2025-1-23 14:32:57 Author: cybersecuritynews.com(查看原文) 阅读量:1 收藏
Cybersecurity researchers have uncovered a new large-scale campaign involving a Mirai botnet variant dubbed “Murdoc_Botnet” that is actively exploiting vulnerabilities in AVTECH IP cameras and Huawei HG532 routers.
The campaign, which began in July 2024, has already compromised over 1,300 devices worldwide, with the majority of infections concentrated in Malaysia, Thailand, Mexico, and Indonesia.
The Murdoc_Botnet leverages two critical vulnerabilities to gain initial access and deploy its malicious payload:
- CVE-2024-7029: An unpatchable command injection vulnerability affecting end-of-life AVTECH IP cameras.
- CVE-2017-17215: A remote code execution flaw in Huawei HG532 routers.
Once a device is compromised, the attackers use a combination of ELF files and shell scripts to deploy the Murdoc_Botnet malware.
Researchers at Censys noted that the infection process involves downloading a shell script, granting it execution permissions, and then executing the payload. To maintain stealth, the malware removes traces of its installation after deployment.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Botnet’s Infrastructure
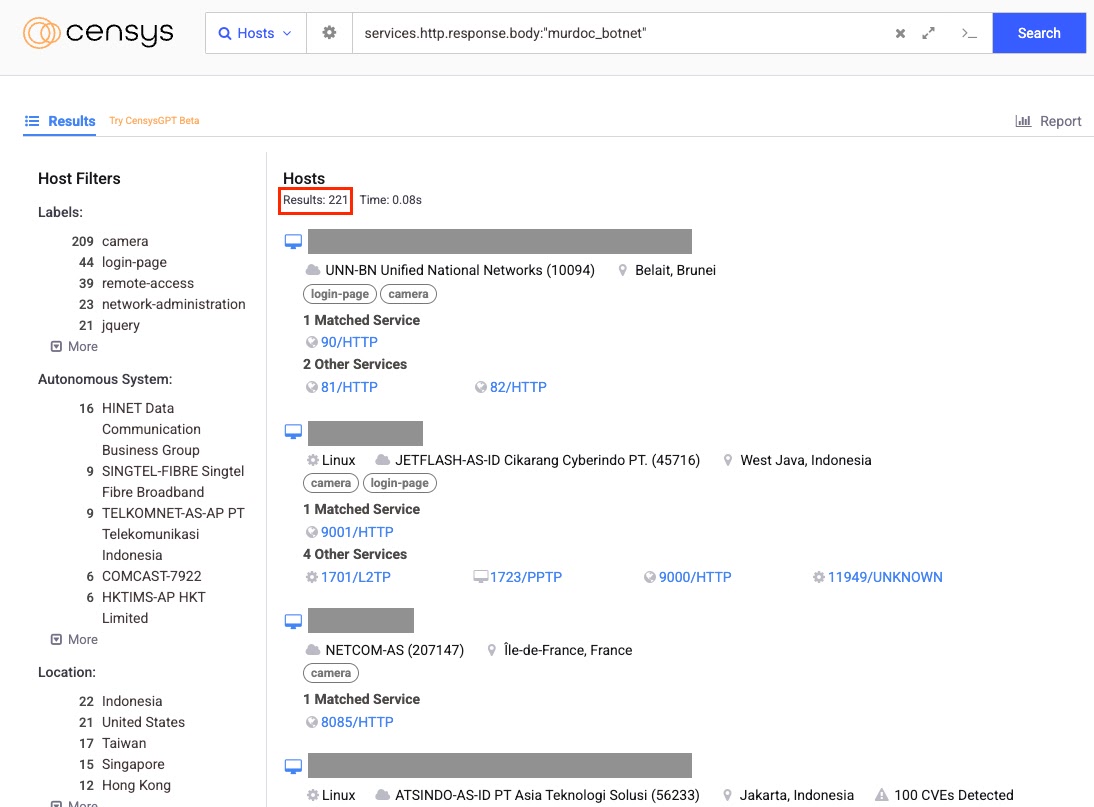
While besides this, 221 Murdoc-infected hosts concentrated in:-
- Indonesia
- The United States
- Taiwan
.webp)
The botnet’s infrastructure consists of over 100 distinct command-and-control (C2) servers, each responsible for managing compromised devices and distributing the Mirai-based malware.
These C2 servers facilitate communication with infected devices, ensuring the botnet’s propagation and enabling it to carry out large-scale distributed denial-of-service (DDoS) attacks.
Technical analysis of the Murdoc_Botnet reveals that it primarily targets *nix-based systems.
The malware utilizes bash scripts that leverage GTFOBins to fetch payloads, grant them execution permissions using chmod, and then execute and remove them to cover its tracks.
Researchers have identified over 500 malware samples, each employing variations of the same infection mechanism.
One particularly concerning aspect of this campaign is its exploitation of CVE-2024-7029, which affects end-of-life AVTECH IP cameras.
These devices no longer receive security updates, making them highly vulnerable to attacks. Currently, there are over 36,182 exposed AVTECH cameras on the internet, presenting a significant attack surface for the Murdoc_Botnet.
.webp)
The global reach of this campaign is evident, with GreyNoise sensors detecting exploit attempts from 17 distinct malicious IPs targeting the AVTECH camera vulnerability and a staggering 37,796 malicious IPs targeting the Huawei HG532 router vulnerability.
To mitigate the risks posed by the Murdoc_Botnet, organizations and individuals are advised to:-
- Monitor for suspicious processes and network activities from untrusted sources.
- Avoid executing shell scripts from unknown or untrusted sources.
- Keep all devices and firmware updated with the latest security patches.
- Isolate or replace unsupported devices, especially those exposed to the public internet.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
如有侵权请联系:admin#unsafe.sh
