (whichever is higher).
- Starting from April 2024, banking, insurance and financial services organizations in New York can face fines of $2,500 to $75,000 per day for failing to comply with 23 NYCRR Part 500.
In addition to the regulatory consequences, the financial impacts of a security incident are severe. The typical downtime after a ransomware attack is 3 weeks. If your organization doesn’t have €10M laying around or can’t afford 3 weeks of lost revenue, read on.
IT visibility and hygiene
Most of these regulations focus on understanding IT assets in your environment and supply chain: how they are used, their dependencies, and their state (end-of-life (EOL), requiring patches, etc.). Yes, we are talking about basic IT asset data visibility and hygiene. More specifically this means:
- Managing IT asset lifecycles, such as identifying and upgrading or removing end-of-life and end-of-support assets that cannot be patched.
- Ensuring vulnerabilities are patched promptly by matching vulnerability intelligence with and prioritizing patching according to severity and where vulnerabilities are in your environment.
- Identifying supply chain risks by obtaining visibility into all applications used across your organization.
- Document CI dependencies to help assess risk and how threat actors could move through your environment.
- Maintaining an accurate and up-to-date CMDB to facilitate fast incident response.
How Flexera helps improve IT visibility to protect against cyber threats
IT asset visibility is the first step in protecting your organization from cyber threats. Before you can assess risk, you need a normalized, comprehensive view into your IT environment. Flexera has dozens of out-of-the-box connectors to bring in data you’re already collecting. Additionally, we fill in your gaps by:
- Capturing inventory and application usage details via the Flexera Agent.
- Identifying use of paid and free SaaS applications through our browser extension and integration with Cloud Access Security Brokers.
Leveraging our market-leading content library, Technopedia, to scrub your inventory, normalize your data, and enrich it with details like EOL dates and known vulnerabilities.
With this data set, you can get a quick picture of your risk. In the view below, 7.8% of deployed software is end-of-life–a big risk because these apps can’t be patched. We also see 11% of software installations with a Secunia advisory.
Flexera leverages Secunia advisories because they are more up to date than the National Vulnerability database. In December 2024 alone, there were 10 advisories captured by Secunia research without an associated common vulnerability and exposure (CVE).
To further pinpoint where to focus your efforts, you can filter by organizational unit. In this example, we see the engineering organization has the highest number of EOL installs.

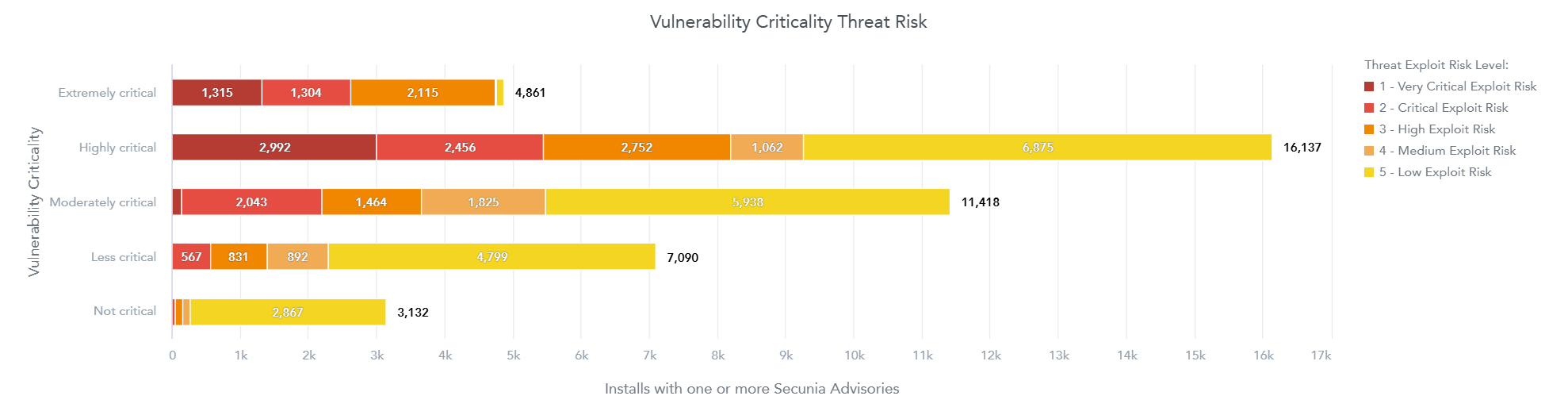
We can also track which vulnerabilities need to be patched first by order of exploit risk. It’s not just the latest exploits that are most risky. Many older, known vulnerabilities are still being exploited due because many organizations lack a comprehensive patching strategy, hence why governments need to regulate cyber-resiliency.

With the combination of EOL dates and vulnerabilities, you can pinpoint where apps need to be removed from your environment.

To find risk by critical business service, the dependency mapping view shows you all the devices, applications and their lifecycle and vulnerability status.

This data is accessible via the UI, PowerBI reports or by exporting to another database using our easy-to-query API. Additionally, this rich data can be leveraged to update your CMDB.
This blog only scratches the surface of how Flexera can help you build a more resilient IT environment. To learn more, fill out this form and one of our experts can provide you with an in-depth, personalized demo!