2025-1-29 11:55:22 Author: cybersecuritynews.com(查看原文) 阅读量:13 收藏
A proof-of-concept (PoC) exploit for the actively exploited Windows Common Log File System (CLFS) vulnerability, tracked as CVE-2024-49138 has been released.
This vulnerability, which Microsoft patched on December 10, 2024, with update KB5048685 for Windows 11 versions 23H2 and 22H2, has already been exploited in the wild.
Security researchers and organizations are now closely analyzing the exploit to understand its implications and ensure robust defenses.
CVE-2024-49138 is a heap-based buffer overflow vulnerability in the Windows CLFS driver (clfs.sys). The flaw resides in two functions within the CClfsBaseFilePersisted class: LoadContainerQ() and WriteMetadataBlock().
These functions mishandle memory when processing metadata blocks for Base Log Files (BLFs), allowing attackers to manipulate critical structures in memory.
Are you from SOC/DFIR Teams? – Analyse Malware Files & Links with ANY.RUN Sandox -> Try for Free
The vulnerability can be exploited by local attackers to achieve arbitrary read/write capabilities in kernel mode (ring 0), leading to privilege escalation. This makes it particularly dangerous as it can grant attackers full control over affected systems.
PoC Exploit For Windows CLFS Buffer Overflow
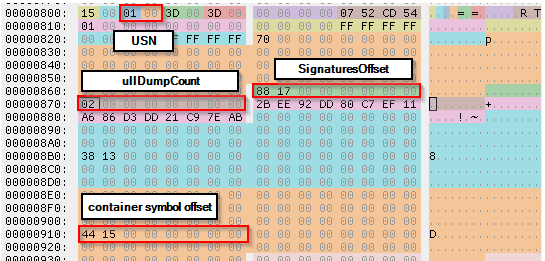
The Common Log File System (CLFS) is a subsystem in Windows designed for high-performance logging. It uses BLFs to manage log containers and metadata. Each BLF contains six metadata blocks, including the General Metadata Block, which tracks clients and containers.
According to HN Security, the vulnerability arises from improper handling of metadata blocks when loaded into memory. Specifically:
- In LoadContainerQ(), the pContainer field of CLFS_CONTAINER_CONTEXT structures can be made to point to invalid or controlled memory.
- In WriteMetadataBlock(), failure during block decoding (ClfsDecodeBlock()) can lead to memory being freed prematurely, leaving dangling pointers.
Exploitation Path of CVE-2024-49138:
- An attacker crafts a malicious BLF with manipulated metadata fields such as SignaturesOffset and ullDumpCount.
- The attacker triggers the vulnerability by loading the malicious BLF using the CreateLogFile() API.
- During execution of LoadContainerQ(), the freed memory is reused, allowing the attacker to execute arbitrary code by hijacking function pointers in a fake CClfsContainer object.
- The PoC exploit demonstrates how this can be used to overwrite kernel structures like _KTHREAD.PreviousMode, enabling arbitrary read/write operations and privilege escalation.
This vulnerability is classified as critical due to its low complexity and high impact. It does not require user interaction but does necessitate local access to the target system.
According to the HN Security Report, Attackers leveraging this flaw can escalate privileges to SYSTEM level, potentially compromising entire networks if exploited on domain controllers or other critical infrastructure.
Mitigation
Microsoft’s patch KB5048685 (for Windows 11 23H2/22H2) addresses the issue by adding checks in LoadContainerQ() to ensure that pointers remain valid even if metadata blocks are freed. Organizations should:
- Apply KB5048685 immediately across all affected systems.
- Monitor for signs of exploitation, such as unexpected writes to BLF files.
- Use endpoint detection tools capable of identifying anomalous behavior linked to CLFS exploitation.
The technique of modifying _KTHREAD.PreviousMode has been mitigated in newer Windows versions (24H2 and later).
Microsoft’s fix ensures that after a failure in FlushImage(), any potentially tampered pointer (pContainer) is validated before use. This prevents attackers from hijacking execution flow via invalid or controlled pointers.
Organizations must prioritize patching systems vulnerable to this actively exploited flaw while implementing additional monitoring measures to detect potential exploitation attempts.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
如有侵权请联系:admin#unsafe.sh
.webp?w=696&resize=696,0&ssl=1)