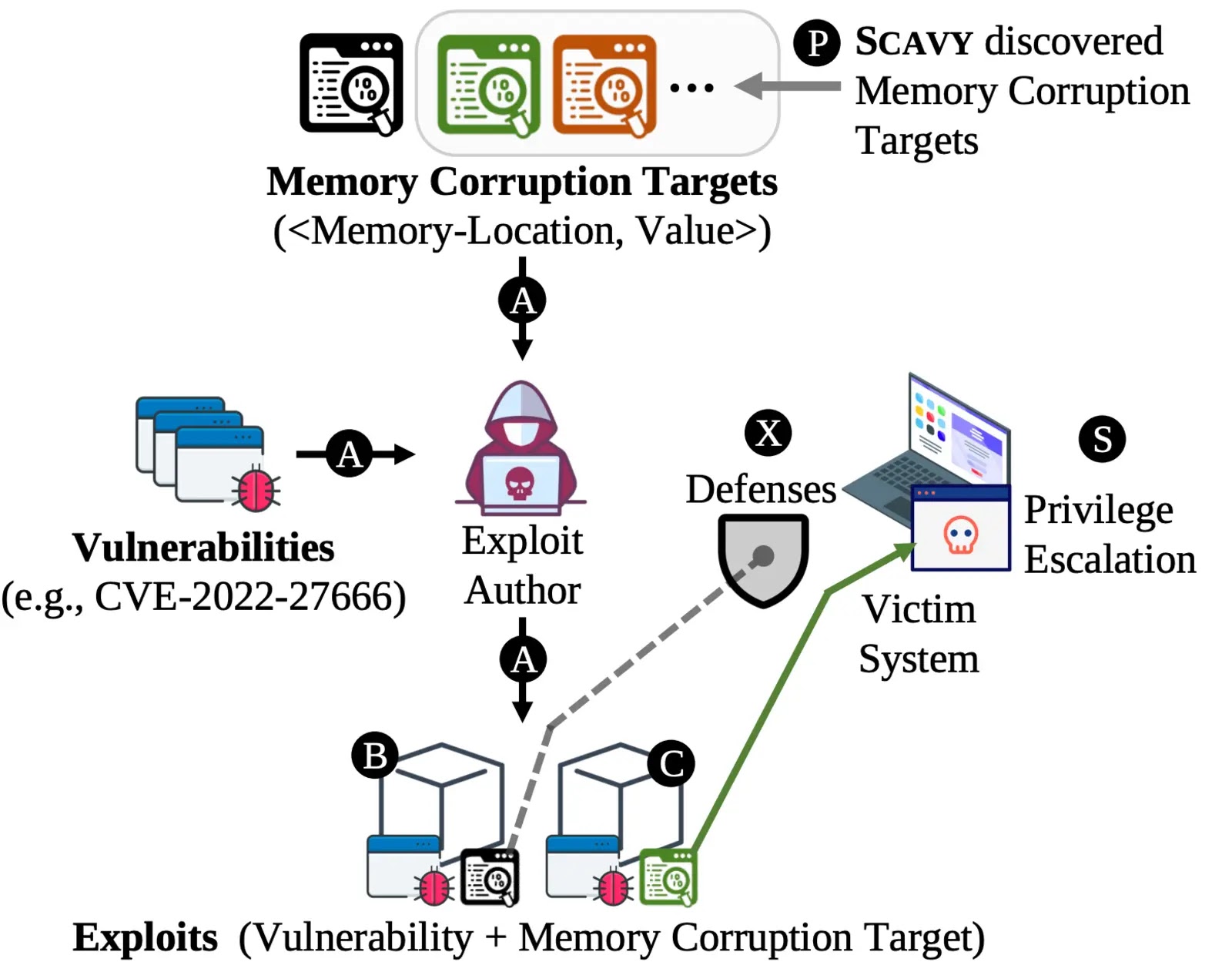
Researchers have unveiled SCAVY, a novel framework designed to automate the discovery of memory corruption targets in the Linux kernel.
This discovery aims to address critical gaps in the detection and prevention of privilege escalation exploits, which often leverage memory-corruption vulnerabilities to gain unauthorized access to system resources.
Kernel privilege-escalation exploits typically exploit memory corruption vulnerabilities to overwrite specific memory locations, known as memory targets.
These targets determine the extent of unauthorized access an attacker can achieve, such as modifying files, accessing restricted memory, or executing privileged operations.
Are you from SOC/DFIR Teams? - Analyse Malware Files & Links with ANY.RUN Sandox -> Try for Free
Memory Corruption in Kernel Exploits
Historically, identifying these memory targets has been a manual and labor-intensive task, focusing primarily on function pointers or structures containing them. This limited scope has left a significant portion of kernel data structures—approximately 90%—unexplored.

