Our cyber threat analysts detected and explored a number of malware campaigns this January. Here are the three most dangerous attacks dissected with the aid of ANY.RUN’s Interactive Sandbox and Threat Intelligence Lookup.
Fake YouTube links redirect users to phishing pages
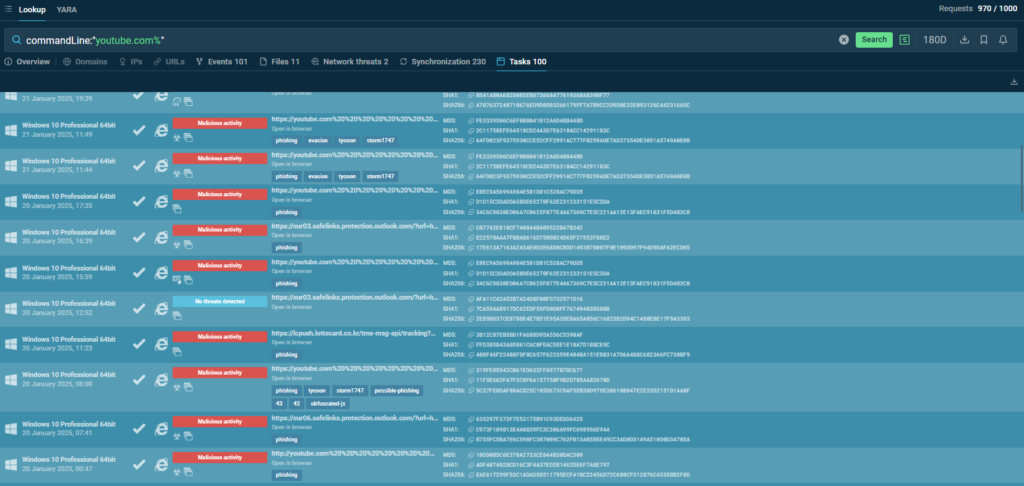
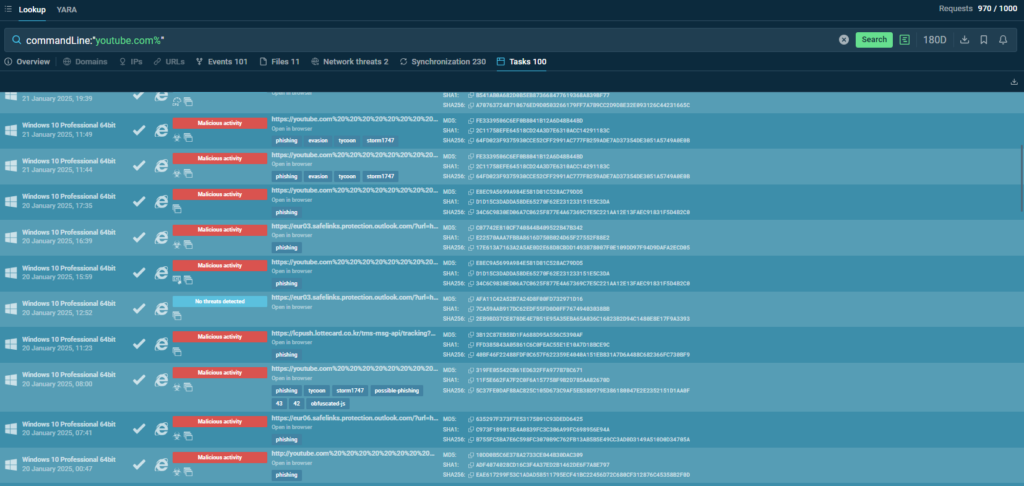
Using the Uniform Resource Identifier authority (URI), phishers obfuscate links and place a legitimate resource address, like http://youtube, at the beginning of URLs to deceive users and make the link appear authentic and safe.
Not just YouTube is getting abused. We’ll keep monitoring and sharing the details with you, so your company can make effective decisions to address the threat.
Watch how the attack unveils in our Interactive Sandbox and gather IOCs for setting up your security systems.
View analysis
Use this search request in TI Lookup to find more sandbox sessions and enforce the protection of your business by fine-tuning malware detection in your network:
commandLine:”youtube.com%”
- Technically, the URI Scheme replaces the userinfo field (user:pass) with a domain name: foo:// <user:pass> @ domain . Zone.
