Security researchers have uncovered a critical vulnerability in Windows stemming from its “Best-Fit” character conversion feature, which has been exploited to execute remote code.
This newly identified attack surface, dubbed “WorstFit,” leverages certain features of Windows’ internal character encoding system to launch sophisticated attacks, including path traversal, argument injection, and remote code execution (RCE).
The vulnerability has already been linked to real-world exploits affecting widely used applications like PHP-CGI, ElFinder, and Cuckoo Sandbox.
Understanding the Best-Fit Feature
Windows employs the “Best-Fit” character conversion mechanism to handle situations where a character in a Unicode string cannot be directly mapped to an ANSI string. Instead of rejecting the character, Windows substitutes it with a visually or functionally similar one. For example:
- The Unicode soft hyphen (U+00AD) is mapped to a standard hyphen (-) in certain code pages.
- The yen symbol (¥) is converted into a backslash ($$ in the Japanese code page (932).
While designed for compatibility, this behavior introduces inconsistencies that attackers can exploit when converting strings between Unicode and ANSI formats.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
The root cause of the vulnerabilities lies in a combination of factors:
- Compiler behavior and C/C++ runtime libraries.
- Developers’ reliance on ANSI APIs instead of their wide-character counterparts.
- Microsoft’s commitment to backward compatibility with legacy code pages.
Exploitation Techniques
Devcore security researchers demonstrated how this seemingly benign feature could be weaponized to compromise systems:
Argument Injection (CVE-2024-4577):
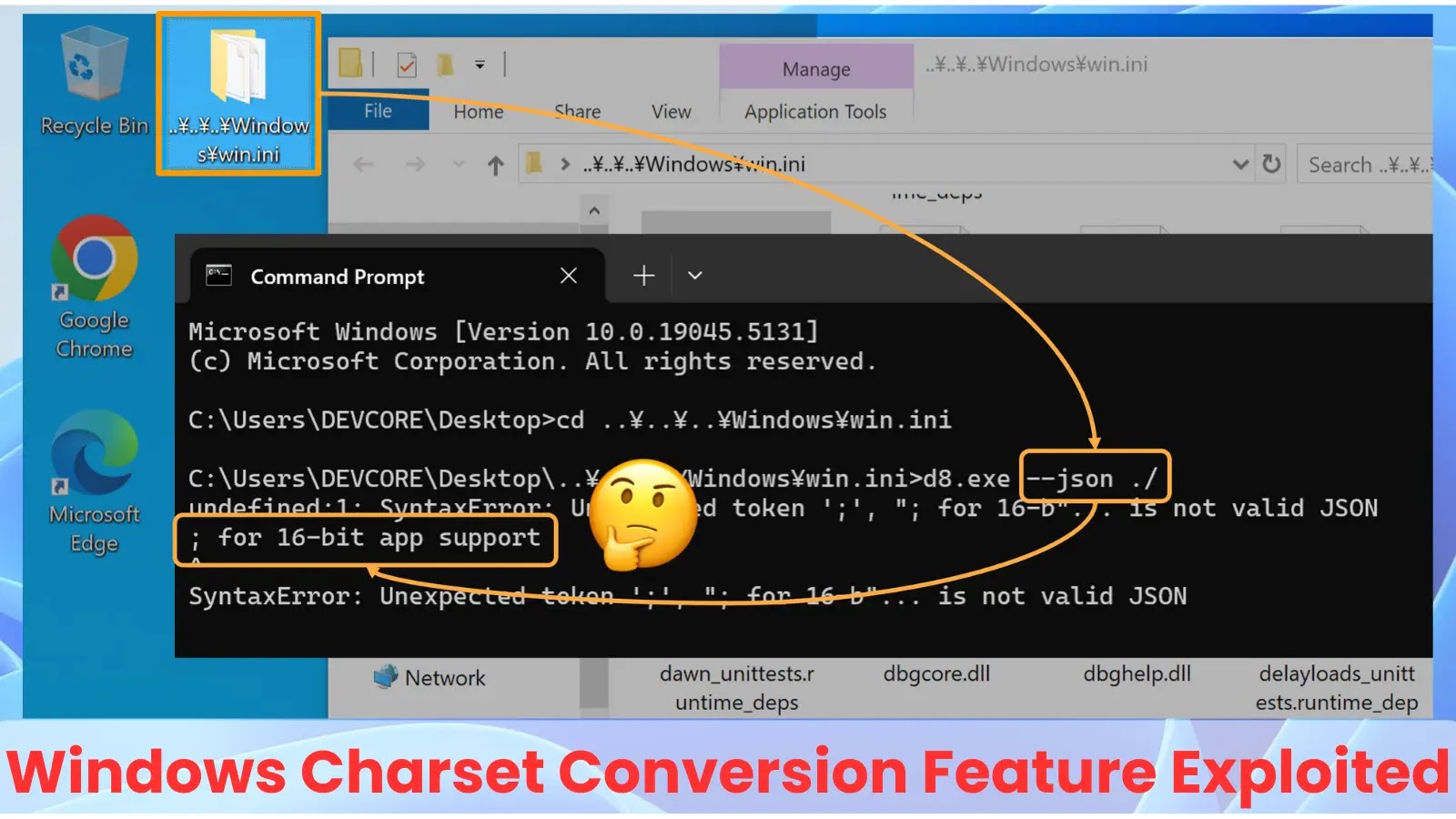
A critical vulnerability in PHP-CGI was exploited using the Best-Fit behavior. By appending ?%ADs to HTTP requests, attackers bypassed input sanitization and injected malicious arguments into PHP processes.
This flaw allowed unauthorized command execution on vulnerable servers, particularly those configured with Chinese or Japanese code pages.
Filename Smuggling:
Attackers manipulated filenames containing characters like ¥ or ₩, which are converted into slashes or backslashes during ANSI conversion.
This enabled path traversal attacks on applications relying on ANSI APIs for file handling, such as Chrome’s V8 shell and Cuckoo Sandbox. These exploits facilitated unauthorized file access and even RCE.
Command-Line Argument Manipulation:
Applications using ANSI APIs for command-line parsing were found vulnerable to argument-splitting attacks.
For instance, injecting fullwidth double quotes (") or yen symbols (¥) allowed attackers to alter command execution syntax. This flaw affected tools like wget.exe and tar.exe, enabling arbitrary command execution.
Real-World Impact
These vulnerabilities have wide-ranging effects:
PHP-CGI Exploits: CVE-2024-4577 has been actively exploited by ransomware groups like Tellyouthepass to compromise servers running PHP in CGI mode.
ElFinder RCE: By exploiting the WorstFit behavior in Windows’ tar.exe utility, attackers bypassed argument sanitization in ElFinder’s archive handling feature, achieving RCE.
Cuckoo Sandbox: A Unicode filename crafted with malicious characters enabled path traversal on outdated Python 2.7-based systems running Cuckoo Sandbox.
The exploitation of Windows’ Best-Fit character conversion highlights the risks posed by legacy compatibility features in modern systems.
As demonstrated by CVE-2024-4577 and related vulnerabilities, attackers can leverage subtle quirks in encoding conversions to breach systems and execute arbitrary code.
Developers must prioritize secure coding practices and adopt wide-character APIs to mitigate these risks effectively.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
如有侵权请联系:admin#unsafe.sh