SCAVY: A Comprehensive Framework
SCAVY (short for Scavenger) is designed to systematically uncover memory corruption targets across a broader spectrum of kernel data structures.
Unlike traditional approaches that focus on specific bug types or vulnerabilities, SCAVY is bug-type agnostic.
It employs advanced techniques such as fuzzing and differential analysis to identify exploitable states caused by memory corruption.
Expanded Search Scope: SCAVY examines all kernel data structures, including those previously overlooked, broadening the potential attack surface for analysis.
Bug-Type Agnosticism: The framework is not limited to specific vulnerabilities like use-after-free or buffer overflows, making it adaptable to diverse scenarios.
Automated Differential Analysis: By comparing program states with and without memory corruption, SCAVY identifies fields whose corruption leads to privilege escalation.
Scalability: SCAVY’s instrumentation and analysis techniques allow it to process millions of potential memory targets efficiently.

The article “Scavy: Automated Discovery of Memory Corruption Targets in Linux Kernel for Privilege Escalation” by Erin Avllazagaj, Yonghwi Kwon, and Tudor Dumitraș, published in the proceedings of the 33rd USENIX Security Symposium at the University of Maryland, claims that SCAVY operates in three main phases.
- Instrumentation and Analysis: It instruments type-casting operations within the kernel to map allocated memory addresses to their corresponding data types. This step ensures accurate identification of kernel structure layouts.
- Discovery of Potential Memory Targets: Using fuzzing techniques, SCAVY corrupts individual fields within kernel structures and monitors their impact on system behavior. Fields that cause observable changes are flagged as potential targets.
- Detection of Privilege Escalation: Through multi-execution reasoning, SCAVY tests whether corrupted fields enable unauthorized access to privileged resources. For example, it checks if corrupted fields allow unprivileged processes to perform root-level operations.
Impact
SCAVY has already demonstrated its effectiveness by identifying 17 new exploitable fields across 12 kernel structures. From these discoveries, the framework generated 955 proof-of-concept (PoC) exploits.
Researchers developed six fully functional exploits targeting five CVEs (Common Vulnerabilities and Exposures), including CVE-2022-27666.
Notably, these exploits bypass popular kernel defenses such as Kernel Address Space Layout Randomization (KASLR) and Supervisor Mode Execution Prevention (SMEP), highlighting the need for proactive discovery of new memory targets.

Research on offensive security is not the only contribution made by SCAVY. Researchers say it allows defenders to apply specific mitigations, like freelist pointer obfuscation or write-once protections for critical areas, by locating previously unknown memory targets.
The attack surface for upcoming exploits may be greatly decreased by this proactive strategy.
While SCAVY marks a significant leap forward, challenges remain, which include automating multi-field corruption analysis, which could further enhance its capabilities.
Further, expanding its applicability to other operating systems or environments could provide broader security benefits.
The research team has responsibly disclosed their findings to Linux maintainers and plans to open-source the framework, fostering collaboration within the cybersecurity community.
SCAVY extends the progressive scope of kernel security research by automating memory corruption target identification and enabling greater defenses against privilege escalation attacks.
As cyber threats increase, tools such as SCAVY will become crucial in protecting critical systems from exploitation.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
如有侵权请联系:admin#unsafe.sh
