
2025-1-29 13:1:0 Author: rhinosecuritylabs.com(查看原文) 阅读量:11 收藏
Vulnerability Overview
Affected Product Summary
Yeti is a Forensic Intelligence platform and pipeline for DFIR teams. It allows threat intelligence and DFIR teams to catalog, search, and link pieces of intelligence such as IP addresses, TTPs, and threat actors. With 10,000 pulls from Dockerhub and nearly 2,000 stars on GitHub, it is a fairly popular tool for DFIR practitioners.
In this blog post, I will detail 2 security flaws that, if used in conjunction, could lead to unauthenticated remote code execution on the application server. The consequences of a successful server compromise could include attackers collecting intelligence on who/what the threat intel teams were monitoring and modifying/destroying IoCs/observables.
The proof-of-concept exploit can be found in our CVE Github repository.
The patch for these CVEs can be found on the yeti-platform repository: SSTI, Insecure secret
CVE-2024-46507: SSTI Leads to RCE
Yeti allows its users to create custom report templates that users can export their IoCs/intel into a custom format. The template content is not sanitized before being processed on the backend, leading to the possibility of code execution.
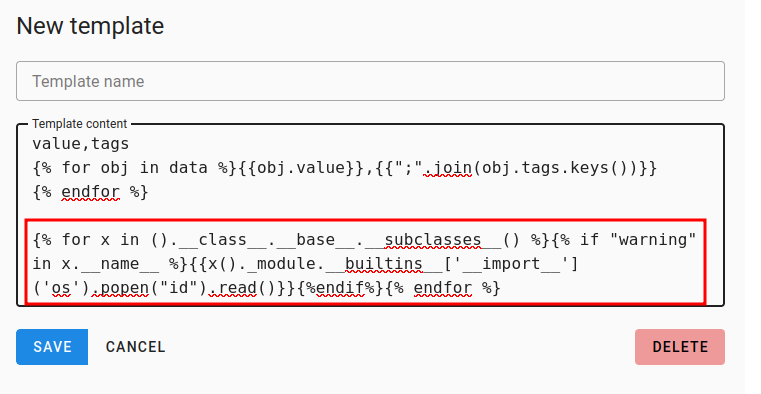
Templates can be used to export observables (hashes, domains, IP addresses). To successfully instantiate an export, there needs to be an observable too export. To create one, can go to Observables -> New Observable -> Save

To trigger the rendering of our malicious template, we need to select our newly created observable to export it with our malicious template.
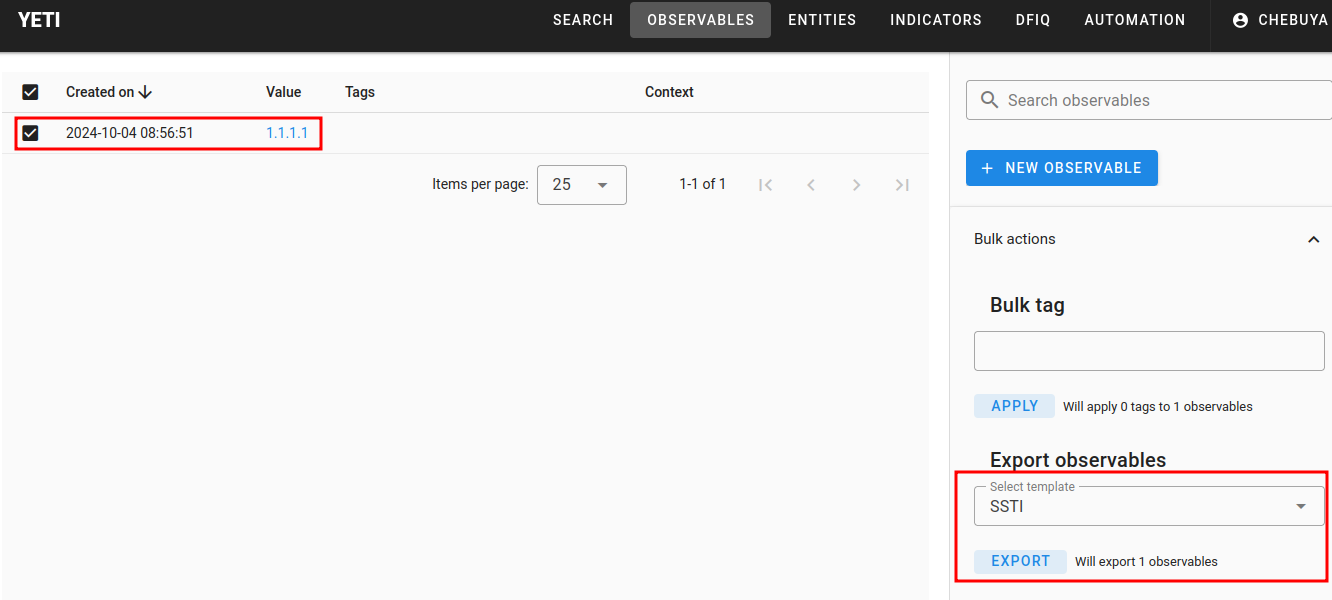
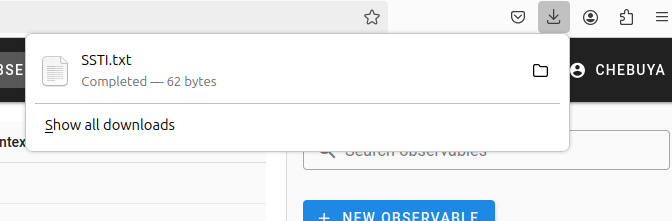
After exporting the observables, a .txt file is downloaded.
