The North Korean-linked Andariel hacking group has been identified using a sophisticated attack campaign that employs the Relative Identifier (RID) technique to covertly create hidden administrator accounts on Windows systems.
This deceptive technique enables attackers to avoid traditional detection measures while maintaining persistent access to compromised systems.
What Is RID Hijacking?
RID Hijacking is an advanced privilege escalation technique that manipulates the RID value of a low-privilege account, such as a guest or regular user, to match the RID of a high-privilege account like an administrator.
In Windows systems, the RID is part of the Security Identifier (SID), which uniquely identifies user accounts. Threat actors can carry out RID Hijacking via a variety of account types, such as:
- Utilizing a regular user account that is present in the system
- Getting the guest account active
- Establishing a new account
According to AhnLab Security Intelligence Center (ASEC), by modifying the RID in the Security Account Manager (SAM) registry, attackers can deceive the operating system into granting administrative privileges to a low-privilege account without requiring the administrator’s password.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
This method is particularly stealthy and difficult to detect using behavior-based security tools.
The Andariel group, a known subsidiary of North Korea’s Lazarus Group, has been observed employing the following steps in their RID Hijacking attacks:

SYSTEM Privilege Escalation:
The SAM registry, which stores user account information, requires SYSTEM-level privileges for access and modification.
Andariel uses tools like PsExec and JuicyPotato to escalate their privileges to the SYSTEM level. These tools enable attackers to execute commands with the highest privileges on compromised systems.
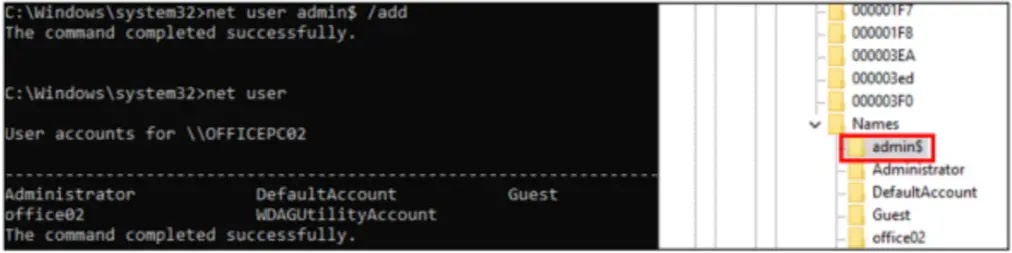
The attackers create a new user account using the net user command and append a $ symbol to the username (e.g., hiddenuser$).
This makes the account invisible in standard user listings but still accessible in the SAM registry.
The newly created account is then added to critical groups, such as Remote Desktop Users and Administrators, using the net localgroup command.

Using SYSTEM privileges, attackers navigate to the SAM registry path:
HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users.
They locate the target account’s key and modify its F value at offsets 0x30–0x33, changing it to match the RID of an administrator account.
This manipulation tricks Windows into treating the low-privilege account as an administrator.
To evade detection, Andariel exports the modified registry settings using the reg export command, deletes their rogue account, and later restores it from the saved backup when needed.
This process ensures that logs do not reveal unauthorized activity.
- Andariel employs both custom malware and open-source tools for these attacks:
- Custom malware developed by Andariel modifies SAM registry access permissions and performs RID hijacking.
An open-source tool called CreateHiddenAccount uses Microsoft’s regini.exe utility to grant necessary permissions for SAM registry modifications.
RID Hijacking is inherently stealthy due to its reliance on registry modifications rather than covert system changes.
Accounts created through this method may not appear in standard administrative tools or commands like net user. However, they can be identified through deeper inspection of:
- The SAM registry.
- Local Users and Groups in Computer Management (after reboot).
- Advanced PowerShell commands such as Get-LocalUser.
Mitigation Strategies
To defend against RID Hijacking attacks:
- Restrict access to privilege escalation tools like PsExec and JuicyPotato.
- Monitor SAM registry modifications using Local Security Authority (LSA) Subsystem Service logs.
- Enforce multi-factor authentication (MFA) for all accounts, including low-privilege ones.
- Regularly audit user accounts and RIDs for anomalies.
The Andariel group’s use of RID Hijacking highlights their evolving tactics to maintain persistence while evading detection.
Organizations must adopt proactive monitoring and robust security measures to mitigate such sophisticated threats.
As cybersecurity landscapes grow increasingly complex, staying vigilant against emerging techniques like RID Hijacking is critical for safeguarding sensitive systems.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
如有侵权请联系:admin#unsafe.sh