- Storm 1747 domain infrastructure — checkers, redirectors and main pages — has a standard template for Tycoon 2FA phishkit installed.
- The technique of replacing user info is also employed by various other phishing kits, such as Mamba 2FA and EvilProxy.
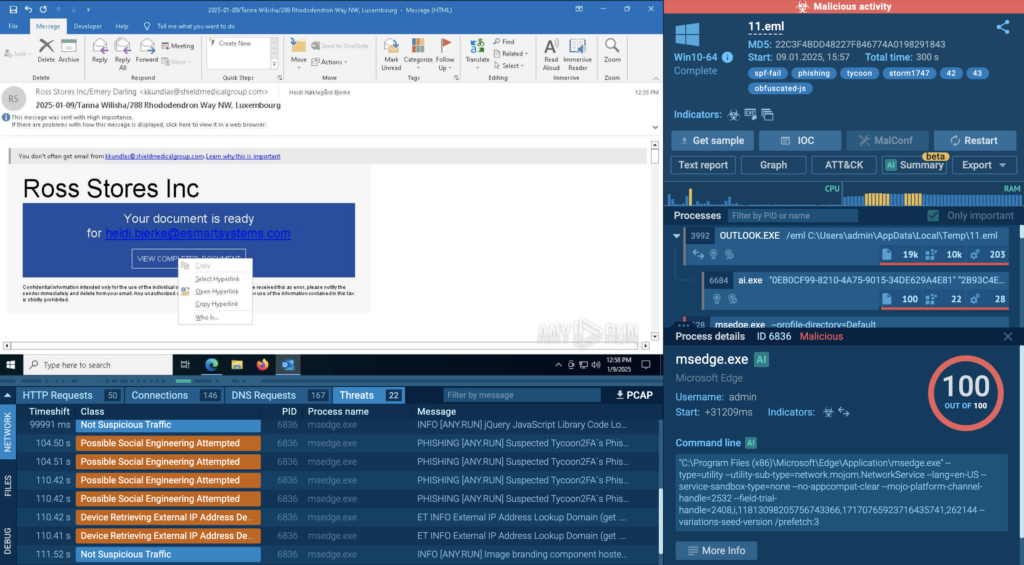
To study the behavior and indicators of all these malware samples, use ANY.RUN’s Interactive Sandbox.
Phishers use fake online shops with surveys to steal credit card information
The new phishing scheme we named FoxWhoops targets American e-commerce customers with fake sites promising a reward for completing a survey
The attack utilizes a system of checks. Users who fail them are sent to a Fox News RSS page or a page with a ‘Whoops!’ image. Those who pass the checks are offered to enter their bank card info to purchase the ‘reward’ at a discount.
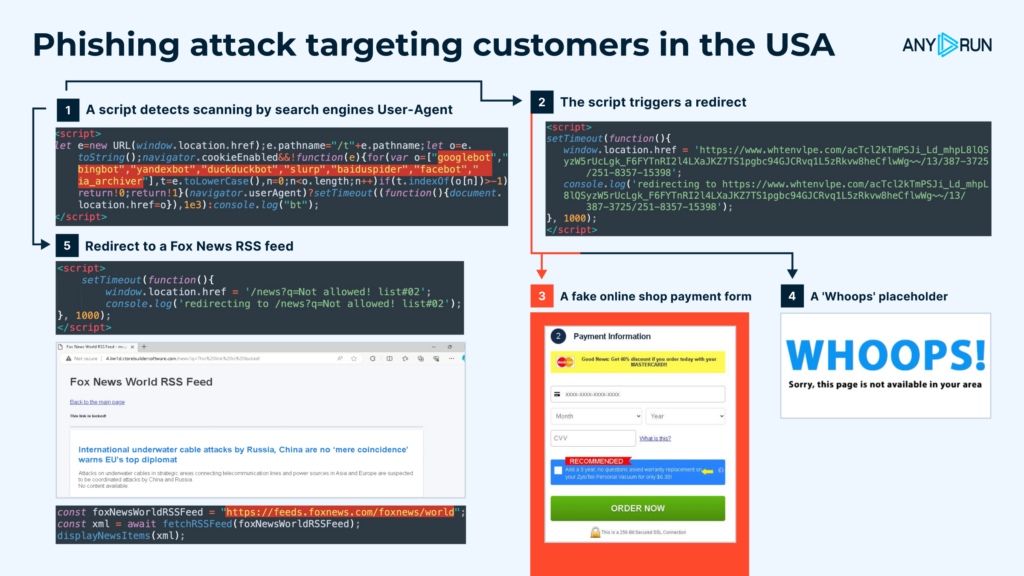
A number of examples of such attacks have been submitted in our sandbox:
Checks and redirects:
- A script detects scanning by Google, Bing, Baidu, DuckDuckGo, etc.