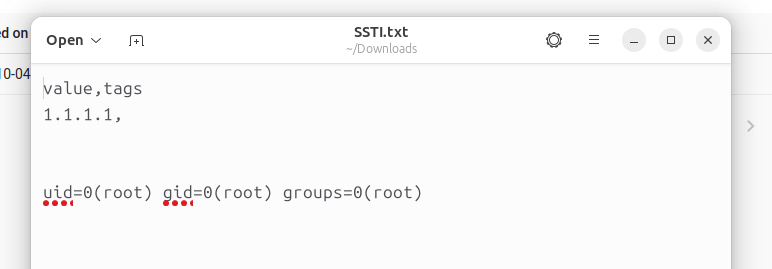
In the .txt file, we see the output of the command that we chose in the malicious template (in this case, id).
CVE-2024-46508: Use of Static Insecure Secret
Yeti makes use of JWTs for authentication. The application is most commonly deployed using a docker-compose file. I was surprised during the installation process, there is no need to ever actually open the .env file to change anything, it was as simple as cloning the repo, running docker-compose, and the application was up in a few seconds. Furthermore, the documentation does not refer to the .env file anywhere. Concerningly, in the .env file the JWT secret was configured as “SECRET” and did not seem to be replaced at runtime. Given the fact that the .env file is not required to be modified in the installation process or mentioned in documentation, there was a good chance that instances deployed in the wild would have not changed the static secret. Furthermore, the variable naming did not make it readily apparent that it was being used for a JWT secret.
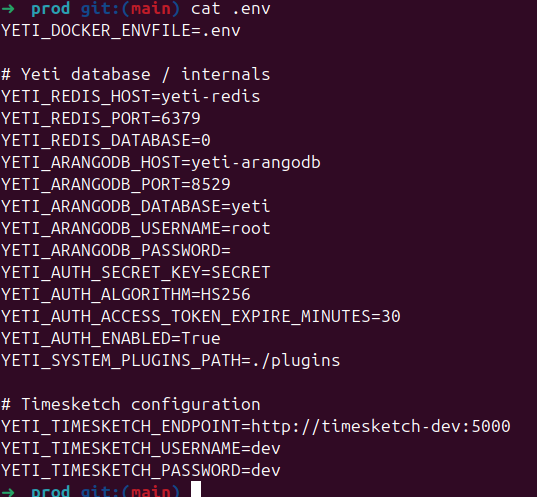
With a known JWT secret, attackers can generate valid tokens and bypass authentication. Combined with the ability to execute commands from an authenticated context, this was more concerning.
Conclusion
We found Yeti interesting as the primary users would be blue teams. While reviewing the codebase, we discovered CVE-2024-46507 allowing authenticated users to execute code on the application server. While looking for other ways to exploit this vulnerability besides brute forcing/obtaining valid credentials for the application, we discovered a static JWT secret being used in the docker deployment process (CVE-2024-46508). Combining both of these issues, it would be possible to obtain unauthenticated code execution on applications in the default configuration. We want to thank the Yeti team for working with us to remediate this vulnerability.
We have added a proof-of-concept to our CVE Github repository that demonstrates this vulnerability. As always, feel free to follow us on Twitter or LinkedIn and join our Discord server for more releases and blog posts.
Twitter: https://twitter.com/rhinosecurity
LinkedIn: https://www.linkedin.com/company/rhino-security-labs/
Discord: https://discord.gg/TUuH26G5
Researcher/Author: https://x.com/_chebuya
Vulnerability Disclosure Timeline
| Date | Note |
| 8/28/2024 | Issue reported to Yeti. |
| 9/8/2024 | Yeti acknowledged the vulnerability. |
| 9/9/2024 | Rhino provided Yeti with additional vulnerability information. |
| 9/19/2024 | Rhino obtains a CVE from MITRE. |
| 10/1/2024 | Yeti patches the vulnerability. |
如有侵权请联系:admin#unsafe.sh