- If the first check is passed, the script triggers a redirect
- If the second check is passed, the user is redirected to a phishing page with a fake online shop payment form
- If the first check fails, the user is redirected to a Fox News RSS feed
- If the second check fails, the ‘Whoops’ page is displayed.
Possible attack scenarios based on these steps:
- Phishing scenario: 1 → 2 → 3. A phishing survey with a ‘reward’ after a small payment in a fake store. Credit card info stolen.
- Evasion scenario: 1 → 4. If the victim fails the first check, they are redirected to what appears to be a Fox News RSS feed. The URL includes a ‘q’ parameter that specifies the reason for the redirect, such as: “IP provider is blacklisted! ASN-CXA-ALL-CCI-22773-RDC“.
- Placeholder scenario: 1 → 2 → 5. Users are shown a placeholder page.

Examine the attack’s mechanics to facilitate employee security training in your organization and prevent social engineering attempts with ANY.RUN’s Sandbox!
A SystemBC client is targeting Linux-based platforms
The Linux version of SystemBC proxy implant is potentially designed for internal corporate services. It is commonly used to target corporate networks, cloud servers, and even IoT devices.
This Remote Access Trojan is designed to maintain encrypted communication with C2 servers, using the same custom protocol, ensuring connection to a unified infrastructure of both Windows and Linux implants.
A proxy implant within a victim’s infrastructure is a crucial tool for attackers, allowing for lateral movement and pivoting without deploying additional detectable tools, further evading detection on the host.
This version is more stealthy and far more dangerous. Samples do not have clear family detection by security vendors.
Take a look at the Linux version analysis in the sandbox:
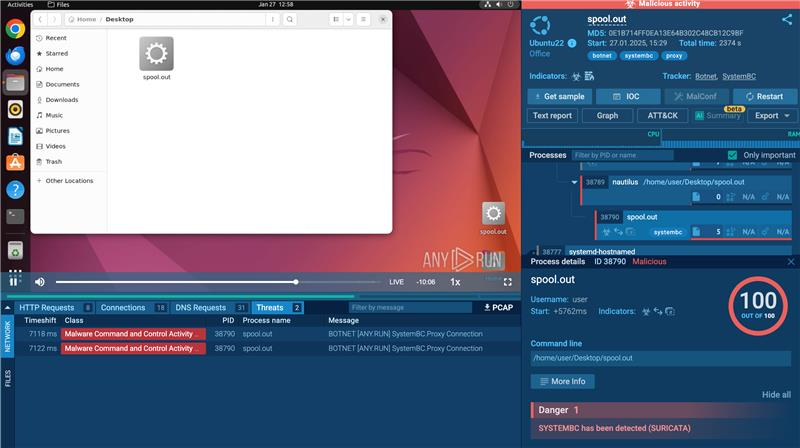
To respond effectively, use ANY.RUN’s Linux virtual machine and quickly detect malicious communication with in-depth network traffic insights, powered by advanced Suricata rules from our experts.

Major Attacks in December 2024
Learn about phishing attacks leveraging Microsoft’s Azure and OneDrive services and discover details on the LogoKit phish kit.
See details
Conclusion
The cyber threat landscape this January was marked by sophisticated and varied attack strategies targeting individuals and organizations alike. From phishing schemes exploiting trusted platforms to deceptive fake online shops, hackers demonstrated increasing ingenuity and adaptability.
Organizations must remain vigilant and proactive by leveraging tools such as ANY.RUN’s Interactive Sandbox and Threat Intelligence Lookup to identify and analyze threats in real time. Staying informed and prepared is the key to safeguarding critical assets in this ever-changing digital battlefield.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.